Forensic analysis is important for understanding and preventing ransomware attacks. Understanding a ransomware attack requires a thorough investigation that must determine the attack's source, techniques and consequences. System logs, several memory dumps and all relevant registry entries have to be analyzed to determine the ransomware's method of network compromise and its subsequent actions. Ransomware Protection Plus' forensic analysis shows the attack's full extent after ransomware detection.
This in-depth ransomware investigation identifies Indicators of Compromise (IoCs), such as malicious file hashes and IP addresses. It also pinpoints unusual activity that vastly improves security defenses and prevention of future attacks result from understanding these IoCs. Ransomware forensic analysis helps us understand attackers' tactics, techniques and procedures (TTPs). These TTPs can be charted using frameworks such as MITRE ATT&CK®, helping you comprehend the attacker's behaviour and mitigate ransomware attacks.
Ransomware attack investigation
Our solution provides you with the detailed attack visibility via process tree. Map adversary behaviour using MITRE ATT&CK® identifier, giving you a comprehensive view of the attack chain, first source of infection and resolution status.
Ransomware attack investigation
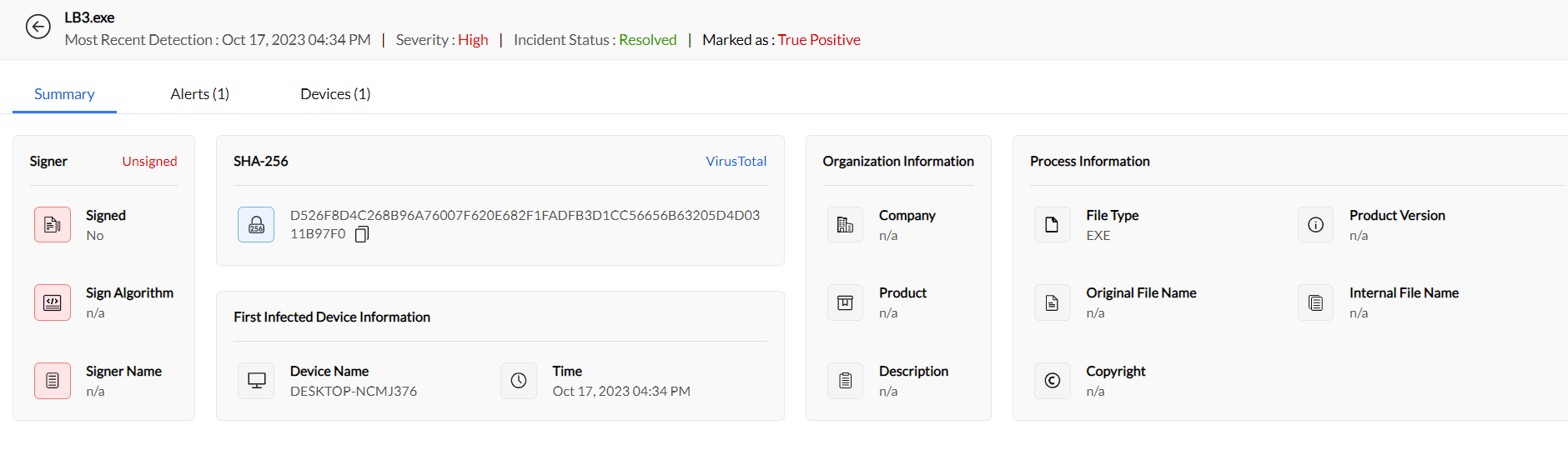
Discover your attack chain
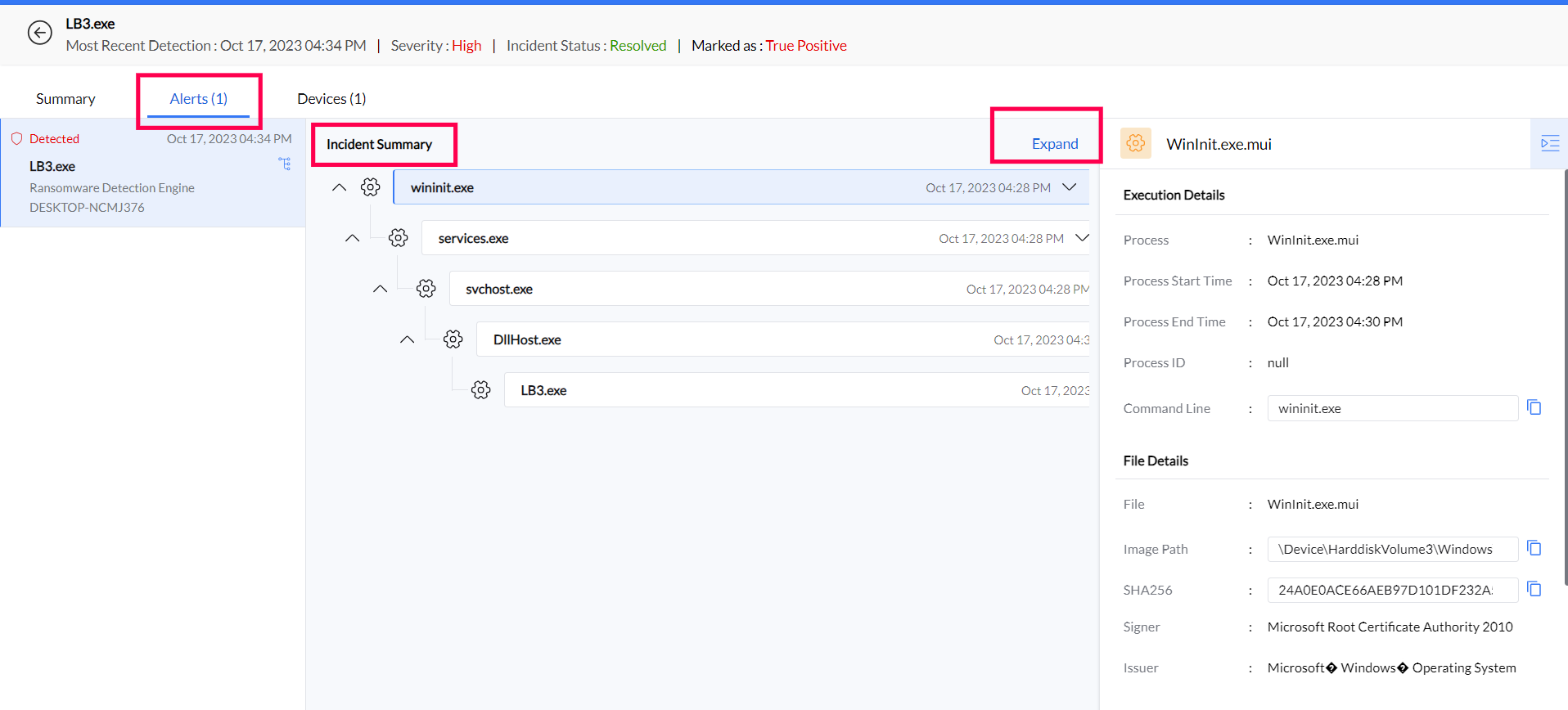
Examine how the attack unfolded by expanding the Incident Summary under the Alerts tab. Uncover child processes and command-line activity with detailed insights like SHA values and image paths at your fingertips.
