- Home
- Logging Guide
- Linux commands
Top 50 essential Linux commands every sysadmin
should know
In this page
- Linux commands for system information and monitoring
- Basic Linux commands for file and directory management
- Linux network commands
- Linux security commands
- How EventLog Analyzer helps with Linux monitoring
Linux is one of the most widely used operating systems, particularly in server environments. For sysadmins, mastering Linux commands is crucial for everyday tasks. Whether troubleshooting, managing files, or securing systems, a strong understanding of Linux commands can save time and enhance efficiency. This article provides a Linux cheat sheet with a curated list of the top 50 Linux commands every sysadmin should know.
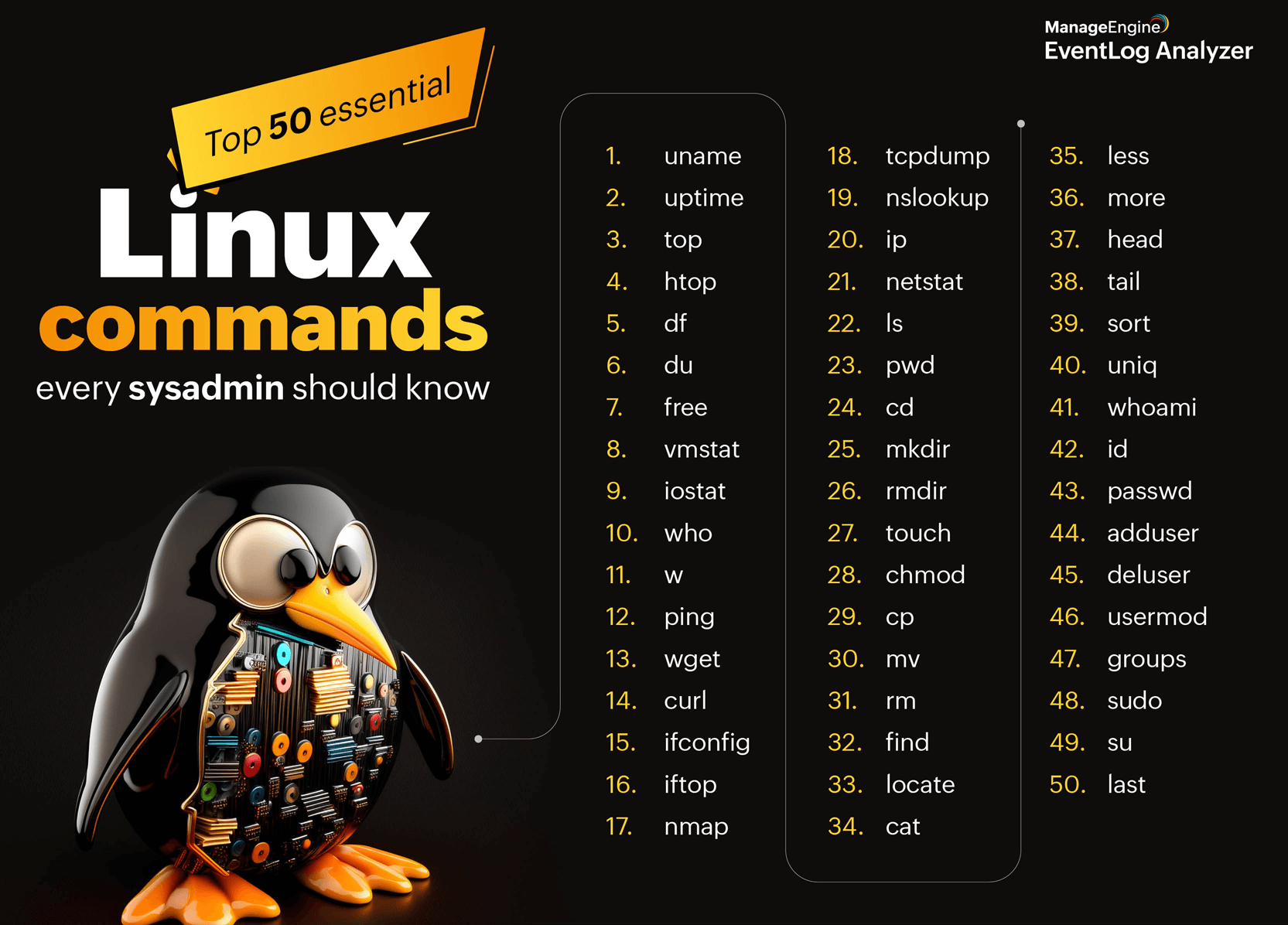
Top 50 Linux commands cheat sheet
Here’s the comprehensive list of all Linux commands:
System information and monitoring
- uname: Displays system information (kernel, OS, etc.).
