- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Monitoring and reporting IDS/IPS logs
Importance of IDS/IPS monitoring
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are among the most sophisticated network security devices in use today. They inspect network packets and block suspicious ones, as well as alert administrators about attack attempts. These systems' logs contain valuable network threat information about attack types, devices being targeted, and more.
With ManageEngine EventLog Analyzer, you can monitor IDS and IPS logs and extract the information they provide to secure your network further. It makes network device monitoring simple by automatically collecting IDS/IPS logs and storing them in a central location. Predefined reports cover various aspects of your network and help you gain perspective on your network's overall security standing. Instant alerts ensure you're the first to know when something suspicious is detected. For instance, malicious traffic alerts let you know when intruders try to access your network.
EventLog Analyzer also allows you to search the collected logs using several powerful search options and securely stores logs for as long as you need them.
Supported IDS/IPS vendors
EventLog Analyzer provides out-of-the-box support for multiple IDS/IPS vendors:
Network security monitoring with EventLog Analyzer's IDS/IPS reports
EventLog Analyzer generates IDS/IPS security reports that provide information on:
The most targeted devices on your network.
Attacks occurring on your network, with information on the most frequent attacks and the source of these attacks.
Attack trends.
These reports help you understand what types of attacks your network is susceptible to, which network devices need to be secured further, how to decide which malicious traffic sources to target, and more.
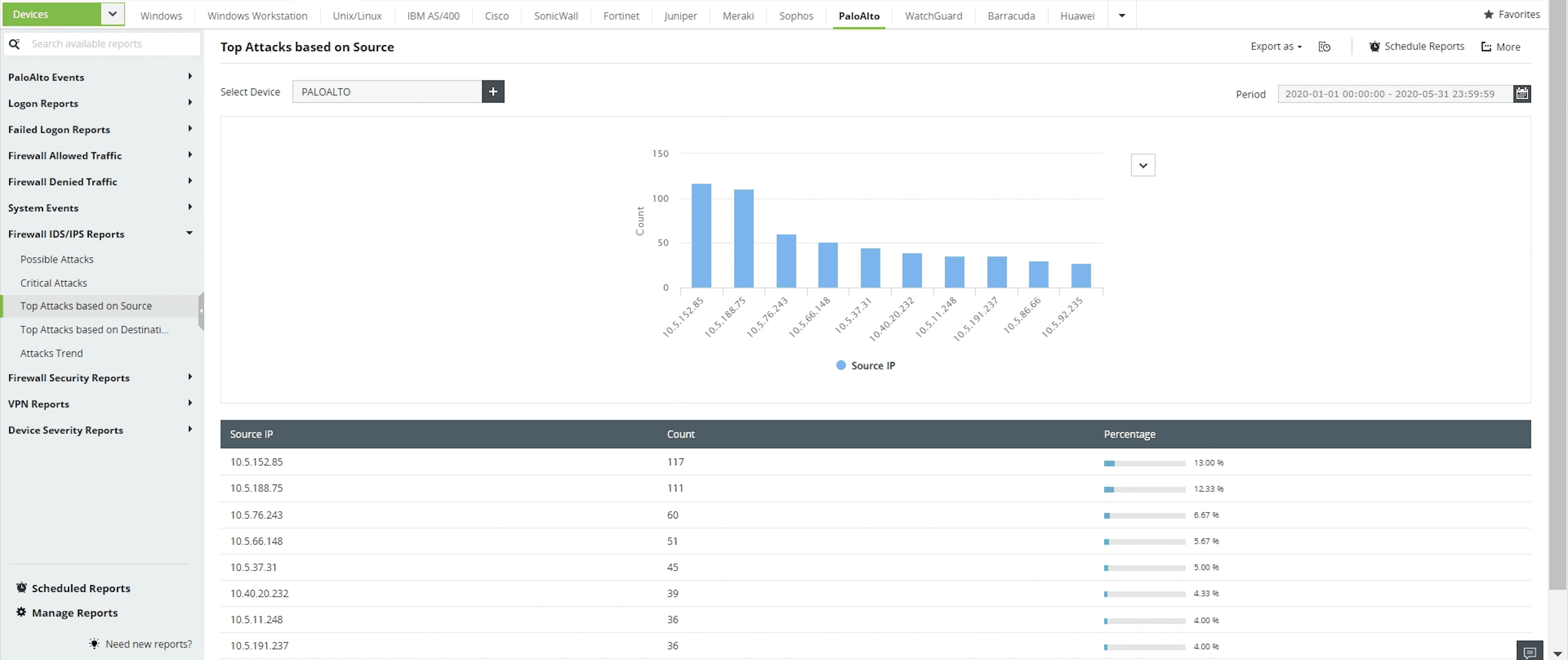
Attacks classified based on source/destination addresses
Prevent network intrusions by analyzing attacks occurring on your network classified on the basis of source and destination addresses.
