How to view and access Windows Defender logs
Last updated on:In this page
What are Windows Defender logs?
Windows Defender logs are records generated by Windows Defender, the built-in antivirus and security solution in Windows operating systems. These logs capture critical information regarding the detection of threats, the actions taken by the antivirus solution, and the overall security posture of the system. The primary role of these logs is to facilitate security monitoring by providing insights into potential threats, enabling administrators to respond effectively to security incidents.
How to find and access Windows Defender logs
To find and access Windows Defender logs, follow these steps:
Method 1: Using Event Viewer
This is the most common way to view Windows Defender logs. Here's how:
- Press Windows + R, type eventvwr.msc, and press Enter to open Event Viewer.
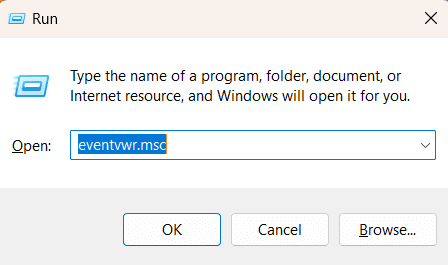
- In the left pane, navigate to Applications and Services Logs > Microsoft > Windows > Windows Defender.
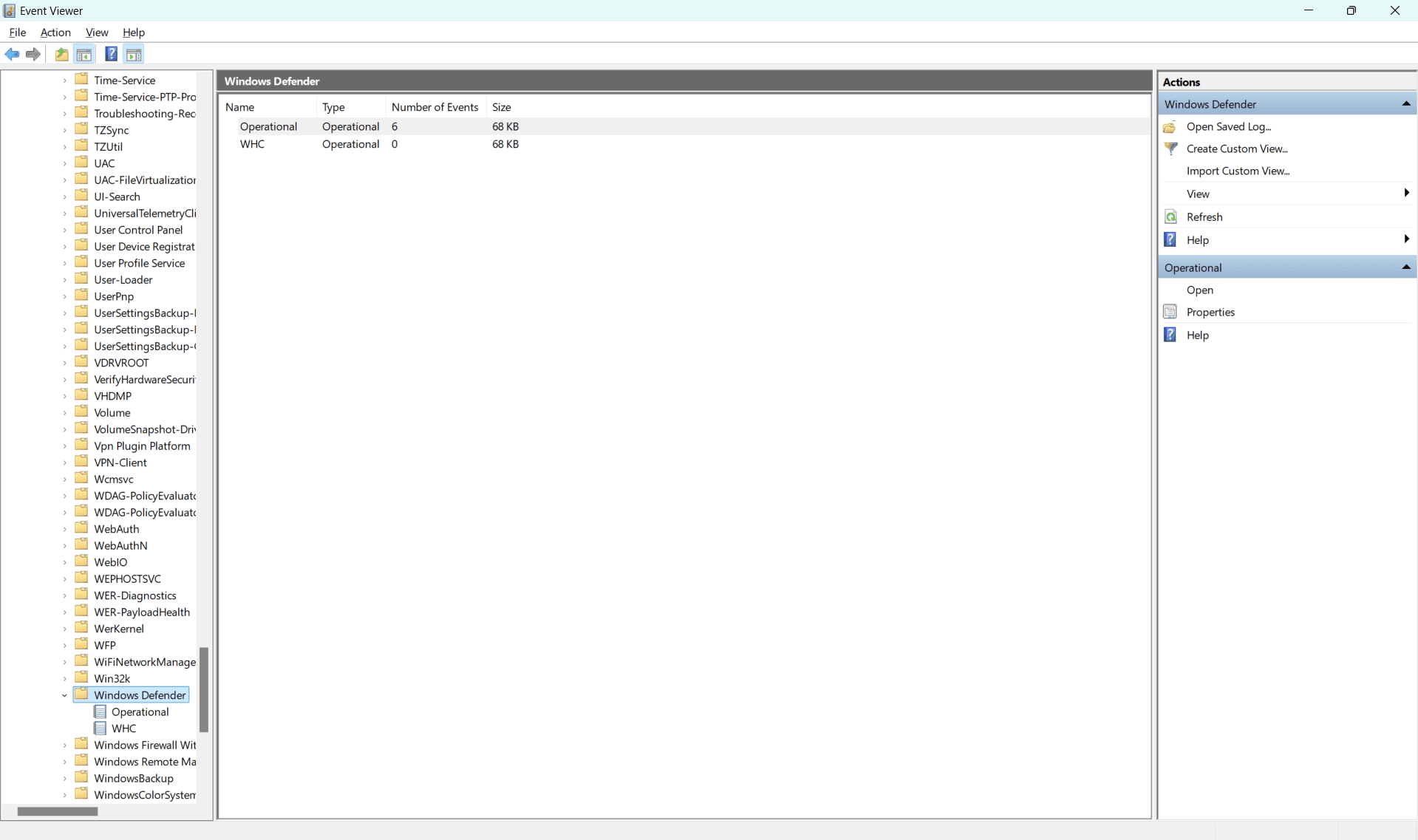
You’ll see two main log categories:
- Operational: This category logs the activities of Windows Defender, such as malware detections and scans.