- uptime: Provides information on the system's uptime and load averages.
- top: Shows live system processes and their resource consumption.
- htop: An interactive version of the top command, offering an enhanced process viewer.
- df: Displays disk space usage statistics.
- du: Shows disk usage details for files and directories.
- free: Shows memory usage (RAM and swap).
- vmstat: Reports system performance metrics (CPU, memory, IO).
- iostat: Displays CPU, device, and network performance statistics.
- who: Lists logged-in users.
- w: Displays who is logged in and their current actions.
File and directory management
- ls: Lists all files and directories in the current directory.
- pwd: Displays the path of the current directory.
- cd: Changes the current directory to the specified one.
- mkdir: Creates new directories.
- rmdir: Removes empty directories.
- touch: Creates empty files or updates the access and modification timestamps of existing files.
- chmod: Modifies file permissions to control access.
- cp: Copies files and directories to another location.
- mv: Moves or renames files and directories.
- rm: Deletes files or directories.
- find: Searches for files based on specific criteria.
- locate: Quickly locates files using a pre-built database.
- cat: Displays the contents of a file.
- less: Views file content one page at a time.
- more: Similar to less but with fewer features.
- head: Shows the first few lines of a file.
- tail: Displays the last few lines of a file.
- sort: Organizes the content of a file in a specific order.
- uniq: Removes consecutive duplicate lines from a file.
Interested in learning more about Linux file and directory management? Explore our how-to guides on Linux file integrity monitoring, locating files in Linux, and removing or deleting directories from Linux machines.
User management
- whoami: Displays the username of the currently logged-in user.
- id: Shows the user and group IDs for the current user.
- passwd: Changes the password for a specified user.
- adduser: Adds a new user to the system.
- deluser: Removes a user from the system.
- usermod: Modifies properties of an existing user account.
- groups: Lists all the groups a user belongs to.
- sudo: Executes commands with elevated privileges (superuser).
- su: Switches to another user account, typically root. Displays the current user.
- last: Displays login history.
Want to know more on Linux user management? Check out our listing users in Linux systems and adding user to a group in Linux machines how-to guides.
Networking
- ping: Checks connectivity to a host.
- wget: Retrieves files from the internet via HTTP, HTTPS, or FTP protocols.
- curl: Transfers data to and from a server using various protocols, including HTTP, FTP, and more.
- ifconfig: Displays and configures network interfaces (deprecated, replaced by the ip command).
- iftop: Monitors real-time bandwidth usage across network interfaces.
- nmap: Scans networks to detect open ports, services, and network devices.
- tcpdump: Captures and analyzes network packets for troubleshooting and security monitoring.
- nslookup: Queries DNS to resolve domain names into IP addresses.
- ip: Configures and manages network interfaces and routing tables.
- netstat: Shows network connections and listening ports.
Short on time? Grab the Linux commands cheat sheet PDF for quick access and keep it as your go-to reference!
