Thank You!
You can click and start reading the chapters from below. We've also sent the
link to your inbox for future reference.
D'après IBM Security, le coût moyen d'une violation de données en 2021 a augmenté à
4,24 millions de dollarsLes entreprises étant de plus en plus nombreuses à développer leurs activités en ligne, il est devenu impératif de protéger les applications et les serveurs web contre les cybermenaces. En exploitant les vulnérabilités de ces serveurs et applications, les pirates peuvent facilement accéder à des données sensibles et entraîner de graves conséquences financières.
Dans ce guide, nous avons abordé certains des types de cyberattaques les plus courants sur les serveurs web et la manière dont vous pouvez les détecter en analysant vos journaux.
Introduction
The Verizon 2021 Data Breach Investigations Report analyzed 29,207 security incidents, of which 5,258 were confirmed breaches (a significant increase from the 3,950 breaches analyzed in last year’s report). If we look deeper into the breach pattern, of the top assets that were exploited, web servers constituted more than 60%. Web servers were one of the main attack vectors, contributing to 80% of the breaches detected and reported last year.1
As you may already know, web servers face a multitude of threats, such as brute-force attacks, SQL injection attacks, cross-site scripting, and denial-of-service (DoS) attacks. A single successful attack can severely affect an organization's reputation, cause substantial financial loss, and undermine customers' trust. Enterprises need to stay one step ahead to avoid being the next victim.
So how do we detect these attacks before it is too late?
Log analysis can provide a lot of insights on what is going on in your network.
How log analysis can help detect web attacks
Every event that occurs in a network is recorded in the form of logs. These logs provide detailed information about the event, such as the time of occurrence, where it occurred from, as well as who was behind it. Analyzing these logs can provide insights on the activity and help you detect the warning signs of cyberattacks and threats in your network. If you are a security admin, we recommend you look for actionable insights in your log data to detect and stop attacks before the damage is done.
This guide elaborates on some of the most popular web attacks and includes tips on how you can detect them by analyzing your web server logs.
Basics of web
server log analysis
First, let’s go through the basics of log analysis. Web server logs provide valuable information related to traffic—who sent the request, the date and time at which the request was sent, and what the requested file was.
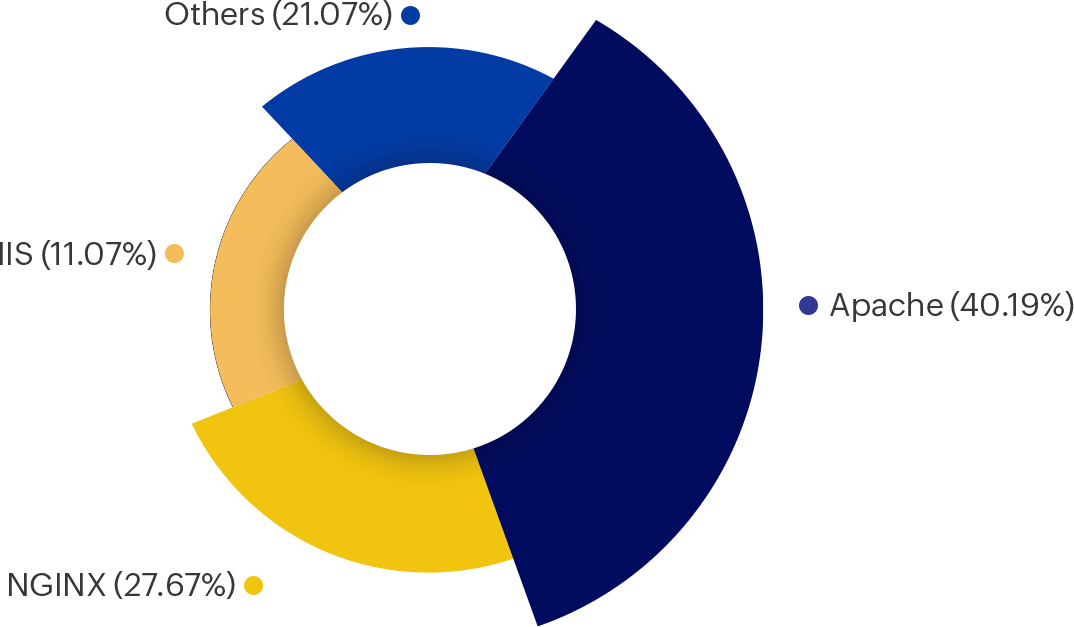
Some of the most common web servers used in today's world include Apache, IIS, and NGINX. Each web server's log format differs from one another.
