- Home
- Logging Guide
- How to analyze allowed and denied firewall traffic events?
How to analyze allowed and denied firewall traffic events?
In this page
- Analyzing firewall logs: Traffic allowed/dropped events
Analyzing firewall logs: Traffic allowed/dropped events
Firewall logs will provide insights on the traffic that has been allowed or blocked. Analyzing these events is essential because, in most cases, this is the starting point of data breaches.
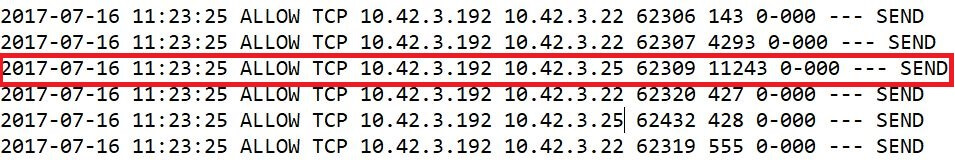
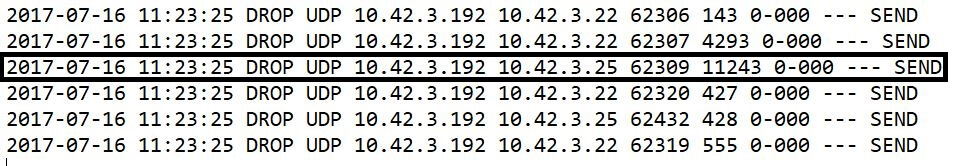
In the above image, the highlighted part is an allowed traffic log. The log data shows the date, time, type of protocol, source and destination IPs, and the port numbers. With this information, we can identify which packet was allowed, when and how. The entry point, in case of a data breach can easily be identified. The image below is an example of dropped packets.
Manually sifting through all the allowed and denied traffic to find traffic from a specific source is a tedious task. However, you get this information in a jiffy with a log management solution like EventLog Analyzer.
EventLog Analyzer, a comprehensive log management solution, provides predefined reports on Denied Connection, User Logons, Failed Logons, Individual User Action, and more. These reports help in analyzing the logs and instantly spot anomalous traffic behavior.











