What is identity life cycle management?

Identity life cycle management involves the comprehensive management of digital identities within an organization, encompassing humans (employees, contractors, partners, customers) and machines (servers, applications, devices) from their creation to revocation. It aims to maintain appropriate access levels, ensuring security and compliance through provisioning, access management, authentication, deprovisioning, and continuous monitoring and auditing.
What is a digital identity?
A digital identity serves as an online representation of an individual, organization, entity, or machine, encompassing personal or machine-specific information used for authentication, verification, and managing interactions and transactions.
For machines, this identity is crucial for secure communication and operations within IT ecosystems, enhancing security and privacy by ensuring that only authorized machines and individuals can initiate and complete procedures and facilitate access to online services.
What is an identity life cycle?
Identity life cycle refers to the various stages that an identity or user account undergoes during its existence within an organization or system. This encompasses creation, maintenance, termination, and any changes throughout its life span. Managed by an identity and access management (IAM) system, it ensures proper provisioning, management, and deprovisioning according to organizational policies and security requirements, involving processes like authentication, authorization, and auditing to monitor identity integrity and security.
Why is identity life cycle management required?
Identity life cycle management is indispensable for several reasons in the realm of information technology and cybersecurity.
- Efficient onboarding and offboarding: Improve the efficiency of onboarding and offboarding processes, reducing the risk of unauthorized access after termination.
- Access control and compliance: Ensure appropriate access privileges based on roles and duties while aligning them with regulatory guidelines to maintain compliance.
- Security: Improve security by effectively managing user accounts to prevent unauthorized access and breaches. Proactively address risks, identify vulnerabilities, monitor activity, and respond to incidents.
- User experience: Ensure a positive user experience by granting appropriate access levels and preventing delays and complications.
- Adaptability to change: Provide a framework for managing organizational changes and adjust access rights according to evolving organization and workforce needs.
What is the identity life cycle management process?
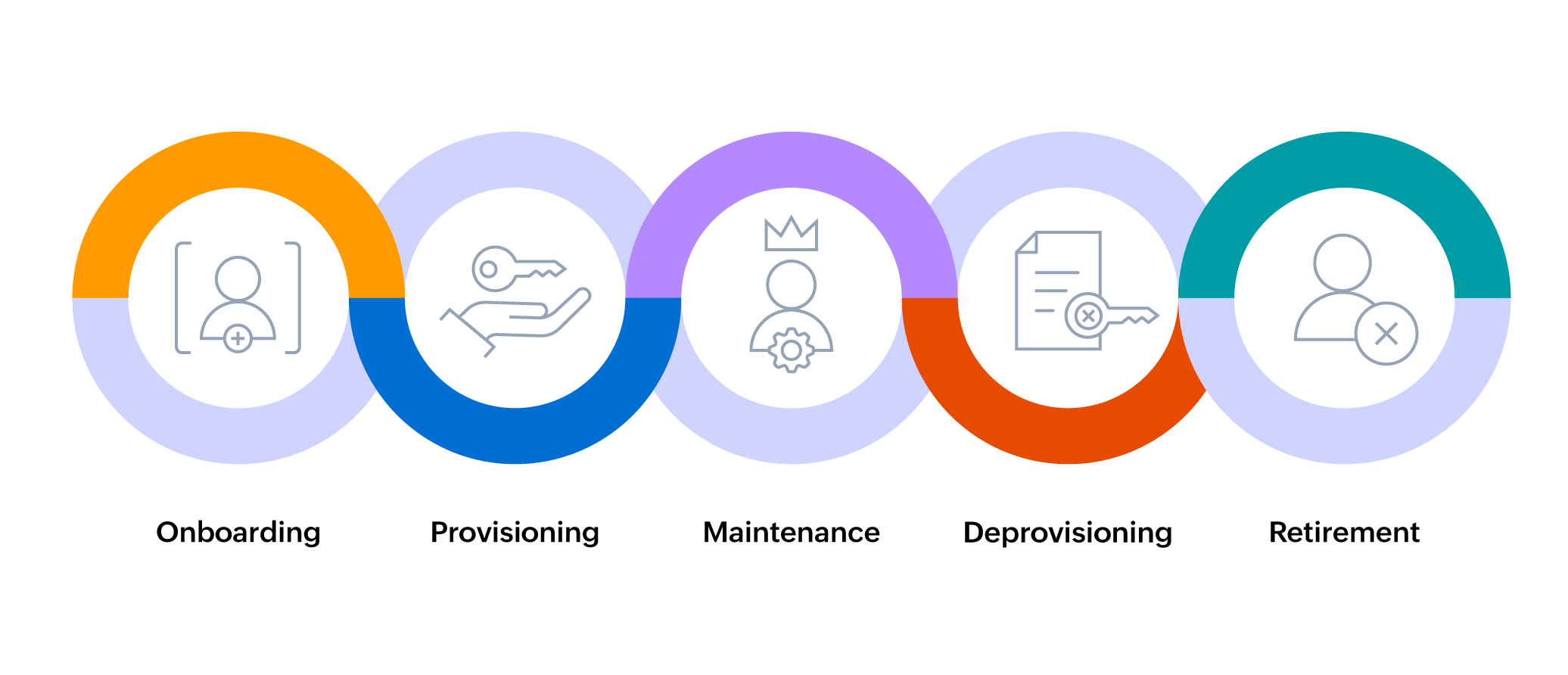
The main focus of identity life cycle management is to oversee all the processes and steps related to identity and access, with the goal of safeguarding both the user and organizational resources.
The primary process of identity life cycle management includes the following stages:
- Onboarding: Creating a new digital identity and setting up access to resources for new users and verifying identities.
- Provisioning: Granting access to specific systems and resources based on user roles and responsibilities within the organization.
- Maintenance: Ongoing management of user accounts and access privileges, including updates and compliance checks.
- Deprovisioning: Revoking access privileges when a user leaves the organization or changes roles.
- Retirement: Permanently deleting or archiving a user’s account, typically after a period of inactivity or when no longer associated with the organization.
Identity life cycle management for external and guest identities
Managing external and guest identities is crucial in the identity life cycle process for many organizations. This is often challenging due to contractors, seasonal workers, and partner/vendor identities. It is crucial to incorporate these external identities into the organization in order to facilitate seamless collaboration and simplify access management.
The process of identity life cycle management for external and guest identities is comparable to that of internal employees, but a notable distinction is the requirement of an identity suspension capability in the directory system. This is because external identities are frequently revoked or created compared to internal ones.
Implementing an identity suspension function in the directory system is vital for efficient management. It allows IT to suspend an identity easily, automatically revoking access until the suspension is lifted. This streamlined approach significantly improves the overall management of external and guest identities within the organization, addressing the unique challenges posed by their frequent changes.
Identity life cycle management challenges
Managing identity life cycles is not always straightforward. Workflows may lack documentation or flexibility, tools may not meet necessary requirements, and team members might be overwhelmed, leading to oversights. Organizations encounter several challenges with identity life cycle management, like:
Inefficient onboarding and access assignment
New users require timely access to resources, but manual workflows and conflicting priorities between human resources and IT can delay this process, hampering productivity and the employee experience.
Management of external users
Contractors and seasonal employees need identity and access management, which can be complicated when they are not integrated into the human resources system, leading to communication gaps and security risks.
Adjusting permissions with role changes
Adjusting permissions for employees changing roles is essential to maintain productivity and security. However, without proper identity life cycle management, employees may retain unnecessary access, leading to privilege creep.
Streamline IT tasks
Manually managing identities, access, and addressing requests consumes IT resources, leaving little time for other critical tasks. Automation through modern identity life cycle management tools can alleviate this burden.
Secure offboarding
Improper offboarding poses security risks, as ex-employees may retain access to company resources due to human error or communication gaps in departments.
