Managing SSH Keys and Key Groups
PAM360 offers comprehensive SSH key management for securely handling key associations, rotations, and deployments across various user accounts and resources. Key features include associating SSH keys with individual accounts or resources, automating key rotation on a schedule, dissociating keys to revoke access, and pushing key files to remote users. PAM360 also provides bulk key management with key groups, allows customization of user home directories for key deployment, and supports key file export and audit history tracking for thorough oversight and compliance.
This document traverse you through the SSH keys management operations performed from the PAM360 interface.
- Associating SSH Keys with User Accounts
- SSH Key Management Operations
- SSH Key Groups for Management
- Miscellaneous Operations
1. Associating the SSH Keys
Upon importing or creating the SSH keys, you can associate the keys with SSH users.
Caution
If a root user or administrator credential has been provided for a resource, keys can be associated with all enumerated user accounts of the resource. If there are no keys available in the PAM360 database, then you will be prompted to create a key during association. Create a key pair and return to these steps.
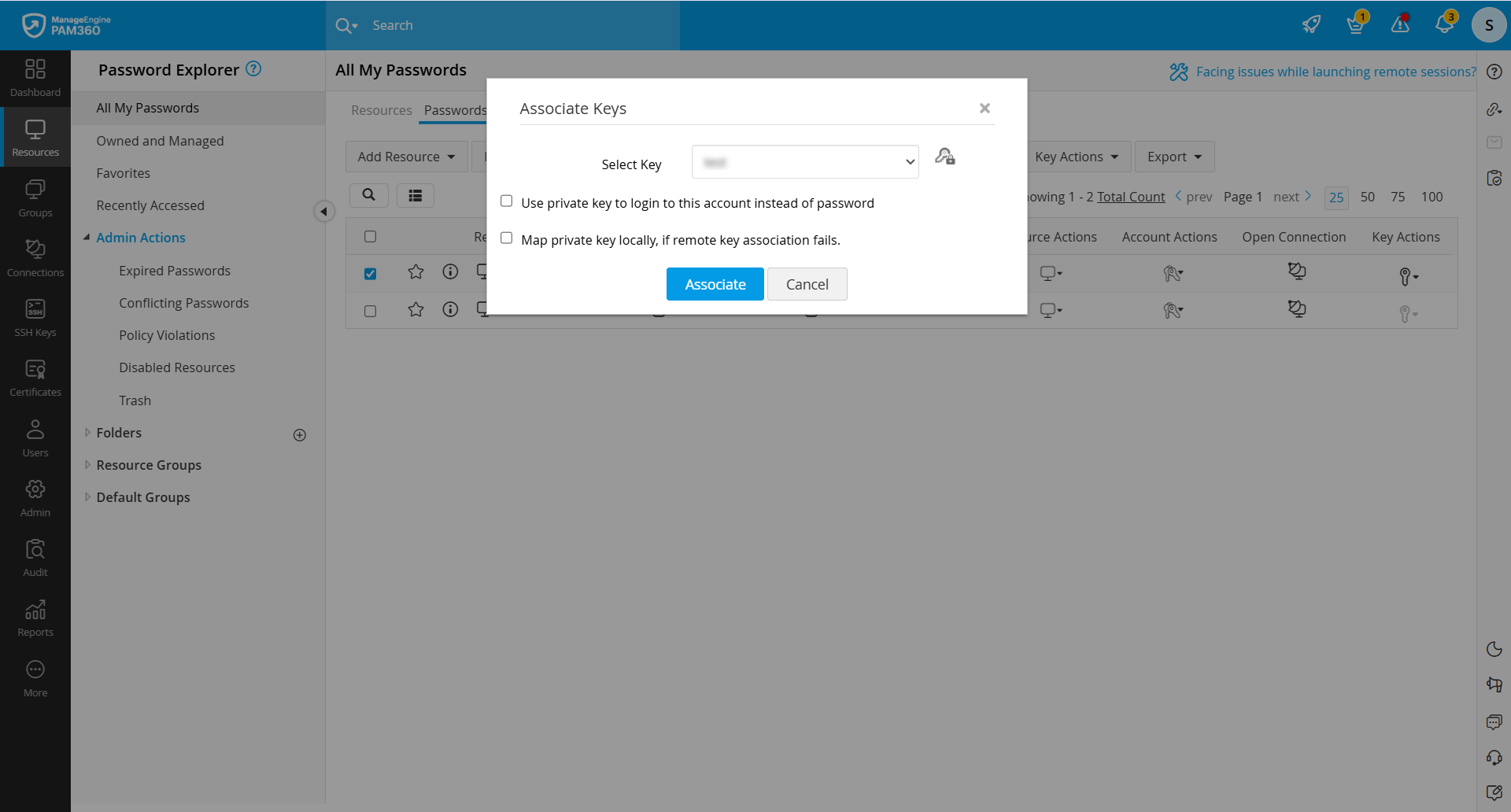
1.1 Associating SSH Keys with User Accounts
- Navigate to Resources >> All My Passwords >> Passwords and select the user accounts for the association.
- Click the Associate button under the Key Actions from the top pane.
- Enable the following permission as required with respect to the SSH key:
- Use private key to login to this account instead of password
- Map private key locally, if remote key association fails
- Select a key and click the Associate button.
1.2 Associating SSH Keys with Resources
- Navigate to SSH Keys >> SSH Keys, select an SSH key from the list displayed and click the Associate button.
- In the Public Key Association window, select the user accounts and select the checkbox to Elevate to "root" user.
Caution
For security reasons, root user login might be disabled for servers/machines. Enabling this option elevates a user login from a non-root user to a root user and allows you to associate keys with all other users on the server. Users have to provide root user and any non-root user credentials to PAM360 to elevate to a root user.
- Click the Associate button.

Now you have successfully associated a particular SSH key to the resources/user accounts.
2. SSH Key Management Operations
2.1 Rotate SSH Keys
You can configure PAM360 to rotate the SSH keys at periodic intervals automatically. With a single click, all the deployed keys can be replaced. The keys can be rotated based on a schedule or anytime based on your need.
To schedule the rotation of keys, follow the below steps:
- Navigate to SSH Keys >> SSH Keys and select the keys to be rotated.
- Click the Rotate option. In the pop-up that opens, enable the requirements that follow and click Rotate:
- Push private key file to remote user account
- Push public key file to remote user account
- Use keyname as filename
A confirmation message will be displayed, and you will be redirected to the Key Rotation Audit page, where the status of rotation is updated.
Caution
Only the keys which have already been associated with user accounts of resources can be rotated.
To schedule the rotation of keys, follow the below steps:
- Navigate to Admin >> PKI Management >> Schedules and click the Add Schedule button.
- In the Add Schedule window, enter a name for the schedule and select the type of schedule as Key Rotation from the drop-down list.
- Select the keys to be rotated and enable the requirements that follow:
- Push private key file to remote user account
- Push public key file to remote user account
- Select the Recurrence Type, Start Time, and Start Date for rotation. Enter the email addresses of the users with the Subject, Content, and Signature to be notified.
- Click Save.
The result of the scheduled execution will get updated in the Key Audit, and the results of the rotation of the keys will get updated in the Key Rotation Audit.
2.2 Dissociate SSH Keys from SSH Users
When an SSH user leaves the organization or is provided temporary privileged access, you can dissociate the keys associated with the user account and discontinue access. Until you dissociate all the SSH keys, you cannot delete the user account or the resource.
To dissociate key from the user accounts, follow the below steps:
- Navigate to SSH Keys >> SSH Keys and select a single key that has to be dissociated.
- Click Dissociate from the More drop-down list.
- If the key is associated with a single user account, select this checkbox to Dissociate key locally if remote dissociation fails, and click OK in the confirmation dialog box to dissociate the key.
- If the key is associated with multiple user accounts, select the user accounts from which the key has to be dissociated, select this checkbox to Dissociate key locally if remote dissociation fails, and click Dissociate in the Dissociate Users window.