Discover your attack chain
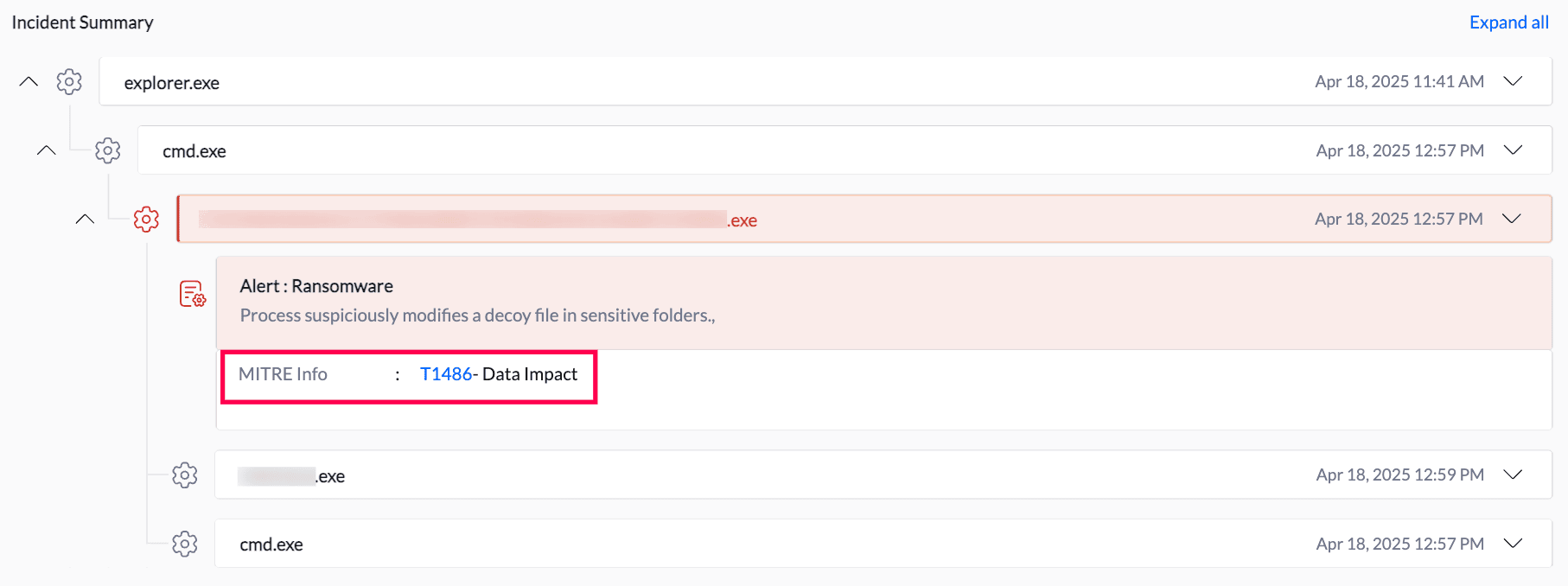
MITRE ATT&CK® Mapping
Quickly identify attacker tactics and techniques like Data Impact (in the example below) mapped directly to MITRE ATT&CK® for contextual threat understanding and better response.
Incident response acceleration
Supplement your incident response workflows with data-driven ransomware attack breakdown, enabling faster resolution and reducing the impact of ransomware attacks.
Post-Attack Forensics
Conduct in-depth ransomware forensic investigation using intelligence feeds to identify IoCs similar to known ransomware variants including the hashes of malicious files or URLs leveraged in malware distribution.
Real-time, cloud-based console
Gain visibility, comprehensive reporting and administrative capabilities from your web browser, allowing for centralized management and effective ransomware response strategies.
More on ransomware forensic investigation
01.What is ransomware forensic investigation?
+-Ransomware forensic investigation is the process of analyzing an attack to unravel how the ransomware infected the system and the scale of damage it caused. It involves tracing the infection path, identify Indicators of Compromise (IoCs), and understand attacker tactics, techniques, and procedures (TTPs).
Read more02.Why is it important to map/investigate ransomware attacks?
+-Mapping and investigating ransomware attacks is essential for identifying how the threat actor breached the system and the resulting impact on systems and business operations. This exercise enables organizations to improve their security posture and prevent recurring attacks.
Read more