Network security audit tool
Maintaining a secure network environment is critical. Regular network security audits play a vital role in achieving this goal. These audits systematically examine your network for vulnerabilities, misconfigurations, and security weaknesses. Traditionally, manual audits were the norm. However, this approach is not only time-consuming and error-prone, but it can also lead to critical security gaps being overlooked.
Network security audit tools or network security audit software provide an automated solution to this challenge. By streamlining the audit process, these tools empower network administrators to gain a comprehensive understanding of their network's security posture. This allows them to identify and address potential threats before they can be exploited by attackers.
Selecting the right network audit tool is essential. Network Configuration Manager stands out as a powerful all-in-one network security audit tool. It offers a comprehensive suite of features designed to simplify and automate network security audits. This empowers network administrators to stay ahead of potential threats and ensure their network's continued security.
Benefits of using network security auditing tool
Network auditing tools offer numerous advantages over manual audits, making them invaluable assets for network administrators. Here are some key benefits:
- Efficiency and automation: Manual audits are often time-consuming and labor-intensive. Network security auditing tools automate much of the process, allowing administrators to allocate their time more effectively.
- Enhanced accuracy: Manual audits are susceptible to human error, potentially resulting in overlooked vulnerabilities. Network security audit software utilizes automated scans and standardized procedures, ensuring a more consistent and precise assessment.
