What is ransomware detection?
Ransomware detection is the process of identifying potential signs of a ransomware attack while the malware enters and starts infesting the network. It is a proactive process that complements ransomware prevention to contain the attack in its initial stages. It involves notifying and alerting the security operations center to prevent the propagation of the attack and protect sensitive files from encryption. Detection techniques focus on flagging malicious activities associated with the attack, such as malicious file creations, deletions and renames, anomalous logons, suspicious spawning of processes, and unauthorized permission changes.
It takes approximately 224 days to detect a ransomware attack, according to IBM's Cost of a Data Breach Report 2024. This is enough time for ransomware to take over an organization's entire network. The earlier the detection, the less the damage inflicted.
Importance of detecting a ransomware attack
Ransomware attacks often go unnoticed until files become inaccessible or a ransom demand reaches the victim organization. By the time the business is aware of the attack, significant and irreversible damage might have occurred, leading to:
- Disruptions in business operations.
- Violations of compliance regulations.
- Compromise of confidential data.
- Loss of customer trust and reputation.
- Financial losses and huge penalties.
Therefore, early detection of ransomware is crucial to protect your business.
Challenges in ransomware detection
Here are some of the predominant challenges faced by businesses in identifying and containing ransomware.
- Absence of a centralized security solution: As businesses grow, their networks expand to accommodate an increasing number of devices. Many security solutions limit the number of devices they support, so organizations decide to rely on multiple isolated solutions. But not having a centralized security solution for all endpoints creates gaps in detection capabilities, making it easier for ransomware to evade detection.
- Use of legitimate tools for attack propagation: Some ransomware strains utilize legitimate tools to move laterally across the network to evade detection, thwarting some ransomware detection solutions. These sophisticated ransomware strains multiply rapidly and infect numerous systems within a short period of time. For example, ransomware like REvil use legitimate tools like PsExec and PowerShell to laterally move, deploy, and spread rapidly across the network without being detected.
- Lack of ransomware awareness among users: Ransomware actors employ social engineering tactics such as phishing to gain initial access to networks. While security teams in many organizations are knowledgeable about ransomware, some employees lack sufficient understanding of its potential impact. Less-informed users can become vulnerable to attack, facilitating the entry of sophisticated strains like file-less ransomware that can evade detection.
Signs of ransomware
Here are eight common signs that indicate if your network is under a ransomware siege.
- Phishing emails: Social engineering attacks like phishing are often utilized by ransomware actors to gain initial network access. Receiving suspicious emails containing malicious URLs or attachments indicates that your business is being targeted by ransomware.
- Increased network traffic and activity: Once ransomware infiltrates your network, it spreads by scanning and infecting vulnerable devices. It establishes a communication channel with a command and control (C&C) server to transmit encryption keys and exfiltrate sensitive data. These activities result in unusually high network activity and traffic, which can indicate ransomware infestation.
- Increased disk activity: Ransomware performs excessive read and write operations while encrypting sensitive data on your storage drives. It accesses multiple files on your hard disk and modifies them, leading to higher-than-usual disk activity.
- High CPU usage: Ransomware consumes excessive computational resources during encryption, putting the CPU under strain. A spike in CPU usage, accompanied by increased disk activity, indicates attempts of data encryption by the ransomware.
- Changes to system settings: Ransomware makes changes to system settings, such as firewall rules, group policies, and security configurations, to move laterally across the network. Unusual changes to system settings indicate a possible presence of ransomware.
- Audit policy changes: To evade detection, ransomware can modify audit policy settings or tamper with audit logs to erase traces of its malicious actions. Therefore, suspicious changes to audit policies and associated logs might indicate ransomware activity.
- Suspicious file extensions: Ransomware renames encrypted files with random strings of characters or numbers and adds malicious extensions, rendering the files inaccessible.
- Backup encryption: Ransomware also encrypts or deletes backup data of sensitive files and folders. This marks the final stage of the attack, after which the ransomware might reveal its presence through a ransom note.
