Enabling REST API access will allow you to use multi-factor authentication as configured in your Microsoft 365 account. Once enabled, the user will be diverted to the Microsoft 365 login portal for authentication to use M365 Manager Plus. REST API is also essential to generate reports on your Microsoft 365 setup.
Steps to configure REST API
Automatic configuration
- Login to M365 Manager Plus' admin portal.
- Choose the Tenant Settings option found at the top right corner.
- Select the Enable Now option found under the Rest API Access column, corresponding to the Microsoft 365 tenant for which REST API access must be enabled.
- You will be diverted to the Microsoft 365 login portal. Enter the credentials of the global admin account you had configured in M365 Manager Plus.
- Click Sign-in.
- An application for M365 Manager Plus will be created automatically. And, you will now see a page that displays the list of permission that the application needs.
- Go through the list and click Accept.
- You will now be redirected to M365 Manager Plus console and REST API Access will be Enabled for the account you configured.
NOTE: If you want to change the permissions required by the application, perform manual configuration.
Manual Configuration
If the automatic configuration was not successful due to permission issues, REST API Access must be configured manually. The error message will show you a pop-up where you should fill the appropriate values to complete the configuration.
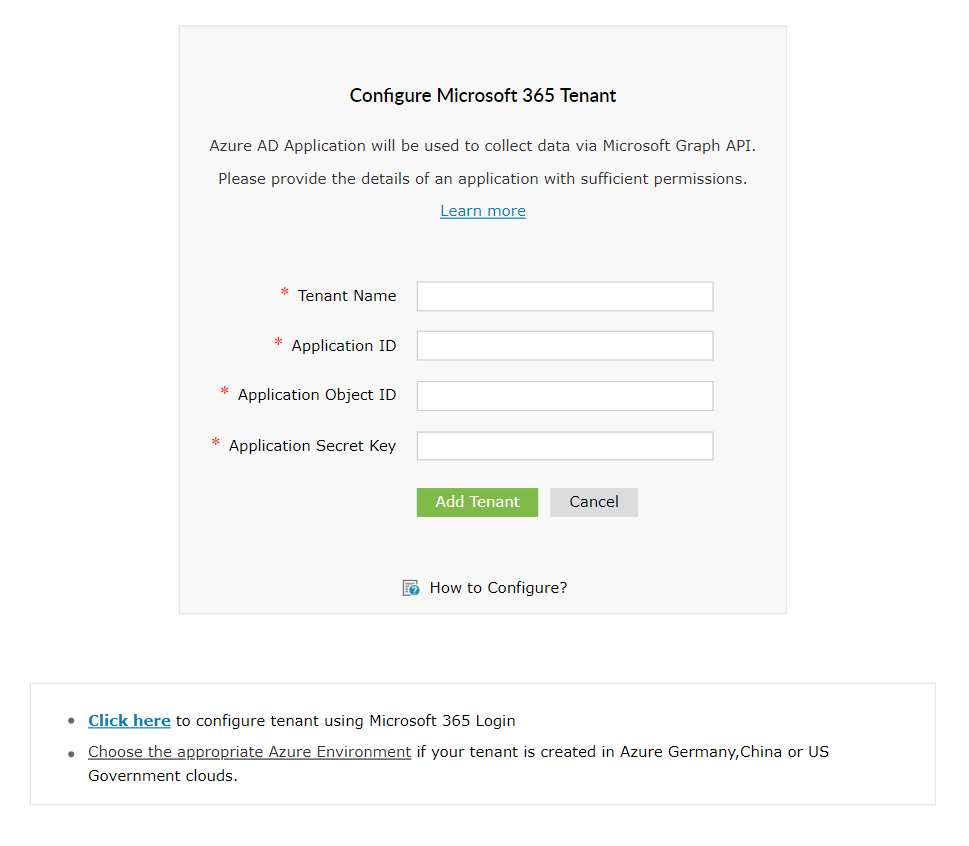
Azure Portal
- Sign in to Azure AD portal using the credentials of the Global Administrator account for which you need to enable REST API.
- Select Azure Active Directory from the left pane.
- Select App registrations.
- Click on New registration.
- Provide a Name of your choice for the M365 Manager Plus application to be created.
- Select a supported account type based on your organizational need.
- Don't enter anything for Redirect URI (optional), you'll configure it in the next few steps.
- Click on Register to complete the initial app registration.
- You will now see the Overview page of the registered application.
- Click on Add a Redirect URI.
- Click on Add a platform under Platform configurations.
- In the Configure platforms pop-up, click on Web under Web applications.
- In the REDIRECT URI field, enter http://localhost:port_number/webclient/VerifyUser.