- Comprehensive visibility:Network audit software can thoroughly scan the entire network infrastructure, providing detailed insights into its security posture. They identify devices, configurations, vulnerabilities, and potential security gaps that might escape notice in a manual review.
- Prioritization and remediation: Many network security audit tools prioritize vulnerabilities based on severity and exploit potential, enabling administrators to address the most critical issues promptly and allocate resources efficiently for remediation.
- Compliance management: Network security audits are often necessary for compliance with industry regulations or internal security policies. These tools facilitate the compliance process by generating reports that demonstrate adherence to specific security standards.
- Proactive threat detection: Regular scans with network auditing software help identify vulnerabilities before they are exploited by attackers, allowing administrators to take proactive measures to maintain a robust security posture.
- Cost savings: Although there is an initial investment in the network auditing tool, the long-term benefits—such as improved security, reduced downtime, and faster remediation—can lead to significant cost savings over time.
You can harness these benefits by utilizing Network Configuration Manager as your network security audit tool.
Features of network audit software, Network Configuration Manager
Asset discovery and inventory
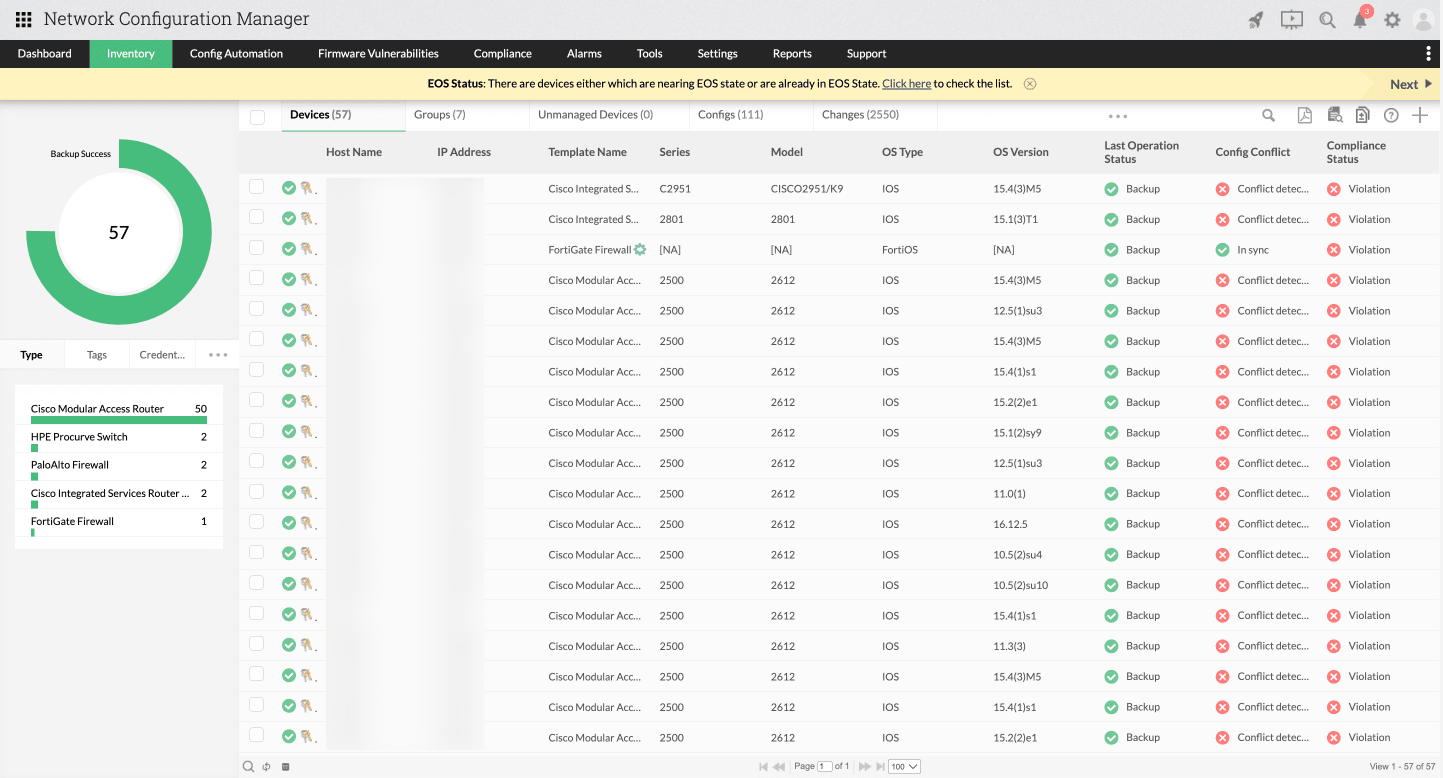
