This feature is available on the Enterprise edition of Patch Manager Plus for builds 11.2.2338.1 and above.
Configuring password protection for the BIOS in the systems of the network is often the first step of defense in preventing unauthorized access to the system. In addition, this also forbids malicious/unauthorized users from making changes to the system's hardware and software configurations.
However, this added security layer can prove to be a hassle, especially when it comes to deploying BIOS updates across the endpoints in your organization's network. Since these updates require authentication via credentials before installation, this would mean relying on the end-users to input the credentials for a successful installation, thus leading to either productivity breaks or a lesser chance of successful installations.
Table of Contents
The Password-protected BIOS Patching functionality lets you deploy updates for the protected BIOS, without having to rely on the end-user for password authentication.
By leveraging this functionality, admins can store the pre-configured BIOS passwords of the end-user systems on the Patch Manager Plus server. This ensures that the BIOS updates are deployed and the passwords are automatically fetched and installed from the server storage, for a seamless installation.
Click here to learn how to identify if the BIOS on Dell machines is password-protected.
While this feature is enabled by default in the server, admins are required to add and map the credentials before deploying the patches for a successful installation. Here are the steps:
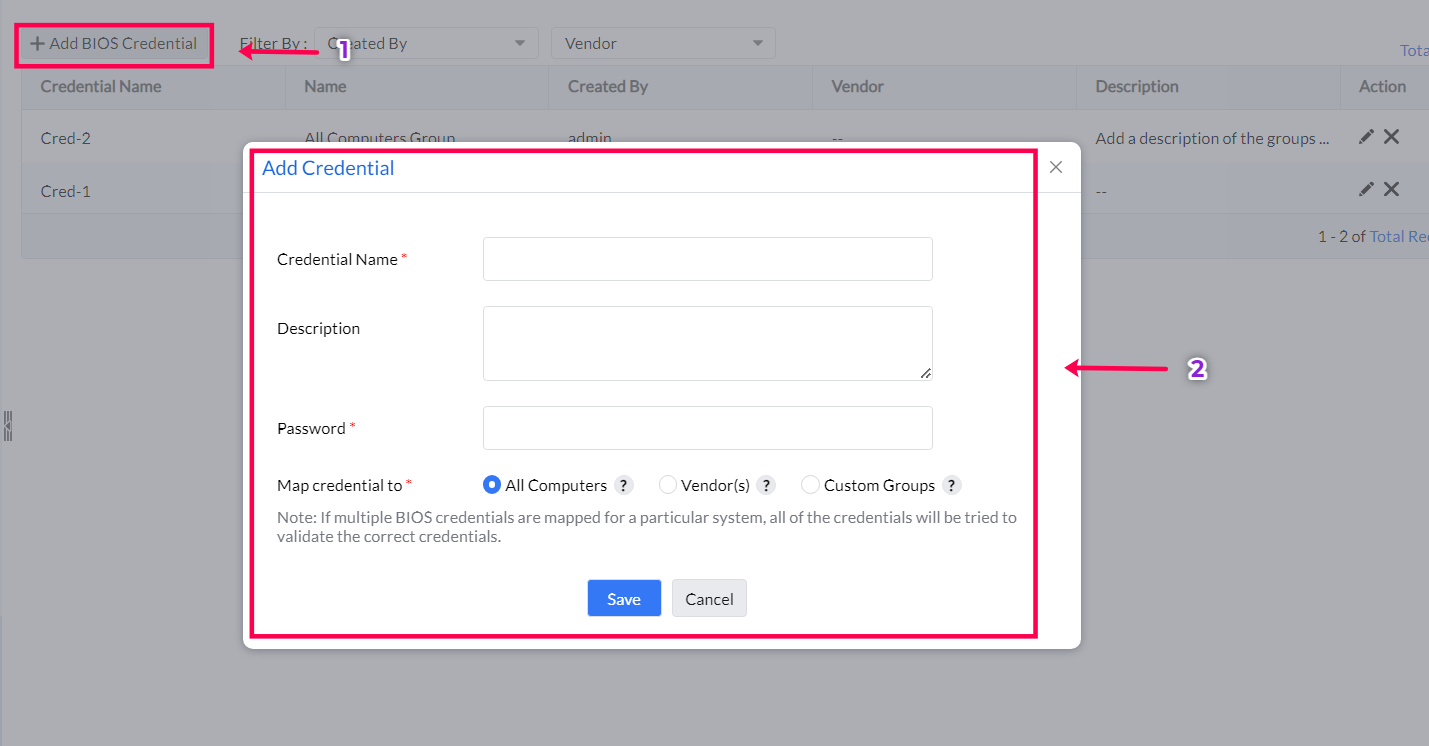
Once the credentials have been mapped, the BIOS updates can be deployed to the systems either via a Manual Deployment or via an Automate Patch Deployment task.
