Automate iOS/iPadOS/tvOS Updates
This document provides guidelines on managing OS updates for iOS/iPadOS/tvOS devices.
Admins have several options to manage and control updates across their devices. These features ensure that updates are handled efficiently, providing flexibility and control over the process.
Capabilities for Admins
- Deploy Updates: Distribute and apply update policies to device groups, automating update delivery across the fleet of managed devices.
- List Available Updates: View all eligible Apple updates and identify compatible devices ready for the latest updates.
- Monitor Update Status: Track the update process across devices, observing stages like in-progress, completed, or failed updates.
- Delay Update: Control when updates are visible or available to end-users, with options to defer updates for up to 90 days.
- Force OS Updates: Initiate immediate updates on devices, bypassing passcodes if necessary to ensure critical updates are applied, even on locked devices.
- Automate OS Update Policy Setup: Configure a one-time OS update policy that automatically applies to all future updates, simplifying the setup process and ensuring consistent deployment across all devices.
- On-Demand Update Policies: Create policies for specific scenarios as needed and delete them after use to maintain flexibility and avoid clutter.
OS Update Management Views
There are two key views in OS update management: the Update View and the Device View. First, let's explore the Update View.
Update View
The Update View offers a centralised overview of OS versions across the entire device fleet. It enables administrators to:
- Monitor applicable OS versions.
- Track compliance with update policies.
- Ensure updates are applied within defined timelines.
This view provides a high-level summary, helping administrators maintain consistency and compliance throughout the fleet. It also allows for quick identification of devices that require attention, ensuring efficient update deployment.
Details about the Device View, which provides insights into individual devices and their specific update statuses, will follow in subsequent sections.
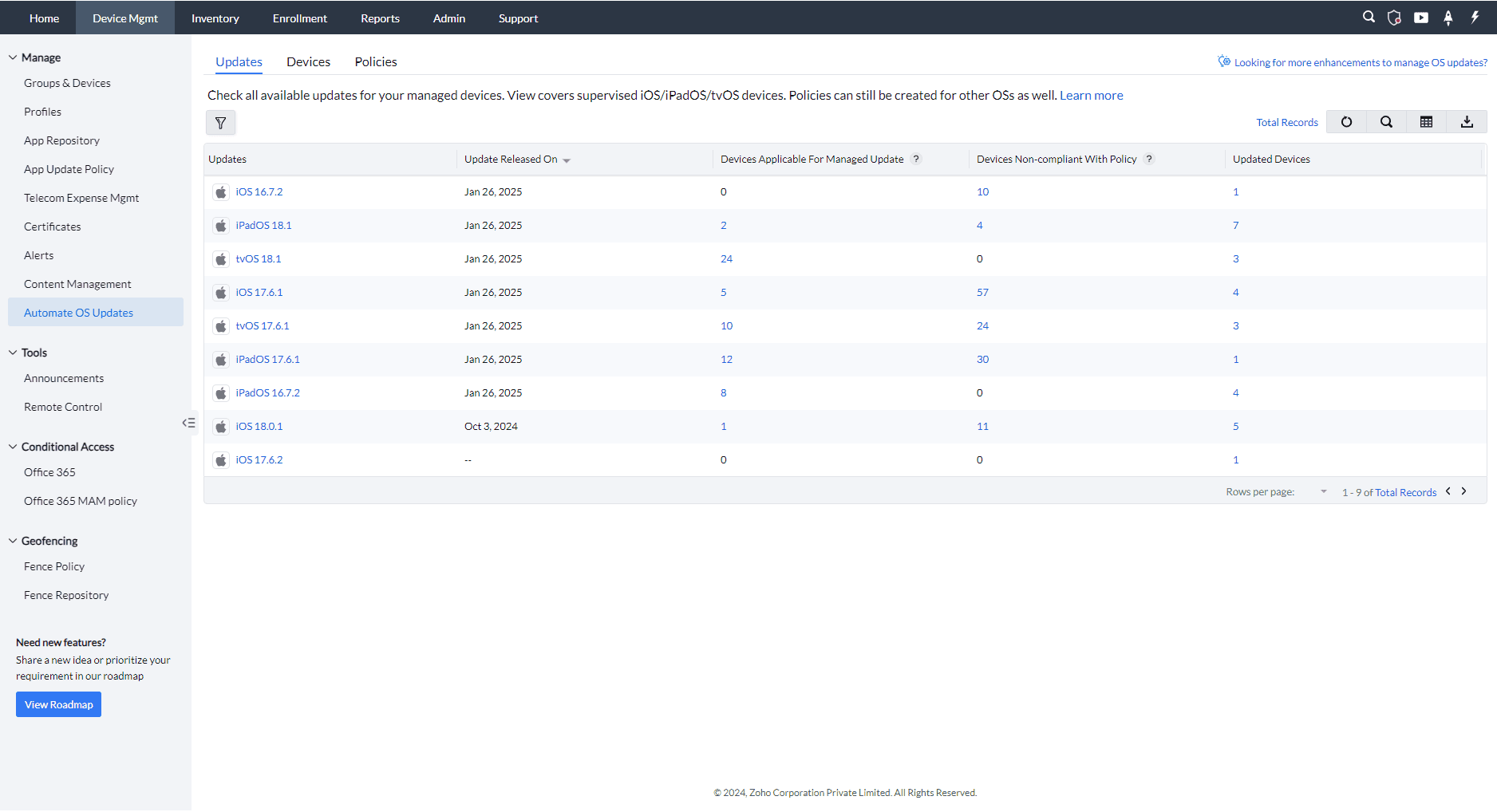
Here are some key columns from the Update View:
| Field | Description |
|---|---|
| Devices Applicable for Updates | Lists the devices eligible for the OS update of that specific version. |
| Non-compliant with Policy | This column shows devices that have not complied with the applied update policy. If a policy is applied to a device but the update hasn’t been installed, the device will be marked as non-compliant. Example: If 5 devices can receive the iOS 16 update, this column shows "5". |
