

Endpoint Central's Data Loss Prevention provides a robust layer of security by preventing unauthorized access and leakage of sensitive data. This document delves into the specifications of the agent processes and the core mechanisms behind Data Loss Prevention, helping you understand how it safeguards your endpoints and protects critical information from unauthorized exposure.
| Agent Process | Running Device Name | Bandwidth Consumption (Approximately) | CPU Consumption (Approximately) | Memory Consumption (Approximately) |
|---|---|---|---|---|
| Processing EDLP Policy | Medlp.exe | N.A. | <0.5% | 20-22 MB |
| Classifying Process | UemsProcessMonitor.exe | N.A. | 0.11-0.13% | 23-25 MB |
| Network Packet Monitor | Netfilter.exe | N.A. | <0.1% | 6-8 MB |
| Clipboard Monitor | HostExe | N.A. | <0.1% | 3-4 MB |
| Monitoring Browser File upload | DLPNativeHost.exe | N.A. | <0.1% | 10-11 MB |
| Component Upgrade | meaaphelper.exe | 14-17 MB | 0-1% | 1 MB |
| Build after 11.4.2504.01 (UemsProcessMonitor.exe is merged with MEDLP.exe) | ||||
| Processing DLP Policy and Process Classification | Medlp.exe (During background scan and process classification) | N.A. | 10-20% | 25-120 MB |
| Processing DLP Policy and Process Classification | Medlp.exe (After background scan completion) | N.A. | <0.5% | 20-25 MB |
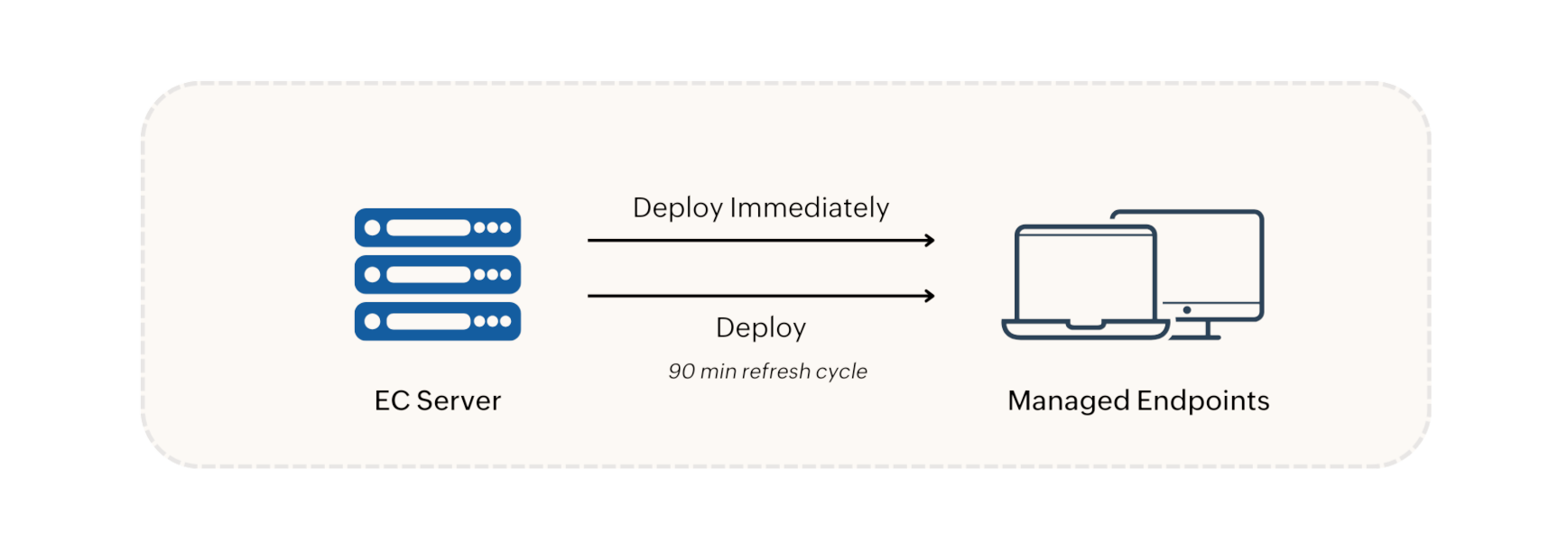
When an Data Loss Prevention policy is created, it is deployed in the following two options:
Policy modifications, deletions, group changes, and unmanaged Device updates are synchronized with agent machines during refresh cycles. In environments with a Distribution Server, policies and configurations are replicated to the Distribution Server and then synchronized with agent machines during the 90-minute refresh cycle.
