- Free Edition
- What's New?
- Quick Links
- Log Management
- Application Log Management
- Application log monitoring
- IIS log analyzer
- IIS web log analyzer
- IIS FTP log analyzer
- IIS log parser
- VMware log analyzer
- Hyper V event log auditing
- SQL database auditing
- SQL server auditing
- MySQL log analyzer
- Apache log analyzer
- DHCP server auditing
- Database activity monitoring
- Database auditing
- Oracle database auditing
- IT Compliance Auditing
- IT Compliance Auditing
- SOX Compliance Audit
- GDPR Compliance Audit
- ISO 27001 Compliance Audit
- HIPAA Compliance Audit
- PCI Compliance Audit
- FISMA Compliance Audit
- GLBA Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- CCPA Compliance Reports
- CCPA Compliance Software
- NERC Compliance Audit Reports
- Cyber Essentials Compliance Reports
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
- PDPA compliance audit reports
- CMMC Compliance Audit
- SIEM
- Security Information and Event Management (SIEM)
- Threat Intelligence
- STIX/TAXII feed processor
- Server Log Management
- Event Log Monitoring
- File Integrity Monitoring
- Linux File Integrity Monitoring
- Threat Whitelisting
- Advanced Threat Analytics
- Security Log Management
- Log Forensics
- Incident Management System
- Application log management
- Real-Time Event Correlation
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Linux Log Analyzer
- Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Cisco Logs Analyzer
- VPN log analyzer
- IDS/IPS log monitoring
- Solaris Device Auditing
- Monitoring user activity in routers
- Monitoring Router Traffic
- Switch Log Monitoring
- Arista Switch Log Monitoring
- Firewall Log Analyzer
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet log analyzer
- Endpoint Log Management
- System and User Monitoring Reports
- More Features
- Resources
- Product Info
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Routers, critical devices regulating network traffic, need continuous monitoring to ensure network uptime, detect potential security threats in the early stages, and stay compliant with regulatory mandates. Enable continuous router log monitoring with EventLog Analyzer to:
- Monitor router user activities, suspicious configuration changes, and insider threats.
- Effectively implement capacity planning through traffic trend analysis.
- Detect malicious traffic and spot potential security threats.
What is router monitoring?
Router monitoring is the process of continuously tracking a router's performance, health, and activities to ensure optimal network operation, keep security threats at bay, and achieve compliance. The various aspects of router monitoring include:
- Hardware checks: Check the statuses of the router's CPU utilization, memory usage, disk space, and power supply.
- Router traffic monitoring: Track inbound and outbound traffic to identify potential bottlenecks and security threats.
- Interface monitoring: Track the statuses of the router's interfaces, including link statuses, error rates, and packet loss.
Monitoring these key metrics is essential for network administrators to identify and resolve potential issues proactively, preventing network outages and downtime.
ManageEngine EventLog Analyzer, a comprehensive log monitoring solution, helps you effectively monitor router logs, maintain network reliability, improve performance, and enhance overall network security.
How EventLog Analyzer helps with router monitoring
Router device discovery automation
Automatically discover router devices in your network for log collection and configure them from within the EventLog Analyzer console. Within minutes of deployment, start collecting logs for the effective monitoring of router traffic.
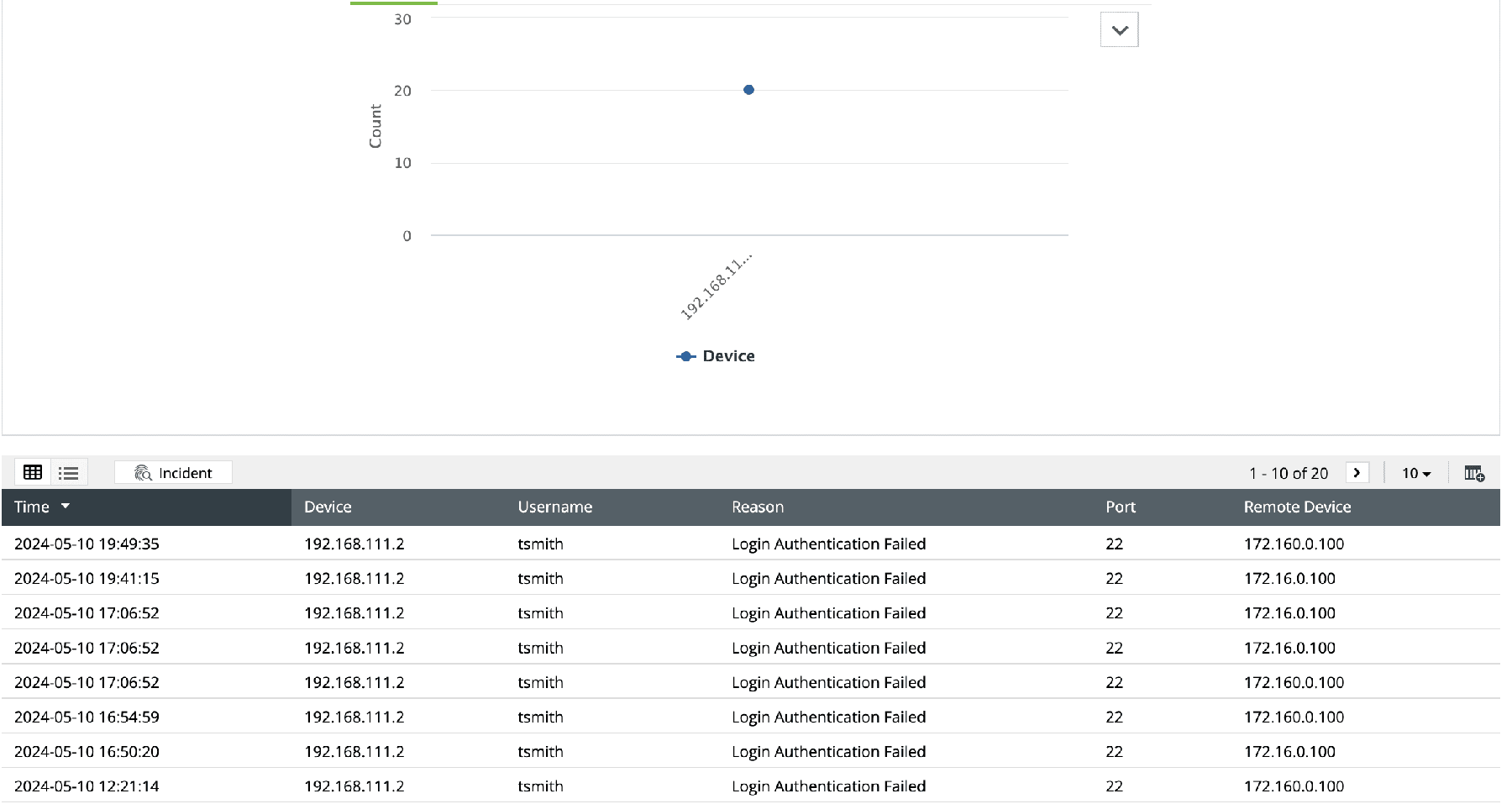
Router logon monitoring
Get visibility into the user logon activities on routers. Gain detailed insights into failed logons, failed logons due to bad authentication, failed SSH logons, and failed VPN logons with automated report generation. Visualize router logons, VPN authentication, and SSH logons based on remote devices, users, and interfaces to spot user authentication anomalies instantly.
Router traffic monitoring
Monitor TCP, UDP, and ICMP traffic with detailed reports providing information on the source IP address, destination, protocol used, and number of packets transmitted. Monitor the overall router traffic and categorize the traffic based on the source and destination for the effective identification of anomalies.