Apache’s web server, officially known as the Apache HTTP Server, is the most popular web server in the market, with a market share of 40.19% as of March 2022.2
Apache web servers generate two different types of logs.
1. Access logs: They contain information regarding all the requests processed by the server.
2. Error logs: They contain information regarding errors that are encountered while processing requests.
In this resource, we will be analyzing Apache web servers' access log files.
Two commonly used log formats for Apache access logs are the Common Log Format and the Combined Log Format.
Common Log Format
Log entries written in the Common Log Format look like:
127.0.0.1127.0.0.1This denotes the IP address of the client that sent the request to the web server.-Hyphen (-)This denotes that the requested piece of information is unavailable. In the above log file, the missing information happens to be the RFC 1413 identity of the client.frankFrankThis field indicates the username of the person who made the request.[10/Oct/2000:13:55:36 -0700][10/Oct/2000:13:55:36 -0700]This field denotes the date and time at which the request reached the server. It follows the format day/month/year:hour:minute:second.
"GET /apache_pb.gif HTTP/1.0""GET /apache_pb.gif HTTP/1.0"GET refers to the HTTP method used by the client. /apache._pb.gif refers to the document that was requested by the client. HTTP/1.0 refers to the protocol used by the client, and its version.200200This indicates the HTTP status code that the server returns to the client.23262326 This denotes the size of the object returned to the client. It is measured in bytes.
Understanding HTTP response status codes
The following table denotes the various HTTP response status codes that can be returned by the server.
| Response code | Meaning |
|---|---|
| 1xx | Informational |
| 2xx | Successful |
| 3xx | Redirection |
| 4xx | Client error |
| 5xx | Server error |
Combined Log Format
Log entries written in the Combined Log Format look like:
127.0.0.1 - frank [10/Oct/2000:13:55:36 -0700]
"GET /apache_pb.gif HTTP/1.0" 200 2326
"http://www.example.com/start.html""http://www.example.com/start.html" This refers to the HTTP referrer, and it denotes the address of the page where the request was executed."Mozilla/4.08 [en] (Win98; I ;Nav)""Mozilla/4.08 [en] (Win98; I ;Nav)" This denotes the user agent. It refers to the web client that sent the request.
This log format is very similar to the Common Log Format except for the two additional fields at the end of the message.
Common web server
attacks
Some of the most popular cyberattacks in today's world include brute-force attacks, SQL injection, and DoS attacks.
Take a look at these alarming stats:
- According to the Cisco Annual Internet Report (2018-2023), the total number of DDoS attacks will increase from 12.1 million in 2021 to 15.4 million in 2023 globally.3
- Akamai observed 6.3 billion web attacks worldwide during 2020. SQL injection was found to be the top web attack vector. 4
- Based on new findings, Kaspersky has stated that in 63% of cyberattacks investigated by the Kaspersky Global Emergency Response team, password brute force and vulnerability exploitation were used as initial vectors to compromise an organization’s environment.5
In this resource, we are going to explore each of these attacks, along with techniques to detect them in their early stages.
Brute force
attacks
In a brute-force attack, hackers try to guess the login credentials of a user using the trial-and-error method. Brute-force attacks are more common in public-facing, aka internet-facing, systems. Therefore, any website or application's login form is likely to be the target of a brute-force attack. Attackers use a bot or script to try out different combinations of usernames and passwords until they crack open the account. Apart from usernames and passwords, attackers also try to guess passphrases, emails, links, or directories and find hidden webpages. By exploiting hidden webpages, they can gain access to the primary website.
Although time-consuming, brute-force attacks are still very popular and have a high rate of success.
Some common tools used for brute-force attacks include THC Hydra, Aircrack-ng, John the Ripper, and Hashcat.

Repercussions of a brute-force attack
If attackers gain access to a password-protected account (especially an administrative account), they can:
- Deface the website.
- Exploit vulnerabilities.
- Inject malware.
- Insert spam links and damage SEO rankings.
- Retrieve sensitive information and publish or sell it.
- Execute another attack or shut down the targeted website.
- Redirect users to malicious websites.
Detecting brute-force attacks
What your logs can tell you
Check your logs for the following red flags:
- Multiple requests within a very short period of time
- Multiple requests with the same username and IP address but a different password for each request
- Multiple requests with the same IP address but different usernames and passwords
- Multiple requests with different IP addresses targeting the same user account
- A suspicious user agent or referrer
- Excessive bandwidth consumption during a single session
- A large number of requests where authentication has failed
A sample brute-force attack
127.0.0.1 - - [10/Oct/2000:13:55:36 -0700] "GET /sample.com/?username=administrator&password=abcde&Login=Login HTTP/1.0" 200 2326 "http://www.sampleexample.com/start.html" "Mozilla/4.08 [en] (Win98; I ;Nav)"
127.0.0.1 - - [10/Oct/2000:13:55:37 -0700] "GET /sample.com/?username=administrator&password=12345&Login=Login HTTP/1.0" 200 2326 "http://www.sampleexample.com/start.html" "Mozilla/4.08 [en] (Win98; I ;Nav)"
127.0.0.1 - - [10/Oct/2000:13:55:38 -0700] "GET /sample.com/?username=administrator&password=admin&Login=Login HTTP/1.0" 200 2326 "http://www.sampleexample.com/start.html" "Mozilla/4.08 [en] (Win98; I ;Nav)"
127.0.0.1 - - [10/Oct/2000:13:55:39 -0700] "GET /sample.com/?username=administrator&password=abc123&Login=Login HTTP/1.0" 200 2326 "http://www.sampleexample.com/start.html" "Mozilla/4.08 [en] (Win98; I ;Nav)"
127.0.0.1 - - [10/Oct/2000:13:55:40 -0700] "GET /sample.com/?username=administrator&password=admin123&Login=Login HTTP/1.0" 200 2326 "http://www.sampleexample.com/start.html" "Mozilla/4.08 [en] (Win98; I ;Nav)"
Source: Cybrary
In the above sample, you can see that the attacker (with the same IP address in each request) is targeting the administrator account's password.
Expert's tips to prevent brute-force attacks
- Weak passwords are easy to crack. Enforce long, complex passwords. They are almost impossible to crack as more combinations have to be tested, which requires additional time and computation power. It takes over 359,000 years to crack a password that has 13 characters.
- Avoid reusing passwords across websites.
- Limit the number of login attempts that users can make in a specified time frame.
- Enable CAPTCHA to prevent bots and automated tools.
- Implement additional layers of security such as multi-factor authentication and enforce account lockouts.
- Utilize data obfuscation.
Our recommendation:
Implement a security information and event management (SIEM) solution that:
- Scans logon events on critical servers and workstations. For example, if a device experiences multiple failed logons within a short span of time, the solution's event correlation engine must recognize the attack pattern and raise an alert immediately. It should also create an incident report with details about the breached device and logon events.
- Allows you to navigate a detailed timeline of events for each detected incident, and drill down to the raw log contents to get in-depth information on compromised accounts, infected devices, and more.
- Leverages user entity and behavior analytics (UEBA) to spot anomalous activities, such as multiple failed login attempts, account compromise, and data exfiltration attempts, and investigates them to detect attacks in their early stages.
- Tracks critical activity such as account lockouts, privilege abuse, and unauthorized copying of sensitive data using pre-defined reports. If a suspicious event is detected, an alert notification must be sent immediately via email or SMS.
SQL injection attacks
The SQL injection technique refers to the insertion of SQL queries in the input fields of web application forms that accept inputs without validating them. Instead of entering the expected input, attackers enter (or inject) an SQL query to bypass authentication and access or modify the contents of the underlying database. In spite of being one of the oldest attack types, it is still very popular and dangerous.
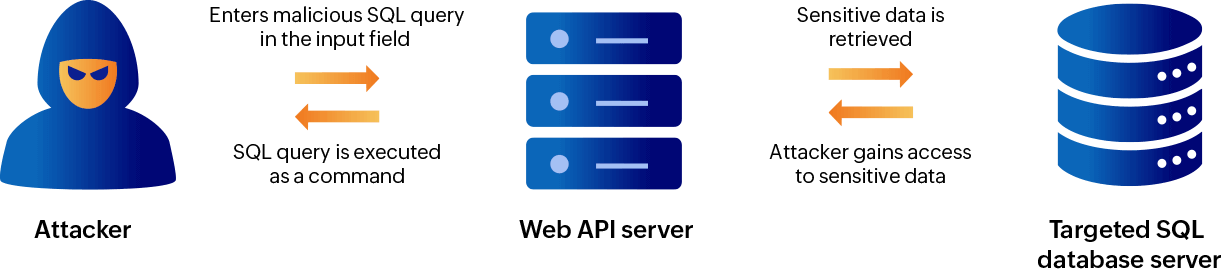
Repercussions of a SQL injection attack
If the attack is successful, it can lead to:
- Attackers gaining access to the sensitive data stored in databases, such as personally identifiable information.
- Manipulation or deletion of the contents stored on the database server.
- Website defacement.
- Privilege escalation.
Detecting SQL injection attacks
What your logs can tell you
Check your logs for the following red flags:
- SQL commands: SELECT, FROM, WHERE, UNION, AND, and more
- Vulnerability scanners such as sqlmap
- Commands related to the operating system, such as exec, cat, and more.
- Many encoded characters (such as %)
Also, try correlating multiple log files to understand how the attack unfolds.
A sample SQL injection attack:
127.0.0.1 - - [10/Oct/2000:13:55:36 -0700] "GET /sample.com/?id=a%27+or+1%3D1&Submit=Submit HTTP/1.0" 200 2326 "http://www.sampleexample.com/?id=1&Submit=Submit" "Mozilla/4.08 [en] (Win98; I ;Nav)"
Source: Cybrary
In the above sample, you can see the command a' or 1 = 1 being used.
Without the encoded characters, the above log file will look like:
127.0.0.1 - - [10/Oct/2000:13:55:36 -0700] "GET /sample.com/?id=a'+or+1=1&Submit=Submit HTTP/1.0" 200 2326 "http://www.sampleexample.com/?id=1&Submit=Submit" "Mozilla/4.08 [en] (Win98; I ;Nav)"
Source: Cybrary
Here's another example.
A sample SQL injection attack:
127.0.0.1 - - [10/Oct/2000:13:55:36 -0700] "GET /sample.com/?id=%28SELECT%20%28CASE%20WHEN%20%281450%3D2167%29%20THEN%20%27%27%20ELSE%20%28SELECT%202167%20UNION%20SELECT%201463%29%20END%29%29 HTTP/1.1" 302 20 "-" sqlmap/1.3.6#stable (http://sqlmap.org)"
Source: Cybrary
In the above sample, you can see they’re using SQL commands, encoded characters, as well as the vulnerability scanner sqlmap.
Without the encoded characters, the above log file will look like:
127.0.0.1 - - [10/Oct/2000:13:55:36 -0700] "GET /sample.com/?id=(SELECT (CASE WHEN (1450=2167) THEN " ELSE (SELECT 2167 UNION SELECT 1463) END)) HTTP/1.1" 302 20 "-" sqlmap/1.3.6#stable (http://sqlmap.org)"
Source: Cybrary
Expert's tips to prevent SQL injection attacks
- Sanitize the inputs provided by the user. Validate the data entered and make sure it matches the type of data that is expected.
- Ensure that all the software components of the web application are updated to the latest patches.
- Limit the privileges of the database. This can be done by implementing Zero Trust architecture. The core principle of Zero Trust is "Never trust, always verify." Any user, application, or device will not be granted access unless it has been thoroughly audited and verified. The principle of least privilege (PoLP) is an important component of the Zero Trust security model. Implementing PoLP ensures that an account only has enough access to perform its responsibilities, which prevents an attacker from gaining access to sensitive data if they compromise the account.
- Do not display database error messages on the client's web browser as attackers can use these to their advantage.
- Discover vulnerabilities in your web application and remediate them.
- Use parameterized queries and prepared statements.
- Implement a web application firewall (WAF). A WAF acts like a barrier in front of the web server by monitoring incoming and outgoing traffic, and blocking requests that seem to contain malicious SQL code.
Our recommendation
Implement a SIEM solution that:
- Audits activities on your SQL or Oracle databases and IIS or Apache web servers with prepackaged reports and generates instant alerts regarding any event that poses a threat to security.
- Correlates SQL audit logs with information collected from other event sources to detect data breach attempts at an early stage. The SIEM solution must also provide out-of-the-box SQL injection correlation rules for various attack patterns.
- Provides detailed reports on SQL injection to help you conduct detailed forensic analysis on how the attack happened.
DOS Attacks
Is the website you are trying to access down?