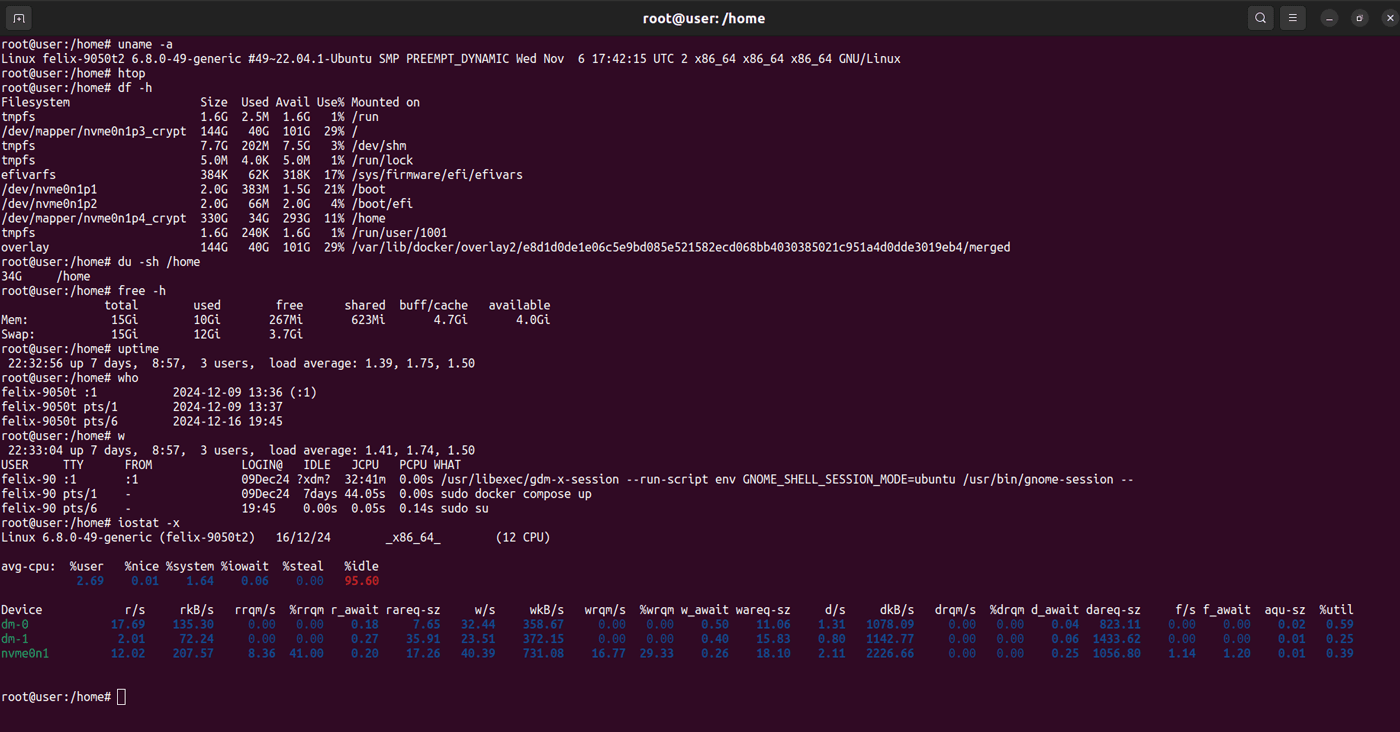
Linux commands for system information and monitoring
These Linux commands help sysadmins gather critical information about system performance, hardware details, and resource usage, enabling proactive management and troubleshooting.
| Command | Description | Example | Example output |
|---|---|---|---|
| uname | Shows system details, including the kernel version and system architecture. | uname -a | Outputs detailed information like kernel name, version, and architecture. |
| df | Reports disk space usage for mounted file systems. | df -h | Displays filesystem details (size, used, available space, and mount point) in a human-readable format. |
| du | Shows the disk usage for files and directories. | du -sh /path | Summarizes the size of the specified directory. |
| free | Shows memory usage, including total, used, and free memory. | free -h | Outputs memory details in a human-readable format. |
| vmstat | Provides detailed information about memory, CPU, and I/O activities. | vmstat 5 | Outputs system performance data every 5 seconds. |
| last | Displays a list of last logged-in users. This is useful for identifying any suspicious login attempts. | last | Lists recent logins, including user names, login times, and source IP addresses. |
| who | Shows who is currently logged in, including their login times and originating IP addresses. | who | Lists logged-in users and their login times. (e.g., "user tty7 2024-12-08 10:00") |
| w | Similar to the who command, but also displays the user’s activity. | w | Shows a summary of system uptime, logged-in users, and active processes for each user. |
| iostat | Tracks CPU usage and disk I/O statistics. | iostat -x | Shows extended I/O statistics for devices. |
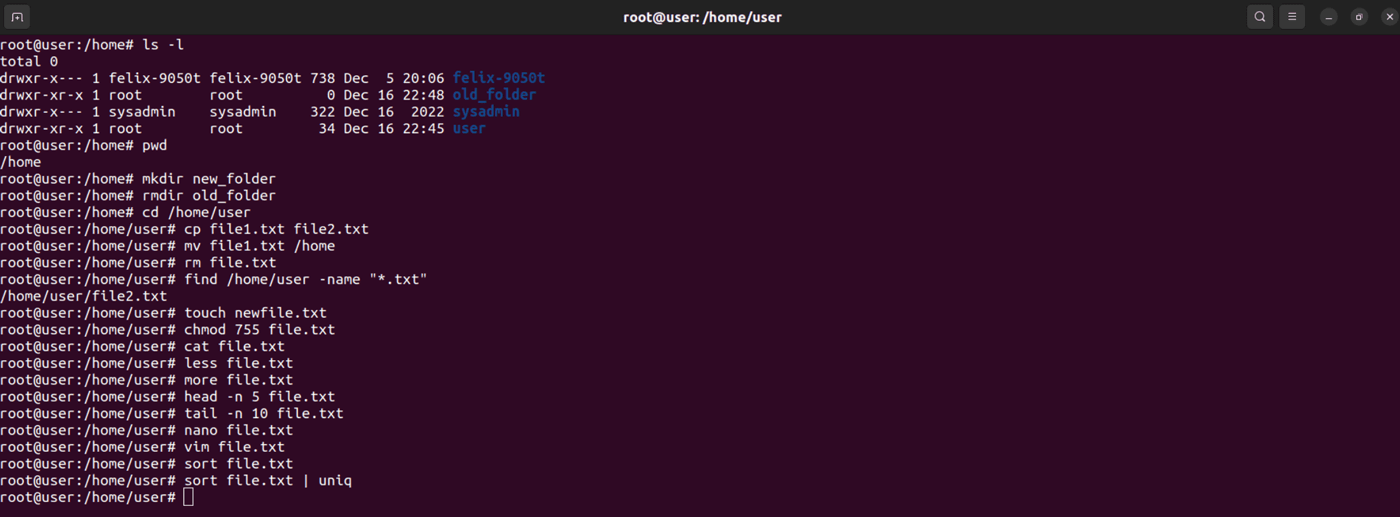
Basic Linux commands for file and directory management
File management is critical for maintaining a system's organization and ensuring that data is accessible and secure. These Linux commands help manage files, directories, and storage, from creating and modifying files to searching for them.
| Command | Description | Example | Example output |
|---|---|---|---|
| ls | Displays the files and directories within the current directory. | ls -l | Displays files in a detailed, long-list format with permissions, ownership, and size. |
| pwd | Prints the current working directory, showing the full path from the root. | pwd | The command displays the current directory the user is working in. (e.g., "/home/user/documents") |
| mkdir | Creates a new directory in the specified location. | mkdir new_folder | Creates a folder named new_folder in the current directory. |