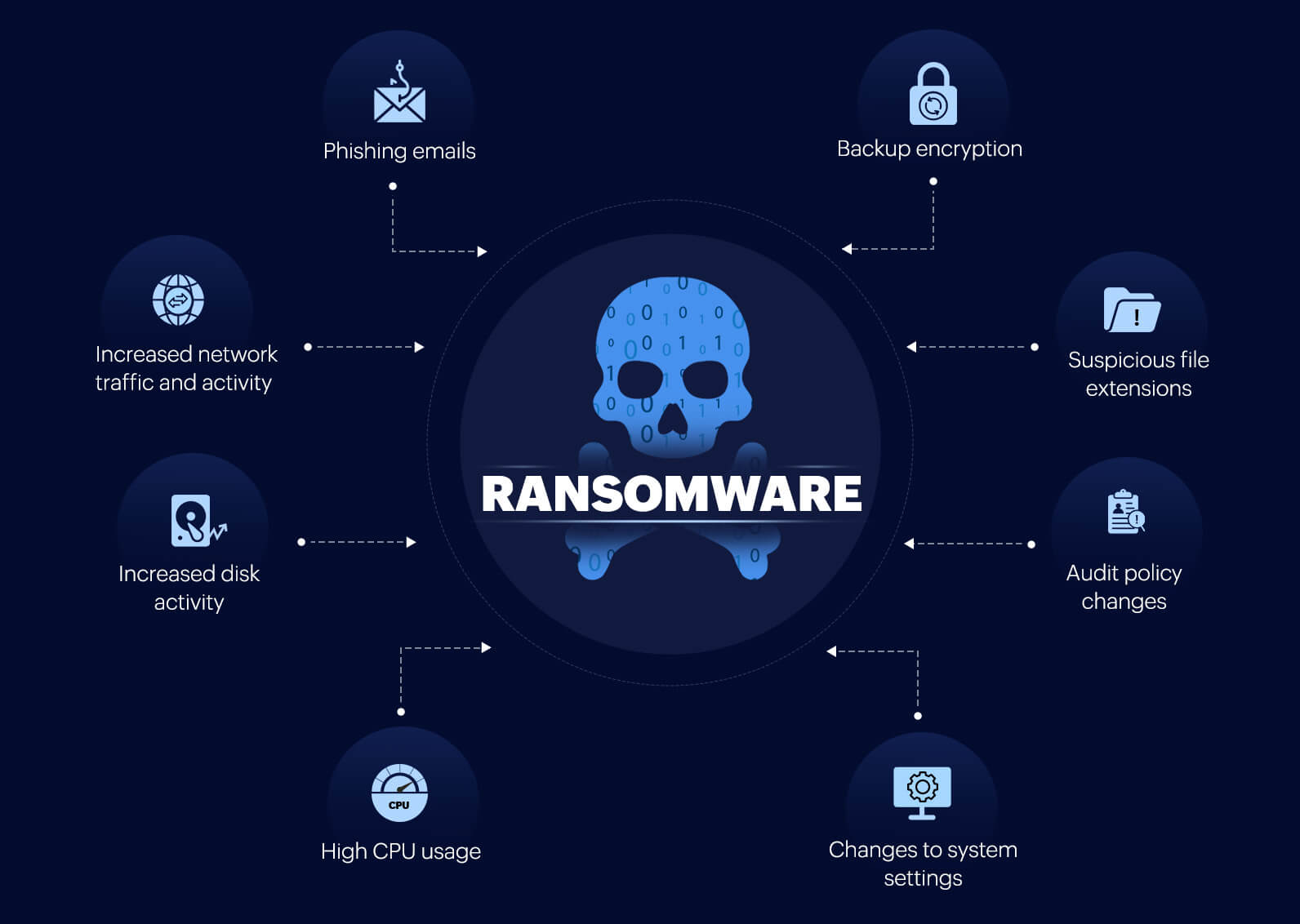
Figure 1: Signs of a ransomware attack
Ransomware detection techniques
The four common detection techniques used to identify ransomware are:
1. Signature-based detection
Also known as static file analysis, signature-based detection is the most common technique for detecting ransomware. This detection tool, or anti-ransomware solution, consists of a library of common malware signatures, or IoCs, which include binary file hashes, domain names, and IP addresses of the C2C systems. When suspicious executables are identified, the solution scans and captures data from the file without executing it. It then cross-checks the file contents against the malware signatures. If any signs of malware are detected, the solution blocks the file from being executed across the network.
This technique is beneficial for detecting known malware or older strains of ransomware that are not sophisticated. However, in the case of novel and modern ransomware strains, this technique is ineffective because these strains can evade detection by altering their signatures and hash values through permutation tactics.
