File integrity monitoring serves as a critical layer of defense, ensuring the integrity and security of files and folders within systems and networks. File integrity monitoring tools provide early alerts on potential security breaches, malware infections, and insider threats by monitoring changes to critical files and detecting unauthorized modifications. For a file integrity monitoring tool to be effective, an organization should plan its architecture and implementation correctly.
The architecture usually entails placing monitoring agents on separate servers or systems, with important data being aggregated and managed by a centralized management server. Configuring the tool to monitor particular files or folders, creating thresholds, continuously monitoring for changes, identifying unauthorized alterations, and putting in place suitable response mechanisms like alerts and workflows are all part of the implementation process for a file integrity monitoring tool.
Organizations are protected from potential breaches and data tampering by the proactive security measures that a file integrity monitoring tool's architecture and implementation together offer. These measures identify and mitigate unwanted changes to files. In order to use a file integrity monitoring tool more effectively in today's cybersecurity landscape, it is imperative to understand its architecture and implementation.
The architecture of file integrity monitoring tools
Figure 1 shows a general overview of the architecture of file integrity monitoring systems.
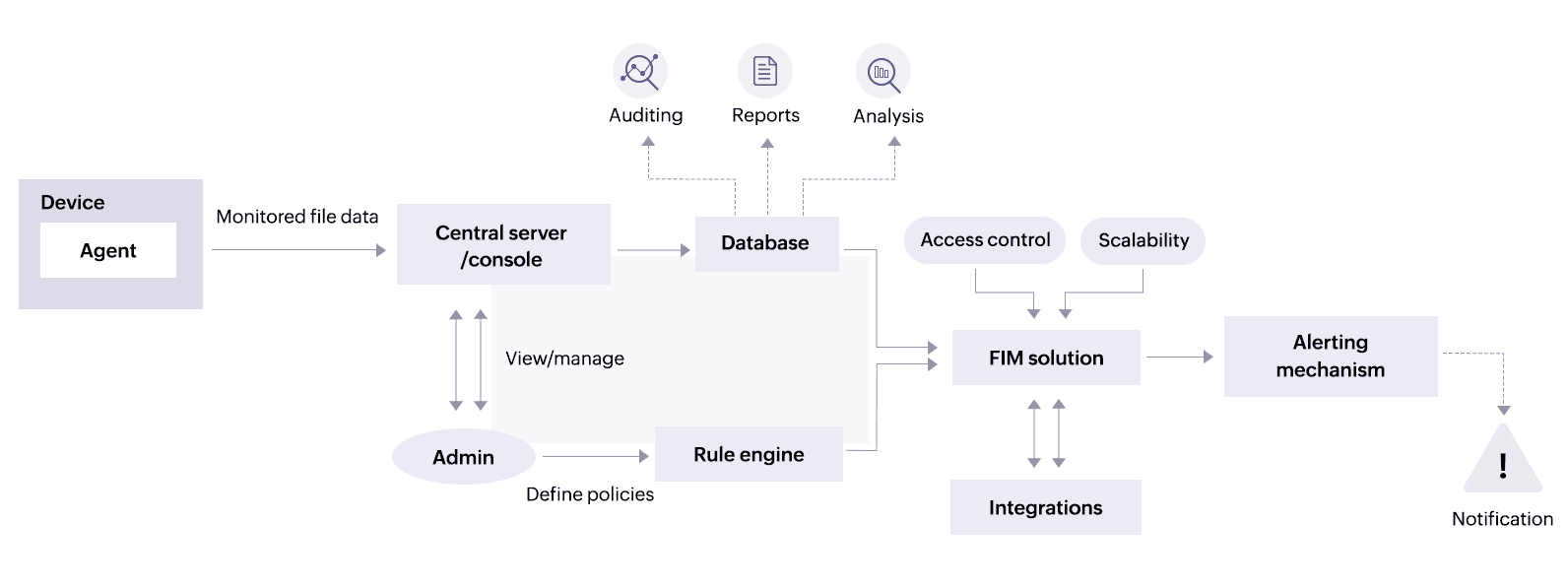
Figure 1: The architecture of a file integrity monitoring tool.