| rmdir | Deletes an empty directory. | rmdir old_folder | Deletes the directory named old_folder if it is empty. |
| cd | Changes the current directory. | cd /home/user | Switches to the /home/user directory. |
| cp | Copies files or directories. | cp file1.txt file2.txt | Copies file1.txt to file2.txt. |
| mv | Moves or renames files and directories. | mv file1.txt newdir/ | Moves file1.txt to the newdir directory. |
| rm | Removes files or directories. | rm file.txt | Deletes file.txt. |
| find | Searches for files and directories based on criteria. | find /path -name "*.txt" | Finds all .txt files in the specified path. |
| locate | Quickly searches for files using a pre-built database. | locate file.txt | Displays the location of file.txt from the database. |
| touch | Creates an empty file or updates file timestamps. | touch newfile.txt | Creates newfile.txt or updates its timestamp. |
| chmod | Modifies file permissions to control access. | chmod 755 file.sh | Grants read, write, and execute permissions to the owner, and read and execute permissions to others. |
| cat | Displays the entire content of a file. | cat file.txt | Prints all the contents of file.txt to the terminal. |
| less | Displays file content one page at a time. | less file.txt | Opens file.txt for page-wise viewing with navigation. |
| more | Similar to the less command, but supports only forward navigation. | more file.txt | Displays file.txt content one page at a time. |
| head | Shows the first few lines of a file | head -n 5 file.txt | Shows the first 5 lines of file.txt. |
| tail | Shows the last few lines of a file. | tail -n 10 file.txt | Shows the last 10 lines of file.txt. |
| nano | A basic command-line text editor. | nano file.txt | Opens file.txt in Nano editor for editing. |
| vim | An advanced text editor with rich features. | vim file.txt | Opens file.txt in Vim for advanced editing. |
| sort | Sorts the lines in a file alphabetically or numerically. | sort file.txt | Displays file.txt sorted line-by-line. |
| uniq | Removes duplicate lines from a file. | sort file.txt | uniq | Displays only unique lines from file.txt. |
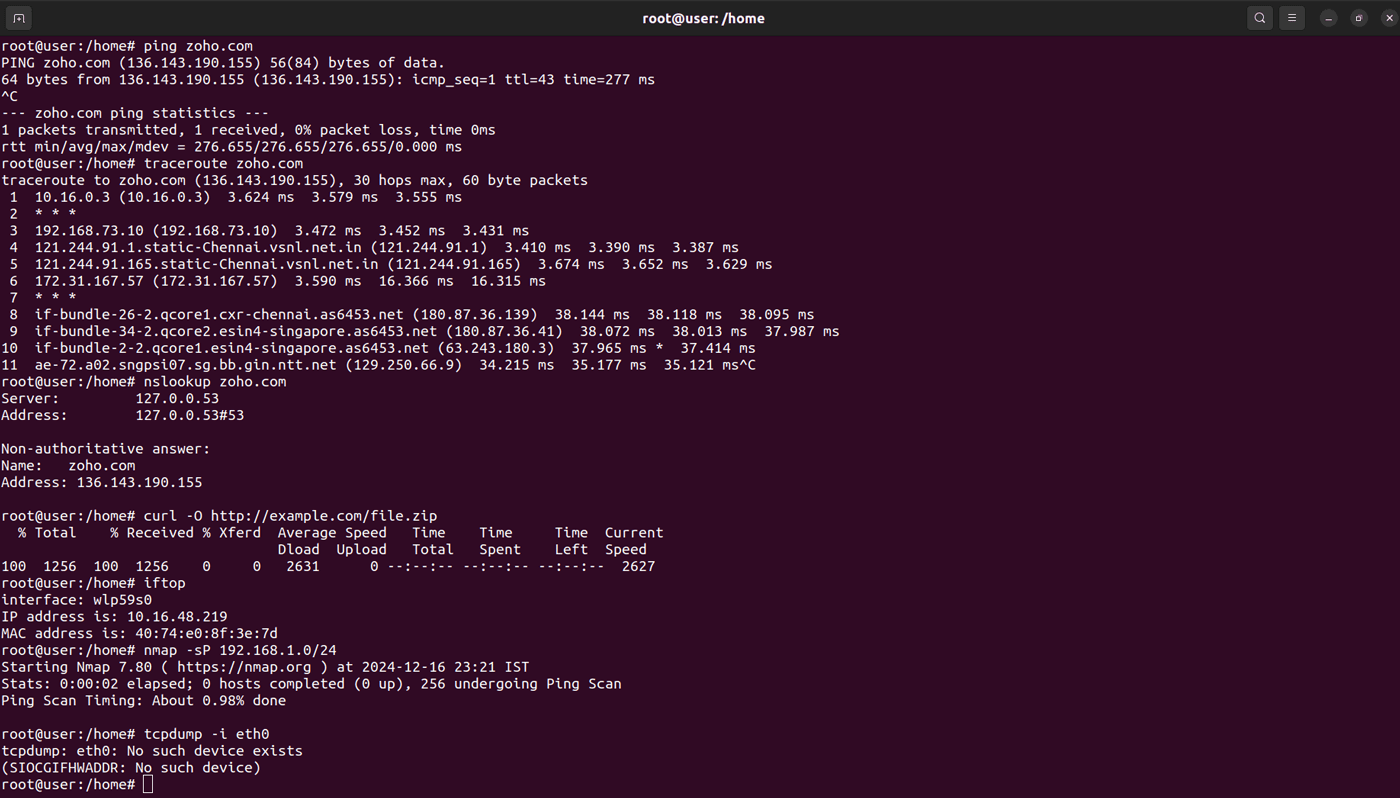
Linux network configuration and management commands
These Linux network commands are crucial for configuring network interfaces, monitoring network connections, and diagnosing network-related problems
| Command | Description | Example | Example output |
|---|---|---|---|
| ping | Tests connectivity to a remote host via ICMP packets. | ping google.com | Sends ICMP echo requests to google.com and shows the response time. |