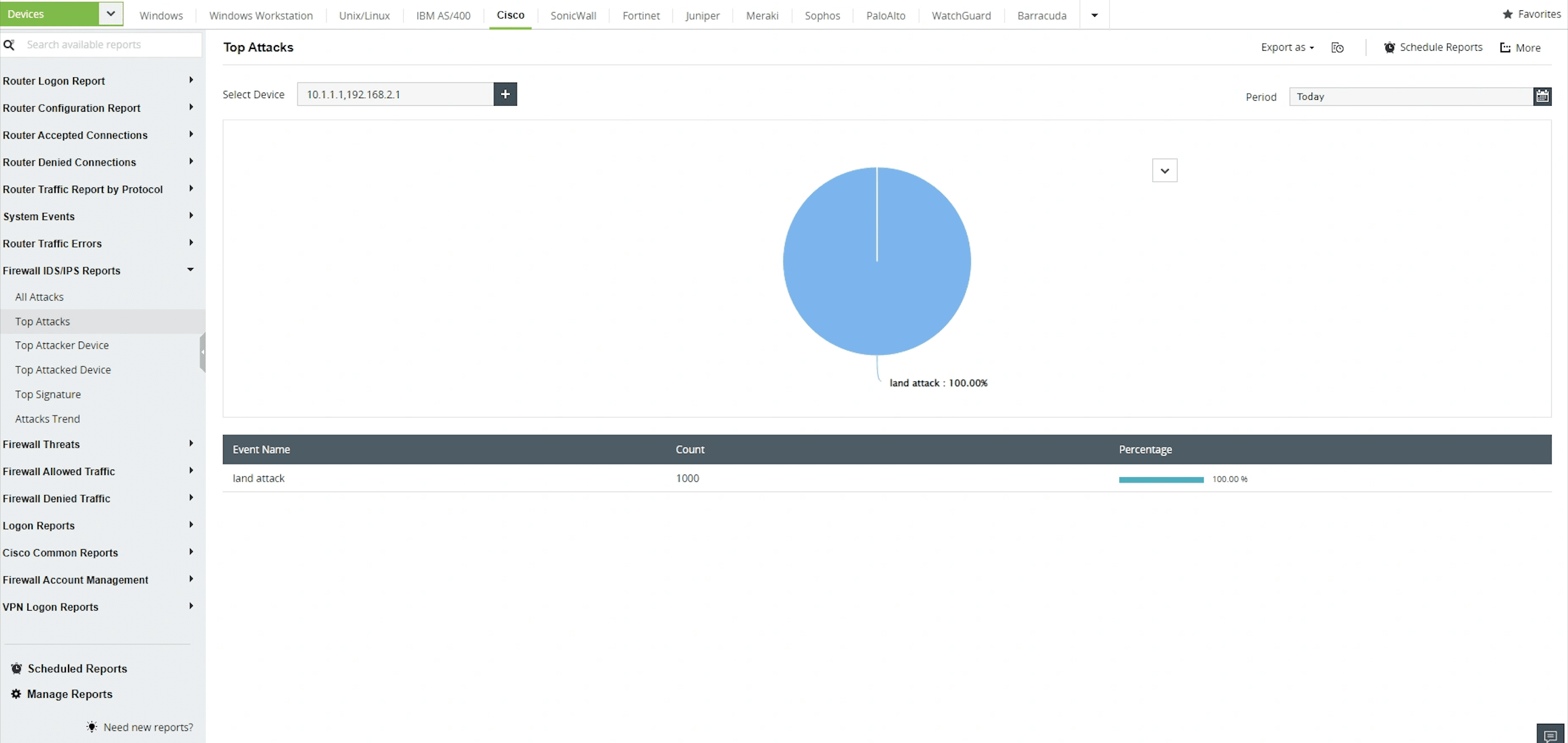
Frequently targeted devices on your network
Monitor and protect devices on your network that were targeted by attackers on a regular basis.
