In any organization, a user may access numerous devices and applications, but not always with the same username or credentials. Consider for a moment whether your username is the same for your Linux, Windows, or SQL accounts. Devices and applications use platform-specific user registries that are distinct from each other.
Linking these user accounts is a common challenge organizations face, especially during single sign-on implementation. This administrative challenge can hinder an organization's security performance if the security analytics solution is not able to map user behavior across platforms and assign risk scores accordingly. Imagine monitoring various user accounts in separate silos, each with a different risk score, even though they all actually belong to the same user. This is the issue at hand. The figure below shows one user, Michael Bay, using different user identities to log on and access various devices and applications.
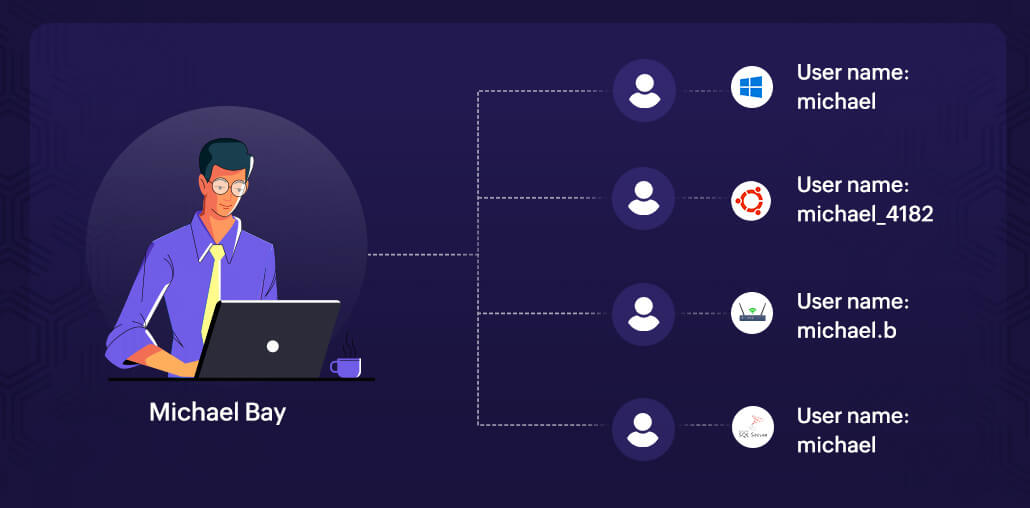
A UEBA solution is able to track anomalous activities of users and entities, and generates a risk score, thereby helping you track and prevent occurrences of insider threats, account compromise, and data exfiltration. To track anomalies more effectively, the UEBA engine in SIEM solutions leverage a feature called user identity mapping. This is how a SIEM solution knows that the different activities performed using different usernames are actually the actions of the same user (Michael).
What is user identity mapping?
User identity mapping (UIM) is the process of mapping different user accounts in an enterprise to a base account such as Active Directory by matching common attributes. With UIM, the activities of discrete user accounts from different sources are attributed to the one user who is actually performing them. So, when all of the user's identities are mapped, they will have just one representation and risk score. Having a UEBA solution with UIM can improve risk scoring accuracy and anomaly detection capabilities.
How does ManageEngine Log360 map user identities for enhanced anomaly detection?
Users are mapped across the network using their AD account as the basis, or Source Account using mapping configurations. Mapping configurations are rules that the admins can create using the UIM feature by specifying which of the user's source account attributes and target account attributes should match. The Source Attribute is a value from the user's AD data (e.g., SAMAccount_Name). The Target Attribute could be any field value in the target account (e.g., the SQL server's User Name field). Users identified by these specified attributes will be automatically mapped. Here's how it works in four easy steps.
- Admins create mapping rules (refer Figure 1) by specifying which of the user's Source Account (AD) attributes and target account attributes should match. All AD users and their details are automatically identified by Log360 when domains are added.
