File integrity monitoring (FIM) and file activity monitoring (FAM) are often considered similar in the sphere of IT security. Though these processes have a few overlaps, they are not same. Let's look the difference between FIM and FAM.
What is FIM?
FIM is a cybersecurity process that can alleviate your data security concerns. Working across systems such as Windows and Linux, FIM tools monitor unauthorized changes made to your sensitive files and folders to detect potential data breaches. You can think of it as a file change auditing system that reports activities like file creation, deletion, and modification along with file permission changes.
FIM is usually deployed at the workstation level to monitor changes to local files, folders, and directories. A comprehensive SIEM solution, such as ManageEngine Log360, integrates FIM capabilities into its feature set. By correlating FIM information along with other network information, a SIEM solution can effectively help you keep your business secure.
What is FAM?
FAM is a subcategory under FIM. FAM monitors anomalous user interactions with sensitive files and folders to detect potential insider activities. It is also known as file system monitoring, as it establishes access governance in file systems and file servers. It reports file-related user activities like attempts to read, write, copy, and paste files, ownership modifications, and file access permission changes.
File integrity monitoring use cases
Unauthorized changes to critical Windows files
FIM facilitates Windows file monitoring, which involves tracking unauthorized changes to critical Windows files such as Program files and System32 files. These files are typically stored in the local drive of all workstations by default. FIM comes with unique templates for monitoring such critical locations that are common across all Windows workstations. By utilizing default templates for critical file locations, FIM tools like Log360 can simplify Windows file monitoring for all workstations.
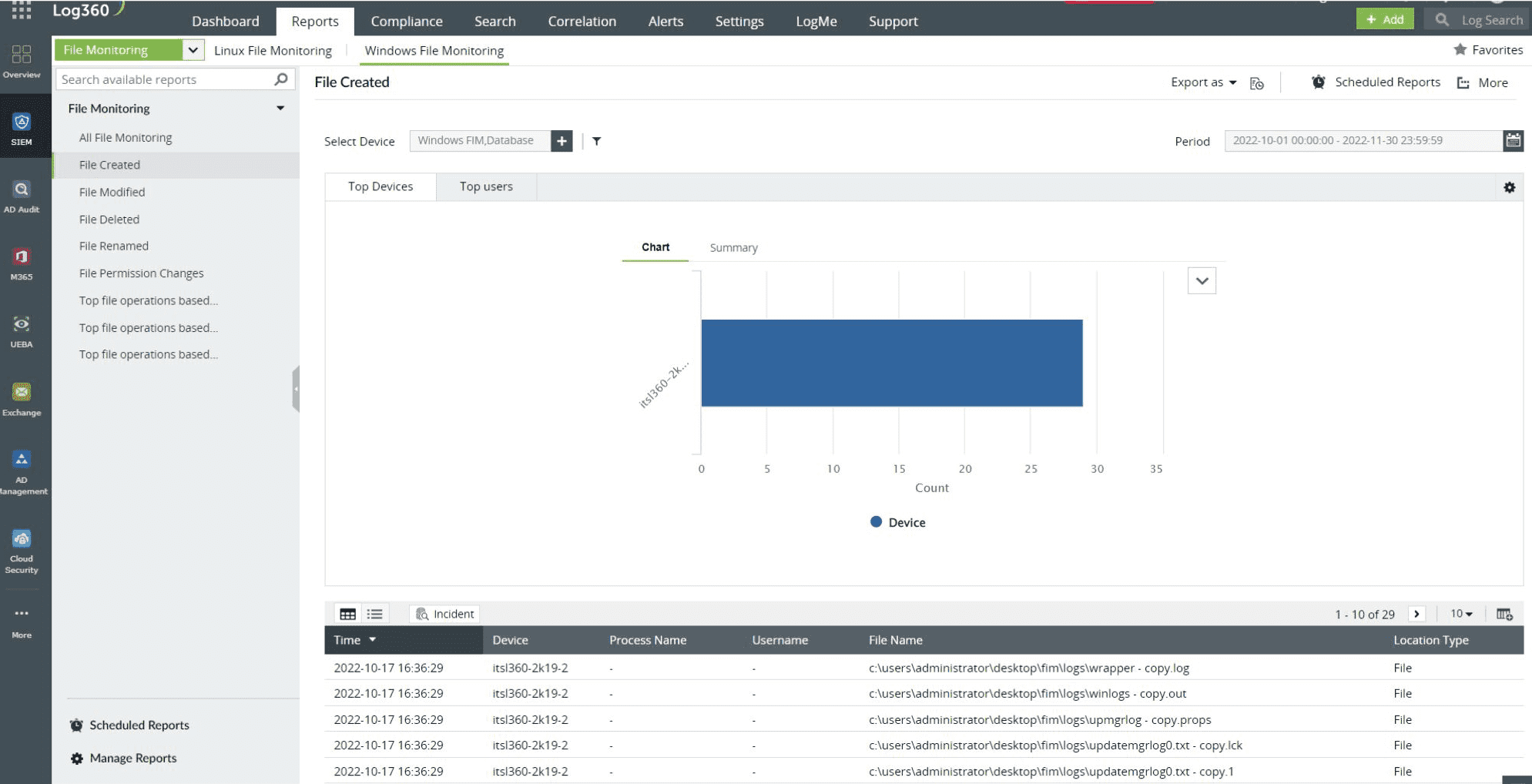
Figure 1: FIM report in Log360
Unauthorized access to critical file servers
Windows file servers are vulnerable to insider threats. File activity monitoring enables the detection of insider threats by facilitating Windows server audits. By tracking failed user attempts to read, write, or delete confidential files on critical file servers, file activity monitoring in Log360 helps you investigate data breaches and identify potential insiders.
