Direct Inward Dialing: +1 408 916 9892
Written by Mahidhar Adarsh, IT security team, ManageEngine Updated on September 2025
Start your free trialAlthough it is good to mandate that your employees change their passwords regularly, this activity must be supervised. Unmonitored password changes or resets by a rogue insider could lead to a serious security breach. Administrators need to keep an eye on password changes and resets to ensure they're authorized and to keep their Active Directory (AD) environment secure. In this documentation, you'll learn about how to audit password change activities in AD.
Perform the following actions on the domain controller (DC):
Once the above steps are complete, events will be stored in the event log. This can be viewed in the Event Viewer by following the steps below:
Auditing the password changes through the above manual method becomes tedious, as every organization deals with hundreds to thousands of user accounts.
ADAudit Plus, a comprehensive AD auditing tool, enables admins to effortlessly audit password changes and other Active Directory changes.
View recent password changes and scrutinize the activities of users who frequently change their passwords.
A high number of failed password changes could indicate a brute-force attack
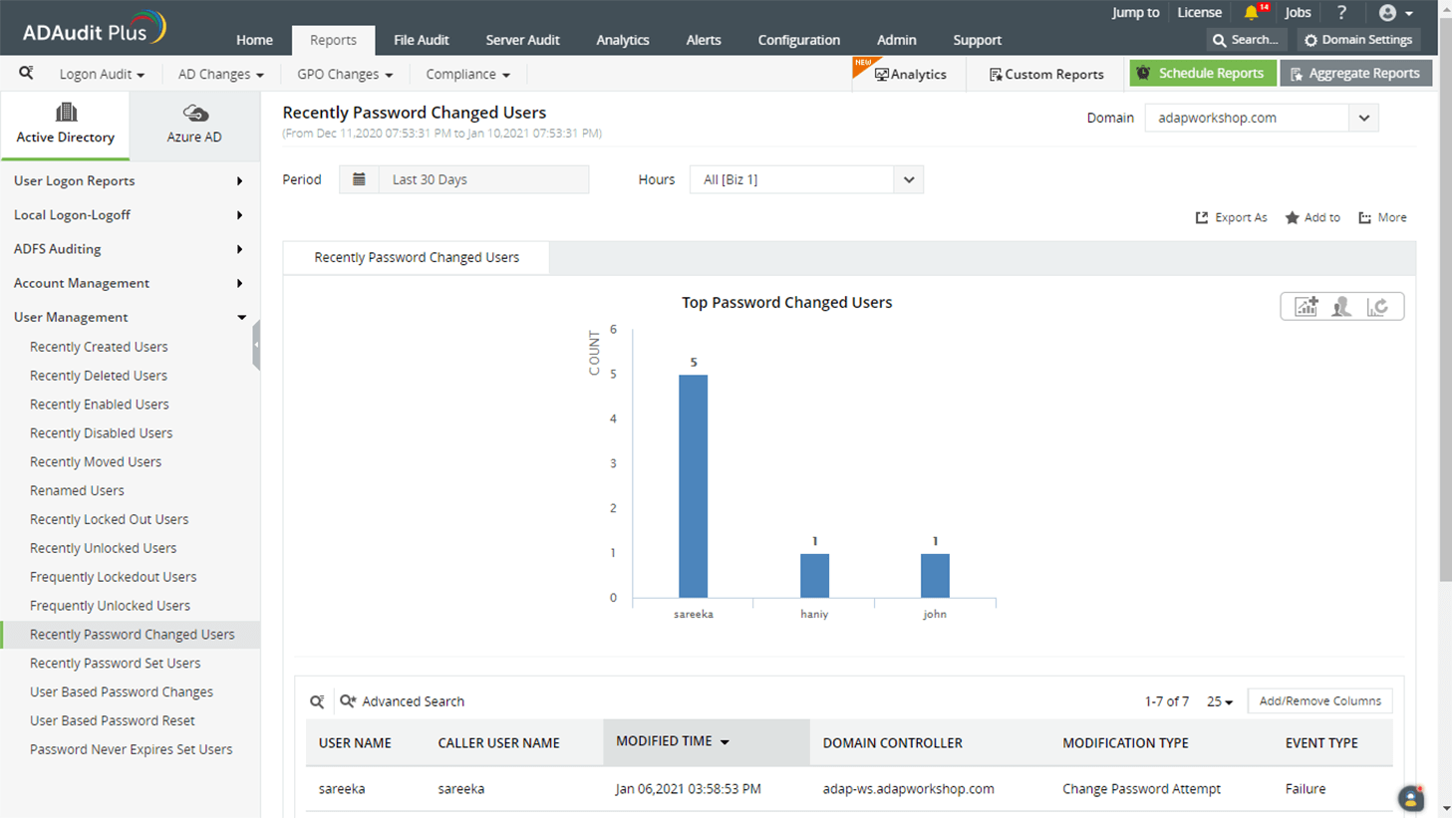
View recent password changes and scrutinize the activities of users who frequently change their passwords.