To dissociate key from a selected user account, follow the below steps:
- Navigate to Resources >> All My Password >> Passwords.
- Select a user account for which you wish to dissociate keys and click Dissociate Keys from the Key Actions column.
- If the user account is associated with a single key, select OK in the pop-up window.
- If more than one key is associated with the selected user, select the keys which have to be dissociated and click the Dissociate button in the Dissociate Keys window.
Additional Details
When you select and delete the user accounts enumerated in PAM360, the SSH keys associated with them are automatically dissociated.
2.3 Push SSH Keys to Remote User Accounts
In addition to deployment, PAM360 allows you to push a private key or a public key, or both onto its associated user accounts.
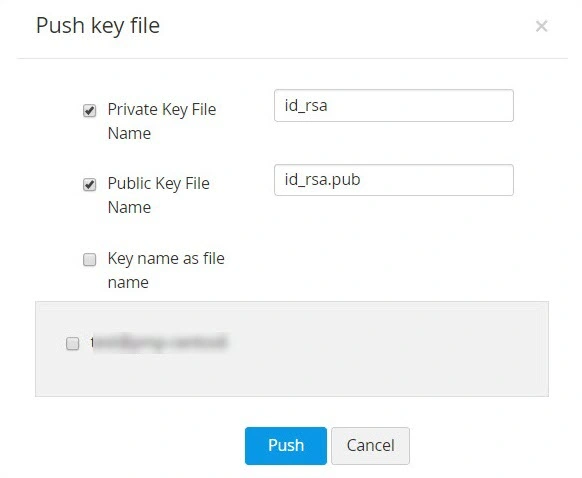
i. To push a key file to remote user accounts:
- Navigate to SSH Keys >> SSH Keys and click on the Push Key to User icon beside the selected key.
- Select the keys that needs to be pushed (private, public, or both), provide the appropriate key names, select the required associated users, and click Push. The key files are now pushed to the selected users.
This feature is also available as a part of the Key Rotation schedule. After the scheduled key rotation is performed and fresh key pairs are created and deployed, you can automatically push either the private key or both the private and public keys onto its selected associated users by enabling the 'push key to user' option instead of pushing the key files manually after every scheduled rotation.
ii. Add commands and restrict host per key:
You can add commands to specific user accounts, thereby providing an additional layer of restriction enabling them only to execute the commands on establishing a connection with the host. Also, you can predefine the appropriate key-to-user relationship by specifying the IP address of the user in the appropriate format (as specified below).
To add a command to a public key,
- Navigate to Resources >> All My Passwords >> Passwords.
- Select the user account for which you want to add a command and click on Add Command from the Key Actions column.
- An Add Command dialog box opens up, where you can add commands to be executed in the following format. i.e.,(command="usr/local/bin/script.sh").
To restrict hosts for a key, click on Add Command and provide the name or IP address of the hosts in the following format. i.e.,(from="host1/ip1,host2/ip2")
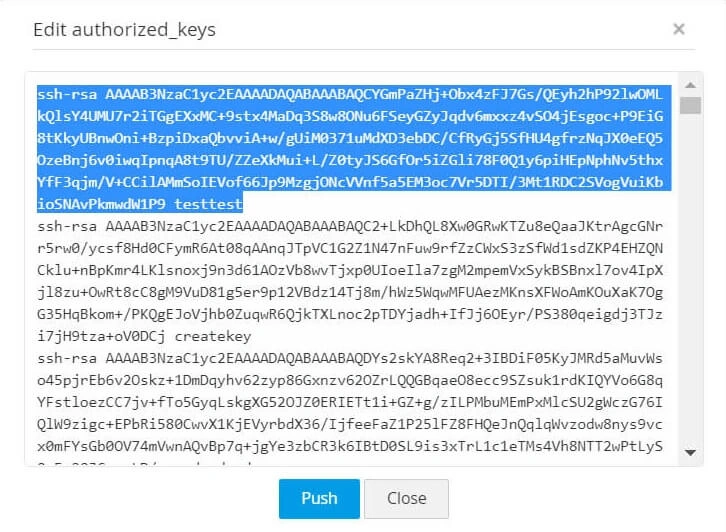
2.4 Edit Authorized Keys File
You can fetch authorized key files from various user accounts, edit the key content and push them to respective user accounts from PAM360. To do this,
- Navigate to Resources >> All My Passwords >> Passwords.