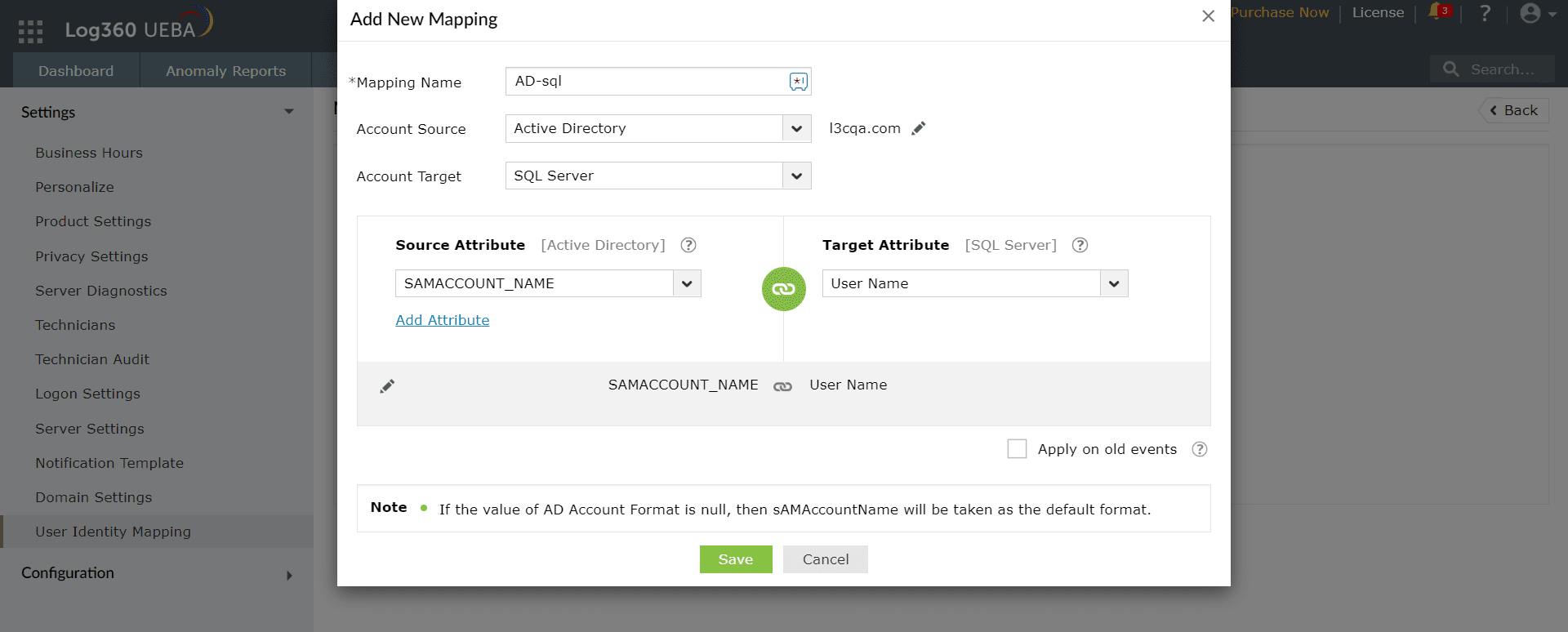
Figure 1: Creating new mapping to link user accounts using Log360
- Log360 will then look for user accounts across log sources that meet this criterion and map them to the user’s AD account.
- Admins can review these mappings and verify them.
- Admins can also create individual identifier rules for each specific AD user to map different user accounts to that particular AD user.
The individual user accounts are thus mapped with AD, and all anomalies associated with the user across sources can be viewed in a single dashboard.
The user accounts that were earlier considered separate and had individual risk scores, will now have only one representation and one risk score. The consolidated risk score is calculated from the individual's action across platforms (Windows, Linux, and SQL).
ManageEngine Log360 is a unified SIEM solution with integrated UEBA, DLP, CASB, and SOAR capabilities. Log360 collects logs from across the network, employs ML algorithms to identify suspicious activities of users and entities, and generates a risk score. The risk score is assigned based on the degree of deviation from the expected behavioral baseline, which helps you prioritize threats. Log360 improves risk scoring accuracy by factoring in peer group analysis, seasonality, UIM, anomaly modeling, and enables you to customize your risk score. To learn more, sign up for a personalized demo with our product experts.



