Steps to configure SAML SSO for Boomi
About Boomi
Boomi is an intelligent integration and automation platform that connects applications, data, and people to streamline business processes. It offers a unified platform for integration, API management, and data management, empowering organizations to automate workflows and achieve digital transformation.
The following steps will help you enable single sign-on (SSO) for Boomi from Identity360.
Prerequisites
- The MFA and SSO license for Identity360 is required to enable SSO for enterprise applications. For more information, refer to pricing details.
- Log in to Identity360 as an Admin or Super Admin.
- Navigate to Applications > Application Integration > Create New Application, and select Boomi from the applications displayed.
Note: You can also find Boomi from the search bar located at the top.
- Under the General Settings tab, enter the Application Name and Description.
- Under the Choose Capabilities tab, choose SSO and click Continue.
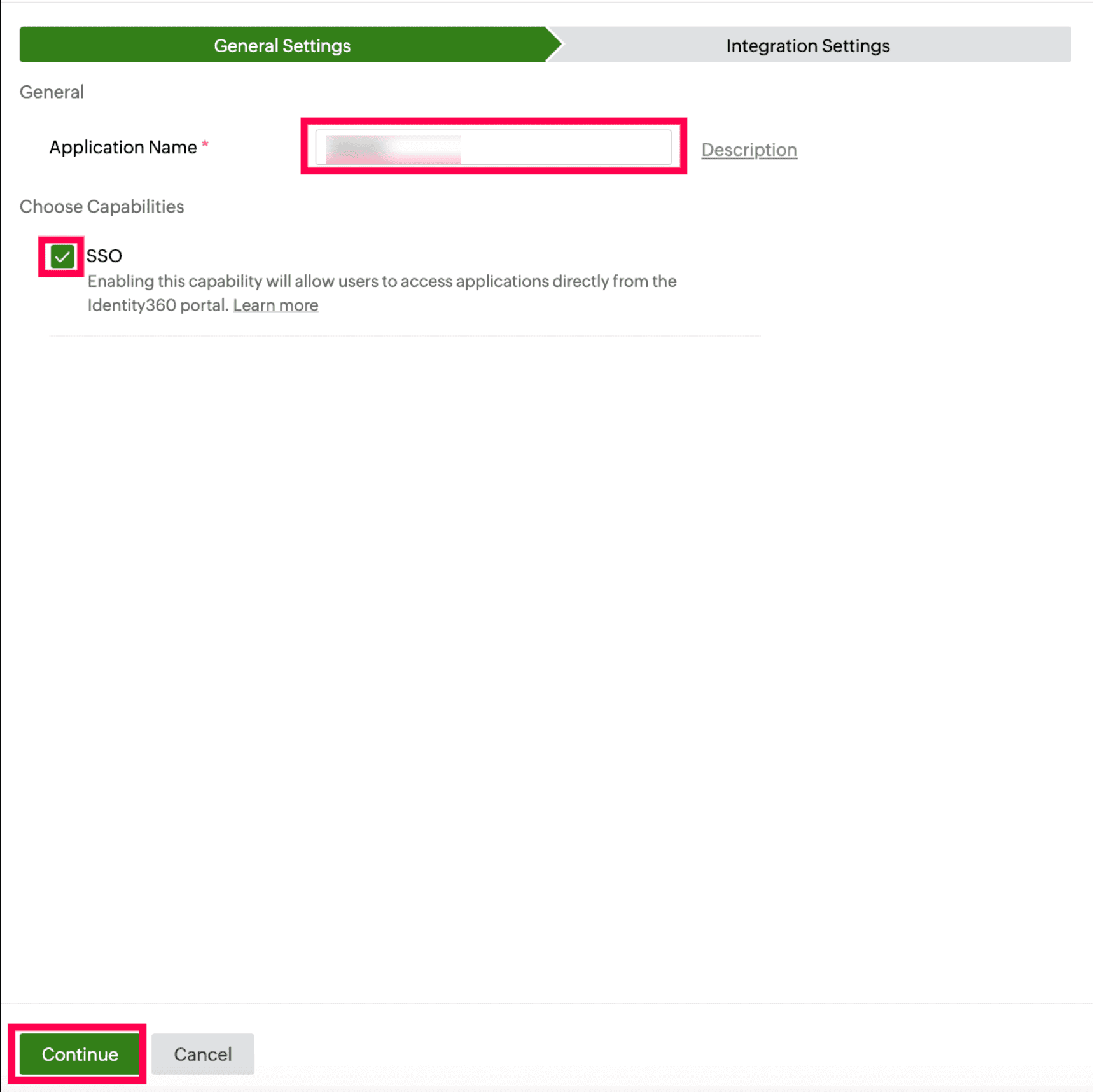 General Settings of SSO configuration for Boomi
General Settings of SSO configuration for Boomi
- Under Integration Settings, navigate to the Single Sign On tab and click Metadata Details.