| ifconfig | Configures or displays network interfaces (deprecated in favor of the ip command). | ifconfig eth0 | Displays the IP address, netmask, and other details of eth0. |
| ip | Configures network interfaces and routing. | ip addr show | Shows IP address information for all network interfaces. |
| netstat | Displays network connections, routing tables, and interface statistics. | netstat -tuln | Lists listening ports and associated services. |
| ss | Displays socket statistics, offering a faster alternative to the netstat command. | ss -tuln | Displays a list of listening ports and active connections. |
| traceroute | Traces the path of packets to a destination host. | traceroute google.com | Displays the route and hops taken to reach google.com. |
| nslookup | Queries DNS to retrieve domain or IP address information. | nslookup example.com | Displays the IP address associated with example.com. |
| curl | Transfers data to or from a server using various protocols. | curl -O http://example.com/file.zip | Downloads file.zip from example.com. |
| wget | Downloads files from the internet. | wget http://example.com/file.zip | Downloads file.zip to the current directory. |
| scp | Securely copies files between systems. | scp file.txt user@remote:/path | Copies file.txt to the remote server’s /path directory. |
| rsync | Synchronizes files and directories between two locations, locally or remotely. | rsync -av source/ dest/ | Copies files from source to destination while preserving permissions, timestamps, and symbolic links. |
| iftop | Shows real-time bandwidth usage on a network interface, helping identify abnormal traffic patterns. | Iftop | Bandwidth usage by IPs. |
| nmap | Scans for open ports on the system or network. This command is useful for identifying exposed services. | nmap -sP 192.168.1.0/24 | Host 192.168.1.1 is up. |
| tcpdump | Captures and analyzes network packets to troubleshoot and monitor network traffic. | tcpdump -i eth0 | Monitor packets on the eth0 interface. |
Linux security and monitoring commands
For system security, user management, and continuous monitoring of critical system resources, these Linux security commands are indispensable.
| Command | Description | Example | Example output |
|---|---|---|---|
| sudo | Grants superuser privileges for executing commands. | sudo apt update | Run updates as a superuser. |
| passwd | Changes a user’s password for securing accounts. | passwd username | Prompts for a new password for the specified user. |
| fail2ban-client | Manages Fail2Ban to prevent brute-force attacks by banning IPs. | fail2ban-client status | Displays the status of the Fail2Ban service and banned IPs. |
