How to view and access Windows Firewall logs
Last updated on:In this page
What are Windows Firewall logs?
Windows Firewall logs are records generated by the Windows Defender Firewall that document network activity based on predefined security rules. As a host-based firewall, it monitors and regulates incoming and outgoing system traffic. These logs play a crucial role in monitoring network security by providing detailed information about access attempts, including the source and destination IP addresses, protocols, and port numbers. By analyzing these logs, administrators can assess the effectiveness of firewall rules, identify potential security threats, and ensure compliance with security policies.
How to view and access Windows Firewall logs
Here are the different methods to access and view Windows Firewall logs across various Windows operating systems:
In Windows 10 and Windows 11
Method 1: Using the default log file
- Open File Explorer and navigate to C:\Windows\System32\LogFiles\Firewall.
- Locate the file pfirewall.log.
- If the file is not present, logging may not be enabled (see steps to enable logging above).
- Open the file using a text editor like Notepad or a log viewer for detailed analysis.
Method 2: Using Windows Event Viewer
- Press Win + R, type eventvwr.msc, and press Enter.
- Navigate to Applications and Services Logs > Microsoft > Windows > Windows Defender Firewall with Advanced Security > Firewall.
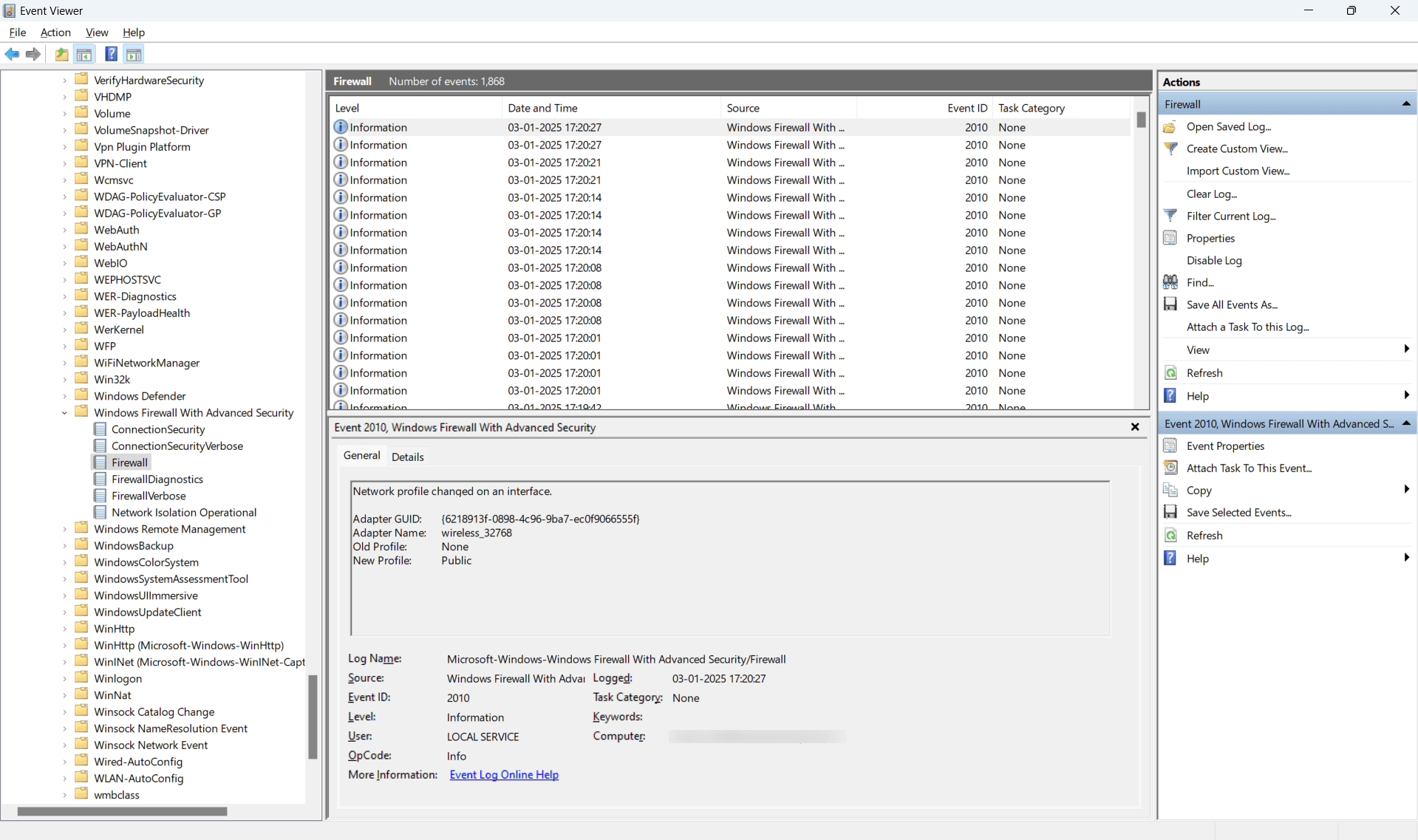
- Look for entries related to blocked or allowed network traffic.