A high number of failed password changes could indicate a brute-force attack
To view reports for password changes categorized by users, navigate to Reports → User Management → User Based Password Changes.
Analyze both successful and failed attempts to change passwords
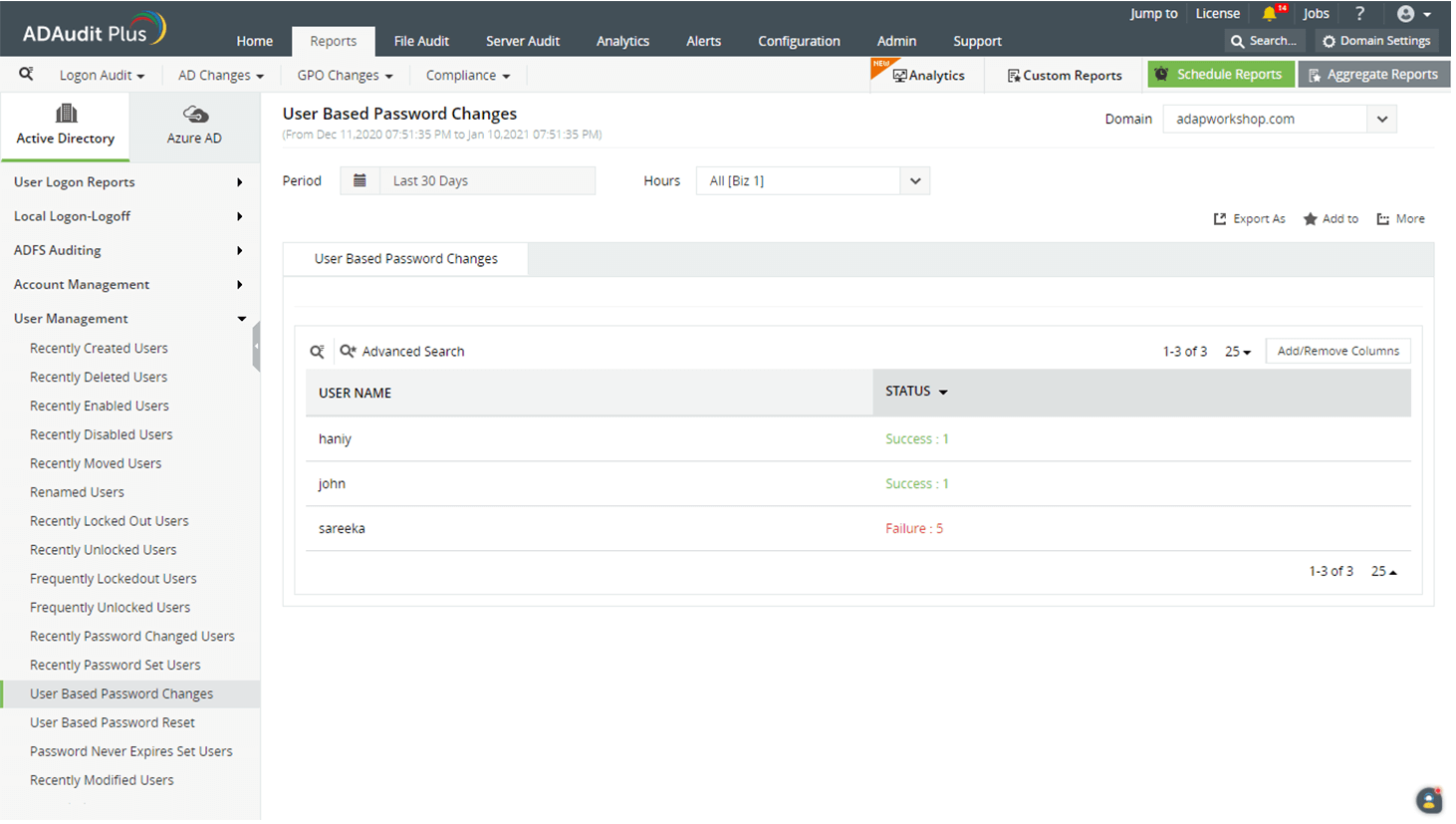
Analyze both successful and failed attempts to change passwords
See recent password changes and find which users most frequently reset passwords.