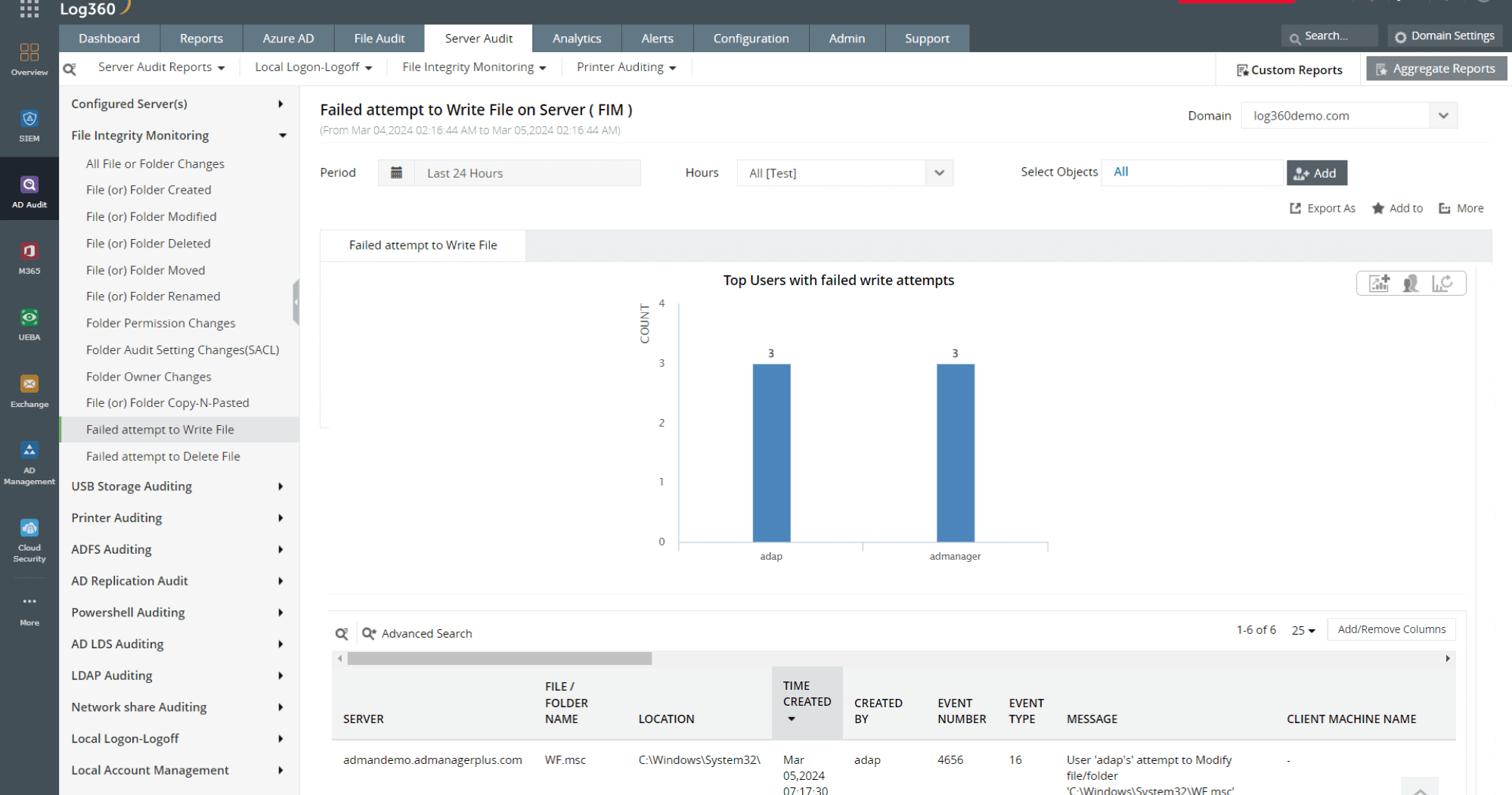
Figure 2: FAM report in Log360
Permission changes to critical files
FIM detects permission changes to all files and folders, including network shares. Adversaries often manipulate access controls on files to exfiltrate or sabotage sensitive data. Log360, with its predefined alert profiles, enables the detection of malicious permission changes to file shares and prevents data breaches with incident workflows.