In Windows 7 and Windows 8
Method 1: Using the default log file
- Open File Explorer and go to C:\Windows\System32\LogFiles\Firewall.
- Open the pfirewall.log file in a text editor.
Method 2: Using Windows Event Viewer
- Press Win + R, type eventvwr.msc, and press Enter.
- Go to Applications and Services Logs > Microsoft > Windows > Windows Firewall with Advanced Security.
- Review the log entries for relevant details.
In Windows Server (2012, 2016, 2019, 2022)
Method 1: Using the default log file
- Navigate to C:\Windows\System32\LogFiles\Firewall.
- Open the pfirewall.log file using a text editor.
Method 2: Using Windows Event Viewer
- Launch the Server Manager.
- Go to Tools > Event Viewer.
- Navigate to Applications and Services Logs > Microsoft > Windows > Windows Firewall with Advanced Security > Firewall.
- Analyze the entries for blocked or successful connections.
Method 3: Using PowerShell
- Open PowerShell as an administrator.
-
Run the following command to query firewall events:
Get-WinEvent -LogName "Microsoft-Windows-Windows Firewall With Advanced Security/Firewall"
These methods vary slightly depending on the Windows version, but the default log location (C:\Windows\System32\LogFiles\Firewall) and Event Viewer logs remain consistent across most versions.
How to analyze Windows Firewall logs
Firewall logs record various types of events, primarily focusing on allowed and blocked connections.
Some of the key entries include:
- Timestamp: The date and time of the connection attempt.
- Action: Indicates whether the connection was "ALLOW" (permitted) or "DROP" (blocked).
- Protocol: Specifies the communication protocol used (e.g., TCP or UDP).
- Source and destination IP addresses: Identifies the origin and target of the network traffic.
- Port numbers: Shows the ports used for the connection, which can help in troubleshooting connectivity issues.
By analyzing these entries, administrators can identify unusual patterns, such as repeated blocked attempts from a specific IP address, which may indicate a security threat or unauthorized access attempt.
How can Windows Firewall logs enhance security?
Firewall logs can significantly enhance network security by enabling administrators to:
- Monitor network activity: Regularly review logs to detect unauthorized access attempts or suspicious behavior.
- Adjust firewall rules: Use insights from the logs to refine firewall rules, allowing legitimate traffic while blocking malicious attempts.
- Investigate incidents: In the event of a security breach, logs provide forensic evidence that can help trace the source of the attack and understand its impact.
- Identify anomalies: By establishing a baseline of normal network activity, administrators can quickly spot deviations that may indicate a compromise or misuse of network resources.
What are the best practices for managing Windows Firewall logs?
Managing Windows Firewall logs effectively is crucial for maintaining a secure and well-monitored network.
Here are some common best practices:
- Enable logging: Activate and configure logging for both allowed and blocked connections via Microsoft Defender Firewall.
- Set log size: Increase the default log size (e.g., 10MB for high-traffic environments) to prevent overwriting crucial data.
- Archive logs: Automate log rotation and store backups securely for future reference.
- Centralize management: Use log management tools like EventLog Analyzer for centralized log analysis, real-time alerts, and reporting.
- Filter noise: Customize logging to focus on critical events, such as denied inbound connections.
- Automate monitoring: Set real-time alerts for suspicious activities like repeated failed connections or port scans.
- Audit and review: Regularly analyze logs to identify anomalies and correlate with other data sources.
- Back up and retain: Schedule backups and define a retention policy to meet compliance requirements.
These practices not only enhance visibility but also streamline incident response and regulatory compliance efforts.
How ManageEngine EventLog Analyzer monitors Windows Firewall logs
ManageEngine EventLog Analyzer is a log management and IT compliance tool that provides comprehensive monitoring of firewall logs, delivering enhanced visibility into network activity and potential security threats.
Here's how:
- Real-time threat detection: EventLog Analyzer continuously monitors firewall logs to detect suspicious activity like unauthorized access attempts, port scans, or unusual traffic patterns. Instant alerts are triggered for potential threats, ensuring timely responses.
