Ensure 360-degree file security and integrity with Log360 FIM
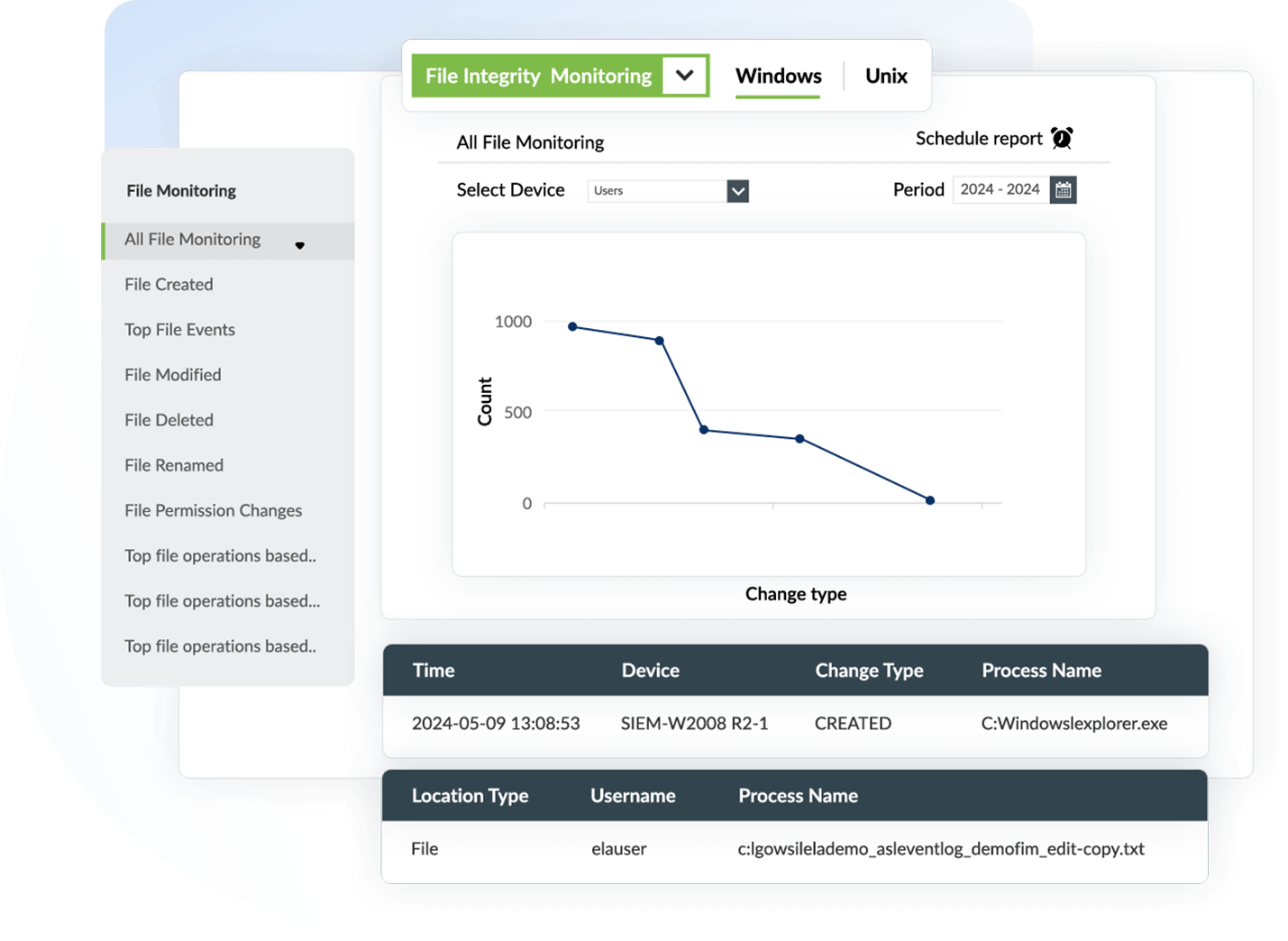
Windows/Linux file integrity monitoring
Log360 FIM monitors malicious file changes in both Windows and Linux environments. Unauthorized access to confidential files within Windows/Linux systems—including system files, configuration files, directory files, and registry files—causes disruptions that impact file security and integrity.
Log360 tracks suspicious file activities such as file creation, modification, deletion, renaming, and permission changes in real time to generate audit-ready reports instantly.