For example, http://localhost:8365/webclient/VerifyUser or https://192.345.679.345:8365/webclient/VerifyUser.
- You can leave the Logout URL and Implicit grant fields empty. Click on Configure.
- In the Authentication page, Under Redirect URIs, click on Add URI.
- Enter http://localhost:port_number/webclient/ GrantAccess as the Redirect URI. For example, http://localhost:8365/webclient/GrantAccess or https://192.345.679.345:8365/webclient/GrantAccess.
- Again click on Add URI to add https://demo.o365managerplus.com/oauth/redirect, https://manageengine.com/microsoft-365-management-reporting/redirect.html and https://identitymanager.manageengine.eu/api/public/v1/oauth/redirect as REDIRECT URIs in the subsequent rows.
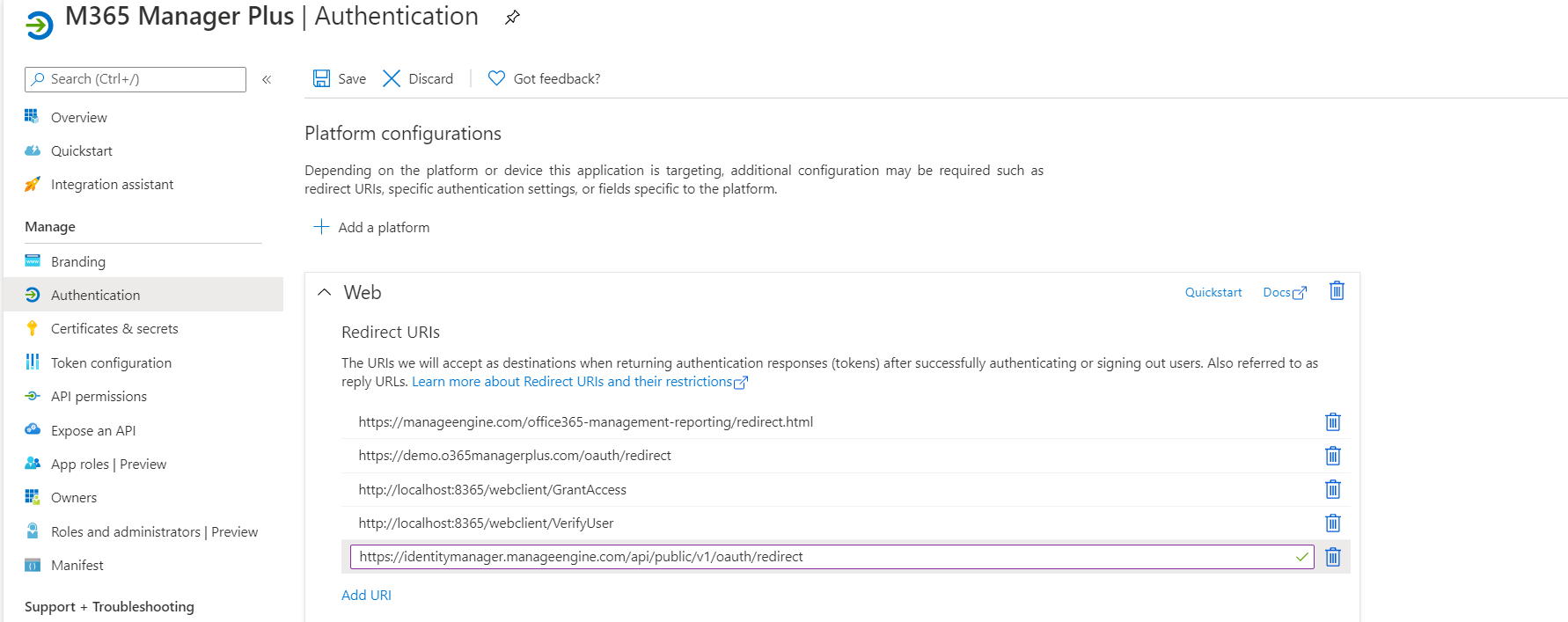
Note: The REDIRECT URI must be,
- Less than 256 characters in length.
- Should not contain wildcard characters.
- Should not contain query strings
- Must start with HTTPS or http://localhost
- Must be a valid and unique URL.
Based on the Connection Type (http/https) you have configured in M365 Manager Plus, the REDIRECT URI format varies.
- For http, the URI value is, http://localhost:8365. Machine name or IP address cannot be used in place of localhost, if http is used.
- For https, the URI value is, https://192.345.679.345:8365 or https://testmachine:8365.
To find your machine's IP, open Command Prompt, type ipconfig and click enter. You can find your IPv4 Address in the results shown.