- Audit and compliance reporting: With detailed firewall log analysis, EventLog Analyzer helps meet compliance requirements such as the PCI DSS, HIPAA, and the GDPR. It generates in-depth reports on firewall activity, including allowed and denied traffic, helping maintain a clear audit trail.
- Security incident forensics: By correlating firewall logs with other security events (e.g., login attempts or malware detections), EventLog Analyzer enables thorough investigation of security incidents. This helps uncover attack vectors and prevent future breaches.
- Network traffic analysis: The tool provides insights into network traffic patterns, identifying abnormal behaviors that could indicate attacks like DDoS or data exfiltration attempts.
- Proactive security posture: EventLog Analyzer's proactive monitoring of firewall logs enables administrators to fine-tune firewall rules and policies, improving security controls and reducing vulnerabilities in the network.
Here are some of the reports that help in the monitoring of Windows Firewall logs:
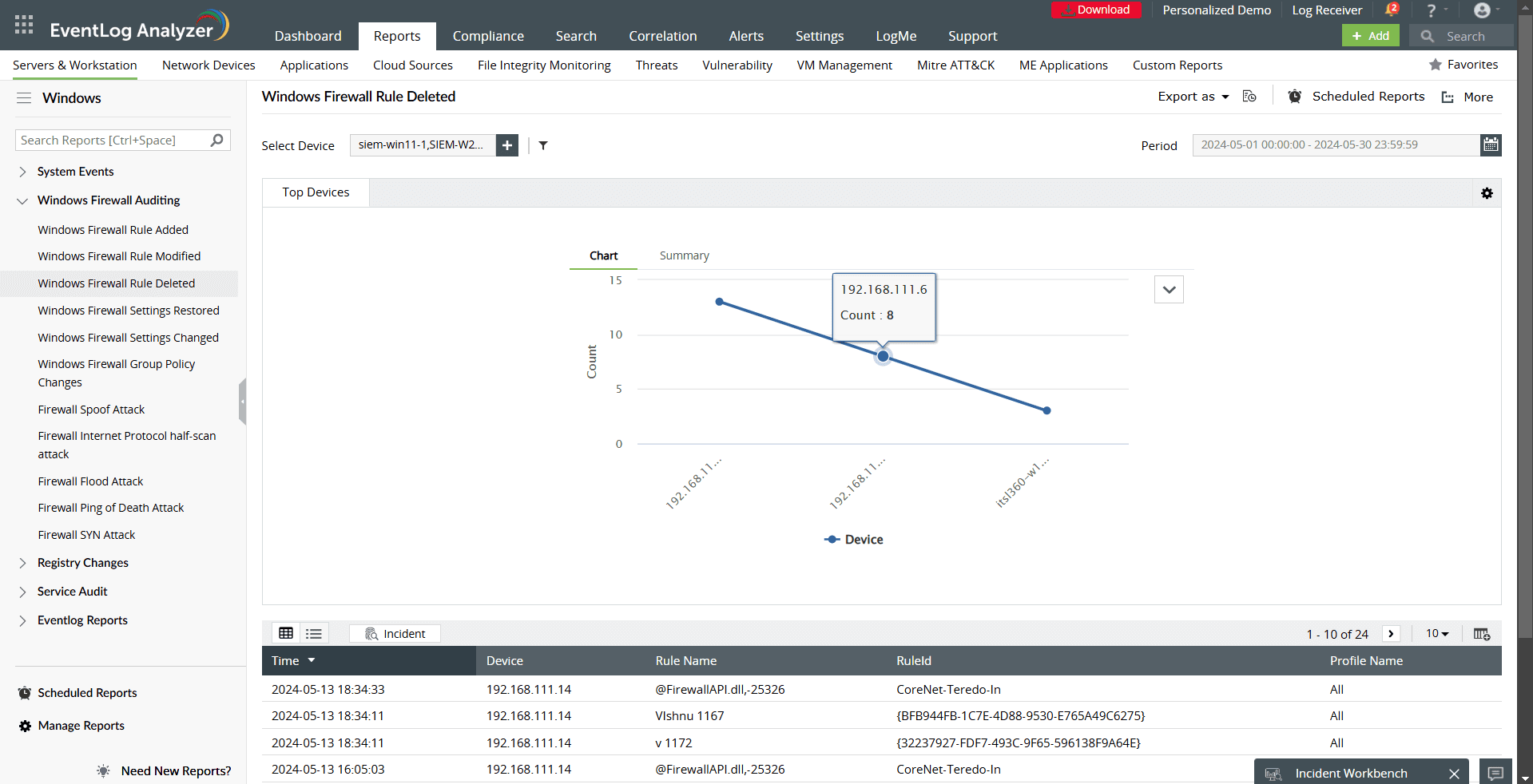
- Windows Firewall Rule Added/Modified/Deleted: Track added, altered, or removed firewall rules to identify unauthorized or misconfigured changes.