Track malicious insider activities
Log360's advanced file integrity monitoring capabilities help you flag anomalous file activities that signal the danger of insider threats within the network. Malicious insiders gain access to files and folders on critical file servers to manipulate, tamper with, or exfiltrate data, thereby compromising file integrity.
Using Log360's predefined reports and alert profiles for file integrity threats, you can track and detect insider activities in the network. These predefined alert profiles include automated incident response workflows that, when enabled, help contain data breaches and prevent further escalation of attacks.
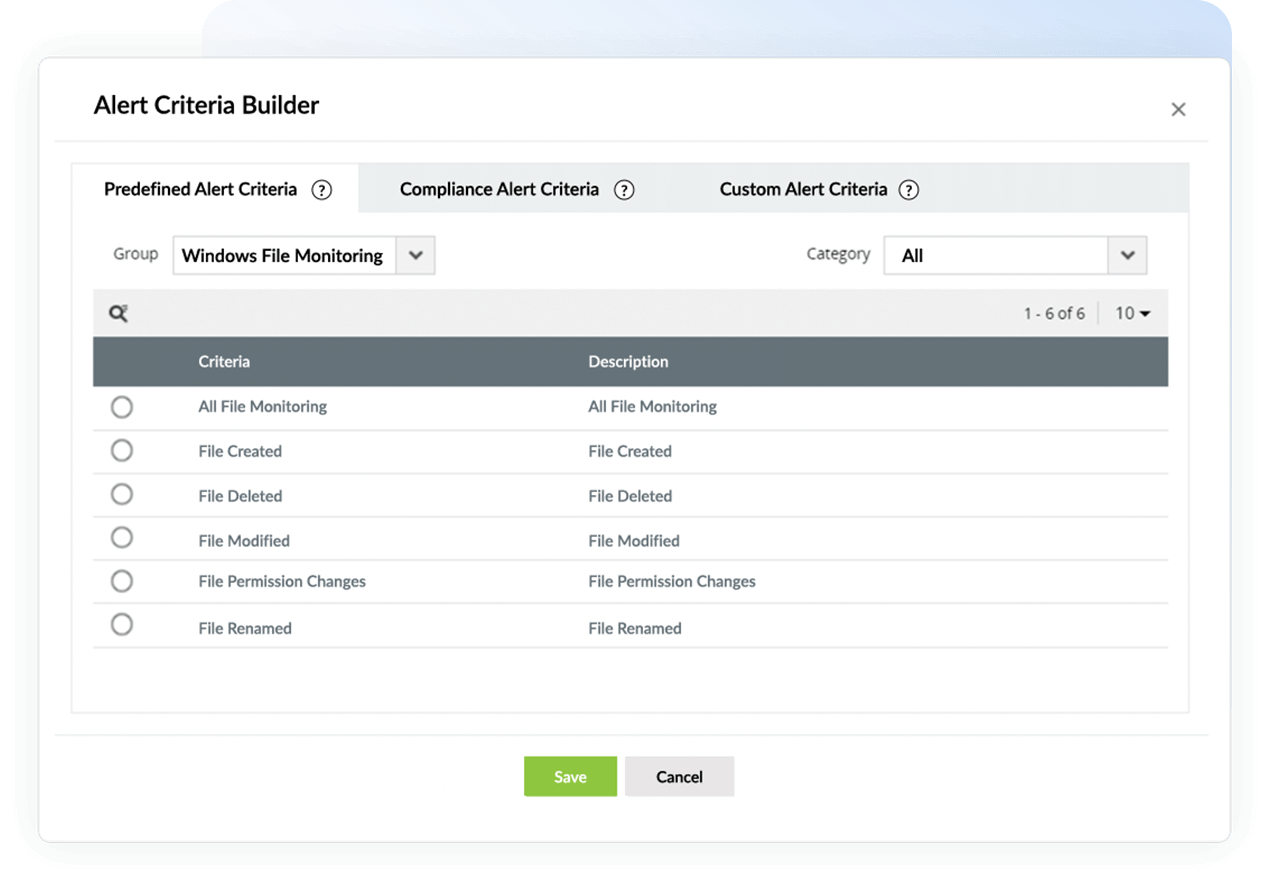
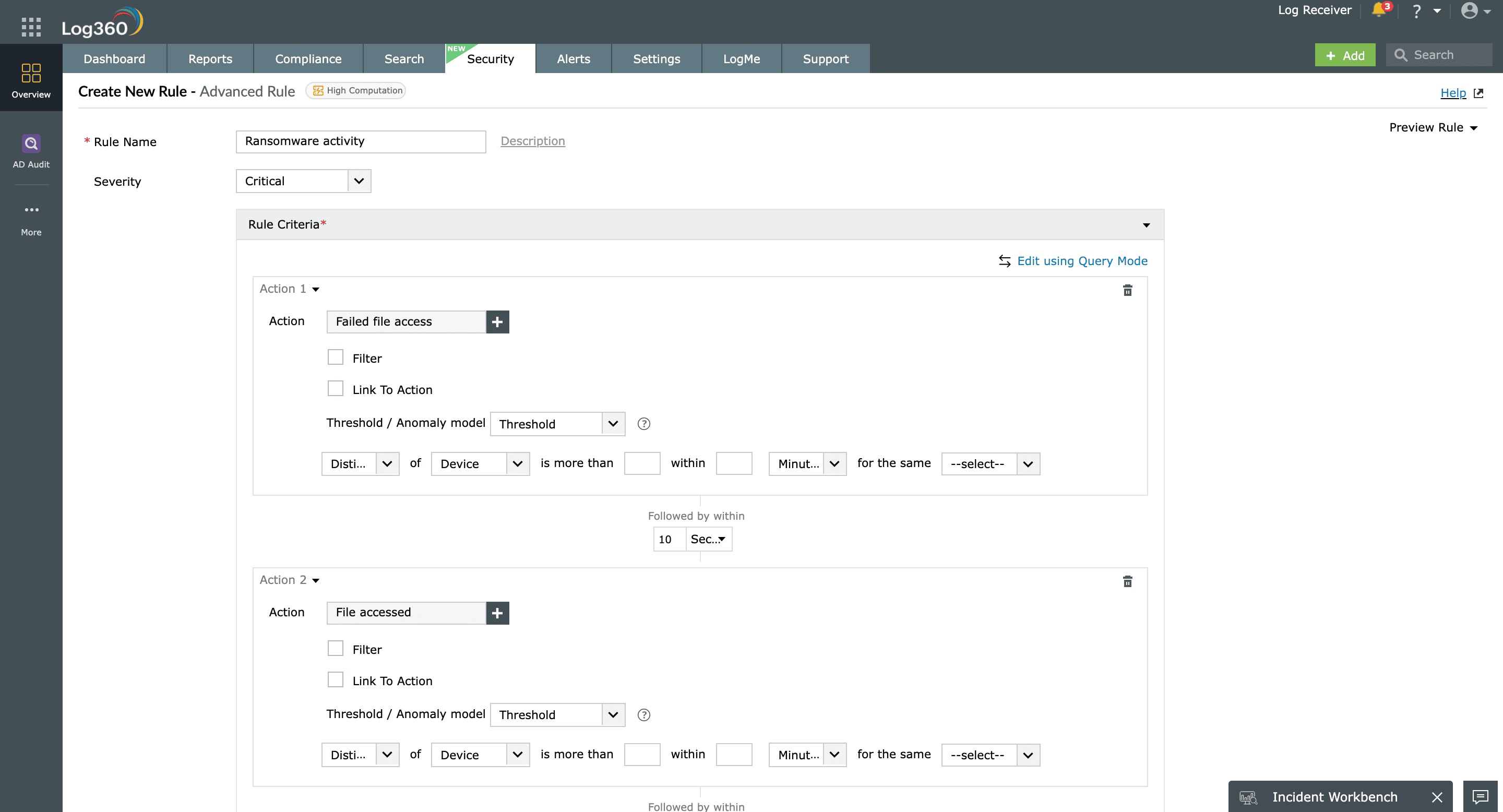
Detect and defend against ransomware attacks
Log360 FIM monitors and reports unusual spikes in file modification, deletion, and rename activities that might indicate a ransomware attack. A ransomware attack disrupts business continuity by modifying, encrypting, and renaming confidential files, rendering them inaccessible to the business. It impacts the CIA triad, affecting the confidentiality, integrity, and accessibility of sensitive files on the network.
With Log360, a sequence of unusual file activities such as unauthorized access, modification, and renaming can be mapped using custom correlation rules to flag a potential ransomware attack.
