TL;DR: Mitigate ransomware attacks with encryption prevention, decoy file monitoring and endpoint isolation to contain threats and limit attack exposure with Ransomware Protection Plus. Automatically neutralize a flagged incident (strict mode) or segregate incidents by marking it as true positive or false positive (audit mode).
Ransomware attacks have become sophisticated, posing significant threats to business continuity. Effective ransomware mitigation is essential to protect sensitive data and maintain operational productivity. Here are some key aspects of Ransomware Protection Plus when it comes to mitigating ransomware.
What mitigation features does Ransomware Protection Plus offer?
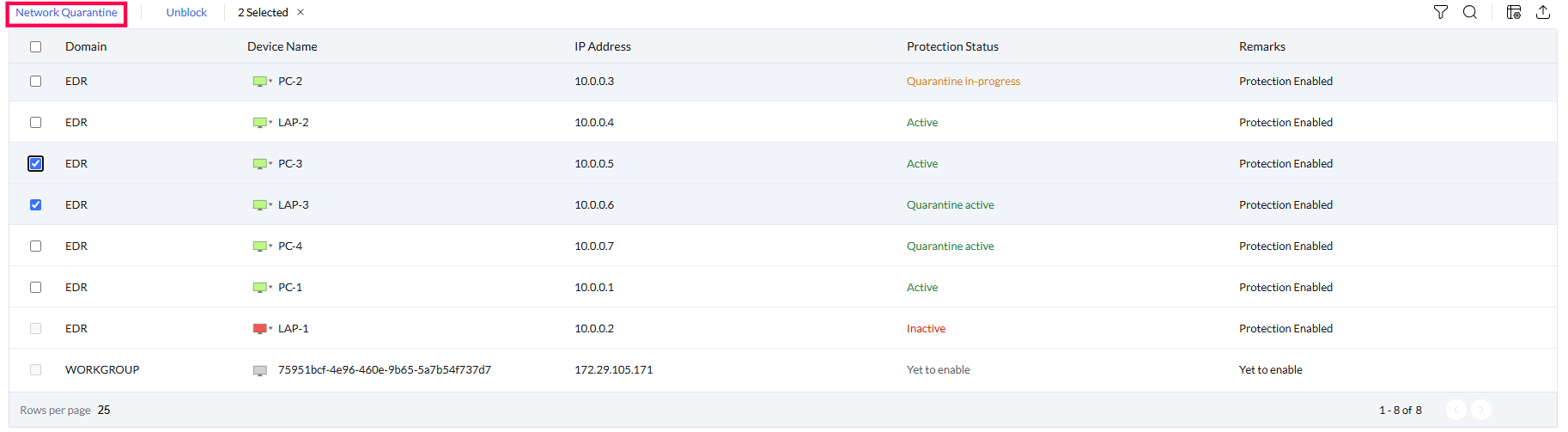
Infected device isolation
You can immediately isolate a device from the network when a device is suspected of being compromised. This would allow security analysts to segment the device and investigate the ransomware attack, while limiting the risk of attack spread.
Infected device isolation
Exploit protection
Safeguard against ransomware that relies on exploiting software vulnerabilities. Detect and prevent exploit attempts and subsequent compromise owing to ransomware attacks.
Rapid Response and Containment
Ransomware protection Plus can automatically respond and contain ransomware threats in real-time, terminating malicious processes and reverting unauthorized changes. This proactive approach ensures that ransomware is dealt with before it causes significant damage and downtime.
Anti-encryption
One of the primary goals of a ransomware is to encrypt data and demand for a ransom for its release. Our kernel-based anti-encryption technology prevents unauthorized encryption, blocking encryption attempts.
Process Monitoring
Our solution continuously monitors system processes, identifying suspicious activities such as mass encryption or unauthorized access to system files. This pre-emptive approach can thwart a ransomware attacker from executing its payload.
Repeat Offender Defense
With the rise of RaaS (Ransomwar-as-a-service), ransomware attacks often involve repeated attempts by the same malware strain. Ransomware Protection Plus has the intelligence to remember from previously encountered ransomware and its malicious behaviour. This ensures a fool-proof mechanism to prevent any future damage.
Decoy File Monitoring
Decoy files are strategically placed across all managed endpoints, acting as bait for an incoming ransomware. Once a file modification via a suspicious activity (like encryption) is detected, immediate alerts are triggered to notify administrators of potential ransomware attacks.
How Ransomware Protection Plus mitigates ransomware attacks?
Ransomware Protection Plus is a comprehensive ransomware mitigation solution that streamlines incident resolution. It allows IT teams to review and validate flagged incidents, spot false alarms, ensuring accurate, informed responses without disruption.
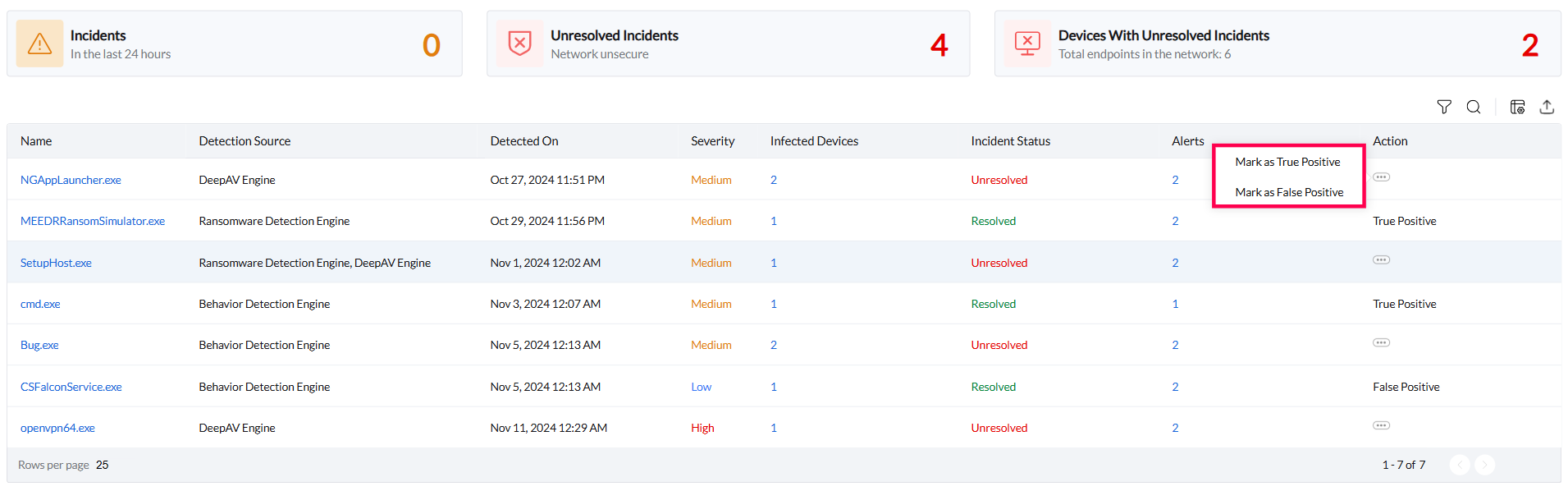
Incident management
To remediate an incident, head to the Incidents tab, find the flagged item, and mark it as either a true or false positive based on your assessment. Once the incident has been categorized, you’ll see follow-up options that help you take the appropriate next steps and fully resolve the issue.
Incident management
Post-detection ransomware neutralization
When an incident is marked as a True Positive, you can choose to kill the malicious process and its related activities, clean up any harmful files and system changes left behind, and roll back the system to its pre-infection state. Rollback not only removes the threat but also restores affected files and configurations, giving your IT team a clean slate. Incidents marked as false positives can be resolved by adding them to the exclusion list, preventing them from being flagged again in the future.
Post-detection ransomware neutralization

Frequently Asked Questions
01.What is ransomware mitigation?
+-Ransomware mitigation refers to the strategies and tools used to neutralize, contain and reduce the impact of ransomware attacks. It includes isolating affected systems, killing the ransomware strain and arresting further spread.
Read more02.Does ransomware mitigation work offline?
+-Yes, Ransomware Protection Plus works even offline.
Read more03.Why is it important to mitigate against ransomware?
+-Without effective mitigation, ransomware can encrypt critical data, disrupt operations, and cause financial/reputational harm. Effective mitigation helps maintain control over systems, reducing downtime.
Read more04.How does Ransomware Protection Plus support recovery and business continuity after an attack?
+-Ransomware Protection Plus use Microsoft VSS for recovery and file restoration using the last saved secure snapshot. It offers one-click rollback of data residing in encrypted/affected systems, ensuring end-to-end incident resolution and allows organizations to come back to business.
Read more