| Update Expires On | Displays the expiration date of a specific OS update. Once the expiration date is reached, the admin can no longer apply that version and must move to the next available OS version. |
Note: These views are applicable only for iOS, iPadOS, and tvOS devices.
The OS update policy creation is only available in Professional, Free, and Trial editions of MDM.
Automating Update Policies
Before diving into the steps for configuring the policy, it’s essential to understand the purpose of automating updates. This feature ensures that all devices receive updates automatically, eliminating the need to manually set up updates each time a new version is released. Automation streamlines update deployment and maintains consistency across the device fleet, reducing administrative overhead.
Prerequisites for Configuring Update Policies
Before configuring update policies, ensure the following prerequisites are met to enable smooth policy creation and deployment:
| Prerequisite | Details |
|---|---|
| Devices running iOS/iPadOS 10.0 or laterr, tvOS 12.0 or later | Must be enrolled and supervised via Apple Business Manager. |
| Battery Requirement | Devices must have at least 50 percent battery. |
| Network Requirement (Wi-Fi/5G) | iOS/iPadOS devices must be connected to Wi-Fi to initiate the OS update, or the "Allow More Data on 5G" option must be enabled in data mode for devices with 5G capability. |
Configure and Distribute Updates
To configure an update policy, follow these steps:
- On the MDM server, navigate to Device Mgmt from the top menu and select Automate OS Updates from the left pane.
- Click on Create Policy, choose iOS/iPadOS/tvOS, and provide a name for the policy.
- Once you’ve configured the policy settings, click Save again to finalise and publish the policy.
- To deploy the policy, select it from the list, click Distribute Policy, choose the device group, and click Select to distribute the OS update policy to the selected devices.
Note: When an OS update policy is configured as "immediately," MDM will detect the update and distribute it to the devices within 24 to 48 hours.
Additional Considerations:
- Immediate Deployment for Testing: You may choose to deploy the update policy immediately for test groups. This ensures the update behaviour can be evaluated on a smaller scale before rolling it out to production.
- Deferring Updates for Production Groups: For production environments, you can defer the update to ensure compatibility and avoid disrupting critical workflows. More details about deferral settings and best practices will be covered in subsequent sections.
