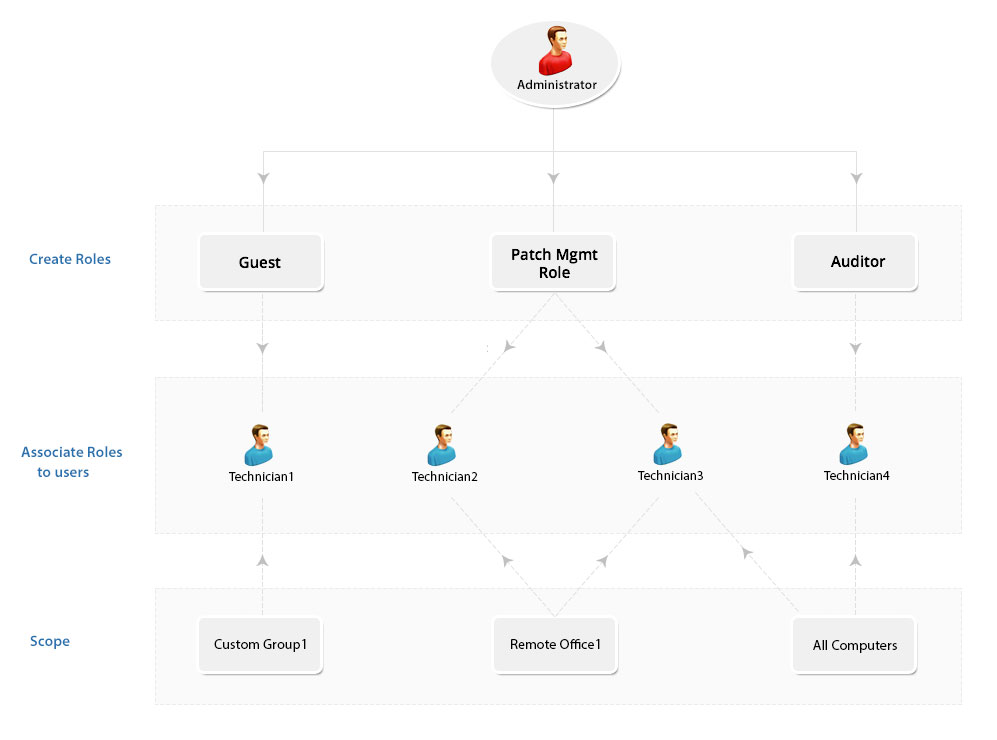
As an administrator, many a time you would have felt mundane routines spill over crucial attention-seeking jobs of your network. Patch Manager Plus answers this concern through its User & Role Management module; delegating routine activities to chosen users with well-defined permission levels. You can easily administer the users, and define their scope to manage a specific set of computers.
Some of the most commonly used Roles are specified under Pre-defined Roles. However, you also have the flexibility to define roles that best suit your requirements under the User-defined Roles and grant appropriate permissions. Here's a brief on the Pre-defined and User-defined roles respectively:
You can tailor-make any number of roles, using Patch Manager Plus and give them permissions of your choice based on your personalized needs. These customized roles fall under the User-defined category. For a better understanding let us quickly see how to create a User-defined Role in the following section.
Follow the steps mentioned below to create a new user-defined role:
The permission levels are broadly classified into:
You have successfully created a new role. The role you have just created will now be available in Roles, in the user creation module. Role deletion cannot be performed if that role is associated even with a single User. However, you can modify the permission levels for all User-defined roles.
You will find the following roles in the Pre-defined category:
Administrator: The Administrator role signifies the Super Admin who exercises full control, on all modules. The Administrator role signifies the Super Admin who exercises full control, on all modules. There can be only one super admin for an organization. In case the super admin leaves the company, you can re-assign any administrator as super admin. However, this can be done only by logging in as super admin. A super admin will also have the privilege to move users from one org to another.
The operations that are listed under the Admin tab include:
Auditor: The Auditor role is specially crafted for auditing Purposes. This role will help you grant permissions to auditors to view the details of the patch summary and reports. Users with Auditor role are limited to read-only access.
Guest: The Guest role retains the read-only permission to all modules. A user who is associated with the Guest role will have the privileges to scan and view various information about different modules, although making changes is strictly prohibited. Guest role also has read-only permission for viewing, details on patches management.
Patch Manager: The Patch Manager role has complete access to Patch Management. A Patch Manager will also have the privilege to access to perform tasks, like Wake-on-LAN, and the ability to schedule Patch Reports.
Technician: The Technician Role has a well-defined set of permissions to do specific operations. Users under the Technician role are restricted from performing all the operations listed under the Admin tab. The operations that can be performed by users associated with the Technician role include:
Patch Manager Plus provides you the privilege of defining a scope for the users, which means you can define the target computers, which can be mapped to every user. By limiting the user's permission to a specific set of computers, you can feel assured that the user has enough permission to perform their roles and not excess permission to take unduly advantage.
The target that you define as the scope can be one of the following:
When the target is defined as All Computers, the user will have permission to execute all the privileges defined in the role, to all the computers. Though the scope is all computers, the permission level is determined only by the role, to which the user is mapped.
You can create specific custom groups for management purposes and associate them with the users. The custom groups that you create should be unique so that no computers can belong to more than one custom group. These are computer-based custom groups, which are created for the user management purpose, and defined as 'scope' for the user. Refer to this to know more about Creating Custom Groups
You can create specific remote offices or use the existing remote offices to be defined as the scope for the users. More than one user can manage the same remote offices. Similarly, more than one remote office can be mapped to the same user. However, you cannot have a combination of remote offices and unique groups as a part of the scope.
More than one user can share the same scope. In such cases, configurations/tasks applied to the scope can be managed by more than one user. To know more, refer to this: Points to be noted
When a scope of the user is modified, the user will not be able to manage the configurations/tasks, which were created by him. She/he will have permission to clone the configurations without the target, so that he can re-use them for his current scope. Modifying the computers within the scope will not be considered as modifying the scope.
You can associate a user with a role while creating a new user. To create a user follow the steps mentioned below:
You have successfully created a user and associated a role with the user with the scope of the computers that need to be managed. Once a user profile is created, you can also choose to customize the user profile details by clicking on settings, after logging on to your Zoho account. To add multiple technicians, you can add users, here and the users will be sent an invite to join the organization, accepting the invite, users will be added to Patch Manager Plus cloud. (You can also inform the users to check their spam folder if they have not received the invite).
Patch Manager Plus offers the flexibility to modify the role of users, to best suit your changing requirements. You can do operations like changing the user role and resetting the user password at any point of time you feel you should.
At times when you find a user's contribution obsolete, you can go ahead and delete the user from the User List. The user so removed will no more exercise Module Permissions.