-
Router traffic error reports:
Track traffic anomalies such as too many fragments, invalid fragment lengths, overlapped fragments, denied DHCP snooping, and permitted and denied ARP requests. -
Denied traffic connections:
Gain visibility into denied traffic and detect anomalies concerning denied connections instantly with trend reports. -
Allowed traffic connections:
Monitor allowed traffic via routers with detailed reports that give information on the destination and source IP address of the traffic, number of packets, and traffic protocol. Visualize the top allowed traffic based on the source, protocol, and destination IP address. Automate trend reports on allowed traffic connections to detect anomalies. Receive real-time notifications about abnormal router traffic trends and activities.
EventLog Analyzer supports Cisco, HPE Aruba Networking, Juniper Networks, Dell, and Huawei router logs, among others. Check out the list of supported devices here.
Router monitoring use cases with EventLog Analyzer
By effectively analyzing router logs, network and security administrators can enhance their network performance, security, and operational efficiency. EventLog Analyzer's router monitoring through log analysis helps with the following:
Security analysis
-
Unauthorized access attempts:
Get notified in real time about abnormal failed logon attempts and unauthorized access to your routers' configurations. -
Security policy violations:
Monitor for violations of security policies, such as unauthorized protocol usage or configuration changes.
Configuration change tracking
-
Configuration error detection:
Identify configuration errors and misconfigurations that may cause network disruptions and security vulnerabilities with exhaustive configuration reports. -
Unauthorized configuration changes:
Detect and get alerted to unauthorized configuration changes instantly and take corrective action.
Network troubleshooting
-
Problem isolation:
Correlate router logs with network events to pinpoint the root causes of network issues. EventLog Analyzer allows you to ingest logs from your network monitoring tools as well for effective problem isolation. -
Capacity planning:
Analyze historical traffic data to forecast future network needs and plan for capacity expansions. Identify peak traffic periods to optimize resource allocation and avoid congestion.
Router monitoring alerts available in EventLog Analyzer
- Performance alerts: High CPU utilization, high memory utilization, and increased latency
- Security alerts: Malicious traffic, security policy violations, anomalies in traffic patterns, failed logon attempts, and unauthorized configuration changes
- Hardware alerts: Power failures, fan failures, and hardware component failures
5 reasons to choose EventLog Analyzer as your router monitoring software
1. Predefined alerts for performance bottlenecks and security concerns
Use predefined alert criteria to detect performance bottlenecks and abnormal traffic. Get automated, real-time alerts for unauthorized access, router logons, configuration changes, and more.
2. Automated router logging
Discover the routers in your network automatically using IP or CIDR ranges. Enable logging on the routers from within the EventLog Analyzer console. Centralize the logs of routers and other network devices to get complete network visibility.
3. Traffic monitoring reports
Get predefined traffic monitoring reports providing information on allowed and denied connections. Use ML-based analytics to detect abnormal traffic patterns.
4. Performance bottleneck detection using correlation
Employ EventLog Analyzer's effective log analysis to identify performance bottlenecks by analyzing interface utilization, packet loss, and latency. By correlating these metrics with network events, you can pinpoint the root causes of performance issues and perform corrective actions, such as adjusting QoS settings or increasing bandwidth.
5. Router user activity analysis
Leverage the Incident Workbench to visualize the recent activity of suspicious users, including their last logon time, the configuration modifications they made, and their risk scores. Detect advanced persistent threats and insider threats as soon as possible with the seamless, easy-to-use security analytics module.