To minimize disruptions, updates can be delayed for thorough testing and compatibility checks. The following section outlines how to defer updates effectively.
Defer Updates
The "Delay" option in allows administrators to defer updates for up to 90 days from the OS release date.
Understanding How an OS Deferral Policy Works
When managing OS updates, the deferral period is calculated from the OS release date. In this scenario, the OS update policy is configured with a 45-day deferral period, allowing time for testing and preparation before updates are made available to devices. The timeline below illustrates how this policy is applied when two updates are released.
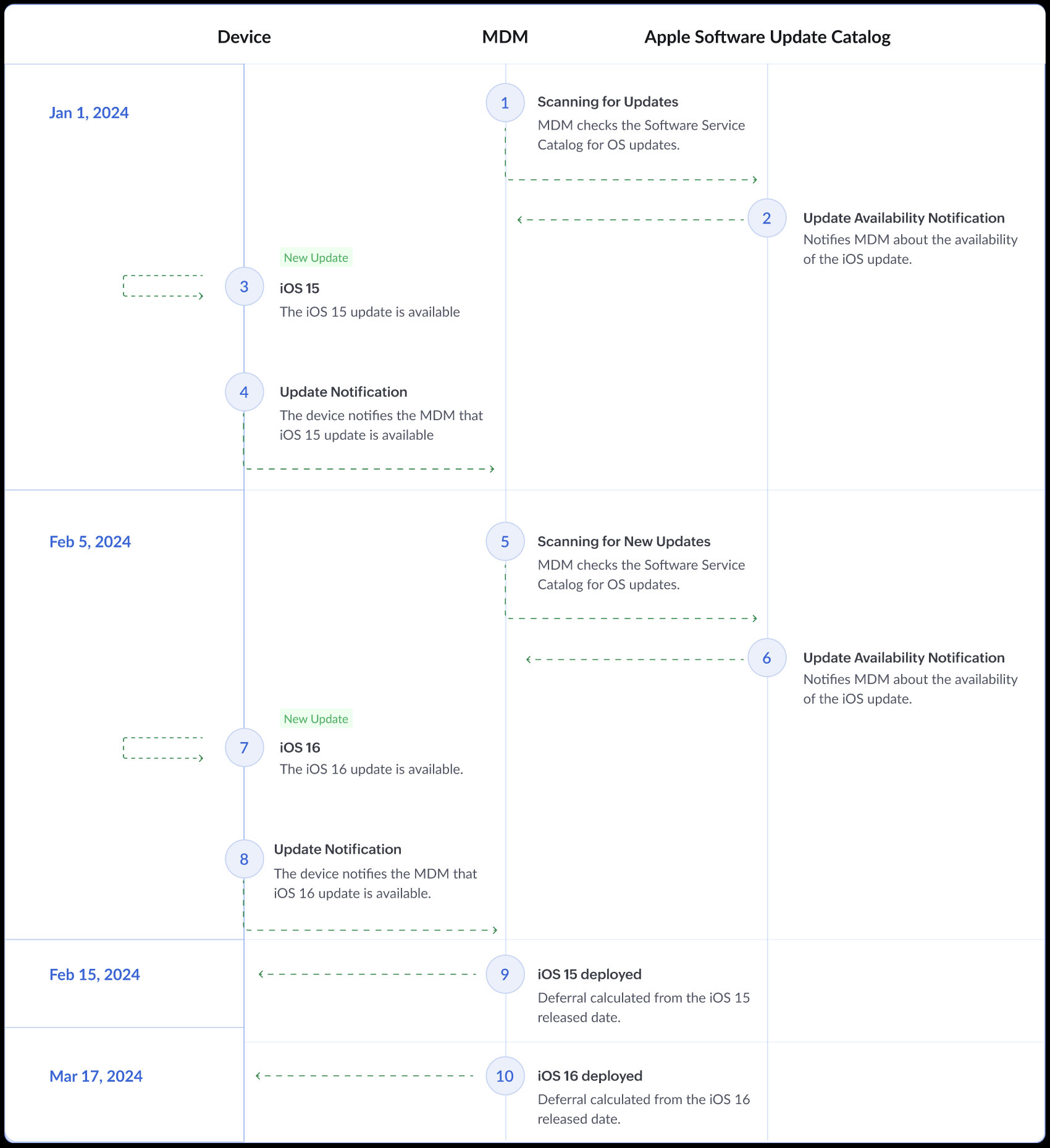
Deferring updates is crucial in scenarios where app compatibility is a concern. For example, if your organization uses an enterprise app that only supports iOS 15, releasing iOS 16 without proper testing could cause the app to become unusable. By deferring the iOS 16 update, your IT team can test the app with the new OS version, address any compatibility issues, and ensure business continuity before rolling out the update across all devices.