It could be because of an ongoing DoS attack. In a DoS attack, the attacker's goal is to flood a target web server with superfluous requests, exhaust its resources and trigger it to crash so it becomes inaccessible to its intended users. When the targeted web server is bombarded with too much traffic in a short span of time, it becomes overloaded and is unable to process requests coming from legitimate users. Healthcare and education sectors are the most affected by this type of attack as business downtime is very costly in these industries. The education sector saw a 41% increase in DDoS attacks between July 2020 and March 2021.6
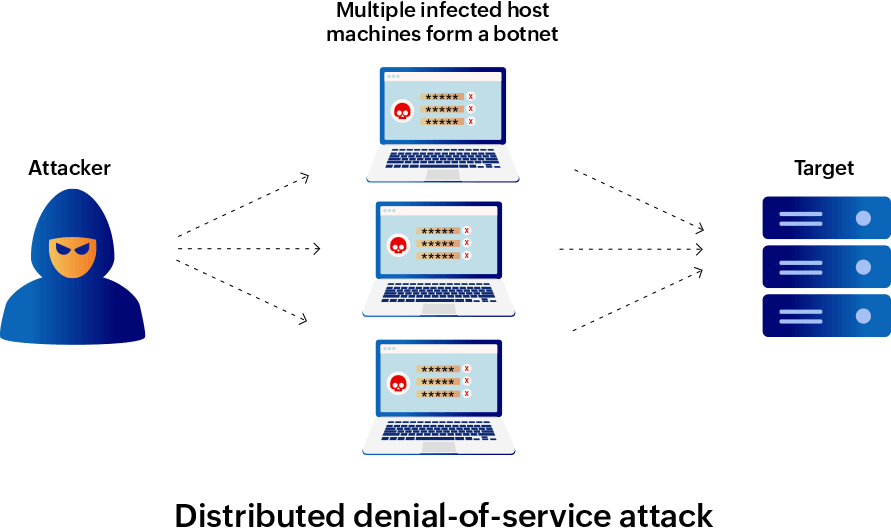
What is the difference between a DoS attack and a DDoS attack?
The DoS attack technique uses one malicious source that floods the web server with a massive amount of requests.
On the other hand, in a DDoS attack, multiple malicious sources that operate together attack a single target simultaneously. These multiple host machines are known as bots or zombie systems. Together, they form a botnet that is used to perform large-scale attacks by cybercriminals. The real owners of these compromised systems might not even know that their system is acting as a bot as the system continues to function normally. Since superfluous requests in a DDoS attack are coming from multiple locations, the exact origin of the attack is disguised, making it challenging to detect and stop it.
A DDoS attack has the potential to cause serious financial ramifications to small and large enterprises. It is a huge threat to businesses, nonprofit organizations, and governments around the world. Imagine a large-scale attack that prevents customers from accessing an e-commerce platform. It could lead to a loss of millions of dollars for the enterprise running the business.7 And once a business has been under attack, there is an 82% chance that it will be attacked again.8
With the surge in the usage of IoT devices, DDoS attacks have become more and more prominent. Sometimes cybercriminals also employ DDoS as a distraction tactic while executing other serious cyberattacks.
Detecting DoS and DDoS attacks
The best preventive method you can take for a DoS or DDoS attack is to continuously monitor and analyze your network.
What your logs can tell you
Check your logs for the following red flags:
You have hundreds of logs where:
- The server is returning a 503 Service Unavailable HTTP response code intermittently or permanently. This response code indicates that the server is down.
- The server is returning a 404 Not Found HTTP response code. This indicates that the server was not able to respond to the request.
- The same IP address is trying to establish a connection with different ports, and the connection state is TIME_WAIT.
Monitoring a 404 response code would be a much better choice compared to tracking a 503 response code as the latter indicates that the server is already down and the threat cannot be prevented.9
To find out if your server is under attack, you can open the Windows Command Prompt and execute the following command to view the list of active connections along with their connection state.10

Expert's tips to prevent DoS and DDoS attacks
Continuously monitor your network traffic for unexpected surges. Analyzing the origin and type of traffic can provide additional insights. Most attackers will test your network defenses before executing a full-fledged attack. Look for unusual data traffic coming from suspicious IP addresses or geographic locations.
Our recommendation
Implement a SIEM solution that:
- Audits log data from your network security devices such as firewalls, IDSs, and IPSs and instantly detects DoS or DDoS attacks in real time.
- Tracks web server activity and detects recurring connection requests from any specific IP or location.
- Uses predefined reports and alerts specifically designed to detect DoS attacks.
About Log360
Manually monitoring and analyzing terabytes of log data on a daily basis is impossible. A SIEM solution automates the entire process of collecting log files from various network devices, parsing them, and analyzing them to provide valuable insights to the security team. By auditing web server activity, a SIEM solution can instantly detect any attack and alert you in real time.
ManageEngine Log360, a unified SIEM solution with integrated DLP and CASB capabilities, thoroughly audits IIS and Apache web server logs and provides actionable insights through predefined reports and alert profiles. Its real-time correlation engine and threat intelligence platform can help enterprises detect data breaches in real time. Log360's graphical reports will give you detailed information regarding important events taking place in your web server, such as failed authentication or bad URL requests. You can receive instant alerts for events that pose a threat to security. This is how a SIEM solution like Log360 helps you reduce the time it takes to detect and respond to threats.