Handling threats and safeguarding your organizational network can be daunting and exhaustive in terms of cost, time, and workforce. You might have an expansive security budget, but how would you effectively optimize your security plan? The basics of threat modeling are here to help you with that.
What is threat modeling?
Threat modeling is an essential proactive security planning strategy that involves predicting, identifying, and mitigating all potential threats.
This is ideally done by deeply analyzing the organizational network and all the vulnerabilities at risk of being exploited by adversaries.
There are several key steps to follow to ensure a comprehensive threat modeling strategy.
1. A structured process and continual analysis of the network's system
To analyze a system for potential threats effectively:
- Pay close attention to externally facing systems like web servers and email gateways, as well as internal applications that could be compromised through phishingor social engineering.
- Scrutinize network devices for misconfigurations and outdated firmware. Map the flow of sensitive data within the system, across networks and to external entities, assessing the strength of encryption and access controls.
- Examine network segmentation to identify weak points where attackers could breach boundaries.
- Evaluate user roles and permissions to ensure users only havenecessary access, and assess the security of third-party integrations to avoid potential back doors.
2. Regular identification of potential threats, vulnerabilities, and attack vectors
- Research known vulnerabilities in your software and hardware, referring to resources such as the Open Web Application Security Project (OWASP) Top 10, to identify and address potential security risks. It's crucial to regularly update your systems with the latest security patches to mitigate these vulnerabilities.
- Focus on strengthening internal security measures by changing default passwords, disabling unnecessary services, and staying up-to-date with security patches.
- Ensure that all software and firmware are kept up-to-date with the latest security patches.
- Continually review how errors and exceptions are handled within the system because they might reveal sensitive information or provide opportunities for attackers.
3. Prioritize and alter the security controls and mitigation strategies according to the risk assessment to reduce the risk of security breaches and data loss.
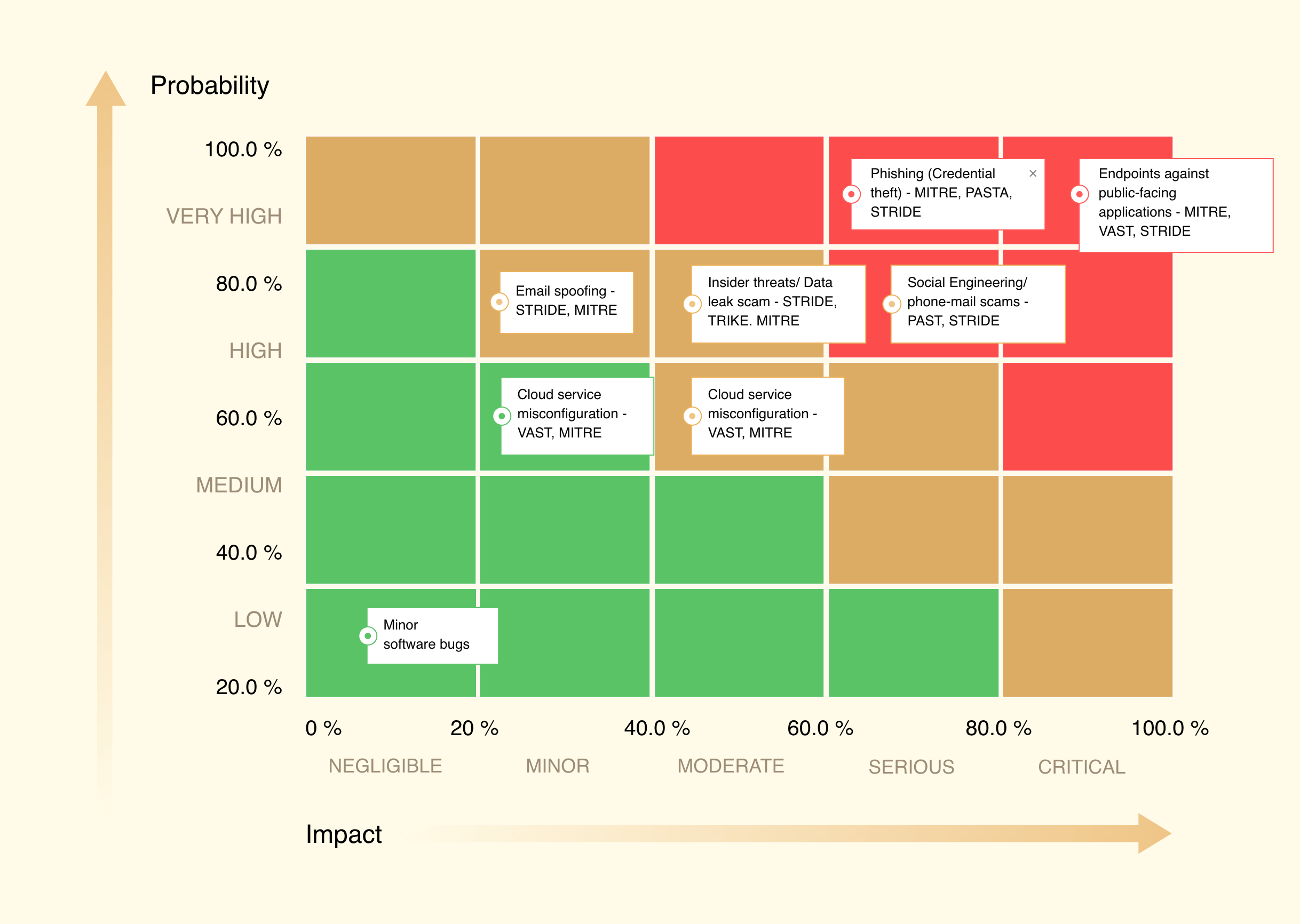
- We gain a clear understanding of the potential threats, their likelihood, and potential impact from risk and vulnerability assessments. Furthermore, by assigning probabilities and estimating potential damages to each threat scenario, we can quantify the risks.