- Select the required user account and click on Edit Authorized Keys from the Key Actions column.
- A window opens displaying the list of public keys in the authorized keys file of the respective user. The keys that are managed using PAM360 are highlighted.
- You can now edit the contents of the keys displayed and deploy them back to the respective user accounts by clicking the Push button.
2.5 Delete SSH Keys
When you try to delete the SSH keys from the PAM360 repository, they are first dissociated automatically from their user accounts. Key deletion fails for the SSH keys that are not dissociated from all their user accounts. To delete the SSH Keys:
- Navigate to the SSH Keys >> SSH Keys tab and select the keys to be deleted.
- Click the Delete button from the More drop-down list and click OK in the confirmation window.
3. SSH Key Groups for Management
PAM360 gives the provision to create key groups for easy organization and to carry out operations in bulk. You can assign, delete, or modify the group similar to working with a single SSH key. The list of items available in a group is enumerated in their respective tabs. You can drill down to the individual items by clicking the name of a group.
3.1 Create Key Groups
To create a group of SSH keys, follow these steps:
- Navigate to SSH keys >> Keys Group and click the AddGroup button. You will be redirected to the Add Key Group window.
- Enter the name of the group. Take care while choosing the name since it cannot be edited later.
- You can choose the resources to be added to a group in 2 ways:
- By Specific key — Select the keys to be added to the group individually.
- By Criteria — This serves as a dynamic key grouping. You will specify the exact criteria based on which you want to create the group. Here, you have many options to choose from - you can search for specific keys based on their name, type, length, or creator and filter the search in a fine-grained manner based on the criteria such as "contains", "does not contain", "equals" "not equal", "starts with" and "ends with". Click the Matching Keys button at the bottom-right corner of the window to see the corresponding keys.
Additional Details
If you select the By Criteria option, the conditions specified are applicable to keys that are discovered later too. If any of those keys match the criteria, they will be automatically included in the new group.
- Click Save to create the key group.
In addition, you can directly select individual keys from the SSH Keys >> SSH Keys tab and click the Save button for faster group creation.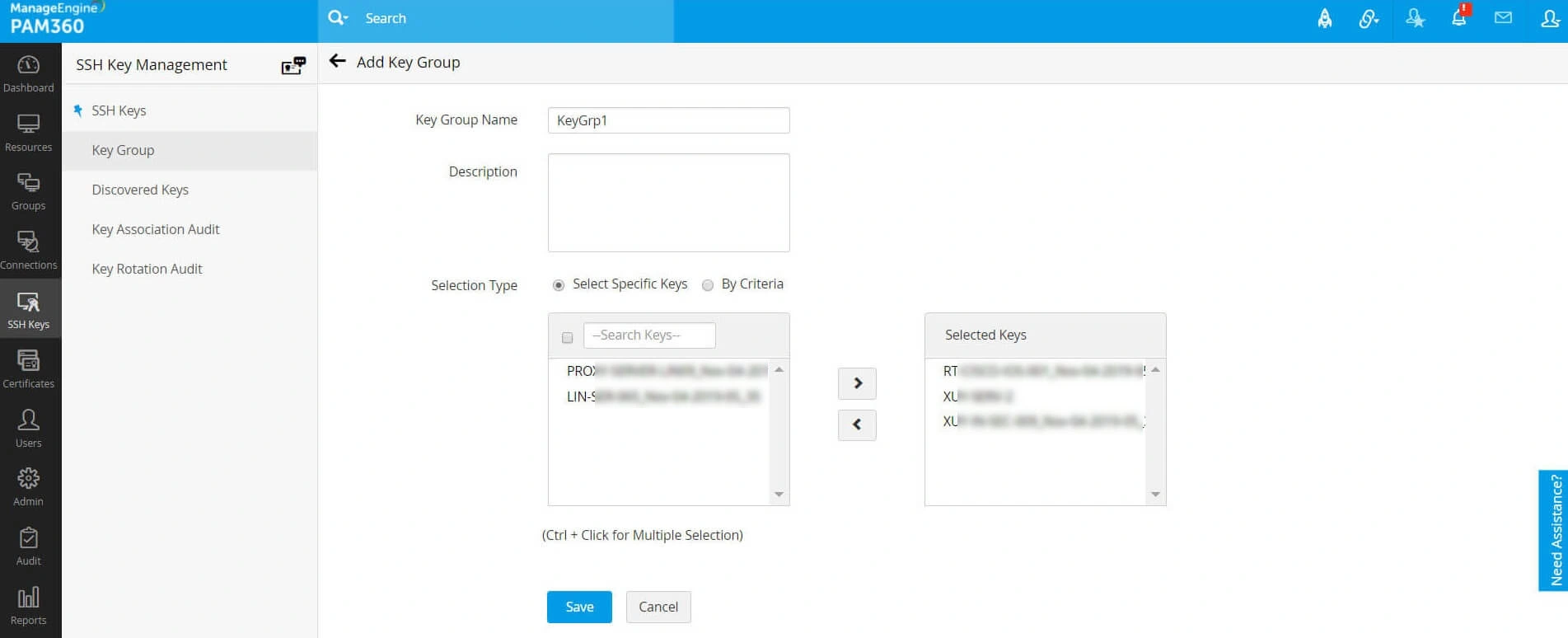
3.2 Edit Key Groups
To make changes to an existing key group, follow these steps:
- Navigate to SSH Keys >> Keys Group and click the Edit icon present in the right corner of the table view.
- You can change the key selection type and edit the keys available in a group or add, modify, or delete the filters applied to a group.
Once you make changes to the group and save, a message will be displayed confirming the update of the changes.
Caution
The name of the group cannot be modified. However, you can add or modify the description and the list of keys available in it.
3.3 Rotate Keys in a Key Group
To rotate all the keys of a key group, navigate to SSH Keys >> Keys Group, select the key groups and click the Rotate button. You will be now redirected to the Key Rotation Audit window, where the status of key rotation is updated.
3.4 Delete Key Groups
To delete a key group, navigate to SSH Keys >> Keys Group, select the key groups and click the Delete button. A pop-up window will appear to make sure that the selected groups are to be deleted. Click OK to delete the groups.
4. Miscellaneous Operations
4.1 Customize User Home Directory
You can customize the home directories of the users, i.e., the location where the public key is to be deployed. To do this:
- Navigate to Resources >> All My Passwords >> Passwords.
- Click the Edit User Path from the Key Actions column dropdown.
- Enter the modified path and click Save.
4.2 Export SSH Keys
To export key files by selecting them from the resources with which they are associated:
- Navigate to the Resources >> All My Passwords >> Passwords tab in the GUI.
- Click the name of the resource in which the key is deployed and click the Export button.
To export the key files, navigate to the SSH Keys >> SSH Keys tab and click the Export Keys icon available in the right corner of the table view corresponding to the required key.
Additional Details
Even while exporting, the passphrases used to protect the keys are still in effect. That is, if the keys are to be used elsewhere, the passphrases have to be provided.
4.3 View SSH Key History
Using PAM360, you can view the history of each SSH key, from the moment it was created or imported, and the subsequent rotations along with time stamps. To view the history of any key, navigate to the SSH Keys >> SSH Keys tab, select a single key and click the Key History button.
4.4 Export Discovered Keys Report
A report of the discovered keys can be exported as PDF or to an email id. To export the report:
- Navigate to SSH Keys >> Discovered Keys and select a single key.
- Click the Export button. You can export the report to the system as a PDF file or to desired email addresses.
- PDF : Export and save the report of the discovered keys as a PDF in the system.
- Email : Specify the email addresses to which the report of the discovered SSH keys is to be exported.