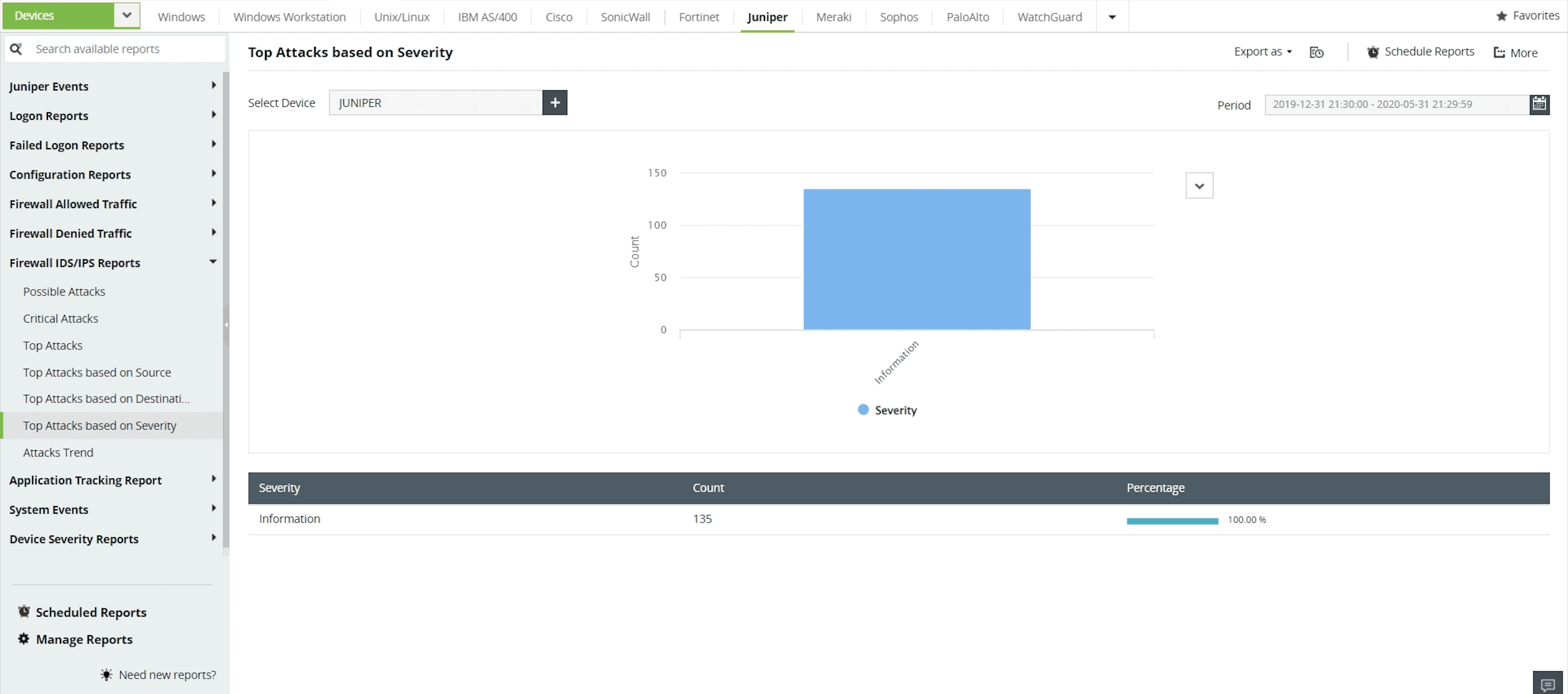
Attacks classified on the basis of severity
Analyze attacks in your IDS/IPS devices by categorizing them on the basis of their status: Emergency, Alert, Critical, Error, Warning, Notice, Information, or Debug.
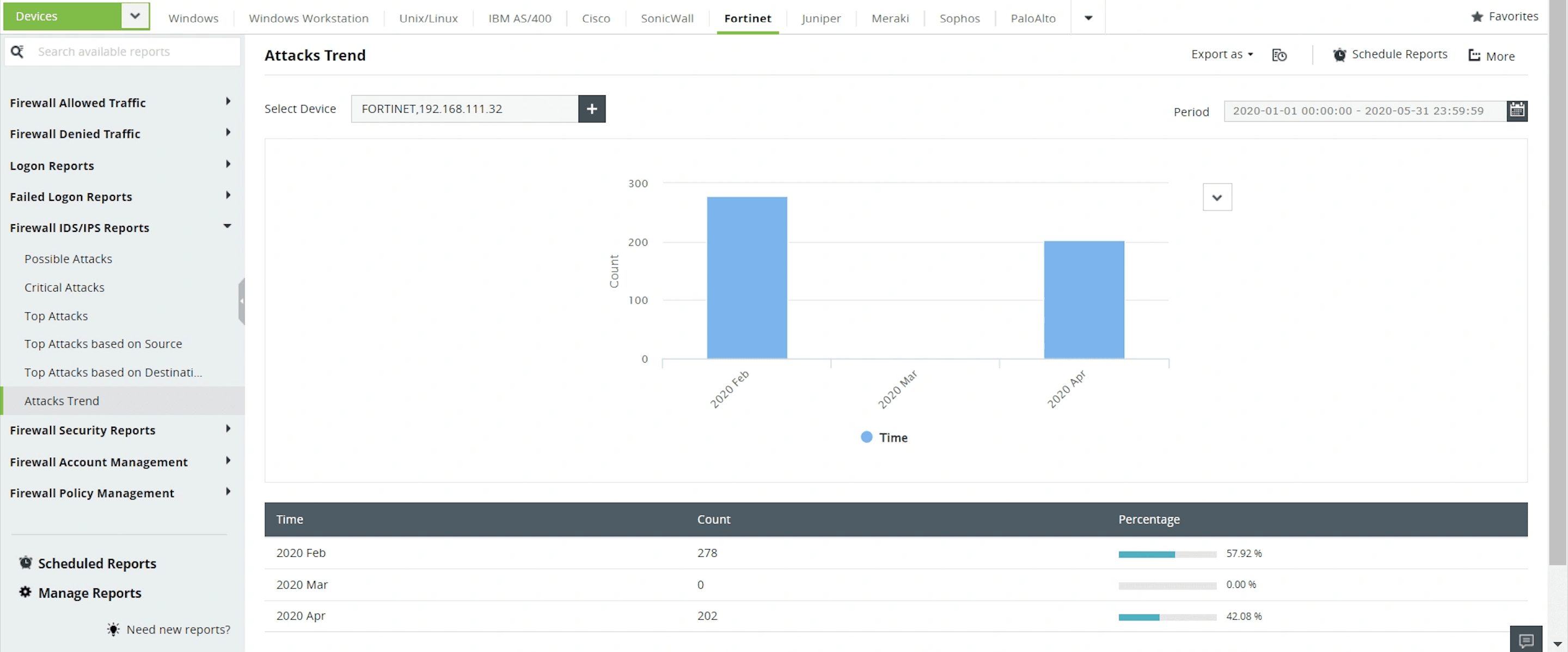
Attack trends
The Attacks Trend report gives you a timeline of various attacks that occurred over a given period of time.
More features offered by EventLog Analyzer
Monitoring routers and switches
Track and analyze traffic, connection requests, configuration changes, logons, and links states on your routers and switches using pre-defined reports and alerts.
Firewall log analysis
Analyze firewall traffic, security threats, policy changes, logons and more for firewall solutions from top vendors including Cisco, Checkpoint, Fortinet, Watchguard, and Sonicwall.
Cyber forensic analysis
Search through raw and formatted logs with EventLog Analyzer's powerful log search engine, then perform a root cause analysis to identify the cause of a security attack.
IT compliance auditing
Comply with various regulations such as ISO 27001, HIPAA, FISMA, PCI DSS, GLBA, and more with pre-defined compliance reports and compliance violation alerts.
Log visualization
Visualize log data collected from multiple sources and gain valuable insights into important network security events using EventLog Analyzer's intuitive dashboards and graphical reports.
5 reasons to choose EventLog Analyzer for network monitoring
1. Comprehensive log management
Gain actionable insights into your network activities by collecting, parsing, and analyzing logs from heterogeneous devices in your organization network.
2. In-depth auditing and reporting
View important security information obtained from your logs in the form of graphical reports. EventLog Analyzer comes with 1,000+ pre-defined reports that are generated automatically upon log collection.
3. A powerful correlation engine
Identify suspicious activity in your organization network by correlating logs from multiple devices. Utilize 30+ pre-defined correlation rules or create rules as per your requirements using EventLog Analyzer's correlation rule builder.