- Copy the Login URL and Login URL values, which will be later used during the configuration of Boomi.
- Download the SSO certificate by clicking Download from the Signing Certificate field.
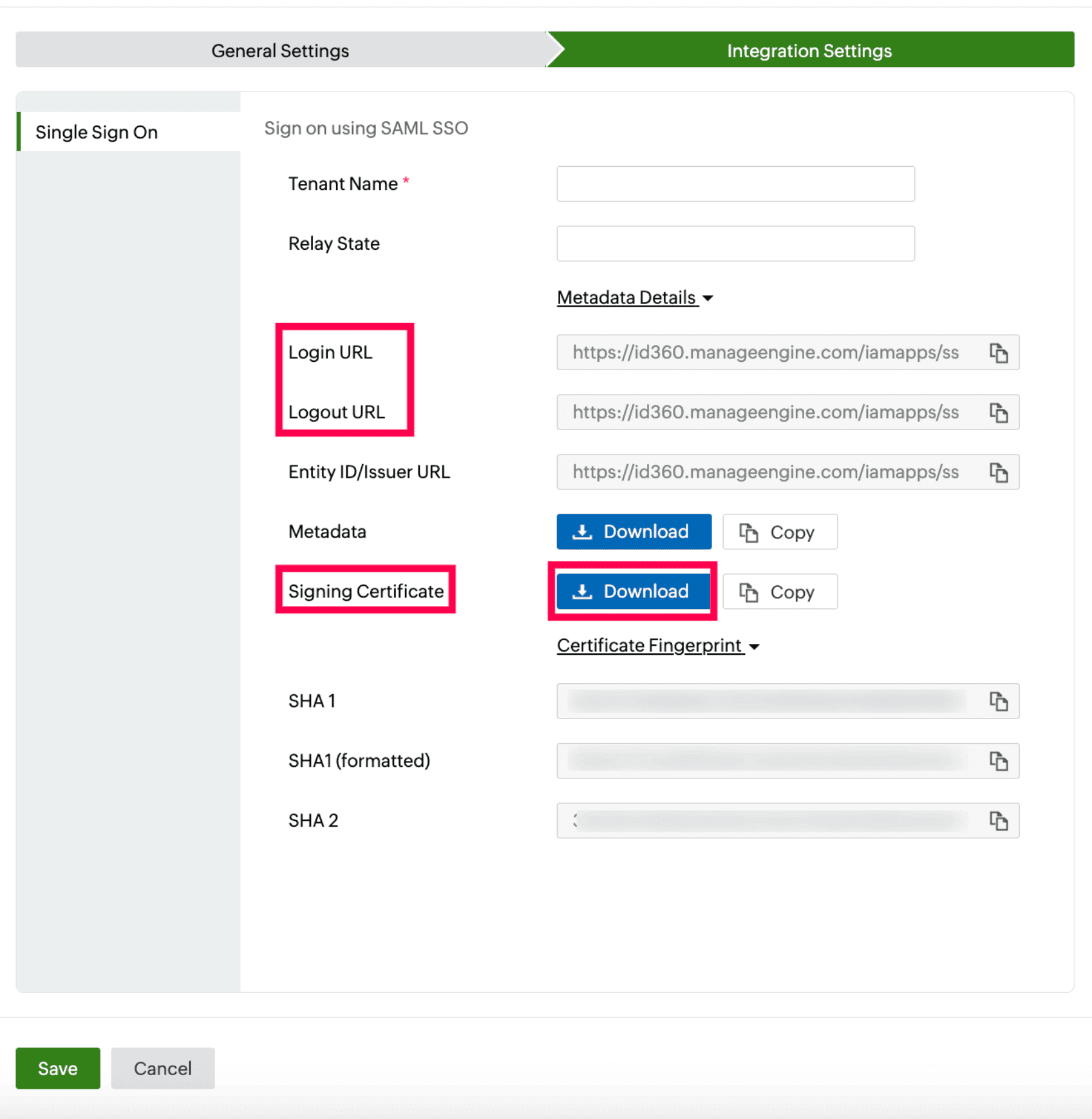 Integration Settings of SSO configuration for Boomi
Integration Settings of SSO configuration for Boomi
Boomi (service provider) configuration steps
- Log in to Boomi with admin privileges.