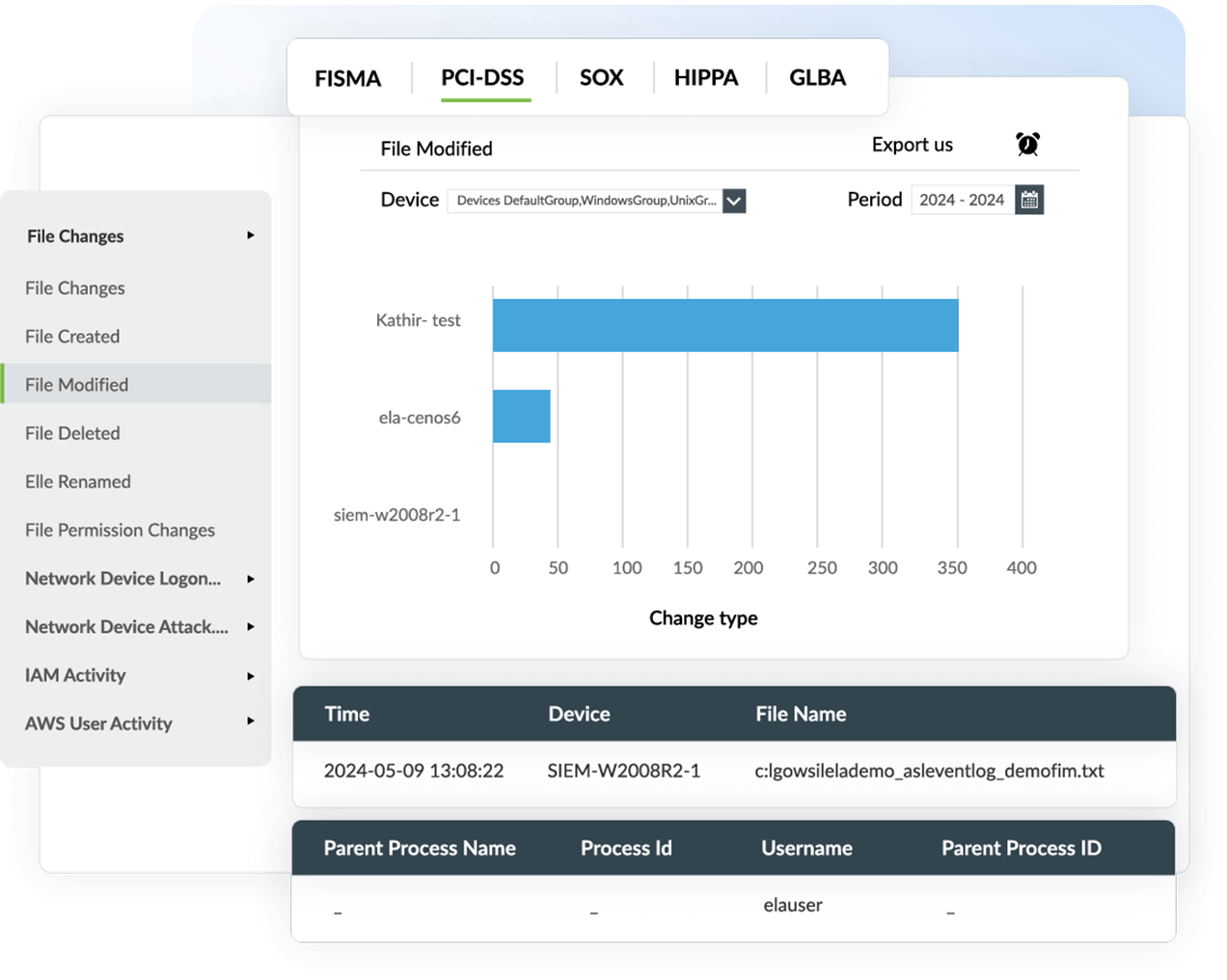
Comply with PCI DSS, GDPR, HIPAA and more
Log360 provides comprehensive audit reports for data security compliance mandates such as PCI DSS, the GDPR, HIPAA, FISMA, SOX, and GLBA. These mandates establish policies and standards for data security in organizations handling PII, personal financial information, payment card details, patient health records, and insurance details.
Log360 ensures data privacy with its out-of-the-box file activity reports, which monitor user activities and processes related to files. These reports can be archived, retained, and documented to demonstrate compliance with regulatory mandates.