- Once quantified, they are ranked based on their likelihood and impact. This can help us focus on high-risk threats first. Utilizing a risk matrix, we can visually categorize and manage these risks more effectively.
We have talked about identifying potential threats. But, how do we cover threat modelling for such a huge class of threats and actors? Let's have a look at it.
How do we define threat modeling for common threat classes?
It is crucial for threat modeling to systematically assess threats across the key categories below and implement tailored security controls.
Here's a breakdown of how to assess common threats across four key categories:
1. Internal threats:
- For insider access threats, analyze and enhance user access controls and physical security measures.
- Monitor privileged user activity and system logs for anomalies.
- In shared environments like cloud or shared hosting platforms, isolate access and monitor resource controls. Conduct regular penetration testing to identify and assess vulnerabilities.
2. External threats:
- To prevent unauthorized access, regularly scan networks and systems for vulnerabilities and apply security patches promptly.
- Mitigate credential compromise threats by enforcing strong password policies and password management tools.
- Implement activity monitoring and anomaly detection for privileged users to identify rogue users.
3. Application hosting:
- For VPN security, assess encryption strength and key management practices along with maintaining MFA.
- Monitor dark web and security forums for leaks related to your application.
3. Data access threats:
- Evaluate and ensure the security practices of your data vendors and include security clauses in contracts with data providers.
- Restrict access to production environments during development and testing activities to safeguard against unauthorized modifications.
- Monitor code changes and deployments for potential security risks.
Now that we are familiar with the basic threat modelling practices, let's look at some of the standard threat modelling techniques.
The top 5 standard threat modelling strategies:
1. STRIDE:
- Developed by Microsoft, STRIDE is a straightforward yet comprehensive framework focusing on six threat categories:
- It employs data flows and trust boundaries to analyze and mitigate threats, making it particularly accessible for beginners and effective for a wide range of applications.
2. PASTA (Process for attack simulation and threat analysis)
- This highly structured, risk-centric methodology involves seven steps. It begins with defining assets and data flows, followed by developing attack trees to dissect potential threats into smaller components. Each attack path is analyzed to identify potential countermeasures to mitigate the risk.
- PASTA is ideal for complex systems and offers a thorough approach to threat identification and prioritization.
3. VAST (Visual, agile, and simple threat)
- Developed by Bruce Schneier, VAST is particularly adept at addressing technical vulnerabilities. It uses a five-step process that includes identifying assets and threats, vulnerability identification, attack scenario development, risk assessment, and recommendations for mitigation. VAST is suitable for security experts who can utilize detailed knowledge of vulnerabilities and exploits.
4. Trike
- Trike's framework is slightly different from others, as it takes a "people-centric" approach, recognizing that many security incidents exploit human vulnerabilities through social engineering, phishing, and similar tactics. It assesses potential attackers, critical assets, and the effectiveness of existing security controls. Trike is valuable for identifying threats that exploit human vulnerabilities and gives a realistic perspective by considering adversary's motivations and capabilities.
5. MITRE ATT&CK: A knowledge base for real-world adversary tactics
- MITRE ATT&CK is a comprehensive knowledge base of adversary tactics and techniques based on real-world observations. It's not a threat modeling framework in the traditional sense, but it serves as a valuable resource to enhance threat modeling efforts.
- It encompasses 14 high-level categories representing the goals of an adversary during an attack (e.g., initial access, persistence, exfiltration). The framework details actions or methods used by adversaries to achieve goals in each stage, and a structured table mapping techniques to tactics provides a visual representation of the attack landscape.