4. Automated incident management
Limit the time taken to detect and respond to security incidents with EventLog Analyzer's incident detection and response system. Handle security incidents quickly by automatically assigning tickets to appropriate security administrators.
5. Augmented threat intelligence
Integrate with commercial and open source threat feeds to detect malicious sources interacting with your organization network.
Frequently asked questions
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are network components that monitor traffic in your organization network to detect and prevent malicious activities and policy violations.
Intrusion detection systems (IDS) are considered to be monitoring systems. They are responsible for monitoring and analyzing the network traffic for malicious threats. When any suspicious activity is detected, they trigger an alert to notify the security team so that the threat can be mitigated immediately. Intrusion detection systems can be deployed in two different ways: host-based intrusion detection systems and network-based intrusion detection systems.
Intrusion prevention systems (IPS) are proactive in nature and are often referred to as control systems. They monitor network traffic and when any abnormal activity is detected, they alert the security administrators and remediate the threat through automated actions such as blocking that particular malicious source or modifying the firewall to stop similar attacks in the future.
Hackers are constantly preying on your organization's network to exploit the vulnerabilities in your web server. Because web servers acts as a threshold to the Internet, they are prone to web server vulnerabilities like a DDOS attack, SQL injection, XSS (cross-site scripting), and more. To secure your web server from intruders, periodically monitor the server's health to spot issues in the web server's disk capacity, CPU load, memory usage, latency, failure, and accuracy.