Addressing these challenges requires implementing modern identity life cycle management tools that can streamline workflows, automate processes, and integrate with an organization’s existing business tools and tech stack. These tools can streamline workflows, enhance security, and improve overall efficiency organization-wide.
Benefits of employing an identity life cycle management solution
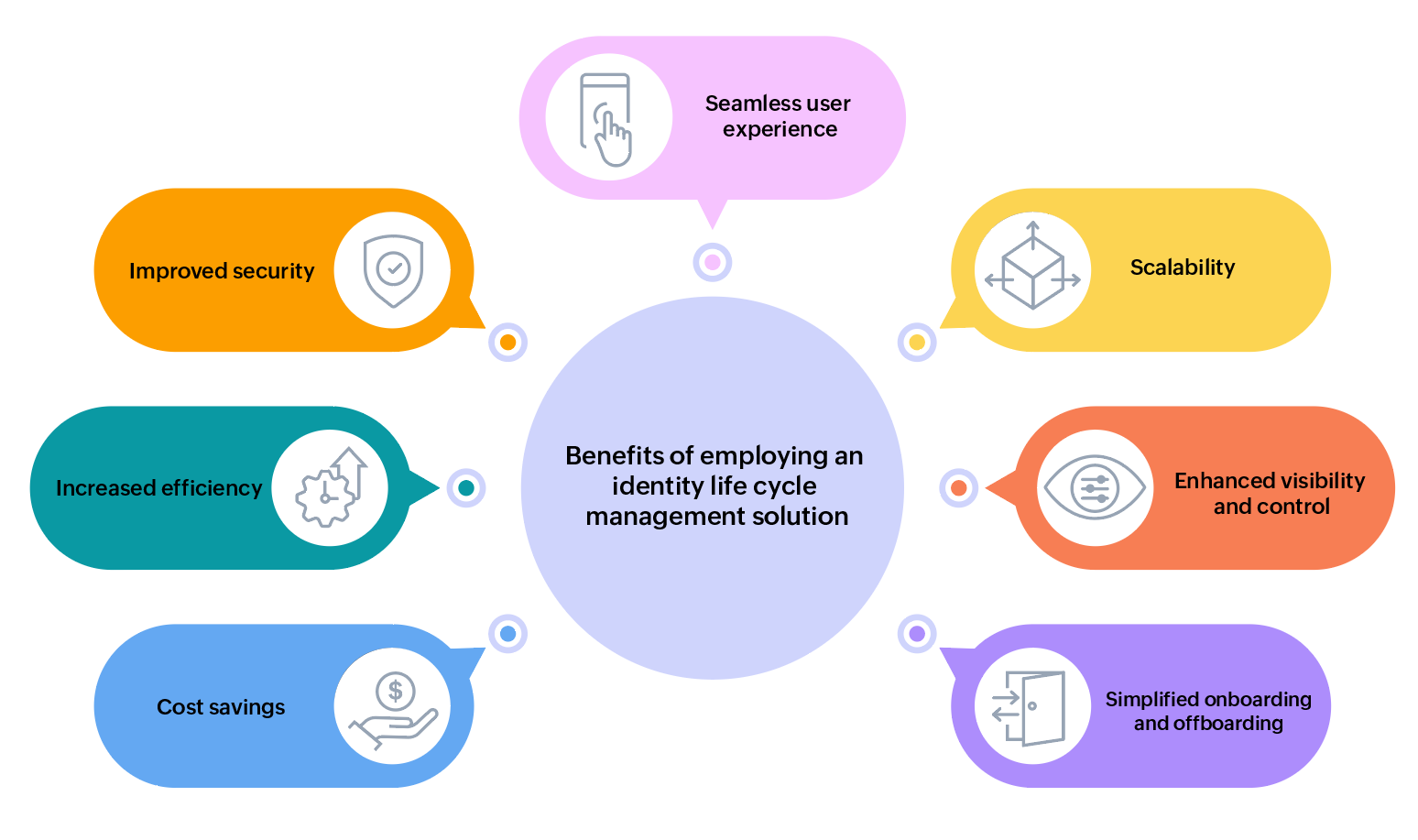
Identity life cycle management is essential for overseeing user identities in organizations, from onboarding to offboarding. Here are the key benefits:
- Improved security: Ensure authorized access and prevent breaches by managing user identities throughout their life cycle.
- Increased efficiency: Automate tasks like provisioning and deprovisioning, saving time and reducing errors for IT teams.
- Cost savings: Automation reduces manual labor costs, identifies unused accounts, and cuts licensing and maintenance expenses.
- Seamless user experience: Enhance user productivity and experience with streamlined login, single sign-on (SSO), and simplified ID control. Manage passwords and access easily for employees, customers, and partners.
- Scalability: Adapt to evolving organizational needs, accommodating changes in user populations and applications without disruptions.
- Enhanced visibility and control: Provide a centralized view of user identities, improving IT teams’ control over resources and preventing unauthorized access.
- Simplified onboarding and offboarding: Streamline the process, ensuring timely and secure access to company resources for new and departing employees.
What are some solutions and tools for identity life cycle management?
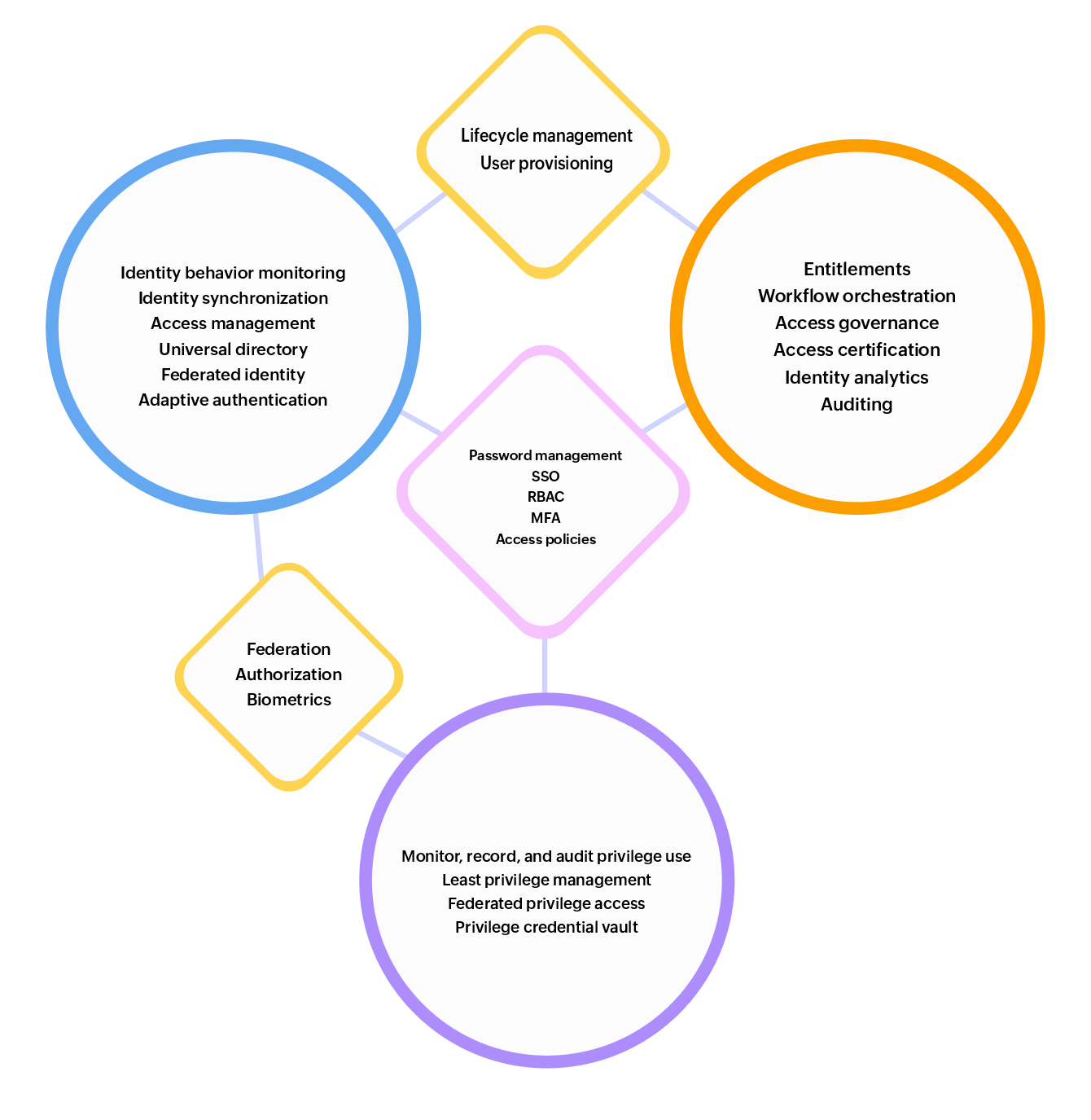
There are several solutions and tools available for managing the life cycle of identities in your organization. These tools are often known as IAM tools, IGA tools, user life cycle management tools, identity life cycle management tools, cloud directories, and so on. While some of these solutions offer comprehensive identity life cycle management capabilities, others provide partial solutions. However, the main purpose of all these tools is to simplify the identity management process.
IAM systems
IAM systems are comprehensive solutions that manage the entire identity life cycle, from onboarding to offboarding. They provide a centralized platform for managing user identities, access rights, and privileges across multiple systems and applications.
Identity governance and administration (IGA) tools
IGA tools offer a structure for overseeing and implementing identity-related policies and controls, aiding organizations in upholding compliance with regulatory mandates and internal security policies.
Privileged access management (PAM) solutions
PAM solutions oversee and track privileged accounts, which possess heightened access privileges to crucial systems and data. They aid organizations in regulating and monitoring privileged access to thwart insider threats and data breaches.
Role-based access control (RBAC) systems
RBAC systems allocate access privileges according to a user’s role in the organization, ensuring that users are limited to the necessary resources for their job responsibilities and minimizing the likelihood of data breaches.
User behavior analytics (UBA) solutions
UBA solutions use machine learning and behavioral analysis to detect anomalous user behavior and flag potential security threats. This helps organizations identify and respond to identity-related risks in real time.
Directory services
Directory services, such as Active Directory, are used to store and manage user identities and their attributes. They provide a centralized repository for user information and can be integrated with other systems for identity management.
Optimize your identity life cycle management with ManageEngine
Effective identity life cycle management is crucial for maintaining operational efficiency and ensuring the security of data and systems within an organization. ManageEngine Identity360, AD360, and PAM360 provide organizations with powerful IAM capabilities to manage and secure identities.
Efficiently manage your organization’s identity life cycle with enhanced security using Identity360. Integrate multiple directory services and applications into Identity360’s Unified Directory for centralized identity and access management. Easily oversee users through the Universal Directory, and onboard users across various directories and apps seamlessly. Administrators can control application access, assign IT tasks, and access detailed reports for insights with Identity360.
Simplify identity life cycle management by automating tasks such as user creation, moving users between containers, and deactivating or deleting inactive users. Implement ML-based UBA for automated threat response, and let users independently reset passwords and unlock accounts using AD360, a unified IAM solution to manage and secure digital identities.
Effortlessly manage the complete life cycle of workloads and machine identities. PAM360, a comprehensive privileged access management solution, enables IT administrators to automate, oversee, and audit tasks related to machine identities, including certificates, keys, passwords, secrets, and other essential entities. Through PAM360, IT admins gain full authority over enterprise machine identities and can actively address issues like process failures and privilege misuse.
Secure access and navigate identities from start to finish.