The following is a list of the file integrity monitoring system components that are necessary to create the whole architecture:
- Agents: Agents are installed in systems that need to be monitored by file integrity monitoring solutions. These agents continuously monitor the changes to files and folders, reporting any detected changes to the central server or console for analysis.
- A central server or console: This component gathers the data collected by the agents and gives administrators a centralized interface through which they can view and manage file integrity events.
- A database: File integrity monitoring systems frequently keep database records of the attributes of the files they monitor, the information about those files, and any changes they find. This data can be used for analysis, reporting, and auditing purposes.
- A rule engine: A rule engine enables administrators to define policies and rules specifying which file changes should be tracked and how they should be managed. These rules can specify criteria such as file paths, devices, types of changes, and exceptions.
- An alerting mechanism: When file integrity monitoring systems detect unauthorized or unexpected changes to files, they generate alerts to notify administrators of potential security incidents. These alerts can be sent via email, SMS, or SIEM systems for further analysis.
- Integrations: To provide an enhanced security posture, a file integrity monitoring system may integrate with other security tools, such as SIEM platforms, endpoint detection and response solutions, IDSs, and IPSs.
Some factors to consider when creating a file integrity monitoring architecture are:
- Authentication and access controls: Strong authentication procedures and access restrictions should be put in place to allow only authorized people to have access in order to protect the integrity of the monitoring system itself.
- Redundancy and scalability: File integrity event logs can require significant storage space, especially in large networks with many devices. So, the file integrity monitoring tool's architecture should be built with redundancy and scalability in mind, allowing for continuous monitoring even in the event of network or hardware failures.
- Redundancy refers to the presence of backup components, such as storage systems, management servers, or monitoring agents, which ensure continuous operations and fault tolerance in case of component failures. By offering substitute resources that can take over responsibilities in the event that essential components become unavailable, redundancy seeks to reduce downtime and preserve system integrity.
- Scalability describes a system's capacity to support growing workloads—such as monitoring more files or systems—without compromising functionality or speed. In order to ensure optimal performance as the system grows, scalability entails designing the architecture to readily handle growth by adding resources like servers or monitoring agents. For example, consider implementing horizontal scaling by adding additional management servers, storage nodes, or monitoring agents as the workload increases. This allows the file integrity monitoring system to handle larger environments and higher volumes of data without experiencing performance issues.
The overall goal of file integrity monitoring systems is to give enterprises visibility into the changes made to important files and directories, enabling them to quickly identify and address security events.
How to implement a file integrity monitoring tool
A typical workflow for implementing a file integrity monitoring tool is shown in Figure 2:
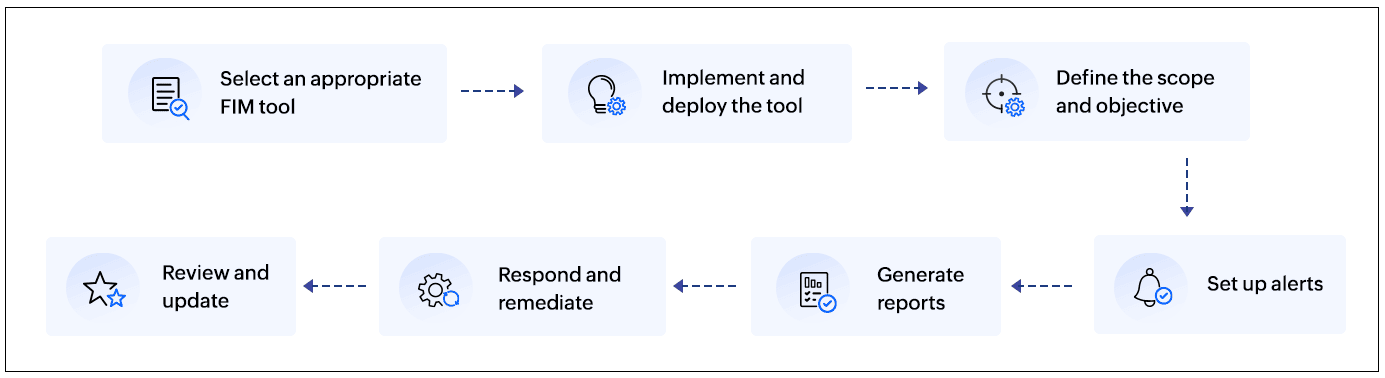
Figure 2: A file integrity monitoring implementation workflow.