View who changed the password, for whom, and if the action was successful or not.
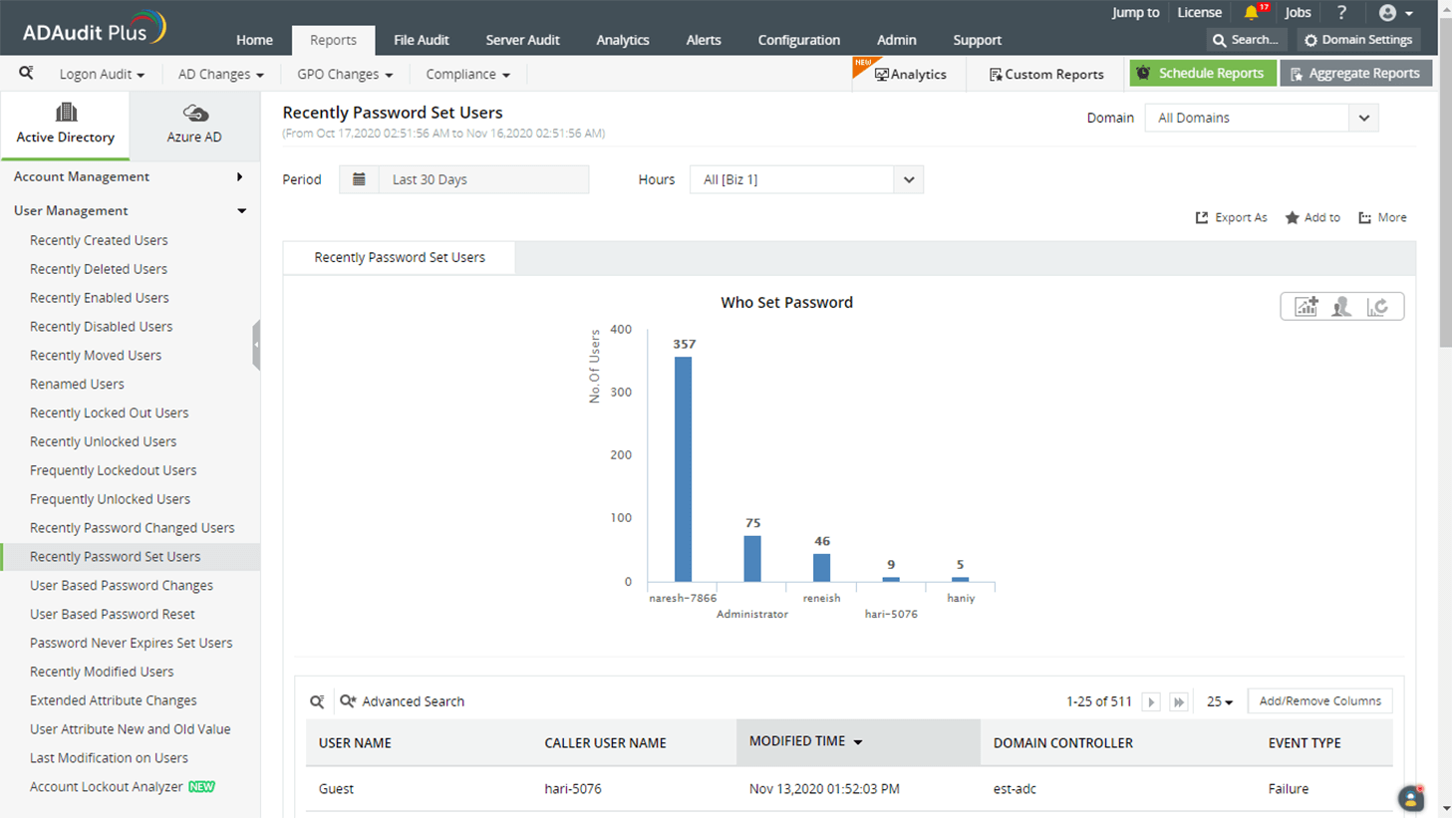
See recent password changes and find which users most frequently reset passwords.
