The risk appetite of every organization is different, because they all differ in what they consider to be risky and how much risk they're willing to accept—or consider acceptable—to achieve their goals. Determining the acceptable level of risk also depends on factors such as:
- The size and nature of their business.
- The economy.
- The industry they're in.
- Their competitors.
- Their pricing and revenue model.
Apart from this, organizations also have to consider the risk posed by users and entities to arrive at their risk score. But how do they do it?
How can organizations determine the risk score of users?
User and entity behavior analytics (UEBA), the anomaly detection capability of a SIEM solution, can help organizations determine the risk score of users and entities. Powered by machine learning algorithms, UEBA uses historical data to establish a baseline of normal behavior for every user and entity. It then monitors the users and entities in real time to determine if they follow the same pattern of behavior or if they deviate from it. Any deviation from the baseline of normalcy will be considered an anomaly, and depending on the degree of deviation, a risk score will be determined. Anomaly detection with machine learning has transformed the way in which cybersecurity teams identify threats. The risk scores provided by UEBA has helped security team prioritize threats. But what is a risk score and how does UEBA risk scoring work?
What is a risk score?
There are different methods and scales to assign risk scores to users and entities. One popular way is to consider the risk score as a value between zero and 100 that is assigned to each user and entity depending on the frequency and severity of deviations from the established baseline. The greater the deviation, the greater the risk. The deviations or anomalies can be a time anomaly, count anomaly, or pattern anomaly.
How does UEBA arrive at a risk score for specific users or hosts?
Apart from looking at the level of deviation (from the established baseline of expected activity) to assign the risk score, the machine learning algorithm is usually also programmed to look for criteria such as:
- The role of the employee and the privileges it provides: For example, a C-suite executive would have higher privileges and access to sensitive data compared to entry-level executives, posing a higher risk to the organization. An account compromise or a risky activity carried out from this account would have catastrophic consequences.
- The employee's resignation status: If an employee has applied for resignation and is serving their notice period, they pose a greater risk. For instance, an opportunistic employee who's leaving the company to join a rival might be tempted to exfiltrate sensitive client information or other confidential business information.
- The data stored on the server or system: A system or a server that stores sensitive data such as leads and customer information, revenue details, employee PII, product roadmaps, designs, and copyright data poses a greater risk, so unusual activity on such business-critical systems or servers would result in a greater risk score than the rest.
- The nature of the account: A service account or a non-human account used by critical applications or services would have higher privileges. This is because it requires these privileges to execute batch files and interact with operating systems and applications hosted across databases, devices, and file servers. These accounts, if compromised, pose a severe risk to the business, and will result in a greater risk score if any anomalous activity is detected.
In addition to these, UEBA also looks at the type of risk to determine the right risk score. So, what are the different types of risks?
What are the different types of risks that UEBA identifies?
The anomaly detection algorithm looks at four different types of risks to assign a risk score. These risks can be thought of as anomaly detection use cases as well.
-
Insider threats: Any threat to the organization's data posed by an individual inside the organization is known as an insider threat. It can be malicious, where the employee is deliberately trying to steal, modify, or corrupt the data; or it could be unintentional, where the user's account was used to steal sensitive information from the company. Some common indicators of insider threats include a new or unusual system or file accessed at an unusual time, or multiple authentication failures.
-
Account compromise: When a particular user's account is accessed by an unauthorized user, it is termed account compromise. This can occur when a user's password is weak or when an attacker uses sophisticated tools to decipher the user's password. Continuous login failures followed by unknown software downloads and installation are a sign of account compromise.
-
Suspicious logons: Any attack, irrespective of its origin as internal or external, will need to have a successful logon at some stage. In the case of an external threat, a successful logon will probably be preceded by multiple logon failures. So, you could say that an anomalous logon is the first sign of an attack. You need to note that your UEBA solution should be capable of alerting on anomalous logon successes as well as failures to make sense of the bigger picture. For instance, a successful logon after multiple failed logon attempts could be indicative of a brute-force attack. An abnormal logon on a server or database could signify an impending threat or attack.
-
Data exfiltration: If an individual is making an unauthorized transfer of data to any user or entity outside the organization, it is called data exfiltration. It is a clear sign of an attack, so the risk score of the user rises exponentially. Your UEBA solution will assign a high risk score and alert the analysts to take immediate action to prevent a data leak. Some signs of data exfiltration are an unusual number of file downloads or data transfers via removable USB devices.
In all the above cases, irrespective of whether the user or employee attacks the system or network, or whether the attacker uses that employee's credentials to attack, that user's risk score will increase. The increase in the risk score is how your UEBA solution will alert the analyst of an anomaly. But, what are the factors that affect or influence risk scoring in UEBA?
How does UEBA calculate the overall risk score?
The anomaly detection algorithm in UEBA solutions differs from vendor to vendor. But this is how the anomaly detection model works in a SIEM solution like ManageEngine Log360 to determine the overall risk score.
After the algorithm has computed risks based on the different sub-risks mentioned above, it will calculate the overall risk score of the user (see Figure 1), taking into account the weight (or weightage) and decay factor assigned to each of the risk types. Here, weightage refers to the importance assigned to that specific sub-risk, and decay factor refers to how soon the risk score will return to normal over time in the event of no further anomalies detected.