Here are the steps to implement a file integrity monitoring tool:
1. Select an appropriate file integrity monitoring tool
Find a file integrity monitoring tool that meets your needs by doing some research. Every choice, both open-source and commercial, has different features. Refer to the "10 things to take into account when choosing a FIM tool" section of this page to gain insights into how to choose a suitable file integrity monitoring solution for your organization.
2. Implement and deploy the file integrity monitoring tool
Install agents in the systems that the file integrity monitoring solution needs to monitor. The central server or console gathers the data collected by the agents. This data is collected by the database that is maintained within the file integrity monitoring solution.
Next, ensure that the tool has appropriate permissions to access the files and directories being monitored. For quicker monitoring and response procedures, integrate the file integrity monitoring tool into your current infrastructure, such as centralized logging and alerting systems.
File integrity monitoring configuration with ManageEngine Log360 is very user-friendly. It is effortless to configure multiple devices at once, and these devices immediately install the necessary file integrity monitoring agents. Agent updates, SACL settings, and all the relevant audit policies are updated automatically.
3. Define the scope and objective
Choose the files and folders that need to be monitored. These could include any files necessary for the proper operation of your system, such as executables, libraries, configuration files, and vital system files.
With Log360, you can configure individual devices and also create templates to indicate the locations of files and folders that need to be monitored for multiple devices (Fig. 3). These features help reduce redundancy and increase efficiency. You can also choose to include or exclude subfolders, specific files, or file types.
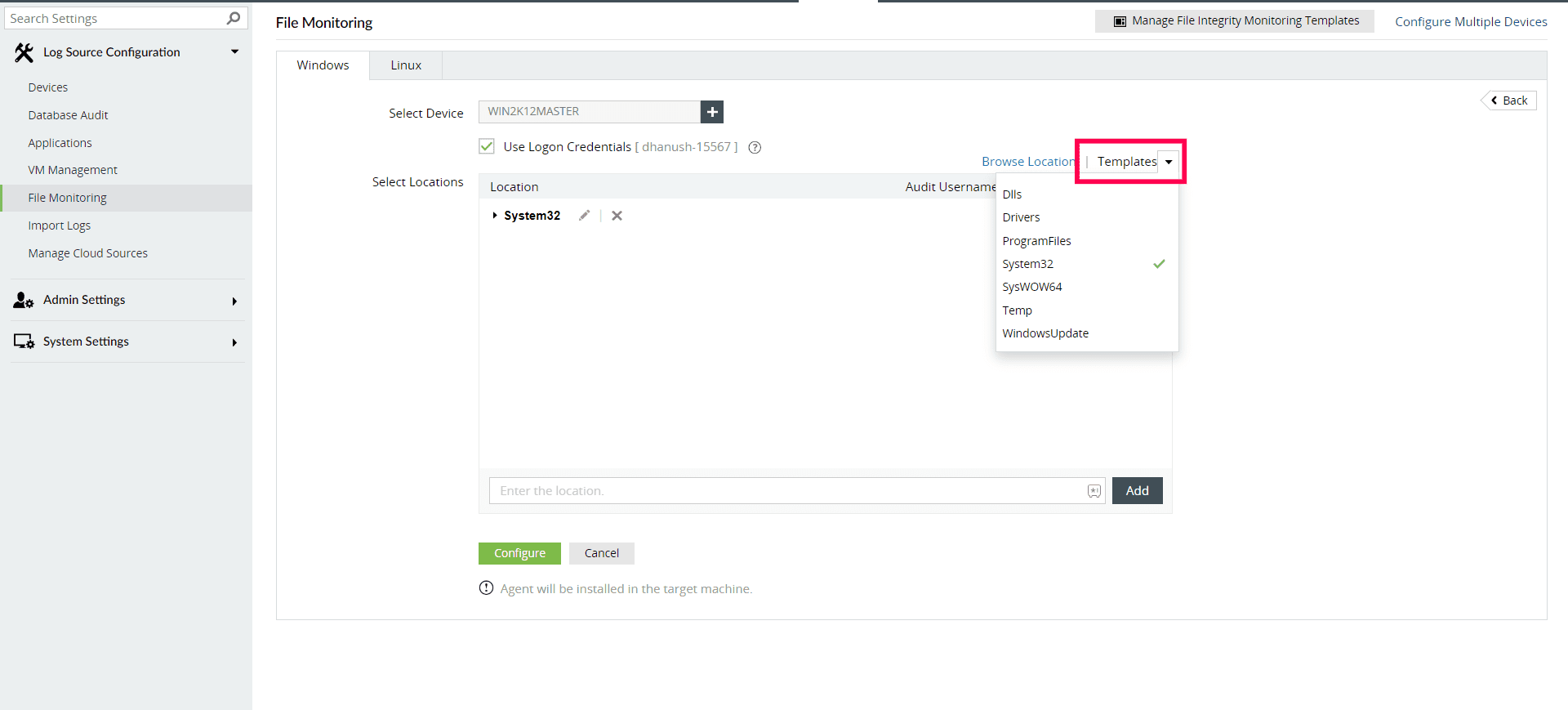
Figure 3: Selecting the folders that need to be monitored using Log360.
Make sure you understand the objectives of your file integrity monitoring, such as detecting unauthorized changes, ensuring compliance with regulations, or identifying potential security breaches.
4. Set up alerts