- Click on Save.
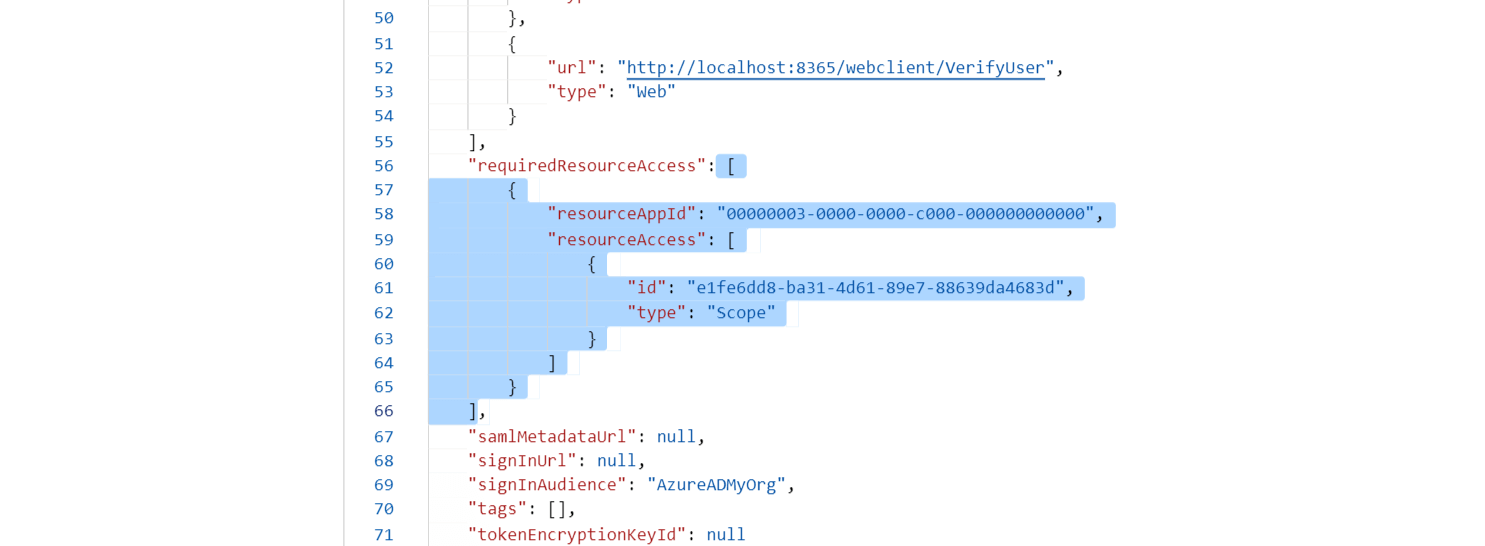
- Click on Manifest in the left pane.
- Look for requiredResourceAccess array in the code.
- Copy the entire content in this file and paste it in the section that is highlighted in the below image.
Note:
- If your tenant is created in Azure Germany, copy the entire content in this file and paste it in the section that is highlighted in the image below.
- If your tenant is created in Azure China, copy the entire content in this file and paste it in the section that is highlighted in the image below.
Note: Copy-paste content only from the open square bracket to the close square bracket. Ensure that all punctuation marks are retained correctly. Once you have pasted the file, it should look like the below image.