2. Traffic-based detection
Ransomware detection based on network traffic involves analyzing all inbound and outbound communications in the network to identify suspicious activity. The detection tool scrutinizes the data packets transferred between endpoints and external networks to flag anomalous time stamps, file size, file entropy, and volume of data transmitted.
While this technique does not rely on predefined malware signatures, it tends to generate false positive alerts and might block legitimate data transmissions. Additionally, the analysis of larger data packets can prolong the detection time, hindering early identification of ransomware. Its effectiveness can be diminished when attackers exploit legitimate file-sharing tools for data transmission.
3. Behavior-based detection
Ransomware exhibits distinctive behaviors that differentiate it from other types of malware. Behavior-based detection monitors these behaviors by observing unusual file activities and processes within the system. This includes abnormal file executions, unauthorized enumerations, sudden increases in file encryptions, storage device overwrites, and excessive file renames.
Behavior-based detection tools utilize predefined alerts with intelligent thresholds to identify anomalous activities that occur repeatedly within a specific timeframe. Unlike signature-based techniques, behavior-based detection does not rely on malware signatures and avoids generating false positive alerts, which are common in traffic-based detection methods. This technique proves particularly advantageous in real-time scenarios, enabling security teams to promptly detect and respond to abnormal activities as they happen.
4. Deception-based detection
Also known as the honeypot technique, deception-based detection aims to deceive and detect ransomware using a pseudo network. This pseudo network operates within an isolated environment and includes fake assets and decoy files placed in shared folders. These files are hidden from internal users to maintain a foolproof environment and prevent false positives. The deception-based detection tool can also be integrated with other anti-ransomware software to simulate legitimate network activities.
When ransomware attacks a pseudo network, all its tactics and techniques—from initial entry to file encryption—are monitored to decode the attack kill chain. This approach helps promptly identify potential ransomware attacks and enables businesses to develop effective prevention and mitigation strategies based on the observed ransomware kill chain.
Best practices in ransomware detection
Here are 10 best practices that enhance your ransomware detection strategy:
- Raise awareness among users and stakeholders about the various signs of ransomware attacks and educate them on the necessary precautions to avoid becoming victims of such attacks.
- Stay vigilant against phishing emails using email filtering and spam blocking tools so that suspicious emails don't reach your inbox.
- Implement a log management solution or a SIEM solution to gain visibility across the entire network.
- Employ an ML-based anomaly detection software to track behavioral deviation among users and entities.
- Continuously audit endpoints and network devices for vulnerabilities and carry out regular patch updates.
- Ensure that security configurations in firewalls, IDSs and IPSs are updated regularly.
- Use network monitoring solutions to analyze incoming and outgoing traffic to block suspicious data packets that contain malicious or sensitive data.
- Monitor changes to sensitive files and folders using a file integrity monitoring solution.
- Regularly backup all critical data and monitor them for unauthorized accesses.
- Carry out periodic audits to prove adherence to compliance mandates that enforce data security.
Benefits of early detection of ransomware
Here are the top five benefits of early ransomware detection:
- Minimal network disruptions: Detecting ransomware in its early stages helps you contain the attack and reduce the associated down time. This restores normal activities in the network, prevents operational disruptions, and ensures the continuity of business.
- Data loss prevention: Early detection helps you respond to the attack promptly, thereby preventing the ransomware from encrypting and exfiltrating sensitive data.
- Ensure compliance: Addressing ransomware early secures sensitive files and folders from unauthorized access and modification. This proactive approach not only helps ensure compliance with data security mandates, but also mitigates potential regulatory consequences.
- Reduce financial damage: Early detection mitigates financial losses associated with ransom payments, legal penalties, and business disruptions. By containing the ransomware early, organizations can avoid costly remediation efforts and preserve financial resources.
- Preserve reputation: Proactive ransomware detection and prevention demonstrate vigilant cybersecurity practices within a network. This proactive stance protects against financial losses and operational disruptions as well as preserves the reputation and goodwill of the business among stakeholders.
Related solutions
ManageEngine Log360, a comprehensive SIEM solution with advanced DLP and UEBA capabilities, helps you proactively detect potential signs of a ransomware attack. Log360's predefined correlation rules, alert profiles, and audit reports on ransomware activities assist in identifying ransomware in the early stages of the kill chain. With prebuilt incident response workflows, Log360 not only detects ransomware but also aids in responding to the attack and mitigating its consequences. To explore more, sign up for a personalized demo of Log360. Or, you can discover on your own with a fully functional 30-day free trial software download.