Ascertain users' regular usage patterns and behaviors to set alert criteria. Then, using this alert criteria as a guide, the file integrity monitoring tool analyzes events in real time. When an event crosses the predetermined alert threshold, a notification is generated and forwarded to the appropriate authority, who then analyzes the issue and takes appropriate actions to rectify it. These alerts include details such as the type of change, the affected files or directories, and the time of the event.
Log360 provides real-time event alerts for important updates, including changes made to files and folders. You can set up alerts by configuring the alert criteria according to your needs (Fig. 4). Alert criteria can also be created based on custom thresholds and user actions.
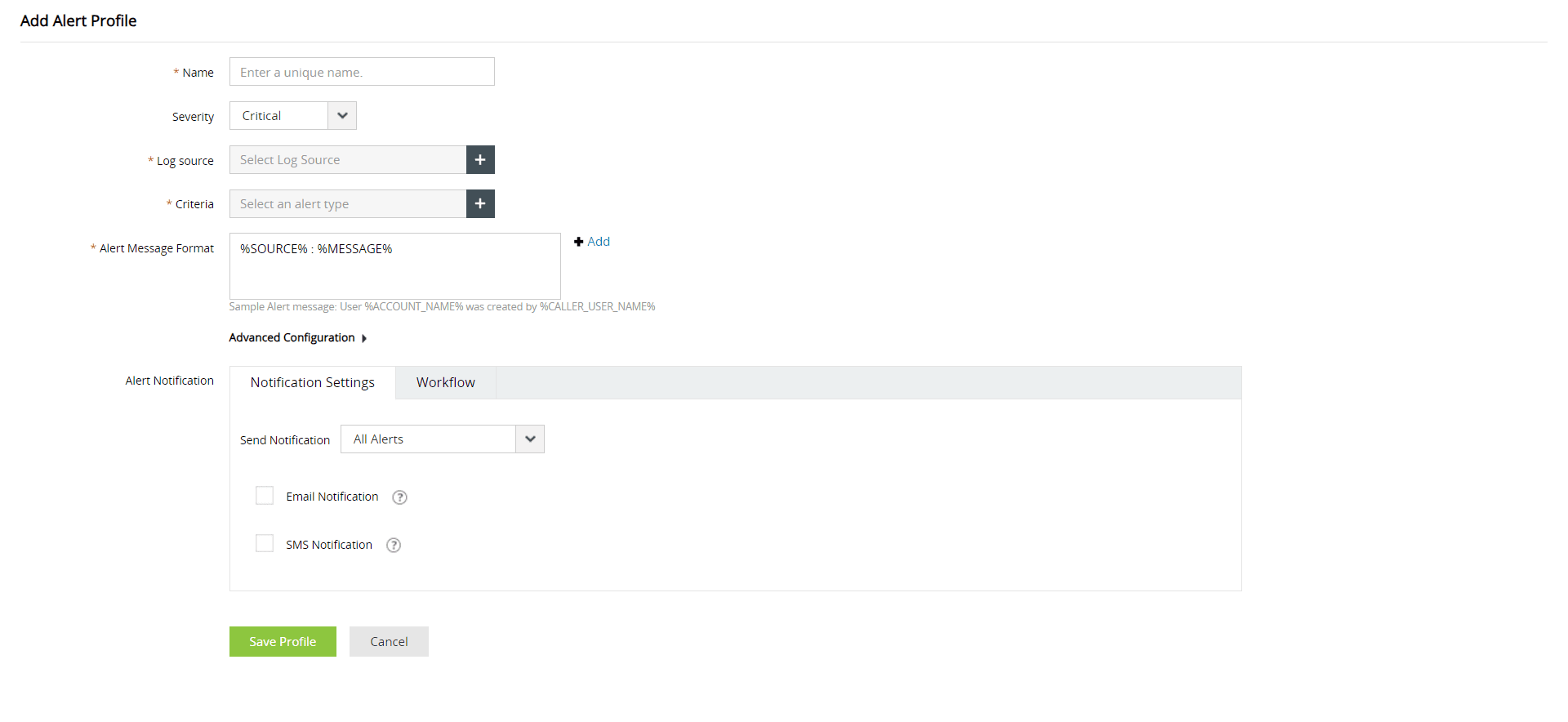
Figure 4: Creating an alert on the Alerts tab of Log360.
5. Generate reports
Regularly generate reports summarizing file integrity monitoring activities, including the detected changes, alerts, and compliance statuses. Use these reports to demonstrate compliance with regulations and evaluate your overall security posture.