Note: For iOS 11.3 and below, users can manually update their devices even if a delay policy is in place. When a delay is applied, a device running iOS 14.0 might update to iOS 14.1 after the delay, even if iOS 14.5 is available. If delay is applied, MDM will automatically install the update 10 days before its expiry. If an update has expired, the next available update will be pushed, factoring in the delay.
However, in cases where immediate action is needed, such as applying urgent security patches, the "Force OS Updates" feature can be used. This allows administrators to deploy updates immediately by clearing device passcodes, ensuring updates are applied even on locked devices.
Note: For passcode-protected devices, OS updates can only proceed once the user enters the passcode. You can either exclude these devices from updates or distribute a passcode policy prompting users to set a new passcode after the update. To force OS updates on such devices, the option to clear the existing passcode should be selected.
With deferral policies covered, the next section delves into the Device View, a centralised interface for monitoring update deployment and ensuring compliance.
Device View
The Device View acts as a centralised dashboard for monitoring the deployment process and post-deployment activities.
It provides detailed insights into individual devices, such as their current OS version, available updates, and the deployment status. By navigating into the policy, admins can further check the status of updates applied under that policy, offering a granular view of the deployment process.
It allows admins to take quick actions like retrying failed updates or initiating scans for devices that missed updates. These capabilities ensure a seamless update experience and compliance across the device fleet.
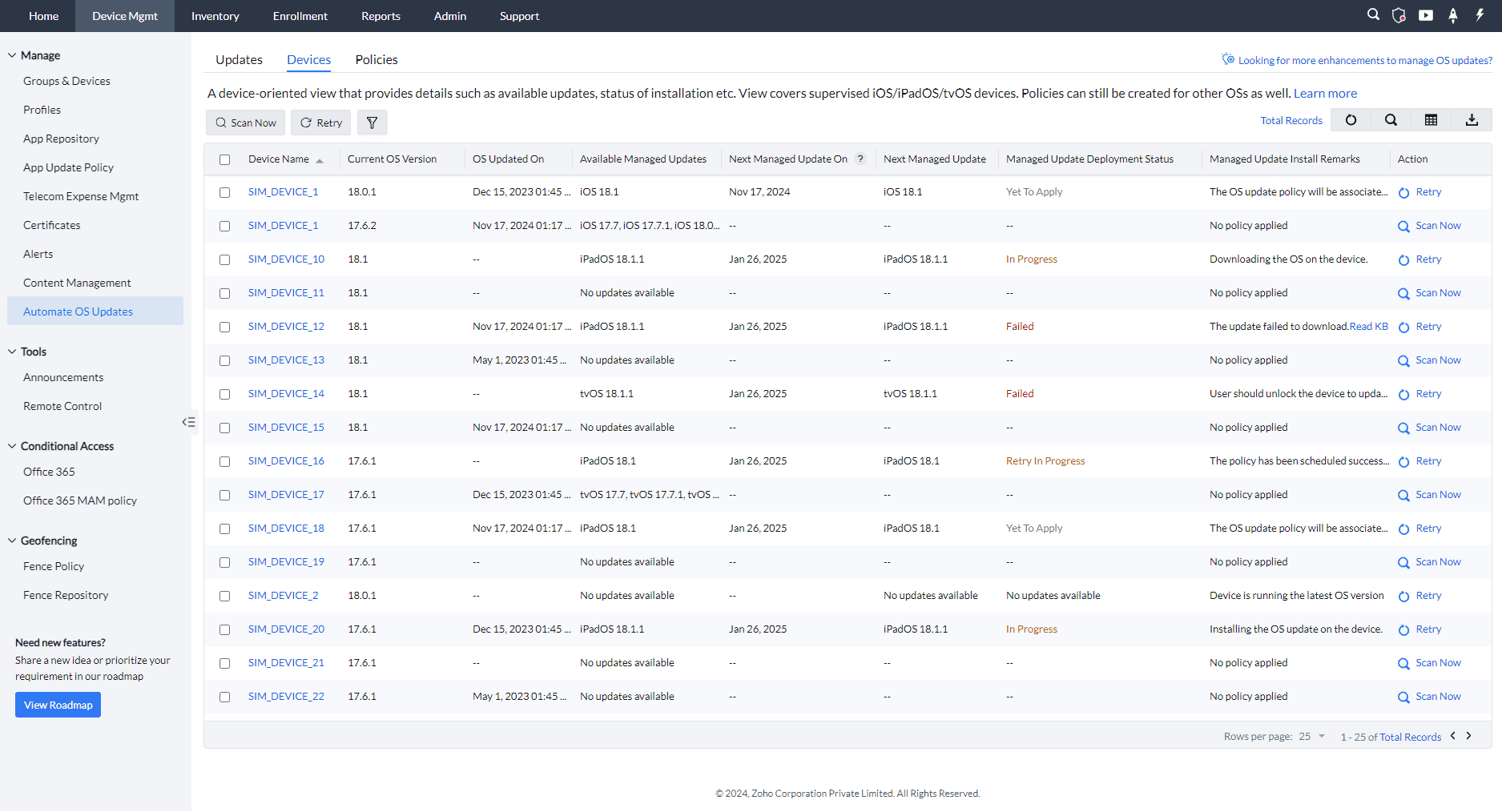
Here are the key columns from the Device View:
| Field | Description |
|---|---|
| Next Managed Update On | Provides the date when the next OS update will be applied to the device. If a deferral policy is applied, this date is calculated based on the OS release date. Example: If the OS was released on Oct 10 and a 15-day deferral is applied on Oct 15, the next update will apply on Oct 25. |