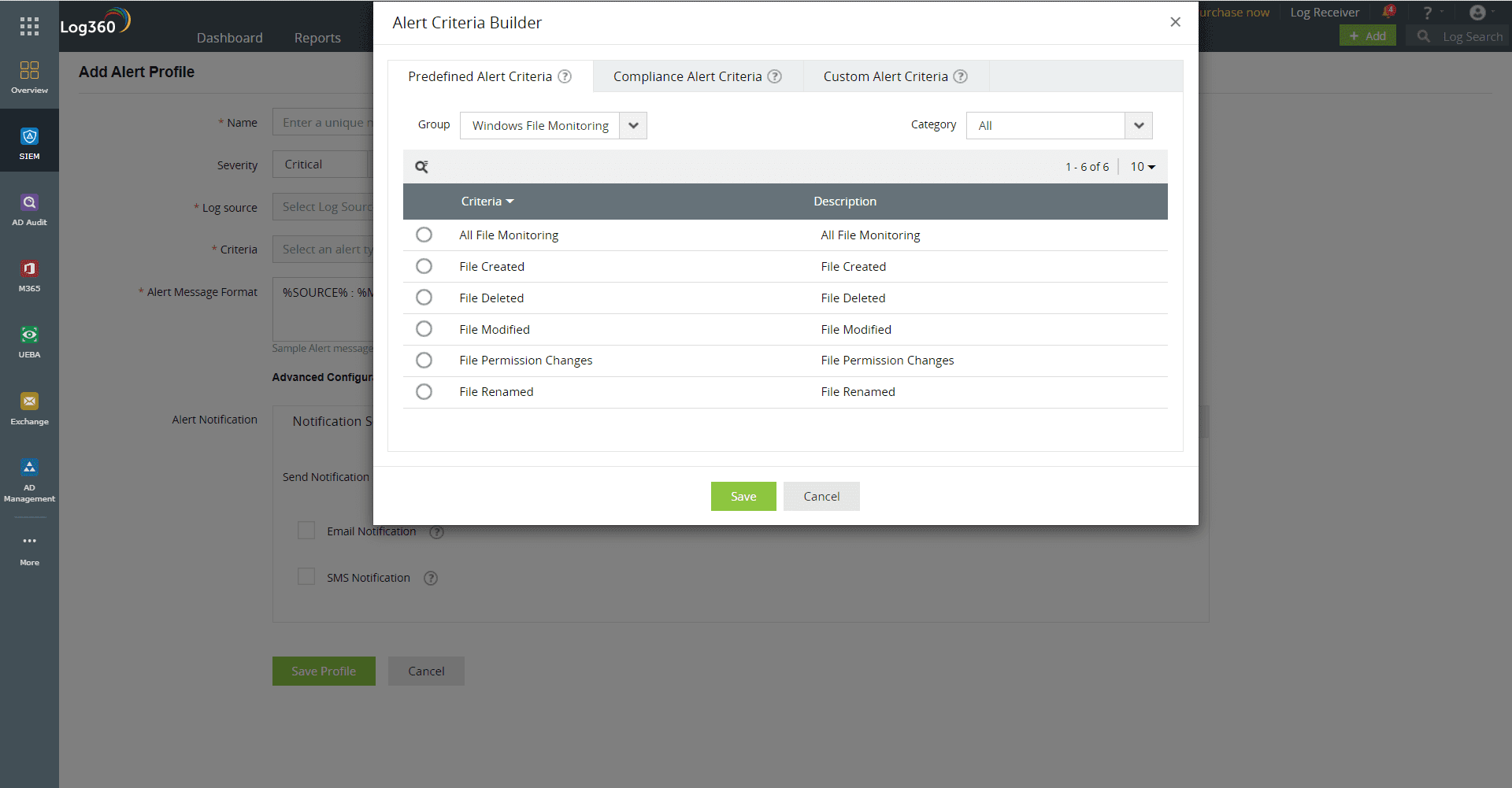
Figure 3: Predefined FIM alert profiles in Log360
FIM in Log360
ManageEngine Log360 can offer the benefits of FIM and FAM in a single console. Here is a glimpse of how FIM in Log360 can help you protect your sensitive files and folders.
- Monitor unauthorized file activities like file creation, deletion, and modification in real time.
- Track anomalous file-related user activities like attempts to read, write, copy, and paste sensitive data.
- Identify anomalous user activities with advanced user and entity behavior analytics (UEBA).
- Create custom correlation rules to detect illegitimate file tampering, data leakage, and data theft.
- Generate alerts in real time with predefined alert profiles for file monitoring and auditing.
- Enable proactive incident response workflows against potential threats with VigilIQ, the threat detection and incident response engine of Log360.
- Generate real-time, audit-ready reports to comply with mandates like HIPAA, SOX, the PCI DSS, the GDPR, and the GLBA.
It's time to ensure file confidentiality, integrity, and accessibility from the convenience of a FIM-integrated SIEM solution. Sign up for a personalized demo of Log360 and learn more.