- Audit: This category is used for logging audit events related to Windows Defender.
Method 2: Using PowerShell
You can also use PowerShell to access specific Windows Defender logs.
- Here's a simple command to get the logs related to Windows Defender:
Get-WinEvent -LogName "Microsoft-Windows-Windows Defender/Operational"
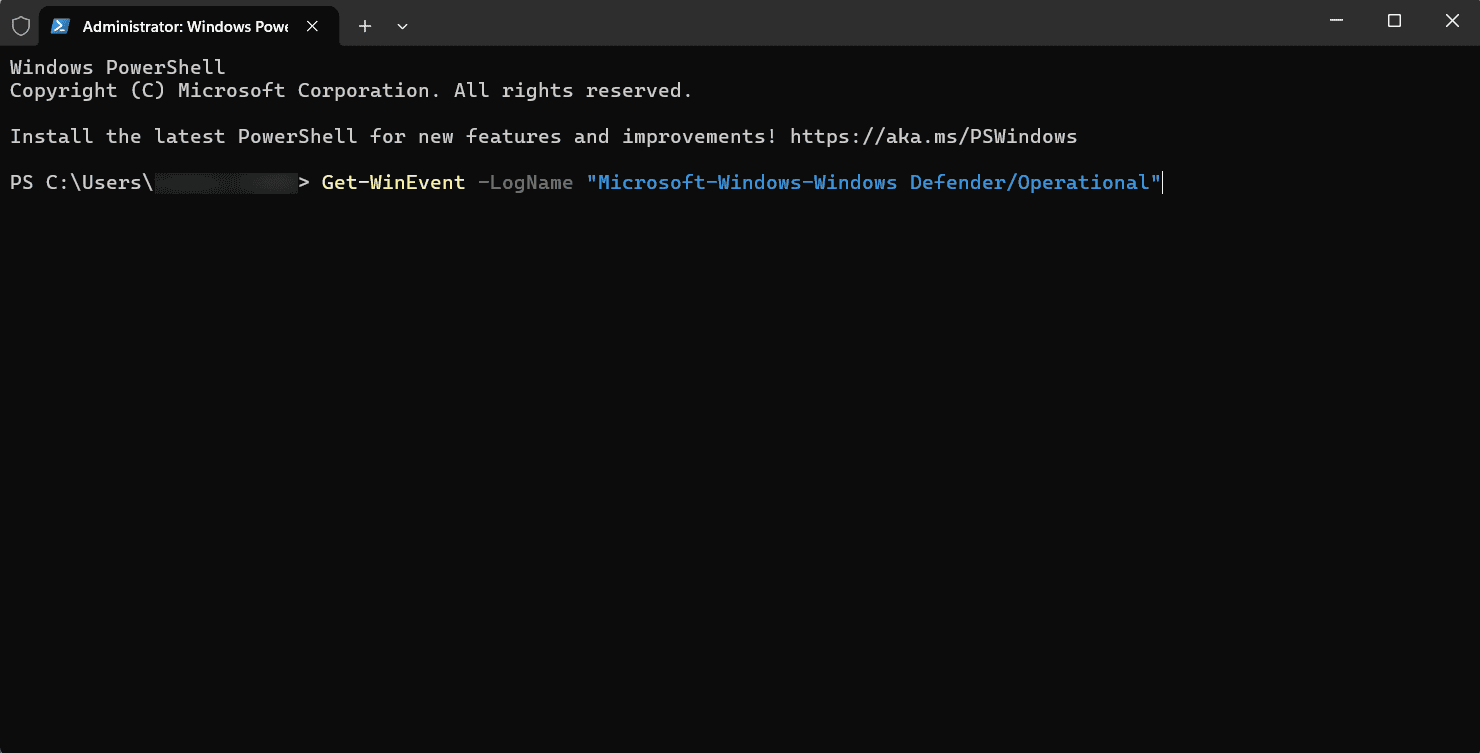
This command retrieves all operational logs from Windows Defender. You can filter results by specifying the time frame or particular event IDs if you need more specific logs.