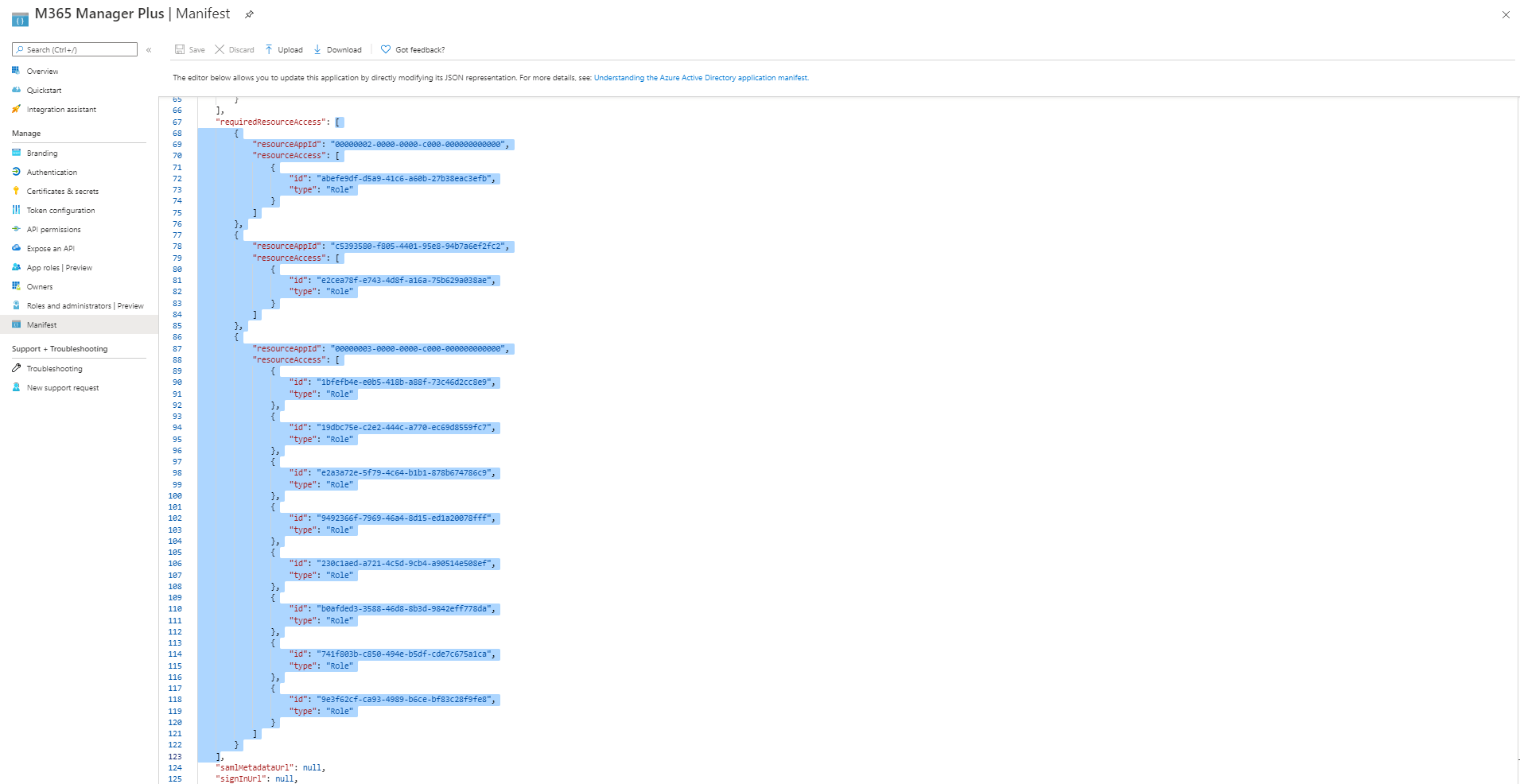
- Click on Save.
- Click on API permissions in the left pane.
- In the Configured permissions section, click on ✓ Grant admin consent for <your_company_name>.
- Click on Yes in the pop-up that appears.
- Click on Certificates & secrets from the left pane.
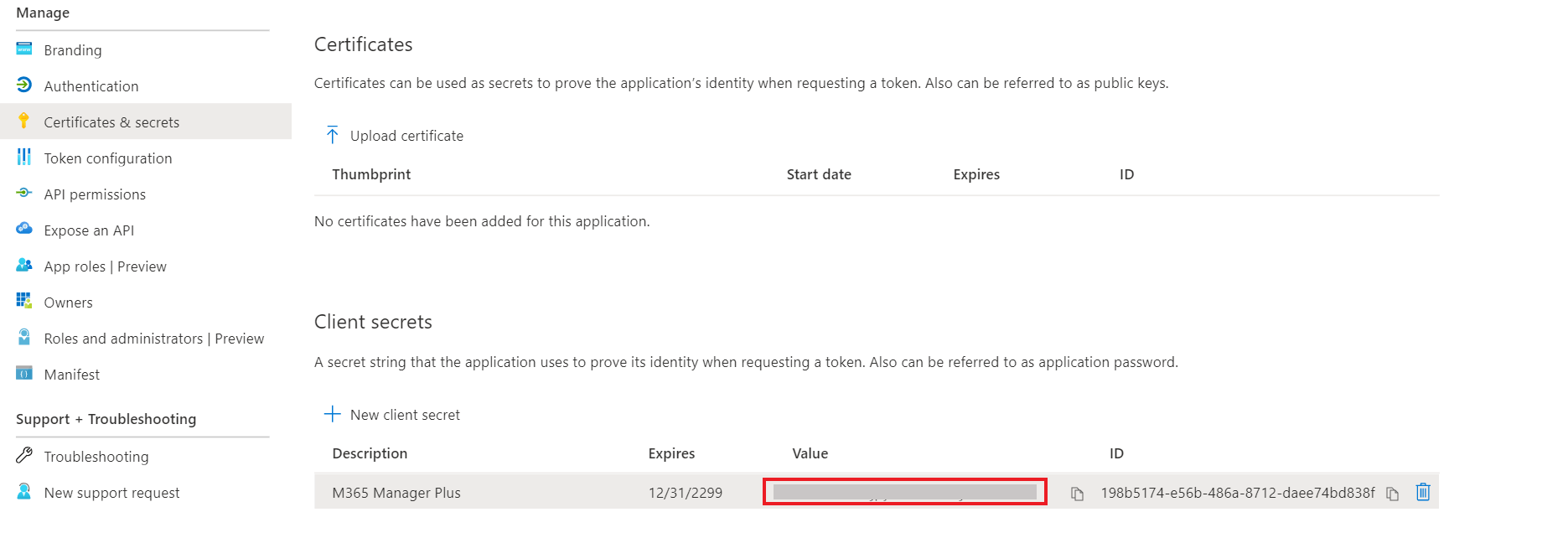
- Under the Client secrets section, click on New client secret.