| iptables | Configures Linux firewall rules. | iptables -L | Lists the current firewall rules. |
| ufw | Manages and configures firewall settings. | ufw allow 80/tcp | Allows HTTP traffic on port 80. |
| auditd | Records security-related events, such as login attempts and access violations, to maintain an audit trail for system security. | auditctl -l | Displays the current audit rules. |
| top | Displays real-time system resource usage. (Use Shift + M to sort by memory usage) | top | Displays CPU, memory, and process utilization in real time. |
| htop | An enhanced version of the top command, providing a more user-friendly, interactive view of system processes. | htop | Provides a visual and interactive display of resource usage. |
| ps | Lists current running processes and their resource usage. | ps aux | Displays all active processes along with detailed information. |
| uptime | Displays the system’s uptime, helps spot irregular downtime. | uptime | Shows uptime, logged-in users, and system load. (e.g., "10:15:23 up 5 days, 4:32, 3 users, load average: 0.24, 0.20, 0.22") |
| lsof | Lists open files associated with running processes. Useful for troubleshooting. | lsof /path/to/file | Displays all processes accessing the file at /path/to/file. |
By mastering these commands, sysadmins can significantly improve productivity and troubleshooting capabilities. But securing the Linux environment requires a deeper level of monitoring and incident response. This is where EventLog Analyzer comes in, offering advanced log management capabilities that complement Linux command-line expertise.
How EventLog Analyzer helps with Linux monitoring
ManageEngine EventLog Analyzer, a comprehensive log management and compliance tool, streamlines Linux monitoring by centralizing syslog from all Linux distributions. While Linux commands give the power to perform actions on systems, EventLog Analyzer ensures that every action is logged and analyzed for security events.
Here’s how EventLog Analyzer enhances Linux monitoring:
- Centralized syslog collection and monitoring: Consolidates syslog data from multiple Linux systems into a single interface, simplifying infrastructure management and providing a unified view for efficient monitoring.
- User activity monitoring: Tracks critical user activities in real time, such as failed login attempts, unauthorized access events, and brute-force attacks, ensuring comprehensive visibility into system usage.
- SUDO command auditing: Monitors privileged operations, including sudo command executions and failed attempts. It enforces least privilege policies and detects unauthorized privilege escalations to prevent potential security breaches.