- Navigate to Settings, and click Account Information and Setup.
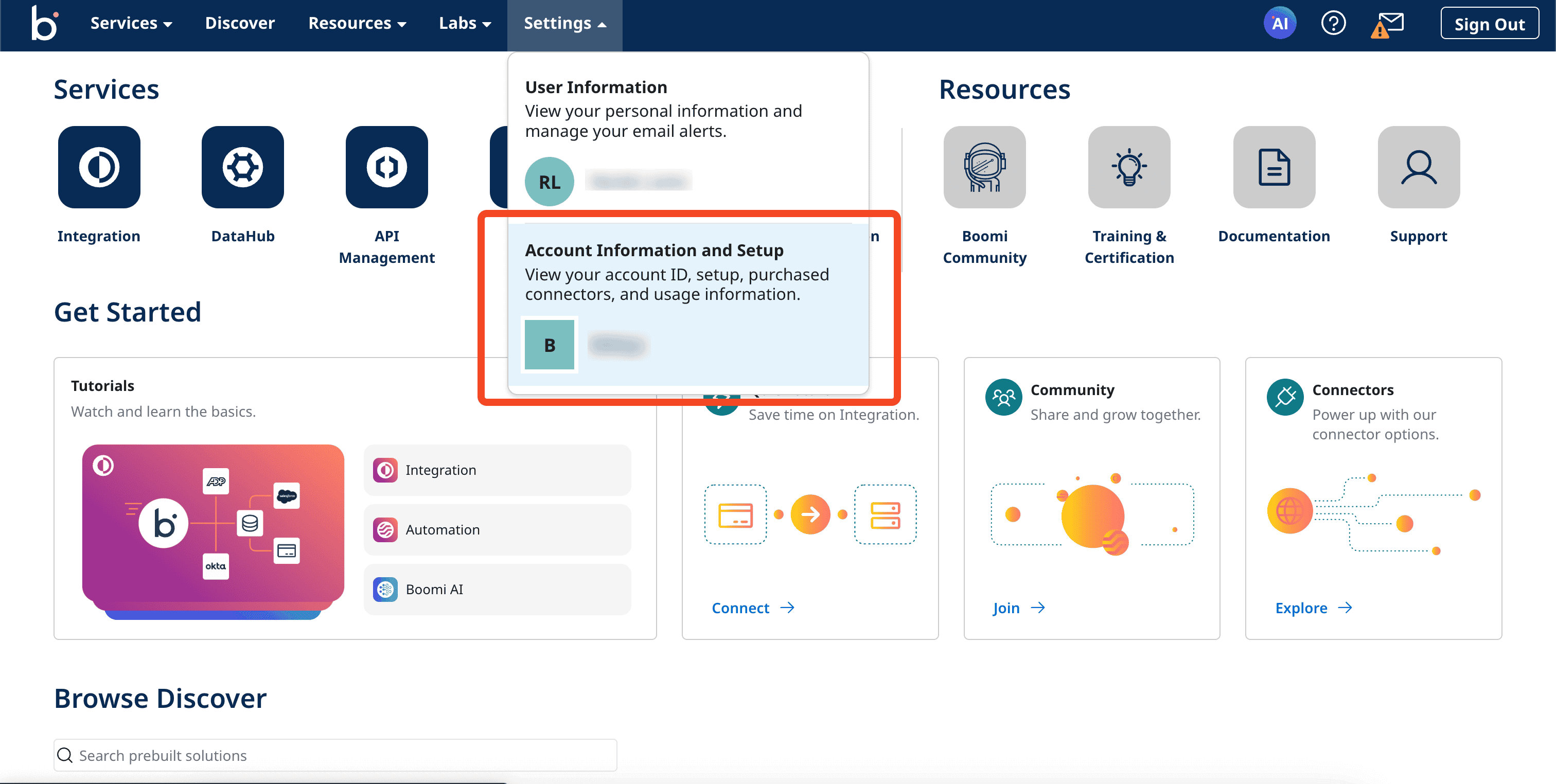 Portal view of the Boomi application
Portal view of the Boomi application
- Navigate to the Security Options section, and click SSO Options.