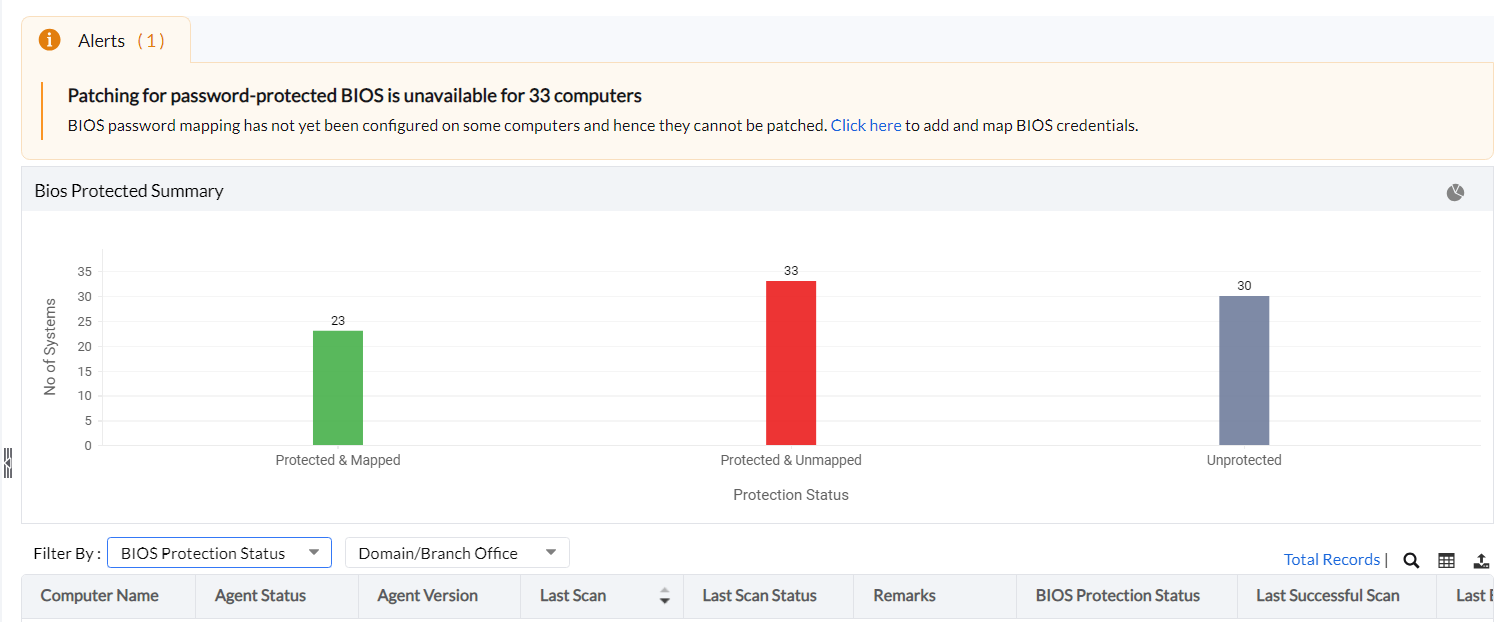
Admins can review and monitor the BIOS-mapping status of all the systems in the network from a single dashboard. To review the status of these systems on the console, navigate to Systems > BIOS Mapping Status (under Attention Required). The system status has been broken down into three types: