PowerShell as a cyberattack weapon: Understanding execution techniques
Content in this page
- T1059: An execution sub-technique using PowerShell
- Key aspects of PowerShell
- How to detect and mitigate PowerShell execution attacks like T1059 using Log360
PowerShell is a powerful scripting language that has a command line interface (CLI) that helps with command and scripting capabilities. Primarily designed to aid system administrators, it automates administrative tasks and manages Windows system environments effectively. It also offers a robust platform for executing commands, running scripts, and dealing with the underlying operating system.
It is a flexible tool for IT specialists, system administrators, and developers, since it combines the capabilities of a CLI, a scripting language, and an automation framework. PowerShell is a versatile tool with a flexible environment that lets both legitimate administrators and threat actors interact with Windows systems and execute commands.
Threat actors can perform malicious activities with help of PowerShell, like discovery of information and execution of code. For instance, the PowerShell cmdlet Start-Process can be used to run a program or the Invoke-Command cmdlet to command on a remote computer.
T1059: An execution sub-technique using PowerShell
T1059 refers to a sub-technique within the MITRE® ATT&CK framework related to executing PowerShell commands. It indicates threat hunters using PowerShell to run scripts, run commands, and do various tasks on a target system to perform malicious activities. Given PowerShell's extensive access to the Windows operating system's functionality, it can perform a wide range of actions like lateral movement, data exfiltration, privilege escalation, and reconnaissance.
Here are some key aspects to understand how PowerShell can be leveraged:
Command execution
PowerShell provides a CLI where users can enter commands manually. A wide variety of commands known as cmdlets that carry out particular tasks are supported by the PowerShell CLI. To complete complex activities efficiently, cmdlets can be coupled and piped together.
The PowerShell CLI is used by adversaries to run arbitrary instructions from the Command Prompt. As a result, they can communicate with the underlying operating system and carry out tasks including running executables, modifying files and directories, controlling services, and working with the Windows Registry.
Script execution
PowerShell provides extensive access to system resources and administrative functionalities on Windows systems. It allows the execution of complex scripts that can automate tasks, perform system management operations, and interact with various Windows components.
Adversaries leverage PowerShell's scripting capabilities to run custom or preexisting scripts, enabling them to achieve various objectives, such as gaining persistence on a compromised system, moving laterally within a network, or stealing sensitive data and sending it to external servers controlled by the adversary.
Obfuscation and anti-analysis techniques
Adversaries frequently disguise their PowerShell commands and scripts when executing them on their target solutions. This makes it challenging for security solutions to detect and analyze the malicious activities, allowing adversaries to evade detection and carry out their attacks successfully.
To make their directives more difficult to decipher, adversaries can employ strategies like string concatenation, character substitution, encoding, or encryption.
- String concatenationTo avoid being caught by signature-based systems, adversaries break up harmful strings into smaller chunks and concatenate them at runtime.
- Character substitutionAdversaries replace specific characters in the PowerShell script with visually similar characters or alternate representations to avoid static analysis.
- Encoding and encryptionIn an attempt to make their PowerShell commands and scripts more difficult to analyze or spot using conventional security solutions, adversaries encrypt or encode them.
Living off the land
Living off the land (LOTL) attacks are used by adversaries who exploit built-in system tools or scripts that are commonly found on the target system to carry out malicious activities. Adversaries use legitimate tools present in the target's environment, making it harder for security solutions to detect and attribute the malicious actions.
Fileless malware
Fileless malware is where a malicious code or script runs directly in a device's memory without leaving any traces on the file system. In order to get beyond more conventional security measures that rely on file-based detection, adversaries adopt this sophisticated method. Fileless malware is challenging to detect and analyze because it makes use of trusted tools and processes, like PowerShell, to carry out its malicious operations.
Utilizing methods like PowerShell in-memory execution, reflective DLL loading, or direct API calls, fileless malware runs fully in memory. Since PowerShell provides a means to execute code in memory without writing files to the disk, it is less likely to be discovered by conventional antivirus and endpoint protection solutions. Therefore, adversaries leverage this feature to execute malicious PowerShell commands or scripts directly in memory.
Log360 can help to detect and mitigate PowerShell execution attacks and such stealthy attacks with a suite of security features like:
- Behavior analytics
- Mitre ATT&CK reports and
- Correlation of network events
How to detect and mitigate PowerShell execution attacks like T1059 using Log360
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities.
- Script block logging analysis
- Behavioral analytics
- MITRE ATT&CK
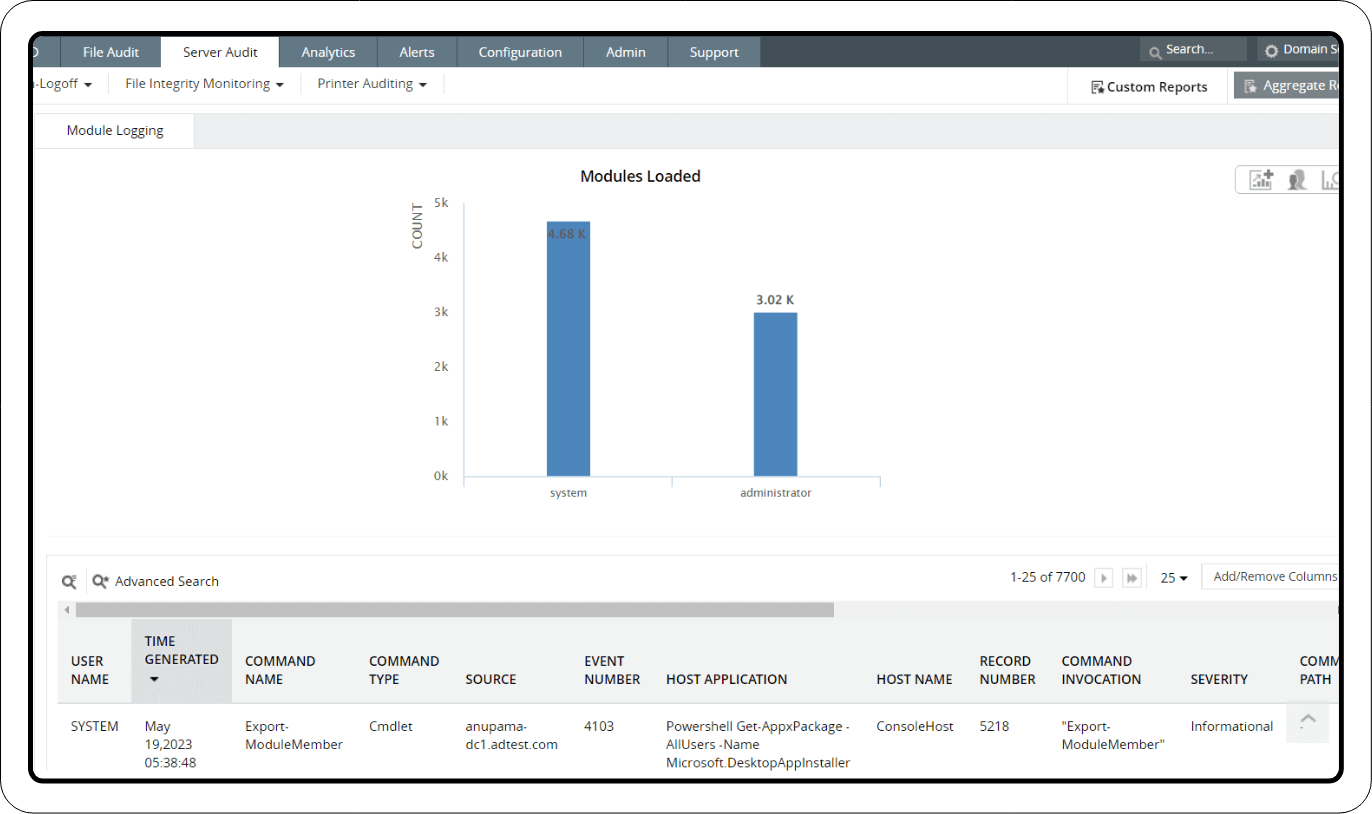
Script block logging analysis
Script block logging is a PowerShell logging and auditing capability, which plays a crucial role in capturing the detailed information about scripts and PowerShell commands that are being executed within an environment. By enabling this, enterprises can keep an eye on the commands and scripts that are being executed by users, administrators, or potentially malicious threat actors.
Threat hunters find it difficult to keep track of all the event logs generated by PowerShell scripts. To monitor all these event logs, organizations can utilize a SIEM solution like Log360, which uses Active Directory auditing to simplify threat hunting.
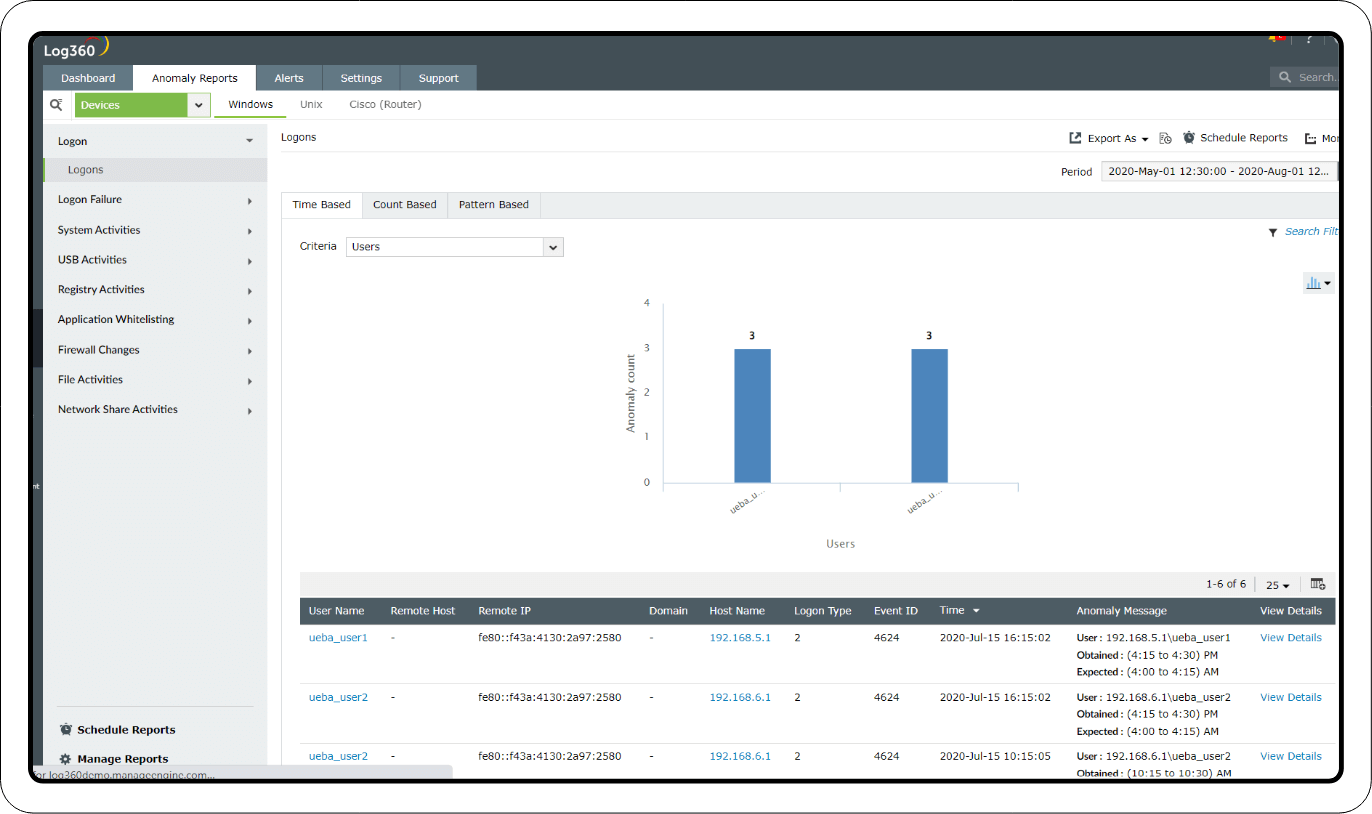
Behavioral analytics
With help of Log360's UEBA feature, threat hunters can identify anomalous PowerShell activities like unusual usage patterns, excessive command executions, or attempts to evade detection through obfuscation techniques. It also provides customizable risk scores for each anomaly, helping you prioritize threats based on severity.
MITRE ATT&CK
Log360's MITRE ATT&CK framework reports help in detecting and mitigating PowerShell-related threats like running malicious code to control the victim's systems.
Here are some MITRE ATT&CK reports that help detect PowerShell activities:
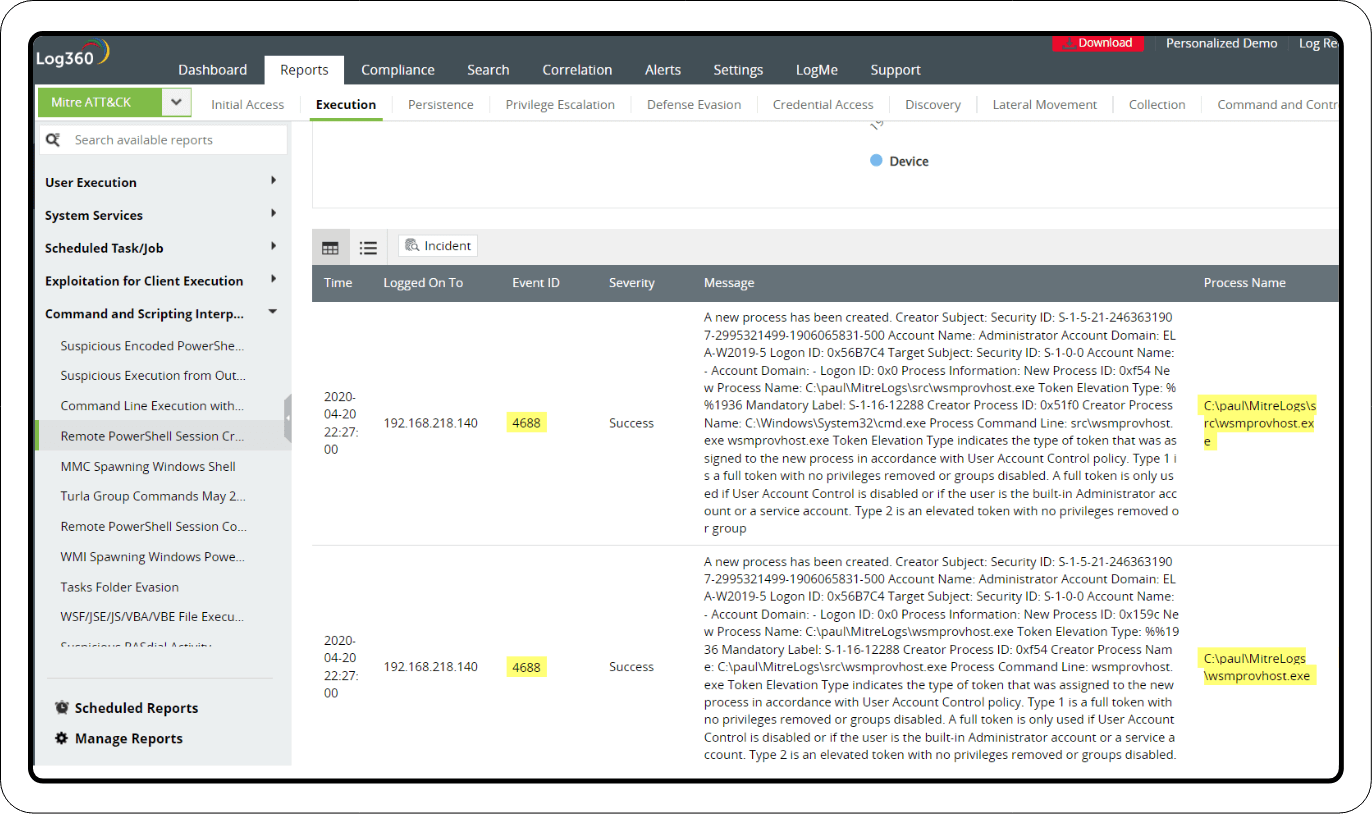
Remote PowerShell sessions
Monitor Sysmon event ID 10 (process access) and event ID 4688/4689 (new process has been created/ended), which are used to record the executed command lines. By analyzing the command lines, you can detect potentially malicious uses of PowerShell.
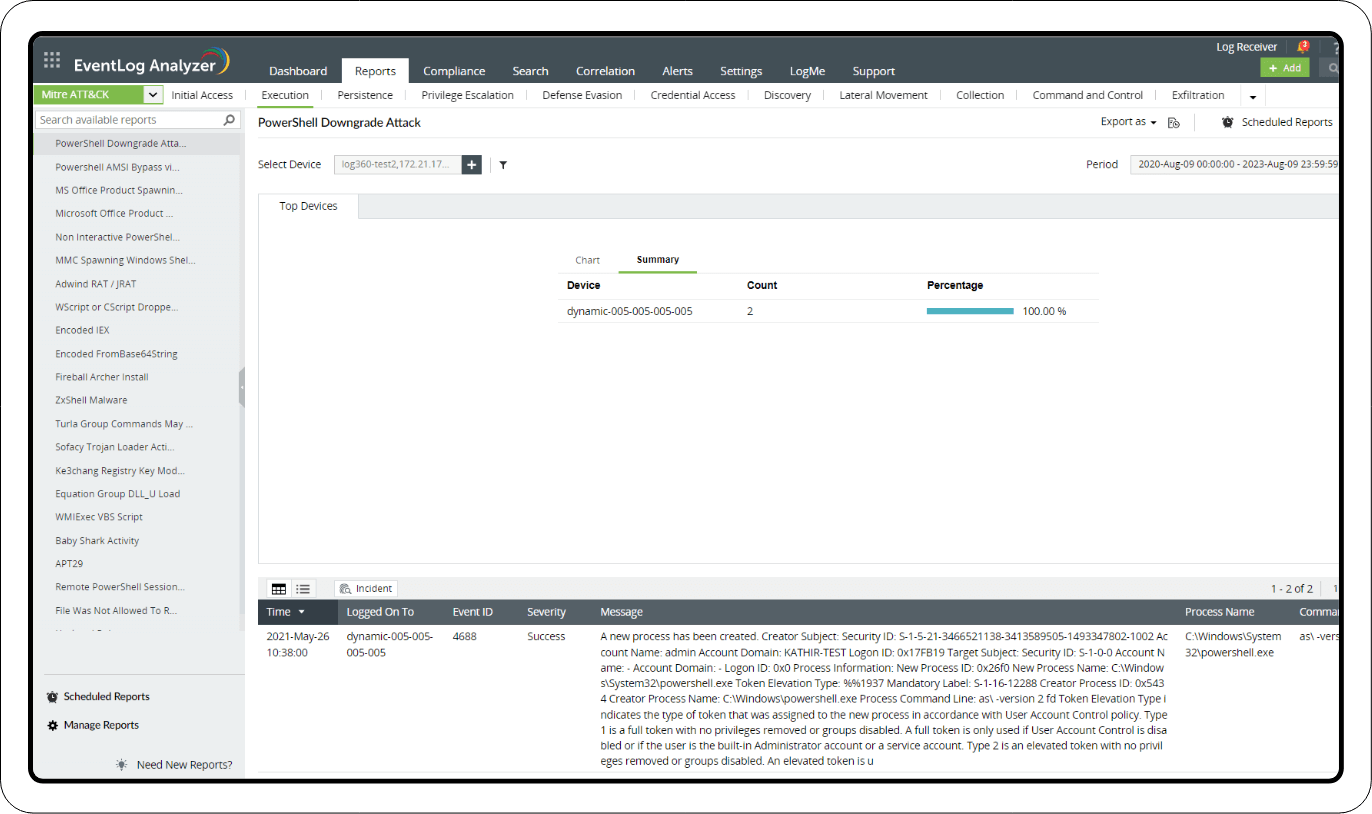
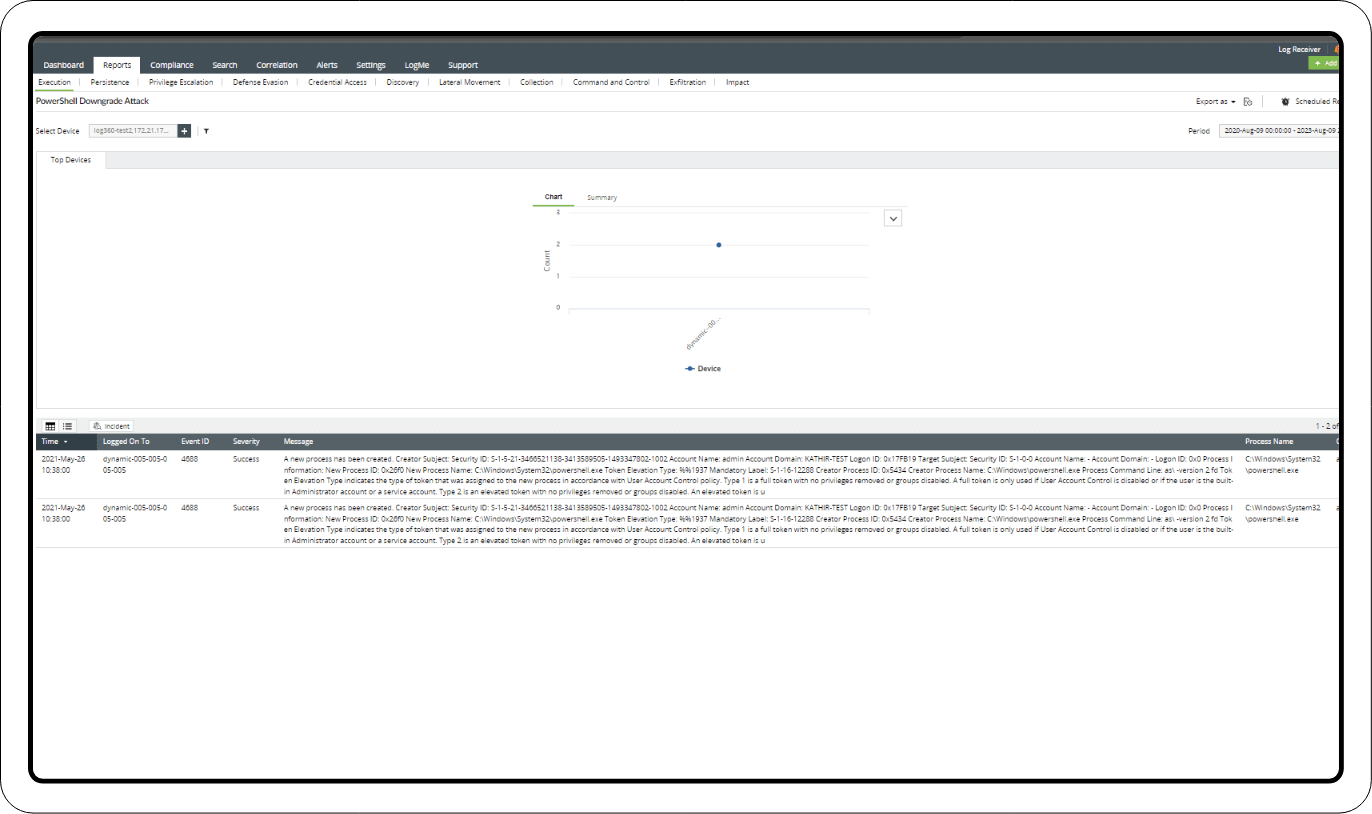
PowerShell downgrade attack
To prevent downgrade attacks, threat hunters should check for event ID 400 or 4688, each of which indicate the start of PowerShell activity, whether local or remote. This is an Engine Lifecycle event and includes the engine version. Check for instances where a PowerShell process (powershell.exe) is created, especially if it's associated with an older version of PowerShell.