- Select Enabled under the Enable SAML Single Sign-On section.
- Import the Signing Certificate, which was downloaded in step 6b of the prerequisites section.
Note: The Signing Certificate provided by Identity360 will be in .pem format. It should be converted to .cer or .der format before importing.
- Paste the Login URL and Logout URL values, which were copied in step 6a of the prerequisites section, in the Identity Provider Sign In URL and Sign Out Redirect URL fields, respectively.
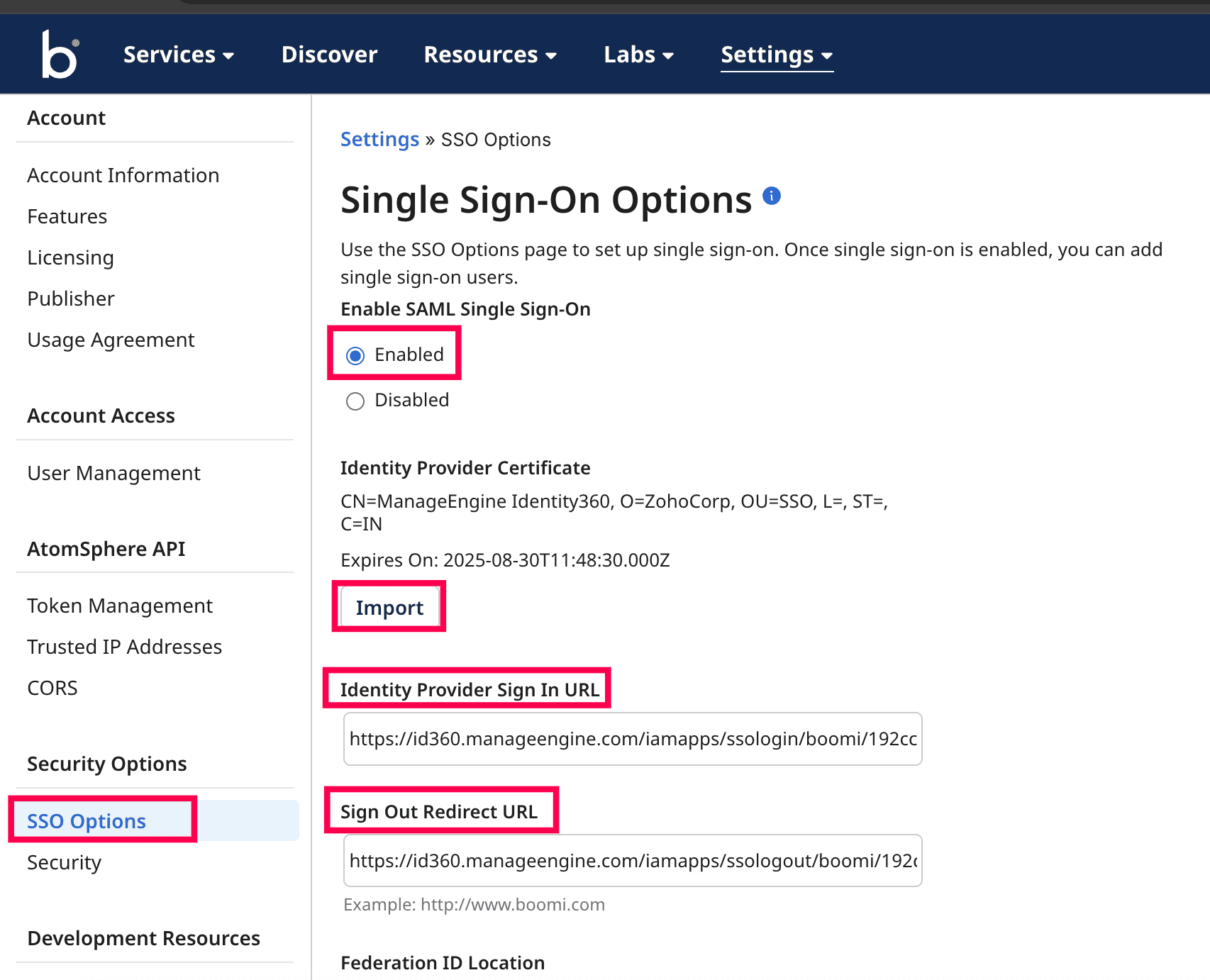 Enabling SAML SSO in Boomi
Enabling SAML SSO in Boomi
- Select the Federation ID is in NameID element of the Subject option under Federation ID Location field.
