One of the most challenging task in system administration is to restrict usage of certain applications. Endpoint Central MSP facilitates you to perform this task at ease. You will be able to block the required applications/executable using this feature. You can apply these restrictions for specific computers. Endpoint Central MSP's prohibited software helps you to uninstall the software applications which are not allowed in the network. Block executable feature, allows you to restrict the executable when it is launched, on the target computers. You can block even executable like, notepad.exe, putty.exe etc which are launched without being installed on the target computer. All the file formats supported under Windows "Software Restriction Policy" can be blocked using Endpoint Central MSP. There are two ways to block an application/executable, they are:
The following prerequisites should be met for blocking the executable
|
You can choose this option to create a policy in order to block an executable. Path Rule, is used to block an executable based on the name of the executable and its extension. If the user, renames the application then the application will not be recognized, which means the application will not be blocked. You can use this rule, if you wanted to block applications even if they are not available in your network. All you need to know is just the name of the executable and its file extension. Using path rule, blocks all the versions of the specified application. For example, if you have created a path rule to block Google Chrome browser for a specific version, say version 44.0. This policy will block all the versions of Google Chrome browser, unless the executable is not renamed.
Hash is a unique value, that represents the executable. If you choose to block an executable using the hash value, then it will be blocked even if renamed. If you wanted to block an executable using hash value, you should locate it on the server, for the hash value can be calculated.
If you wanted to block an executable to a specific target, then you will have to create a policy. Selecting the target computers is the first step in creating a policy. You will have to select the executable which needs to be blocked, if it exists in the database. If you wanted to block an executable for the first time, then you will have to add the executable and choose to block rule as path or hash. You can create two different policies for a single executable, one using path and the other using hash value. Policy will be applied on the target computer for the first time, after the system restart.
Endpoint Central MSP by default has a custom group, which contains all the managed computers. If you wanted to block an executable for all the managed computers, then you can choose "All Managed Computers" group and select the executable, which needs to be blocked. You will have to create a policy by specifying the target and executable which needs to be blocked.
To block an executable for specific target, you will have to create a new custom group or use the existing custom groups. Custom groups can be of any type such as, unique or static. You can block executable by choosing custom group which contains users or computers.
| "Block executable" does not support blocking executable which are initiated by the system. |
Type gpedit.msc
Click Group Policy
Click on "Turn Off Local Group Policy Objects Processing" as shown below.
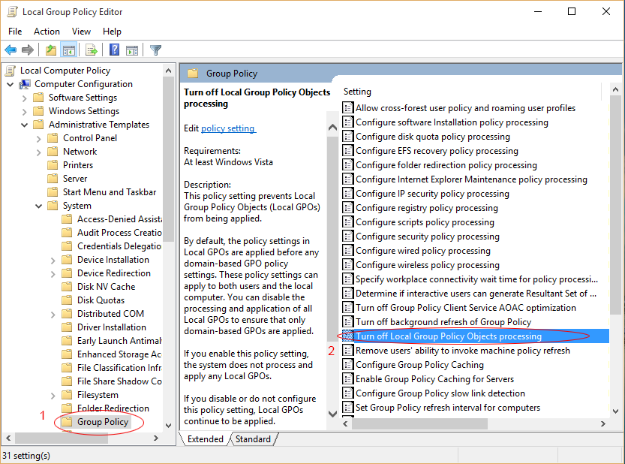
Ensure that you have chosen "Not Configured" as shown in the below image.
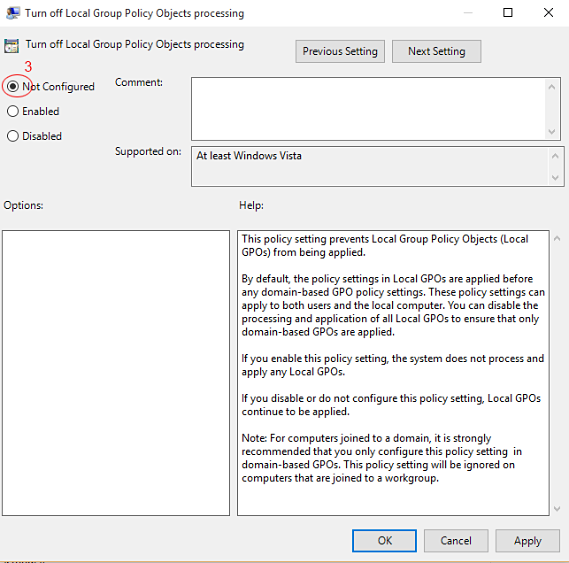
You have now enabled Local Group Policy on the target machine.
Type gpedit.msc
Type gpedit.msc
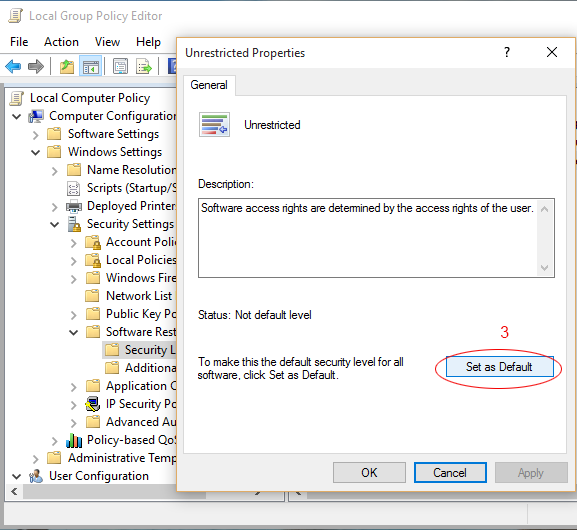
Type gpedit.msc
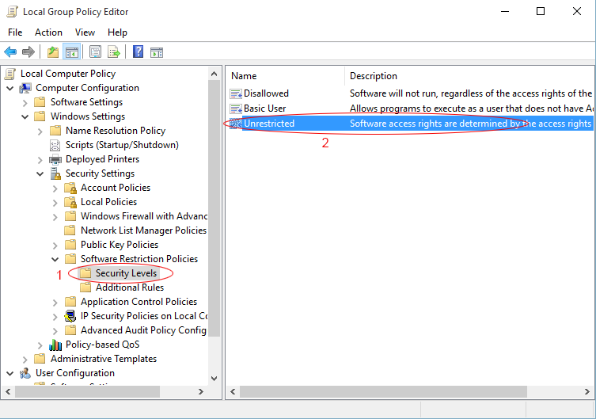
Click "Software Restriction Policy"
Double click "Enforcement" to ensure that "All Users" is selected as shown in the image below
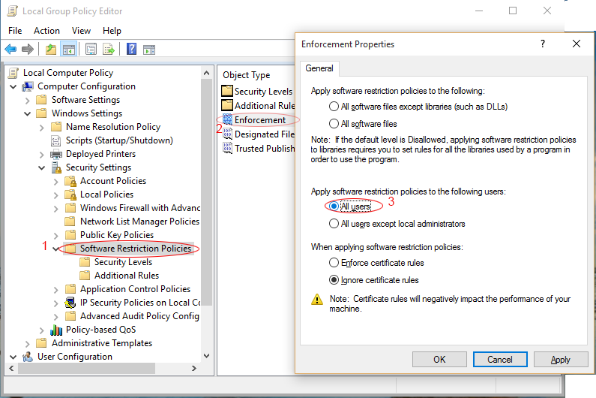
You have now enabled Local Group Policy for Administrators.