The Data Loss Prevention policy will be received by the agent and enforced by the kernel mode driver named medlp. This driver monitors device connections and ensures that only authorized devices can be accessed according to the deployed policy. Audited and blocked device events will be posted in the 90-minute refresh cycle.
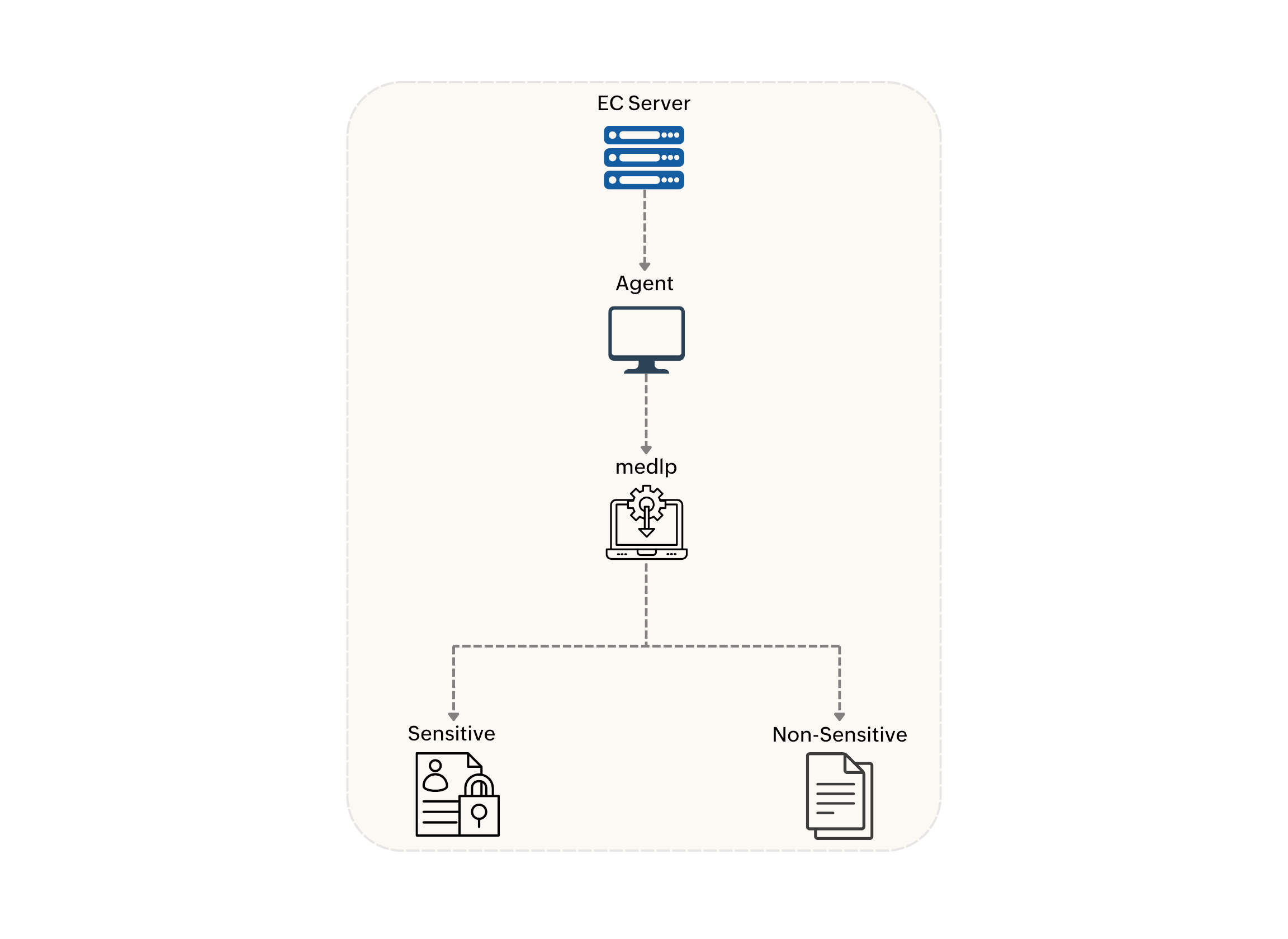
After agent installation, the agent remains dormant until a policy is deployed. Once a policy is in place, the agent scans endpoints for sensitive files based on the defined rules.
Additionally, OCR (Optical Character Recognition) support enables the agent to identify sensitive information even within image-based documents.
To view the complete list of supported file formats, refer List of supported file formats.
When conflicting policies are applied to the same target group, The following is the order of precedence: