A vulnerability scanner is an advanced, automated tool designed to scan the endpoints in a network to detect software vulnerabilities, unauthorized open ports, misconfigurations, compliance issues, and other security loopholes. This tool is essential in identifying potential security threats and ensuring robust protection of the enterprise IT infrastructure.
A modern vulnerability scanner offers the following capabilities:
Based on their functionalities and architecture, vulnerability scanners can be classified into three different types:
For organizations looking to try out a vulnerability scanner to proactively identify and remediate security weaknesses, ManageEngine Vulnerability Manager Plus, with its free edition can be the ideal solution, pre-implementation.
This free vulnerability scanning tool offers an advanced set of capabilities free of charge for up to 25 devices with a single technician to manage the endpoints.
Below we cover:
Traditional vulnerability scanners that can only detect vulnerabilities without offering any mitigation often fail to provide holistic security for the network. Here are the limitations of traditional vulnerability assessment tools:
Scanning for vulnerabilities, system misconfigurations and other security loopholes in the network isn't enough, if those aren't mitigated promptly. This is where Vulnerability Manager Plus stands out. By leveraging the agents installed in the systems, this solution combines vulnerability scanning, patch deployment, security configuration management, and other mitigation strategies together into a single console. This shortens the time taken to detect and remediate vulnerabilities and misconfigurations.
With Vulnerability Manager Plus, you only need one tool and one agent to manage all your system vulnerabilities. This means it's easy to use in changing environments and you don't have to waste time scanning multiple times for the same issues. The tool automatically gathers all the important information and helps you quickly fix any problems.
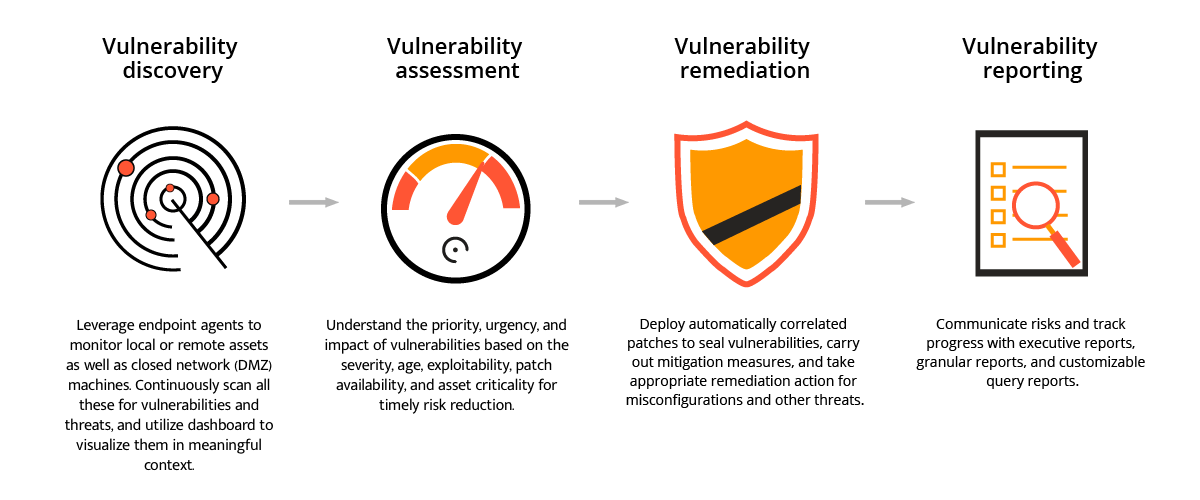
Eliminating blind spots is the basis of successful vulnerability management. To achieve this, Vulnerability Manager Plus:
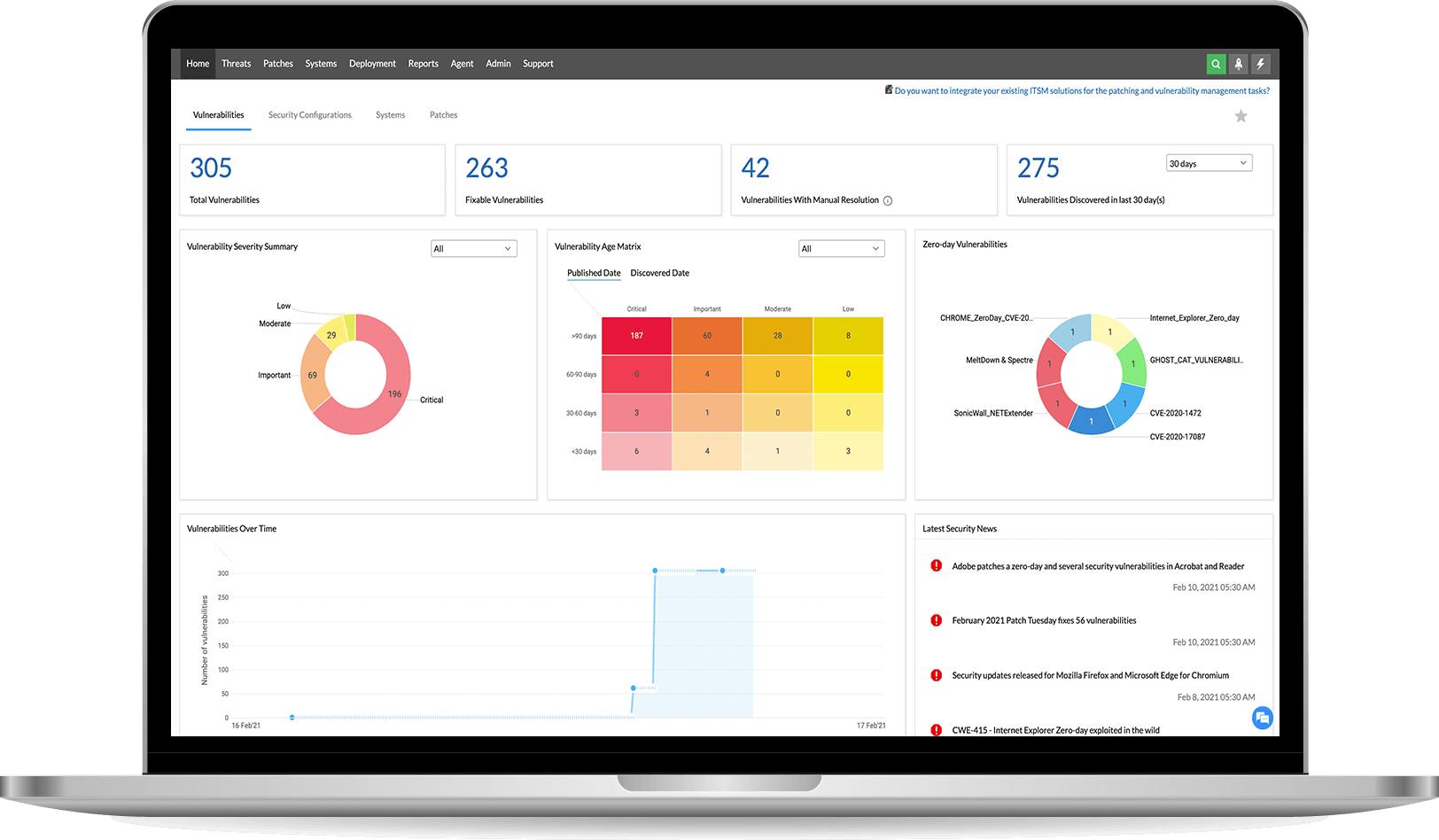
Are you overwhelmed with a flood of security scan data? With Vulnerability Manager Plus, you can easily see how secure your organization is overall, and which areas need the most attention. It's all presented in easy-to-understand dashboards, so you don't have to be a security expert to make sense of it.
Visualize, analyze, and prioritize your response to exploitable and impactful vulnerabilities based on:
Learn more about the importance and benefits of risk-based vulnerability management over traditional vulnerability management.
Our system has a feature that helps you fix security problems quickly and easily. It can automatically identify which problems are most important and suggest patches to fix them. You can also set up automatic updates to keep your system safe without needing to manually manage it. Additionally, you can use the system to configure security settings and remove risky software from all your devices at once. This means you can focus on other things while our system takes care of keeping your devices secure.
To keep your computer network secure, it's important to regularly check for and fix any weaknesses. But it's also important to keep track of how you're doing! That's where Vulnerability Manager Plus comes in - it has lots of different reports that show you how your network security is improving over time. You can choose different types of reports, like ones that show lots of details or ones that are easy to understand. You can even set it up so the reports are sent directly to important people in your organization, without you having to do anything!
Scan and secure your endpoints now with 30 days of free, unlimited access.
Get a personalized demoTry for freeBelow is a detailed breakdown of how Vulnerability Manager Plus works:
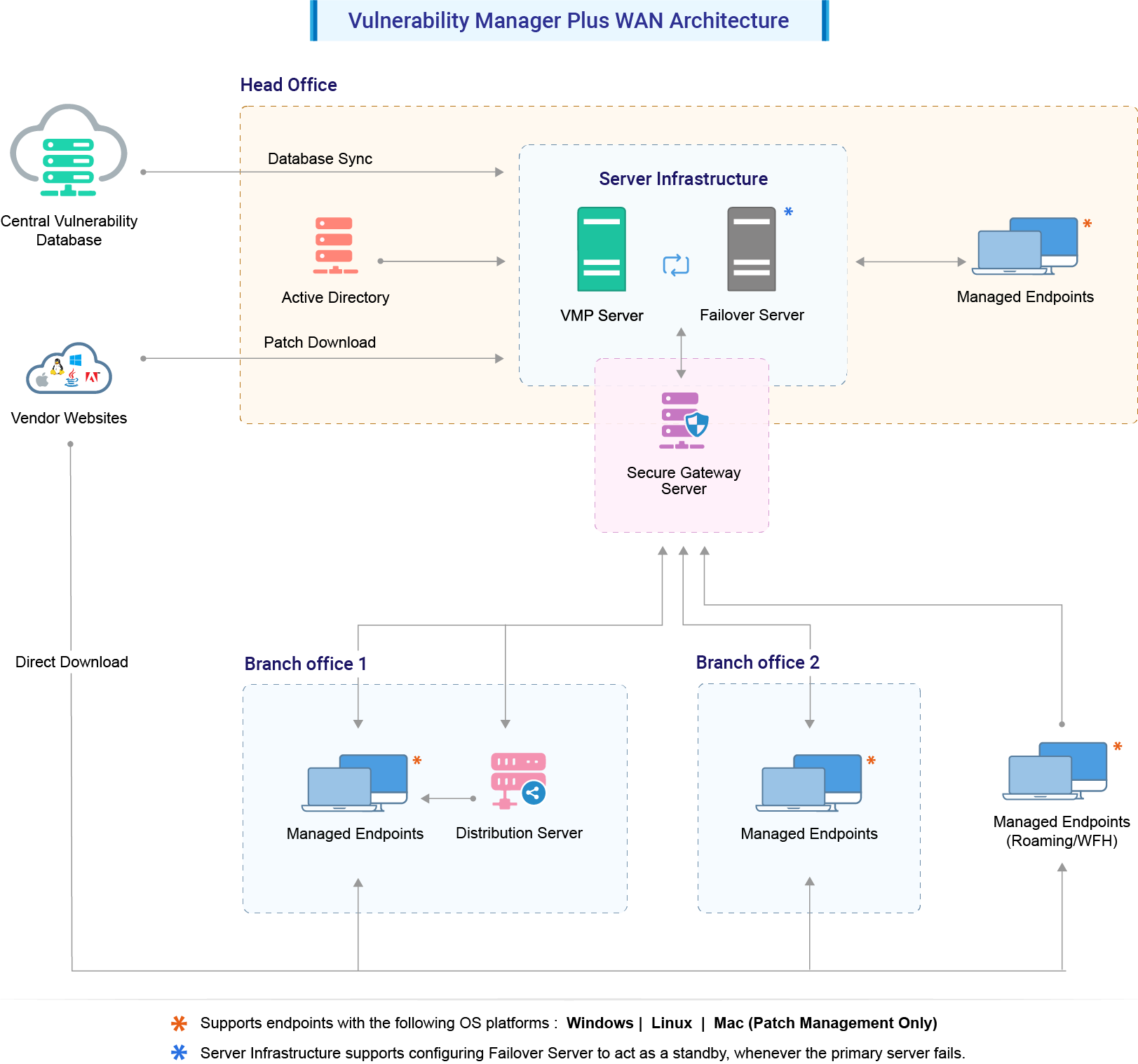
Don't worry if some harmful elements find their way into your business despite your best efforts, as ManageEngine's Vulnerability Manager Plus has you covered. This software comes with a wide range of features to help you manage security and system misconfigurations, keeping all kinds of threats away from your enterprise.
Vulnerabilities are weaknesses in software that hackers can use to access sensitive information or cause damage to an organization. People who care about security are always looking for these weaknesses and give them a special name and score. The company that made the software gets a certain amount of time to fix the problem before the public finds out about it. Once the weakness is known, anyone can try to use it to hack into your system. Unfortunately, some people might not follow the rules and will tell others about the weakness before the company can fix it. If your organization uses software with a weakness, you could be in trouble.
Vulnerability scanning is a security process that checks your computer systems to find any weaknesses or vulnerabilities that could be used by hackers to gain unauthorized access. It's like a thorough check-up for your network and software, where any potential security risks are identified and reported back to you so that you can take action to fix them. This helps to protect your organization's digital assets and ensures that sensitive information remains secure.
A vulnerability scanner is a tool that helps IT administrators check all the computers and devices in a company to find any weaknesses or risks that could cause security problems. It's like a security guard that looks for potential dangers and alerts the team to fix them before anything bad happens.
It's important for organizations to be aware of potential security weaknesses in their computer systems, even if they have software updates available to fix them. If these weaknesses are not addressed, they can be exploited by attackers and lead to serious problems like data leaks or financial losses.
To create a secure environment, it's essential to stay informed about these vulnerabilities and take steps to fix them. By using a vulnerability scanner tool, organizations can quickly find and fix these weaknesses, which can help protect against attacks and keep sensitive information safe.
Vulnerability scanners and antivirus software are both crucial for maintaining cybersecurity, but they serve different purposes and function in distinct ways.
A vulnerability scanner is a tool that systematically examines the endpoints in the network to identify security weaknesses, such as software vulnerabilities, misconfigurations, and open ports. It helps organizations proactively address potential security risks before they can be exploited by attackers.
In contrast, antivirus software is designed to detect, prevent, and remove malicious software, including viruses, worms, and trojans. It operates by scanning files and system memory for known malware signatures and behaviors. These provide real-time protection, ensuring any detected threats are immediately quarantined or removed to prevent infection.
To summarize, while vulnerability scanners focus on identifying security gaps to prevent potential attacks, antivirus software aims to detect and neutralize active threats.
Vulnerability scanning is a critical aspect of cybersecurity, but it faces several challenges that can impact its efficiency and accuracy. Here are some of them:
Effectively addressing these challenges is crucial for maintaining a robust cybersecurity posture and protecting organizational assets from potential threats.
Implementing a vulnerability scanner such as ManageEngine Vulnerability Manager Plus offers a comprehensive solution for organizations aiming to enhance their cybersecurity posture. Here are some of its benefits:
To find the best tool for scanning your organization's vulnerabilities, you need to consider things like how it works, how much it can handle, how much it costs, and what features you need. By looking at these factors, you can find the ideal tool that fits your organization's needs.
ManageEngine Vulnerability Manager Plus offers an advanced set of features including but not limited to automated detection of vulnerabilities and missing patches, security and web server misconfigurations, port audit, vulnerability mitigation for network devices, and so on.
This free vulnerability scanner is available free of charge for up to 25 endpoints. To know more about it, check out the features of the free edition.
Agents are lightweight software packages installed into the endpoints. These agents can offer continual scanning and monitoring of the endpoints in the network when compared to agent-less solutions. Moreover, agent-based scanners have minimum impact on the network since the scans can be pre-scheduled.
Another major benefit of agent-based vulnerability scanners is that they can offer vulnerability scans for systems in air-gapped networks as well as BYOD systems.