As shown in Figure 5, Log360 generates thorough reports (file monitoring reports, correlation reports, compliance reports, and more) with accurate integrity information (file creations, deletions, modifications, permission changes, and more). These reports can be exported in multiple formats, including CSV and PDF. You can automatically receive the reports at regular intervals with the help of flexible report scheduling.
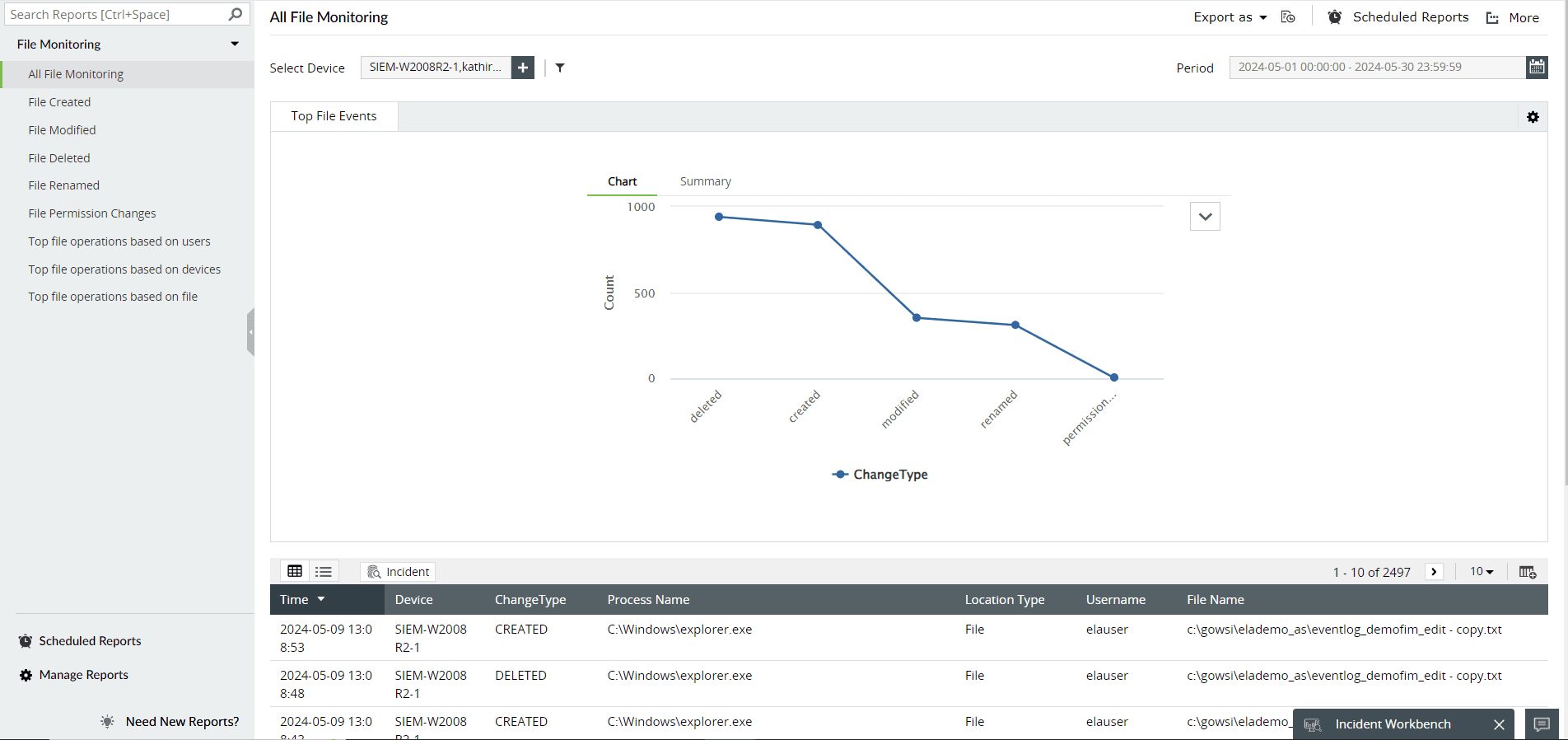
Figure 5: File monitoring reports in Log360.
6. Respond and remediate
Upon receiving alerts, make sure to promptly investigate the detected changes to determine their nature and impact. This may involve reviewing logs, analyzing file contents, and assessing the severity of incidents.
To reduce any security risks or restore the integrity of impacted files, take the necessary remedial actions. This can entail undoing unauthorized changes, applying patches, or implementing additional security controls.
Log360 enables you to create and execute incident workflows and automate common incident response steps (Fig. 6). When alerts are triggered, these workflows get executed automatically to remediate the incidents.