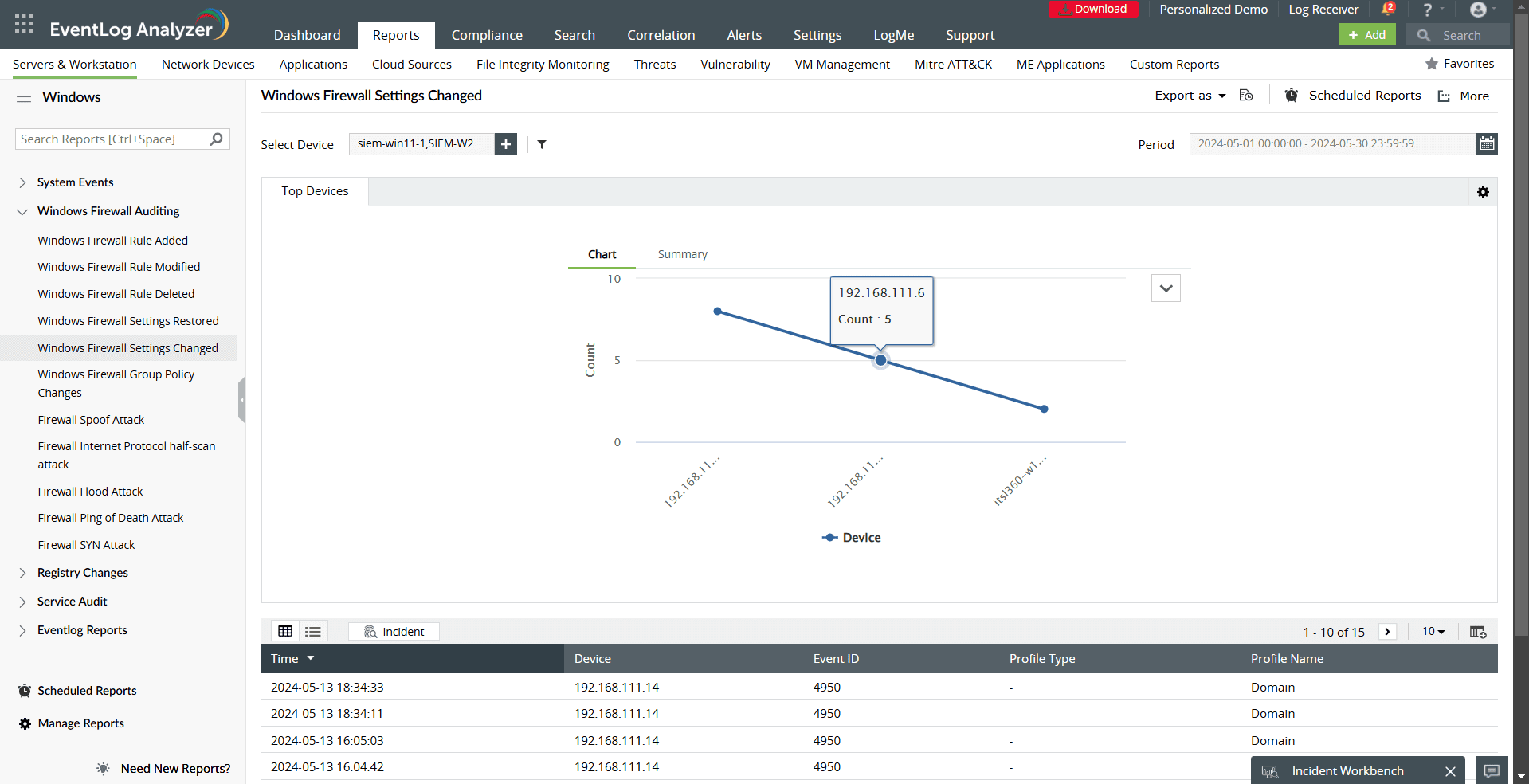
- Windows Firewall Settings Changed/Restored: Monitor changes or restorations to firewall settings that could weaken security.