Network Configuration Manager offers a thorough inventory of your assets, featuring essential details such as host name, IP address, configuration conflict status, compliance status, backup status, and more. This aids administrators in swiftly identifying problematic devices during network audits.
Compliance auditing
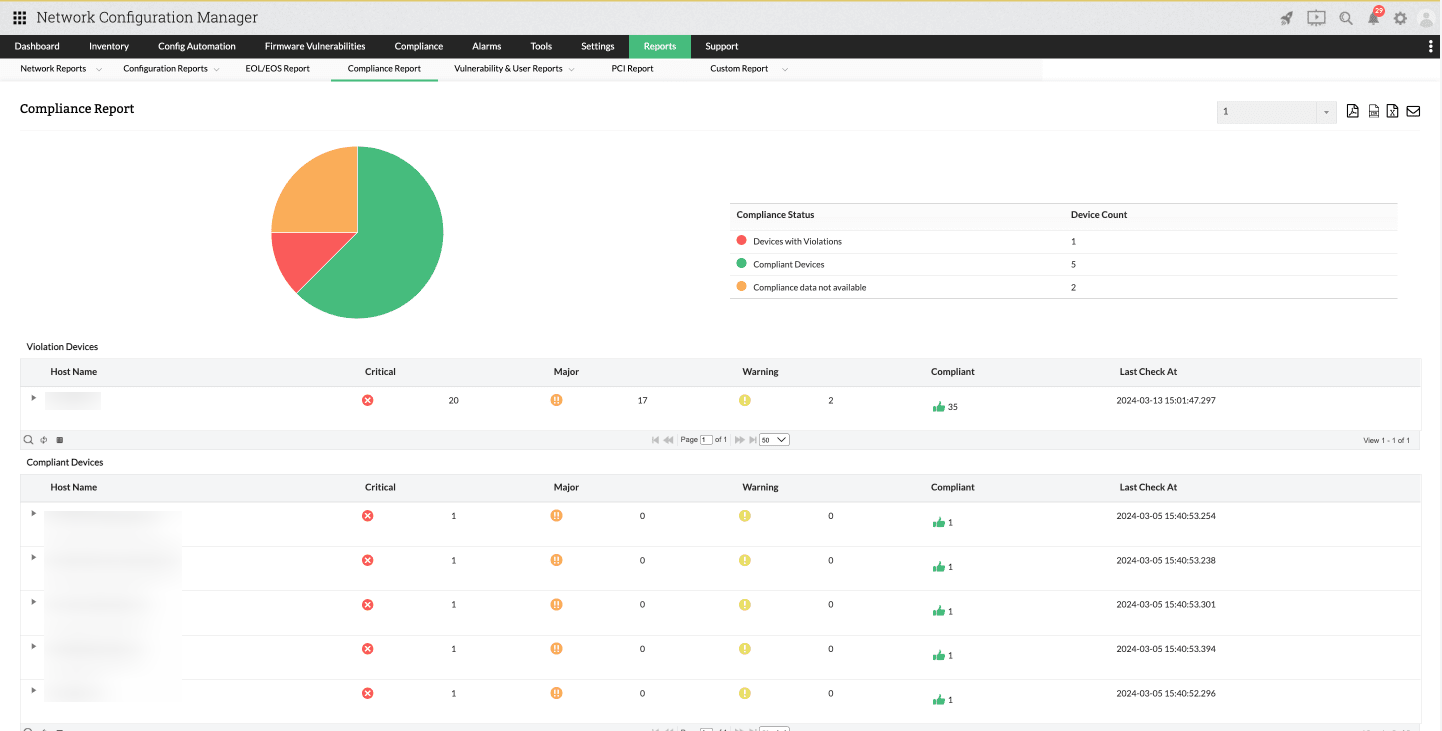
Compliance auditing is crucial in network infrastructure as it serves as the primary avenue for uncovering security vulnerabilities. Network Configuration Manager offers a dedicated real-time compliance report, containing information on devices that are either compliant or in violation. For each device, you can investigate further to find specific policy violations, severity levels (critical, major, and warning), etc.
Accessing the violated policy provides detailed information on the rules that were violated, allowing you to implement Configlets for remediation purposes. This streamlines compliance auditing for administrators and helps seal potential security loopholes, preventing disasters.
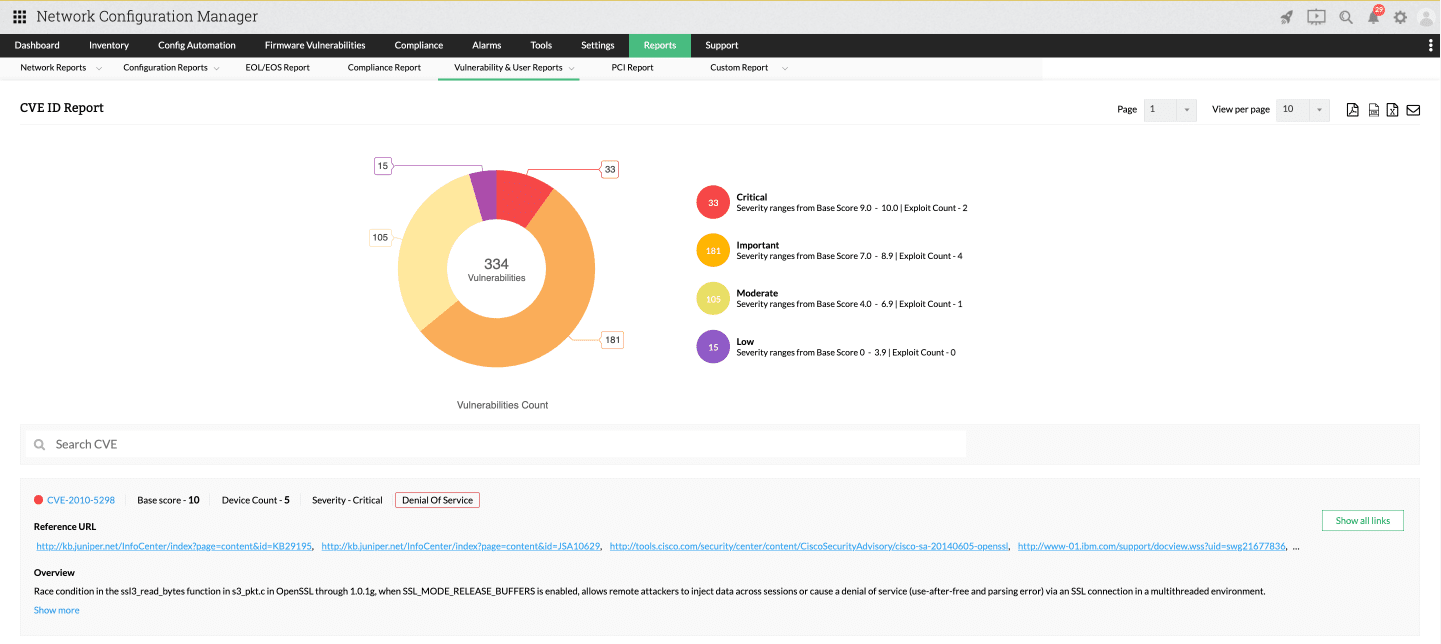
Firmware vulnerability management
The firmware of devices is critical and presents another potential security vulnerability for attackers to exploit. Auditing each device's firmware for potential threats in a manual environment is nearly impossible. However, with Network Configuration Manager you gain access to a dedicated firmware management feature. This feature provides a comprehensive list of vulnerable devices, along with their CVE ID, base score, severity, and links to potential patch fixes. Additionally, you can utilize specific vulnerability reports such as CVE ID report, exposed devices report, firmware version report, vulnerability fix trend, and device vulnerability history for effortless network auditing.