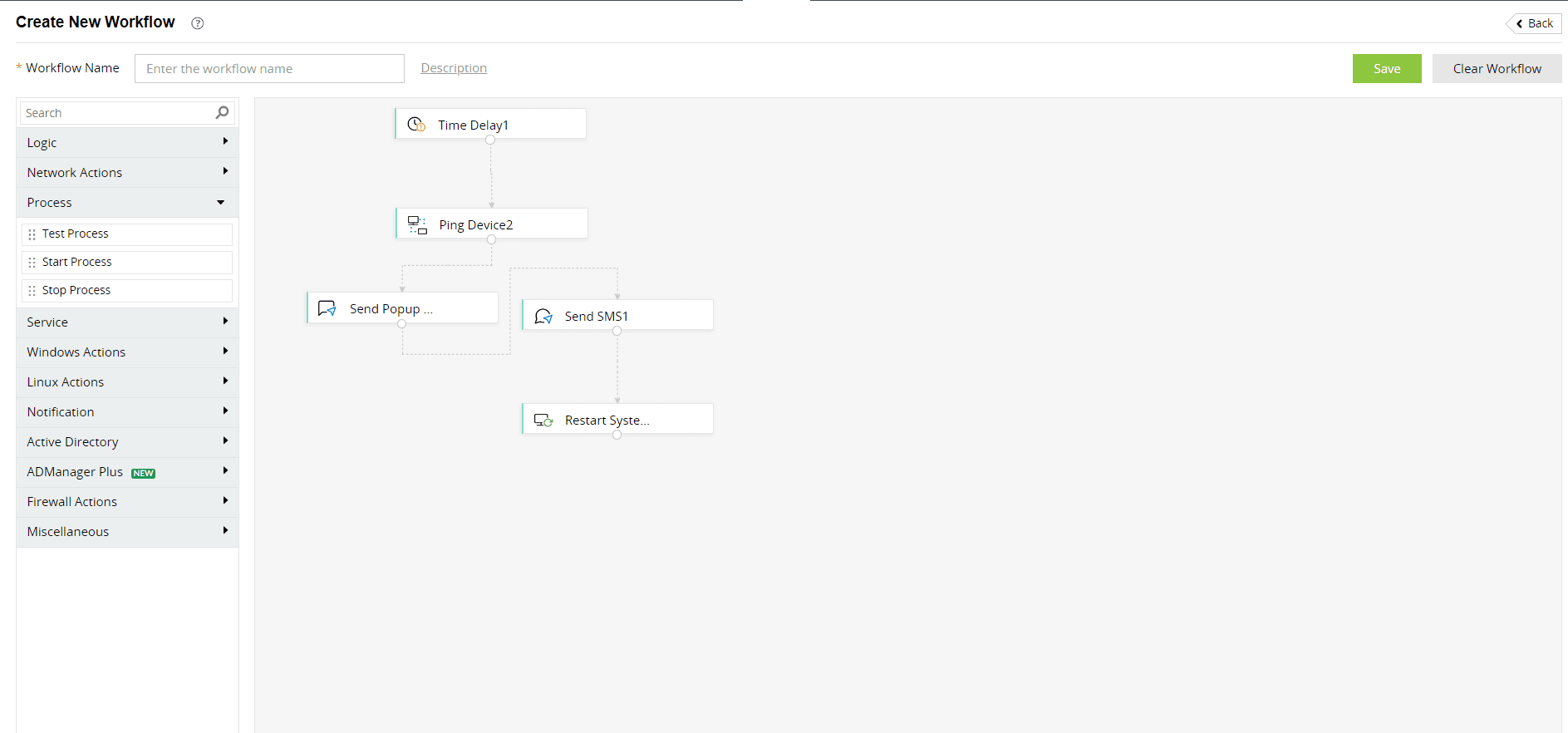
Figure 6: Creating incident workflows using Log360.
7. Review and update
Review and update your file integrity monitoring tool's rules and configurations on a regular basis to keep up with evolving threats and changes in your environment.
Log360 allows you to view dashboards and reports on all file and folder creations, deletions, changes, owner alterations, and permission modifications (Fig. 7). All failed attempts to access files are also recorded. For your security team, these capabilities offer several advantages, including early detection of possible dangers like ransomware, malware, and IT sabotage. This helps your organization reduce its mean time to detect incidents.