- Select the Unspecified option under the Name ID Policy field.
- Select the Password Protected Transport option under the SAML Authentication Context field.
- Select the Exact option under the SAML Authentication Context Comparison Levels field.
- Select the Unencrypted option under the Assertion Encryption field.
- Copy the AtomSphere Sign In URL value, which will be used in Identity360 configuration.
- Click Save.
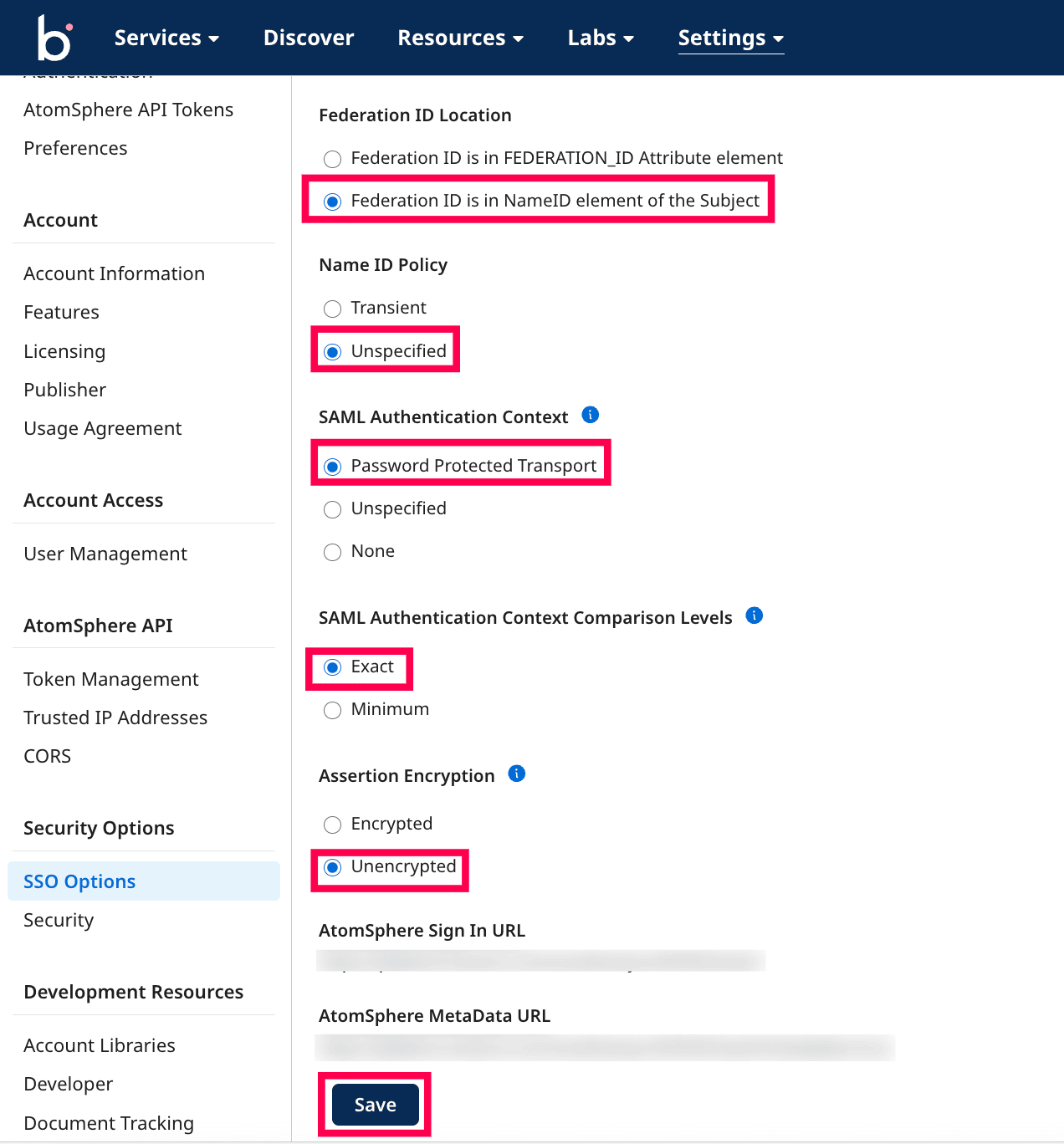 SSO configured in the Boomi application
SSO configured in the Boomi application
Identity360 (identity provider) configuration steps
- Switch to Identity360's application configuration page.
- Enter the Account ID of your Boomi account. If the AtomSphere Sign In URL in Boomi is https://platform.boomi.com/sso/apple-K5CNNR/saml, then apple-K5CNNR is your Account ID.
- Enter the Relay State parameter, if necessary.
Note: Relay State is an optional parameter used with a SAML message to remember where you were or to direct you to a specific page after logging in.
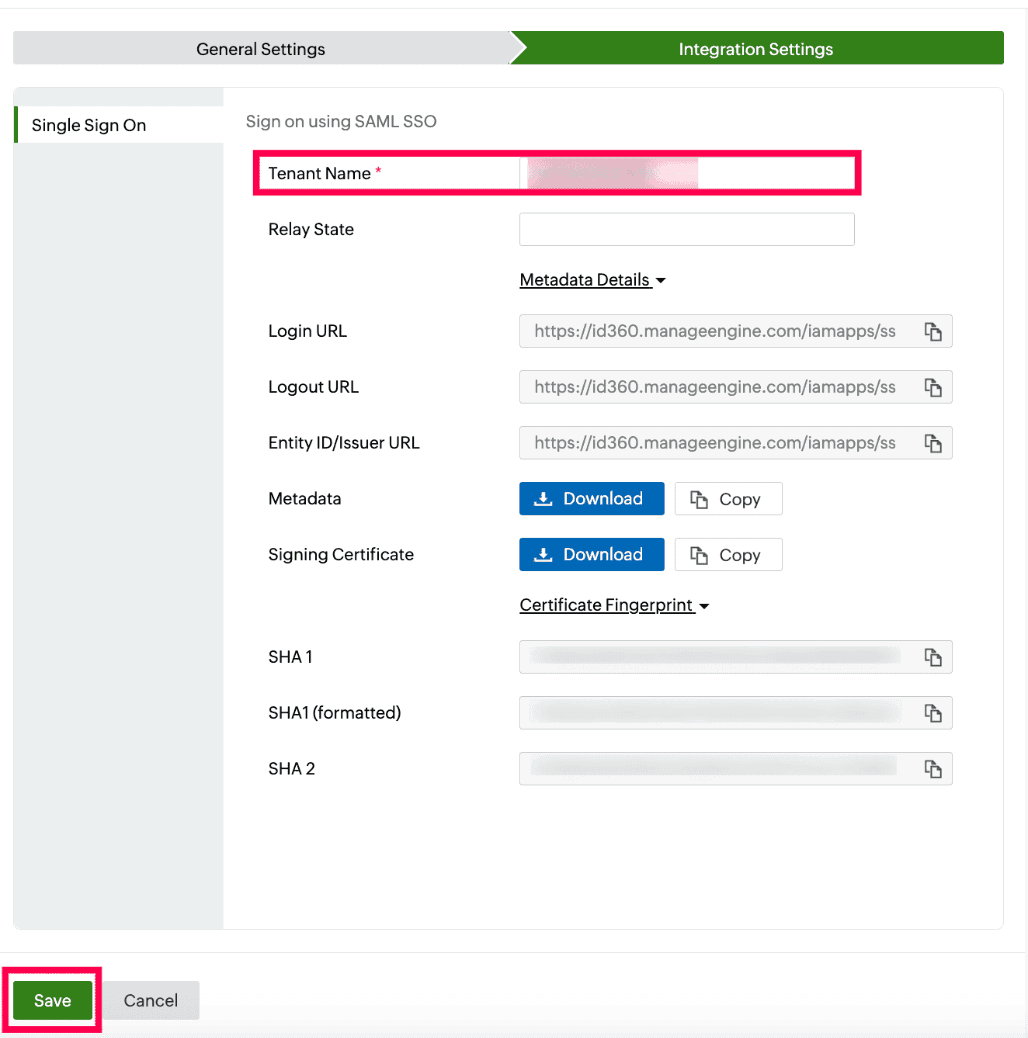 Integration Settings of SSO configuration for Boomi
Integration Settings of SSO configuration for Boomi
- Click Save.