The overall risk score for users and entities can be calculated using the below formula:
Where:
w1 = Weightage assigned to insider threats
w2 = Weightage assigned to account compromise
w3 = Weightage assigned to suspicious logons
w4 = Weightage assigned to data exfiltration
DF1 = Time decay factor assigned to insider threats
DF2 = Time decay factor assigned to account compromise
DF3 = Time decay factor assigned to suspicious logons
DF4 = Time decay factor assigned to data exfiltration

Figure 1: Factors influencing UEBA risk score computation
Now you know how UEBA calculates the risk score of users and entities. But is it possible to further increase its risk scoring accuracy? If so, how?
How to increase the risk scoring accuracy in anomaly detection
The risk scoring accuracy of UEBA can be improved by factoring in peer group analysis and seasonality. This will help in reducing false positive alerts.
- Peer group analysis: Peer group analysis is a technique powered by machine learning algorithms in which statistical models are employed to identify users and hosts that share similar characteristics and categorize them as one group. The idea behind peer grouping is that, by identifying the context behind a user's behavior and comparing it with the behavior of a relevant peer group, the risk scoring efficiency and accuracy will increase. You can learn more about peer group analysis by reading this resource: Digging deeper into peer group analysis.
- Seasonality: If an activity occurs with a specific degree of regularity, such as hourly, daily, weekly, or monthly, it's considered seasonal. If this seasonal activity occurs out of routine, then it should be considered an anomaly, and your UEBA solution should be able to detect it. For instance, a database that is typically only accessed at the end of the month being accessed mid-month would be considered an anomaly. To learn about seasonality in depth here. To further learn how to improve risk scoring and threat detection with UEBA, read this e-book.
ManageEngine Log360 is a unified SIEM solution with integrated UEBA, DLP, and CASB capabilities that can help organizations thwart various cyberattacks. Apart from providing static and dynamic peer grouping capability and seasonality, Log360 also allows you to customize your risk score as shown in Figure 2.
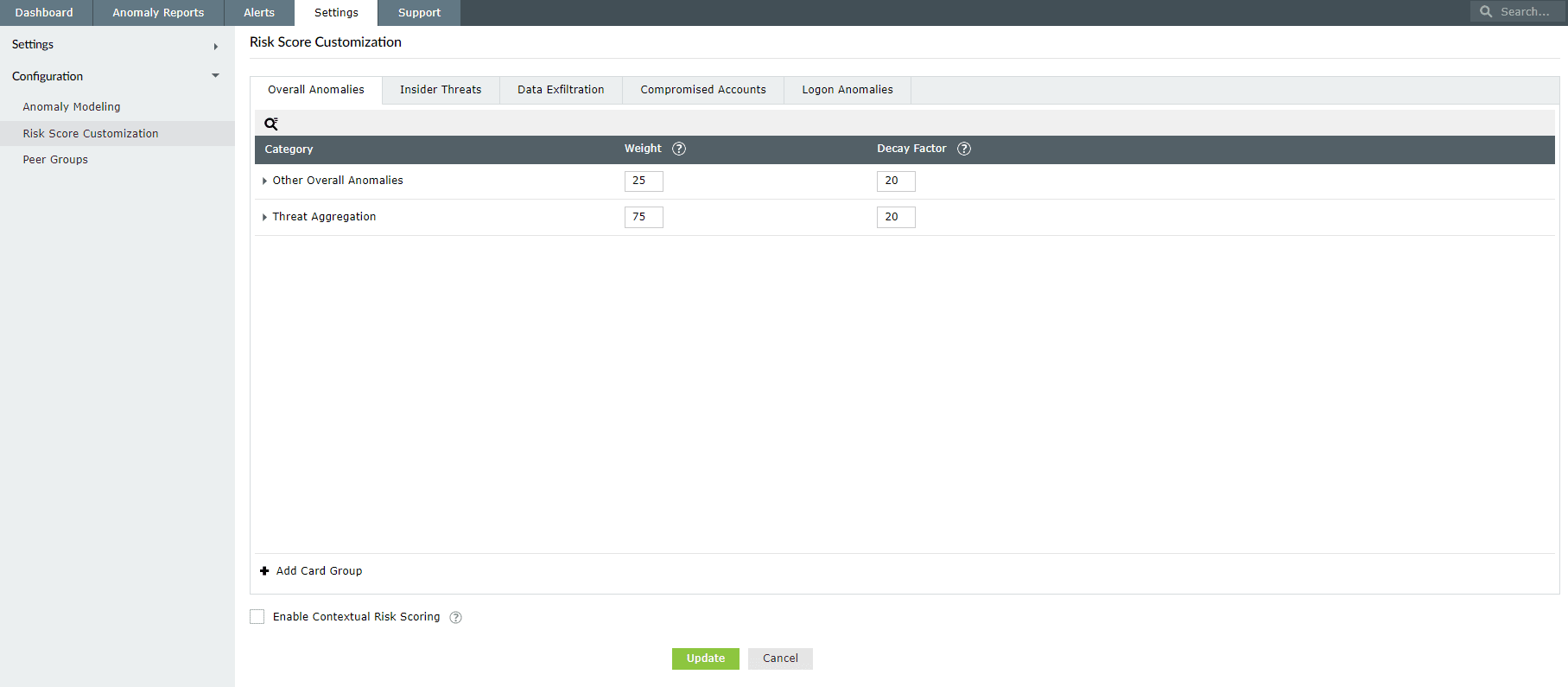
Figure 2: Risk score customization provided by Log360
To learn more about how the Log360 UEBA feature works, schedule a personalized demo and talk to our product experts.