Method 3: Windows Defender Security Center
For a more straightforward view of current logs, open Windows Security (formerly called Windows Defender Security Center):
- Go to Start > Settings > Privacy & Security > Windows Security.
- Click Virus & threat protection.
- Scroll down to Protection history. This will display a list of recent actions taken by Windows Defender, including blocked threats and completed scans.
Method 4: Log file location
Windows Defender also stores log files in a dedicated directory. The logs are stored in:
- C:\ProgramData\Microsoft\Windows Defender\Support\
These are text-based logs that you can open with Notepad or any text editor to analyze historical Defender events.
Method 5: Using ManageEngine EventLog Analyzer
If you're using ManageEngine EventLog Analyzer, you can integrate Windows Defender logs for centralized monitoring. The software will automatically generate reports and alerts based on Defender activity, helping you stay on top of security-related issues.
Key reports in EventLog Analyzer:
- Antivirus logs: You can generate antivirus logs specifically related to Windows Defender activities, such as threat detections, quarantine actions, and scans.
- Security alerts: Set up real-time alerts for any malware detection or suspicious behavior reported by Windows Defender.
This process ensures a comprehensive view of your Windows Defender logs for both manual checks and automated monitoring.
How to analyze Windows Defender log entries
Windows Defender logs contain various entries that provide insights into security events:
- Detected threats: Entries that indicate malware or potentially unwanted programs detected by Windows Defender. For example:
- Detected: Ransom:Win32/Conti.ZA
- Action Taken: Quarantined
- Scan results: Information about completed scans, including the number of files scanned and any threats found.
- Actions taken: Details on what actions were taken in response to detected threats, such as "Removed," "Quarantined," or "Ignored."
- Event timestamps: Each entry includes the date and time of the event, which is crucial for tracking the timeline of security incidents.
By analyzing these entries, administrators can identify patterns of malicious activity and take appropriate action to mitigate risks.
How to leverage Windows Defender logs for enhanced security
Windows Defender logs can be leveraged to maintain and enhance system security in several ways:
- Threat detection: Regularly reviewing logs helps identify and respond to threats quickly, reducing the potential impact of malware infections.
- Incident response: In the event of a security breach, logs provide forensic evidence that can help trace the attack's origin and understand its impact.
- Policy enforcement: Logs can reveal whether security policies are being followed, such as whether appropriate actions are taken against detected threats.
- Trend analysis: By analyzing logs over time, organizations can identify trends in malware attacks, helping to adjust security measures accordingly.
- Compliance and reporting: Maintaining logs is essential for compliance with security standards and regulations and providing documentation of security practices.
How ManageEngine EventLog Analyzer monitors Windows Defender logs
Windows Defender logs are your front-line defense against cyberthreats, providing critical insights into malware detection, threat analysis, and system protection activities. With ManageEngine EventLog Analyzer, a log management and IT compliance tool, you can elevate your security posture by harnessing the power of these logs.
Reports for monitoring Defender logs
EventLog Analyzer provides detailed reports that enhance the visibility of Windows Defender activities, such as:
- Windows threat detection
- Defender malware detection: Analyze logs for malware detected by Windows Defender, including threats blocked or quarantined.