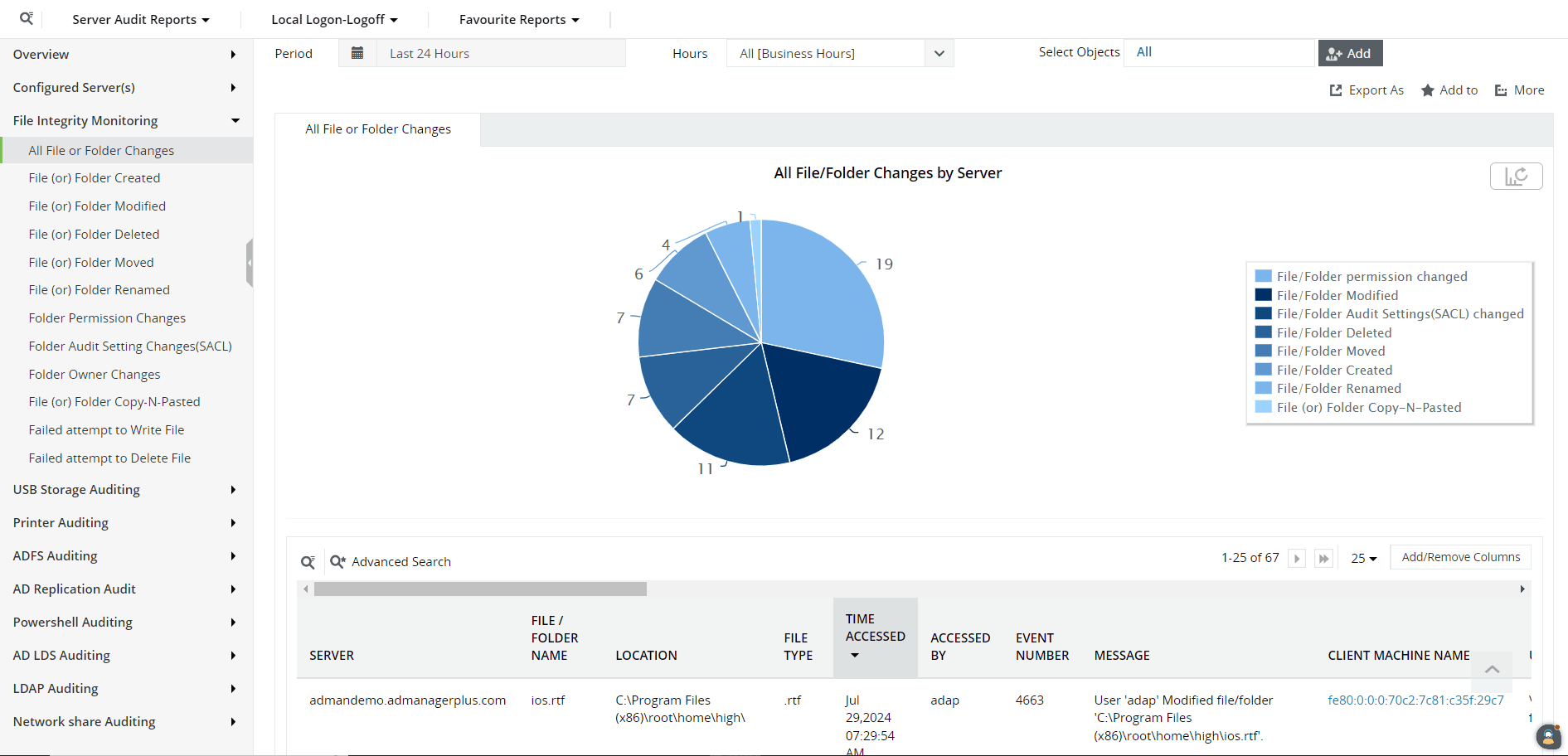
Figure 7: File integrity monitoring dashboards in Log360.
Review the actions performed on files and folders to determine whether any new threats are emerging. Ensure that the file integrity monitoring tool's alert rules and configurations are updated appropriately in order prevent such threats from occurring again.
Conduct regular audits and assessments to make sure your file integrity monitoring tool's implementation is efficient and compliant with security best practices.
By adhering to this procedure, you can set up a strong file integrity monitoring system that can help you identify unauthorized modifications while protecting the security and integrity of your systems and data.
Ready for the next step?
Are you looking for ways to protect your organization's sensitive information from being misused? Sign up for a personalized demo of Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.
You can also explore on your own with a free, fully functional, 30-day trial of Log360.