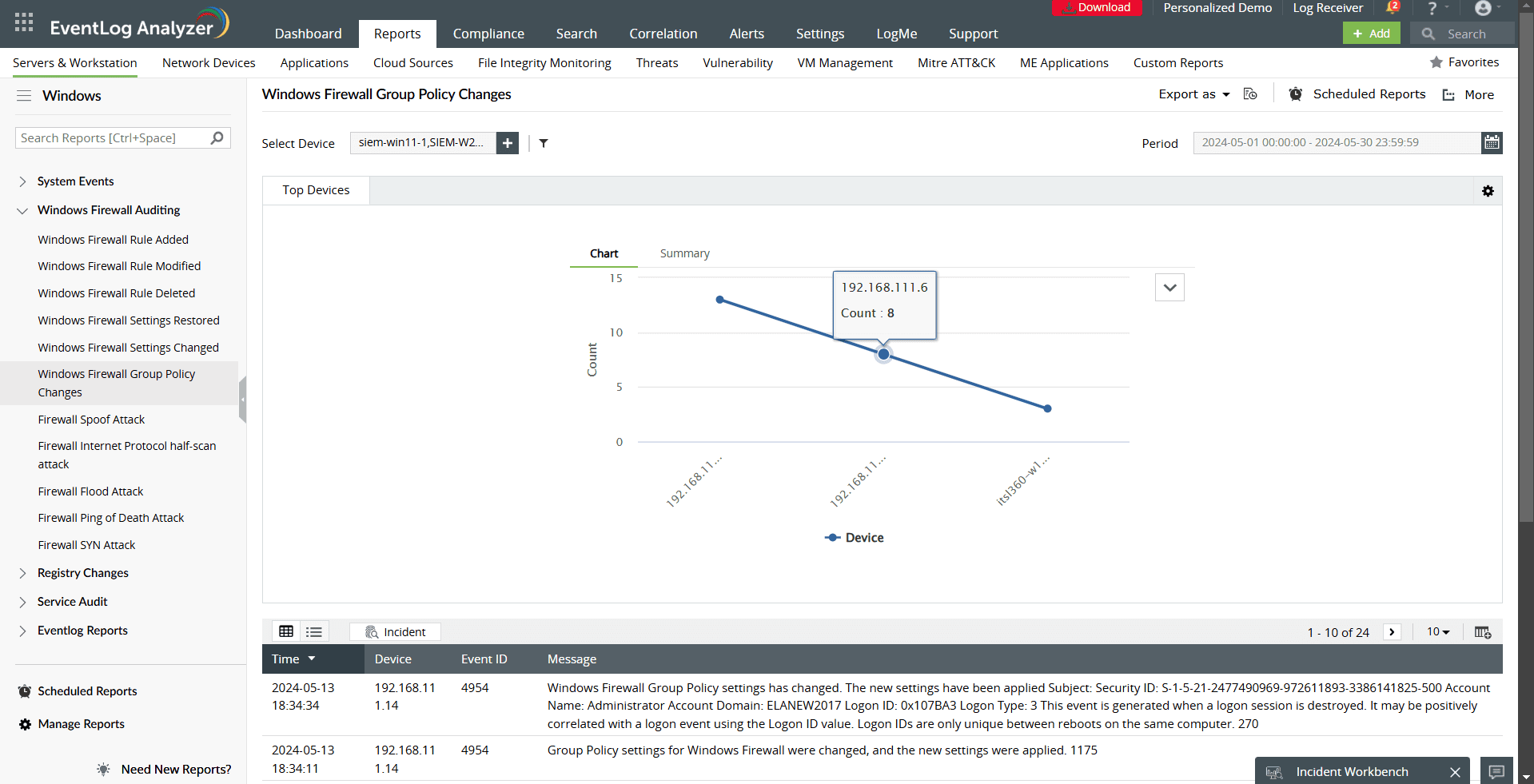
- Windows Firewall Group Policy Changes: Audit updates to group policies affecting firewall settings across the network.
- Firewall Spoof Attack: Identify attempts to spoof IP addresses to gain unauthorized access.
- Firewall Internet Protocol half-scan attack: Detect suspicious traffic that involves scanning for open ports.
- Firewall Flood Attack: Recognize attempts to overwhelm the network with excessive traffic.
- Firewall Ping of Death Attack: Detect oversized ping packets designed to crash systems.
- Firewall SYN Attack: Spot SYN flood attacks aimed at exhausting server resources.
By leveraging EventLog Analyzer for firewall log monitoring, organizations can gain comprehensive visibility into network activity, proactively address threats, and ensure compliance with regulatory standards, bolstering overall security.











