 |
January 2023 |
|
|
 |
Six ways to fortify your endpoints
With rapid transition in technology, CISOs and SOC team found it difficult to move along the transition. Check these endpoint security strategies that will help you fortify your endpoint network for the current and the upcoming challenges and helps your organization stay away from threats.
LEARN MOREFREE TRIAL |
Real-time vulnerability mitigation in just a few clicks!
With Patch Connect Plus' CVE Import feature, you can now import CVE IDs and publish the corresponding patches to ConfigMgr and Intune right from the console.
LEARN MOREFREE TRIAL |
 |
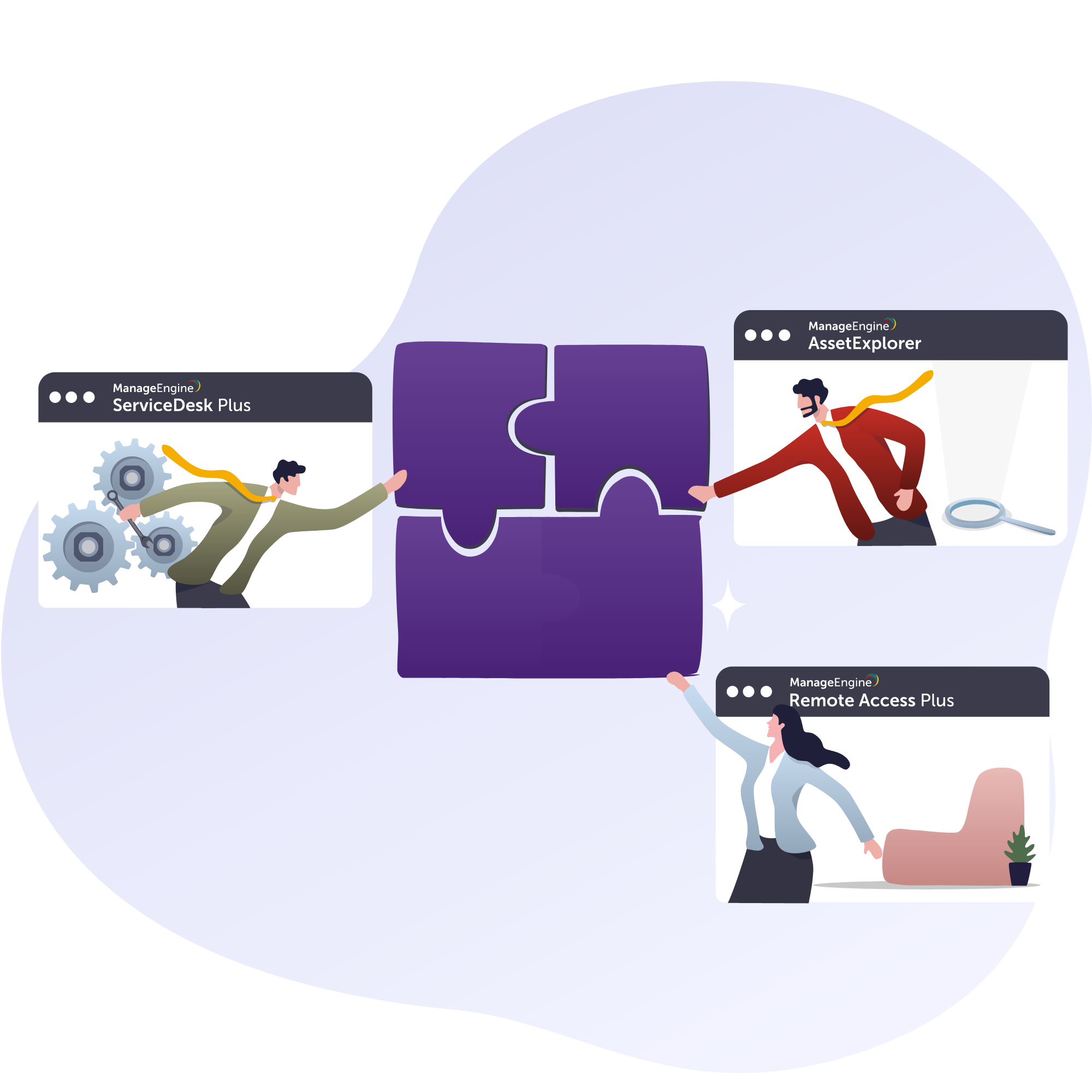 |
ITSM and endpoint troubleshooting unified!
You can now efficiently fine-tune endpoints right from the ticket! Thinking how? We have introduced integration between Remote Access Plus - an advanced unattended access software and ServiceDesk Plus - a help desk solution!
TRY NOWFREE TRIAL |
|
|
Upcoming Events |
 |
Free Training |
Topic
Patch Management Webinar
Remediate known vulnerabilities with automated patch management |
Date
25.1.2023
11:30 AM EDT | 6:30 AM GMT |
| REGISTER NOW |
|
Free Training |
Topic
Endpoint Security Webinar
Secure endpoints from un-known vulnerabilities with unified endpoint security |
Date
1.2.2023
11:30 AM EDT | 6:30 AM GMT |
| REGISTER NOW |
|
 |
|
|
|
|
 |
Your feedback matters!Love using Endpoint Central? Share your feedback and experience with the world and claim your Amazon gift card! SHARE FEEDBACK |
|
|
 |
Did you know |
|
 |
Keylogger
Any method that captures a victim's keystrokes as they are entered into a physical keyboard. A keylogger can be a piece of hardware or software that records everything a user types, including passwords, answers to security questions, and details from emails, chats, and documents.
|
|
|
Unified Endpoint Management & Security Solutions
|
|
|
|
|
 |