- To learn how to assign users or groups to one or more applications, refer to this page.
Your users will now be able to sign in to Boomi through the Identity360 portal.
Note: For Boomi, both SP-initiated and IdP-initiated flows are supported.
Steps to enable MFA for Boomi
Setting up MFA for Boomi using Identity360 involves the following steps:
- Set up one or more authenticators for identity verification when users attempt to log in to Boomi. Identity360 supports various authenticators, including Google Authenticator, Zoho OneAuth, and email-based verification codes. Click here for steps to set up the different authenticators.
- Integrate Boomi with Identity360 by configuring SSO using the steps listed here.
- Now, activate MFA for Boomi by following the steps mentioned here.
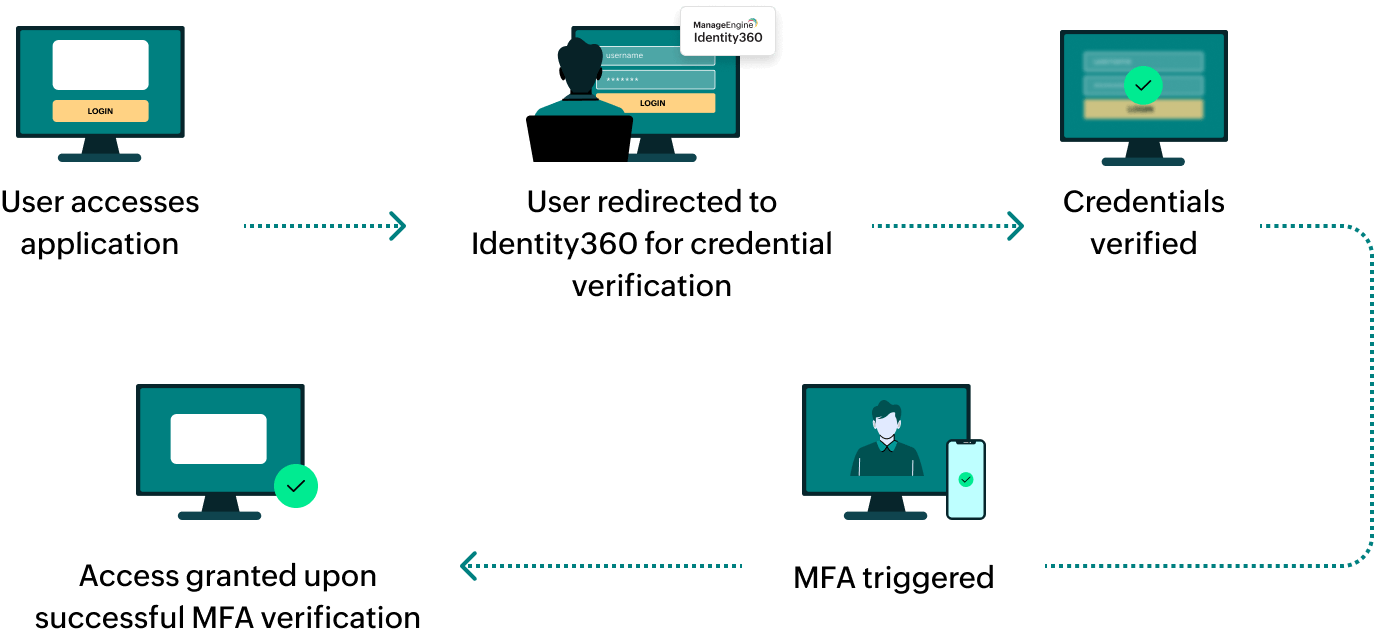
How does MFA for applications work in Identity360?
 General Settings of SSO configuration for Boomi
General Settings of SSO configuration for Boomi Integration Settings of SSO configuration for Boomi
Integration Settings of SSO configuration for Boomi Portal view of the Boomi application
Portal view of the Boomi application Enabling SAML SSO in Boomi
Enabling SAML SSO in Boomi SSO configured in the Boomi application
SSO configured in the Boomi application Integration Settings of SSO configuration for Boomi
Integration Settings of SSO configuration for Boomi