- This section generates an app password for M365 Manager Plus. In the Description field of the pop-up, provide a name to identify the app to which the password belongs.
- Choose when the password should expire.
- Click on Add.
- Copy the string under VALUE and save it. This is the Application secret key which you will require later.
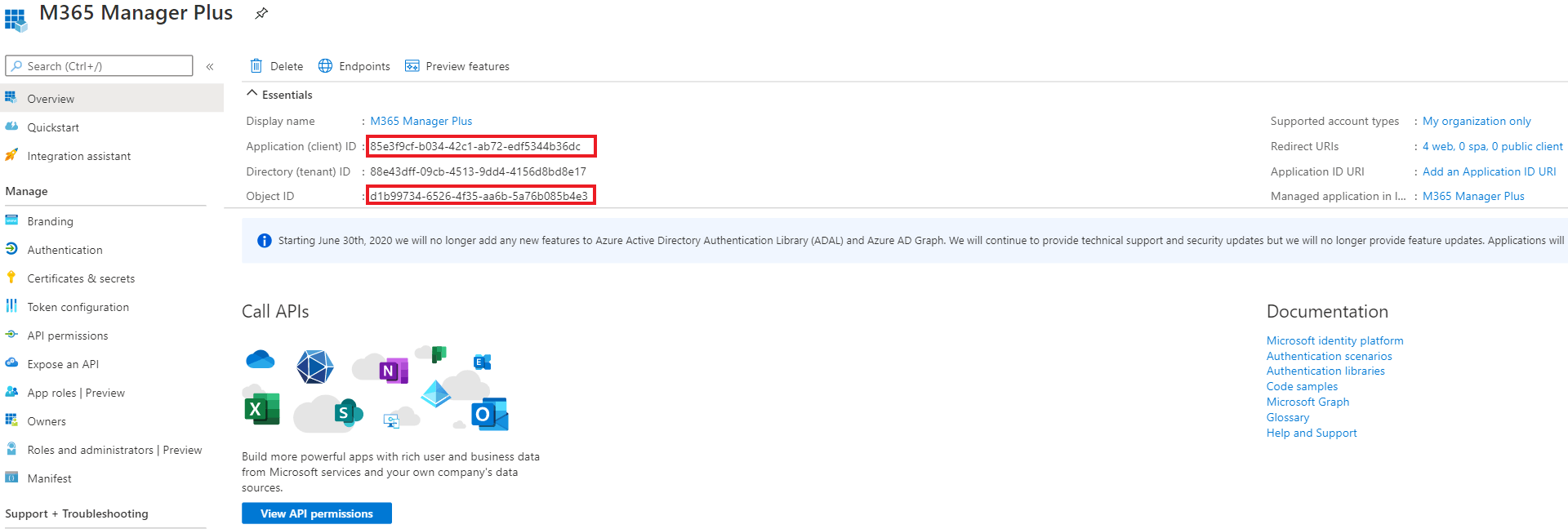
- Now go to the Overview section in the left pane.
- Copy the values of Application (client) ID and Object ID, and save them. You will need these values to configure your tenant in the M365 Manager Plus portal.
- Ensure that the Help desk administrator and Privileged authentication administrator roles are assigned to the application.
M365 Manager Plus portal
- Now go back to the M365 Manager Plus console where you have the pop-up.

- Enter your Tenant Name. For example, test.onmicrosoft.com
- Paste the Application ID and Application Object ID values which were copied in Step 33, in the respective fields.
- For Application Secret Key, paste the value which was copied in Step 31.
- Click on Add Tenant.
- You can now see that the Rest API Access is Enabled for the account you had configured.