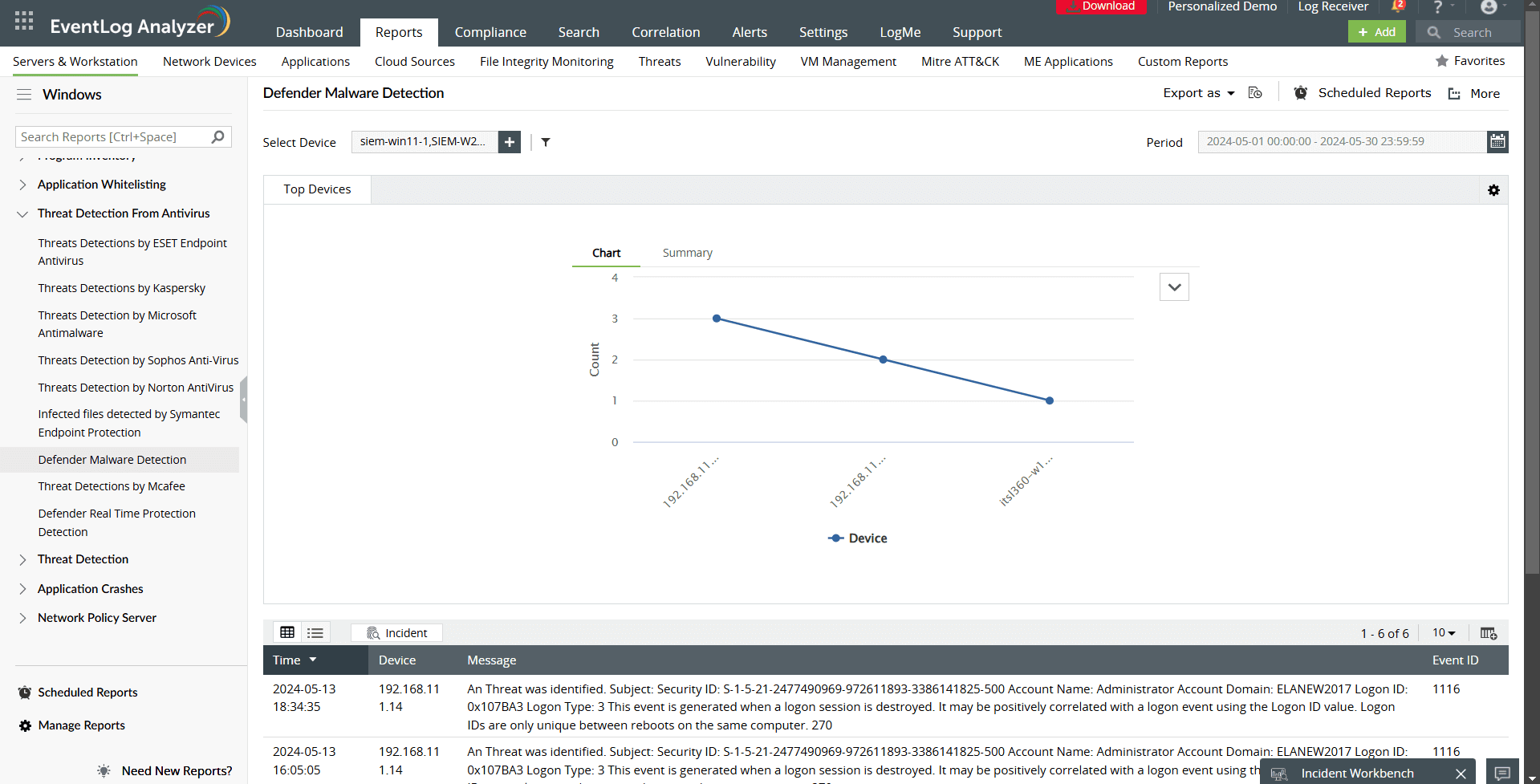
- Real-time Defender protection detection: Track real-time protection actions taken by Defender, such as when threats are detected and neutralized, in real time.
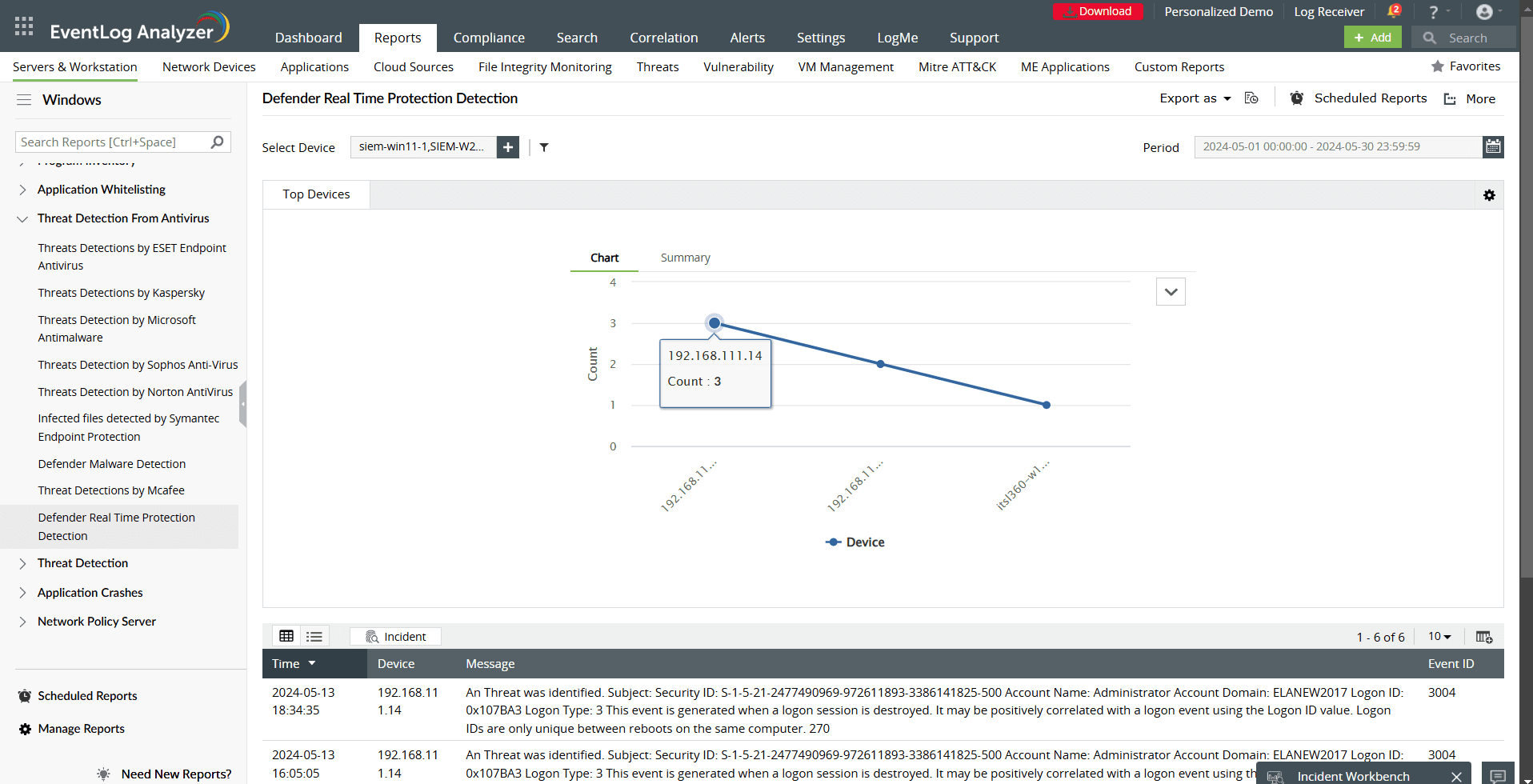
- Defender malware detection: Analyze logs for malware detected by Windows Defender, including threats blocked or quarantined.
Setting up alerts based on Windows Defender logs
Effective alerting transforms Windows Defender logs into actionable intelligence, allowing organizations to respond swiftly to security events and maintain compliance.
Benefits of alerts for Windows Defender logs
- Real-time threat monitoring: Instantly flag potential threats detected by Windows Defender to minimize response times and mitigate risks.
- Enhanced endpoint visibility: Gain comprehensive insights into scans, quarantines, and security incidents to assess device health across the network.
- Compliance assurance: Set alerts for specific events, such as malware detections or access violations, to meet regulatory standards like the PCI DSS, the GDPR, or HIPAA.
Custom alerts for tailored security
Customizing alerts allows organizations to focus on specific scenarios, ensuring a proactive response to critical events:
- Malware detection: Notify teams when particular malware types or severity levels are identified.
- Quarantine failures: Flag instances where Windows Defender's remediation or quarantine processes are unsuccessful, signaling potential vulnerabilities.
- Policy deviations: Detect and alert on violations of predefined security configurations.
Advantages of custom alerts
- Precision monitoring: Target high-priority events while minimizing irrelevant notifications.
- Efficient incident management: Define alert thresholds and escalation paths to streamline responses to critical threats.
- Integration with SIEM: Seamlessly incorporate custom alerts into workflows, enabling automated responses and correlating events from diverse log sources.
EventLog Analyzer’s advanced alerting features
With EventLog Analyzer, managing Windows Defender logs becomes more efficient through features like:
- Predefined alerts: Quick setup for commonly monitored events in defender logs.
- Customizable alerts: Flexibility to define specific conditions, thresholds, and severity levels tailored to organizational needs.
Centralized dashboards: Unified views of triggered alerts and associated log data to simplify investigations and audits.
By leveraging EventLog Analyzer, organizations can analyze trends, identify malware attack patterns, and address security incidents proactively. The ability to set and customize alerts ensures that critical Defender log events are acted upon promptly, bolstering both security readiness and compliance efforts.