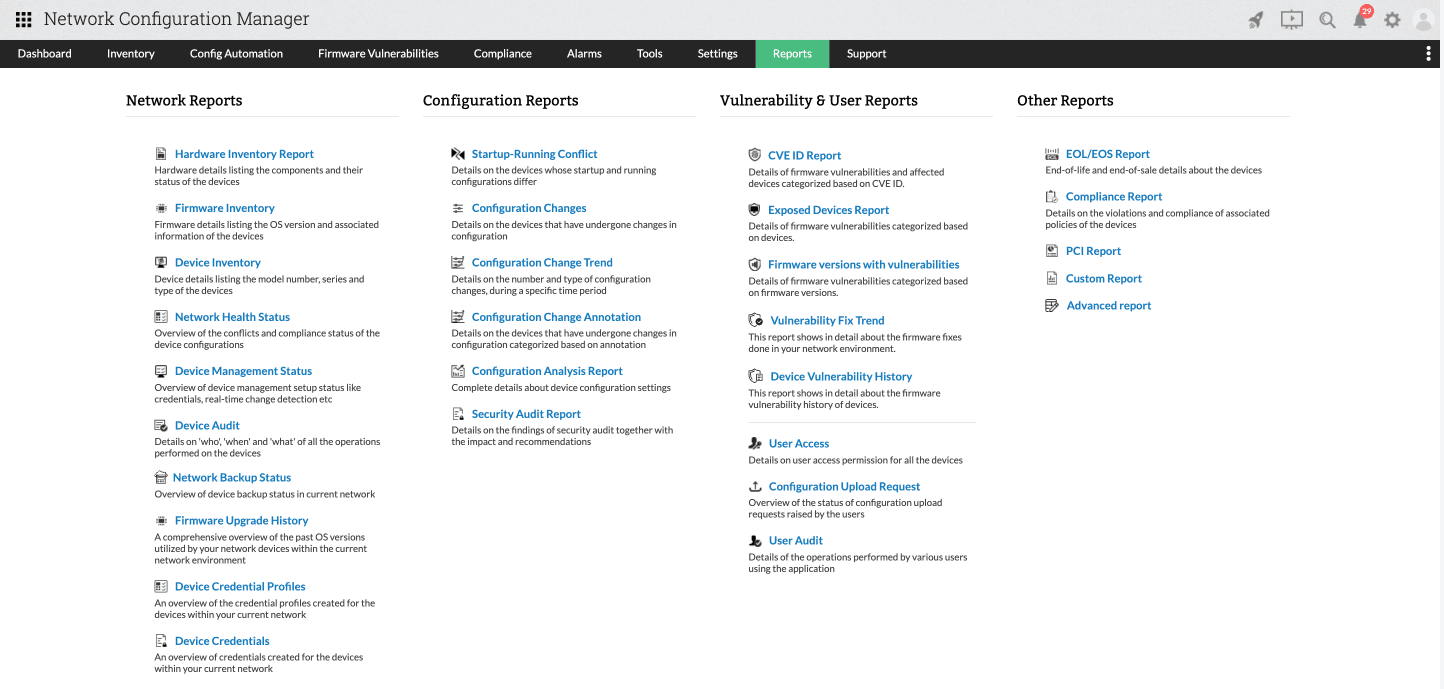
Reporting and analytics
Reports are fundamental to auditing as they offer detailed data on every metric of your network infrastructure. Network Configuration Manager facilitates network security auditing by ensuring that no anomalies are overlooked, offering around 26 reports including the compliance and vulnerability reports.
Why ManageEngine's Network Configuration Manager is an ideal network audit software
Selecting the right network audit software is crucial for ensuring network security, compliance, and operational efficiency. ManageEngine's Network Configuration Manager (NCM) offers a robust solution that simplifies audits while providing advanced features and automation. Here's why NCM is the ideal choice for auditing your network infrastructure:
1. Comprehensive multi-vendor support
NCM supports a wide range of network devices, including switches, routers, and firewalls from leading vendors. This versatility makes it the perfect network auditing tool for organizations with heterogeneous network environments, ensuring streamlined auditing without switching tools.
2. Automated configuration backups for hassle-free audits
One of the key challenges in auditing is managing up-to-date configurations. NCM's automated backup feature ensures that device configurations are consistently saved, offering audit-ready data that reduces manual effort and speeds up the process.
3. Real-time change monitoring and alerts
Configuration drift and unauthorized changes can create significant vulnerabilities. NCM continuously monitors configurations and provides real-time alerts for any changes. This proactive feature makes audits more effective by flagging potential issues as they happen.
4. Compliance and policy management
NCM's built-in compliance auditing tools ensure your network aligns with regulatory standards like HIPAA, or custom internal policies. By generating detailed compliance reports, NCM helps you identify violations and provides actionable steps to remediate them using pre-configured configlets.
5. Firmware vulnerability management
Outdated firmware is a common source of security breaches. NCM, a network security audit software, includes scanning firmware for vulnerabilities, mapping them to CVEs, and suggesting relevant patches. This feature helps administrators stay ahead of potential threats.
6. Audit-ready reports
With over 25 customizable reports, NCM simplifies audits by providing actionable insights. From inventory reports to compliance assessments and vulnerability summaries, these reports ensure a comprehensive view of your network's security and compliance status.
7. Enhanced access control with RBAC
Role-Based Access Control (RBAC) ensures only authorized personnel can access or modify configurations. This feature strengthens audit processes by verifying proper access controls are in place, minimizing the risk of unauthorized actions.
Ready to audit your network configurations with ease? Try Network Configuration for free, schedule a personalized demo with our products experts, and recieve a detailed price quote based on your requirements.
FAQs about network audit tool
What are network audits?
+
Why is it important to use network security auditing software to conduct audits?
+
How does ManageEngine's Network Configuration Manager help with regulatory compliance auditing?
+
Can I access ManageEngine's Network Configuration Manager for free?
+
What is the best tool for network audit?
+