| Managed Update Deployment Status | Displays the current stage of the OS update process for each device. It shows whether the OS update is in progress, yet to be applied, has failed, or has been successfully installed on the device. |
| Managed Update Install Remarks | Displays the status of the OS update process, both at the device and policy levels. It includes information such as whether the update is scheduled, being installed, or has encountered an issue. Example: "Policy has been scheduled" or "Retry in progress." |
| Next Managed Update | Shows the OS update that will be applied next to the device. If multiple updates are available, the earlier version will be applied first. Example: If both iOS 15.0 and iOS 15.1 are available, iOS 15.0 will be applied first. |
| Action | Offers two actions:
|
Remarks During the Update Process
Manage OS updates efficiently by using the table below to understand statuses and their corresponding remarks.
| Status | Remarks |
|---|---|
| Yet To Apply |
|
| Notification Sent |
|
| In Progress |
|
| Failed |
|
| Not Applicable |
|
Troubleshooting Update Failures
In the event of issues during the update process on devices, troubleshooting steps can help resolve them. For detailed troubleshooting, refer here.
Note: If an OS update fails, MDM will retry automatically within a few hours and daily until the update expires. After expiry, the next version will be attempted. For Apple devices, updates require a Wi-Fi connection or enabling "Allow More Data on 5G" in data mode for 5G-capable devices.
With troubleshooting in place, the following best practices will help you optimize and streamline your Apple OS update management process.
Best Practices for Apple OS Update Management
- Staggering Update Roll-outs: Begin with a small test group to identify issues before deploying updates organization-wide, minimizing potential disruptions.
- Backup and Restore Considerations: Ensure devices are backed up before major updates to prevent data loss and allow quick recovery.
- Content Caching: Enable content caching on any Mac connected to the corporate network by going to System Settings > General > Sharing and turning it on. This stores updates locally, reducing bandwidth and speeding up the update process for other devices. For more information, refer to Apple's guide on content caching .