- Real-time auditing and alerts: Sends instant alerts via email or SMS to enable quick responses to suspicious events, minimizing potential security risks.
- Comprehensive reporting for compliance: Provides over 100 customizable reports to track system activities. These reports help organizations meet regulatory requirements such as HIPAA, GDPR, FISMA, CCPA, and PCI DSS.
- Threat detection with pre-built correlation rules: Offers 30+ pre-built correlation rules to identify threats like brute-force attacksand SQL injection attacks. The tool’s event correlation capabilities enable proactive threat detection and mitigation.
- Automated incident response: Streamlines incident response with customizable workflows, reducing manual intervention and enhancing the efficiency of resolution processes.
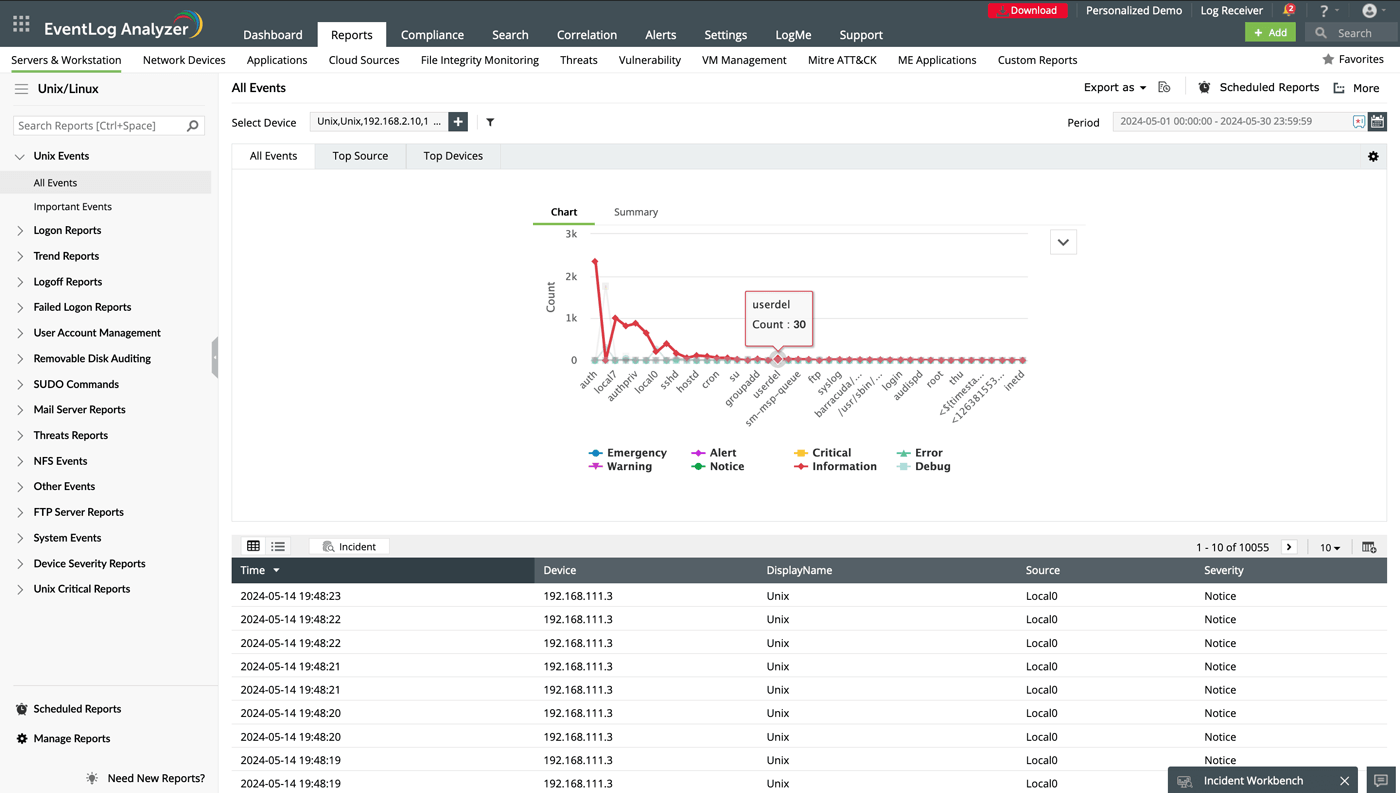
Track all events on your Unix systems such as cron jobs, session connections and disconnections, deactivated services, and more.