View who changed the password, for whom, and if the action was successful or not.
To view reports for password resets categorized by users, navigate to Reports → User Management → User Based Password Reset.
Analyze which user account was most frequently reset in a given time period
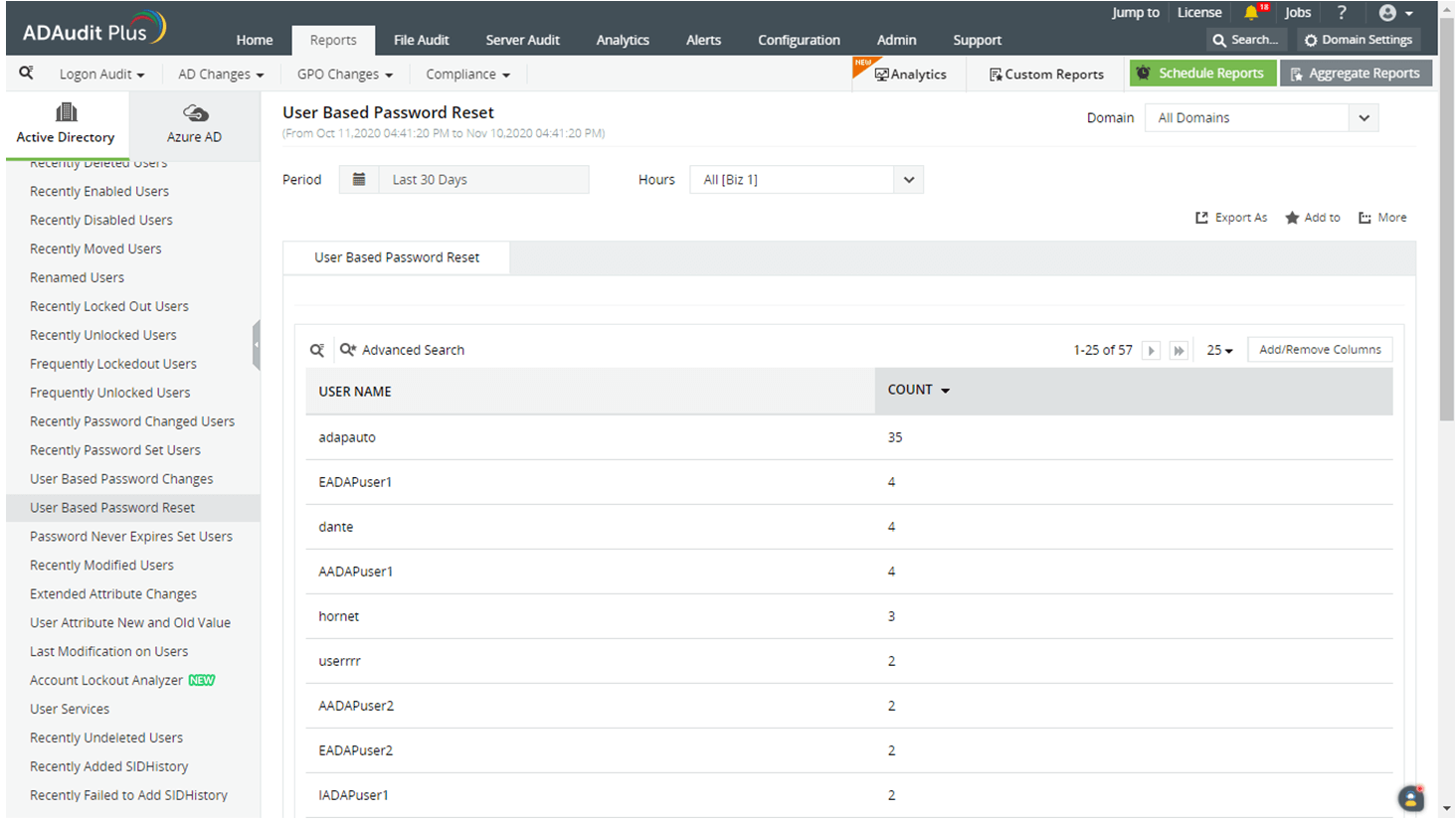
Analyze which user account was most frequently reset in a given time period