Select a time range to filter events.
Select the desired format for exporting the data (e.g., CSV, PDF, or Excel).
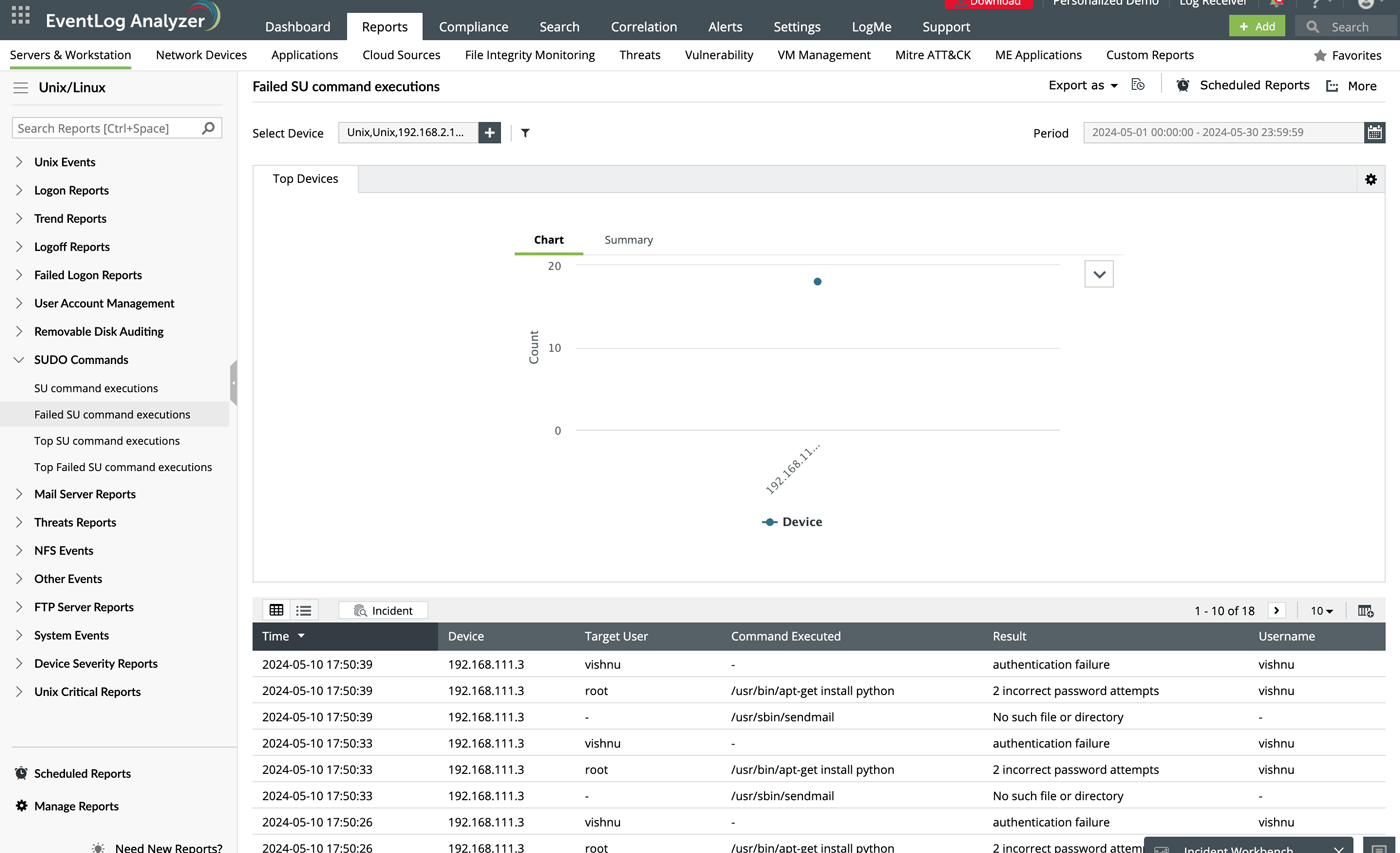
Visual representation of failed sudo command executions over time.
List of specific failed sudo commands attempted by users. This helps track unauthorized or incorrect commands executed with elevated privileges.
The proportion of each failed command execution relative to the total failed attempts, providing insight into the most commonly attempted commands.











