Patch Manager Plus periodically scans the systems in your network to identify the missing patches. The missing patches include both the operating system and third party application patches pertaining to that system. Generally, patches are released with varying severities ranging from Low to Critical. Based on these patch severities, Patch Manager Plus classifies the system into three categories to quickly identify the health status of the systems in the network. Health policy of the systems are calculated based on the missing security updates and third party updates. It is recommended to deploy all the security and third party updates to maintain the health status of the systems. If you do not want a specific missing patch, to impact the system health status, then you can choose to decline the patch. Patches that are declined will not be considered for the System Health Status calculation.
Users can view the severity of the patches right from the console. This allows them to prioritize the patching process and prevent the vulnerabilities in the network from being exposed.
Here's a look at how the severities of the patches are determined:
For OS patches
The severity of the patches are determined as provided by the vendors.
Example: For patches released for Windows OS, macOS and Linux OS, the severities of the patches displayed in the Patch Manager Plus console are similar to the ones specified by the vendor.
For third-party patches (ex. Google Chrome, Mozilla, etc.)
The severities are determined based on the following factors:
Based on the severity of the missing patches, the systems are categorized as Healthy, Vulnerable, and Highly Vulnerable in Patch Manager Plus. The default health policy is as below:
Healthy Systems are those that have up-to-date patches installed
Vulnerable Systems are those that have missing patches in "Moderate" or "Low" severity levels.
Highly Vulnerable Systems are those that have missing patches in "Critical" or "Important" severity levels.
|
You can customize the criteria to determine the health of a system. You can specify the number of patches, which will be considered as a bench mark to rate a system as highly vulnerable or vulnerable. Refer to the example explained below:
Criteria specified to mark a computer a highly vulnerable:
3 or more critical patches are missing
3 or more important patches missing
0 Moderate Patches are missing
0 Low severity patches are missing.
Criteria specified to mark a computer a vulnerable:
2 or more critical patches are missing
1 or more important patches missing
1 Moderate Patches are missing
0 Low severity patches are missing.
Based on the above mentioned criteria, if 3 or more critical patches are missing, then a system will be marked as highly vulnerable. If only 2 critical patches are missing, then it will be marked as vulnerable. If 1 critical patch is missing system will be considered as healthy. Assume 5 moderate severity patches are missing, then the system will be marked as Vulnerable. If 10 low severity patches are missing, system will still be considered as healthy, since you have not specified any number in the criteria.
You can configure the above explained settings by following the steps mentioned below:
Select the Admin tab.
Click the System Health Policy link available under Patch Settings.
Specify the number of missing patches to determine the health status of a system, based on severity and count of missing patches
Under Advanced Settings, choose to exclude 3rd party patches from system health calculation
Click Save Changes.
Most of the times, significance of missing 3rd party patches do not precede over the patches related to operating system. This could be because of the vast number of 3rd party applications and its real need towards the business. If you consider that your system's health should not be determined based on the missing 3rd party patches. You can configure your system health in such a way, that even if one or more 3rd party patches are missing in your system, it can still be rated as healthy if all OS related patches are installed on it. You can exclude all the 3rd party patches and choose to include few of those which might be needed.
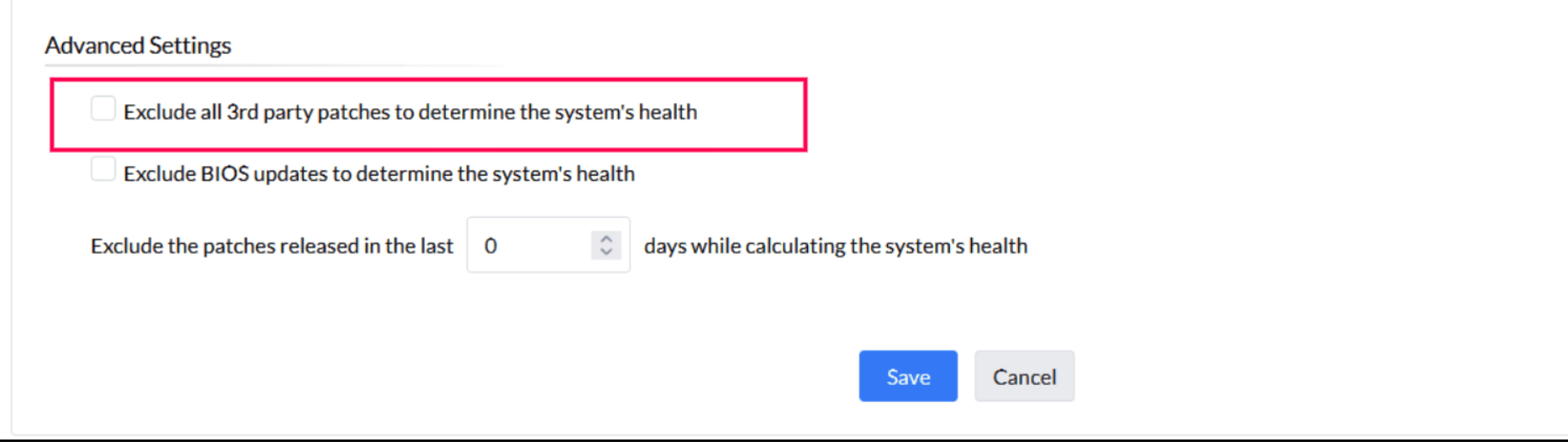
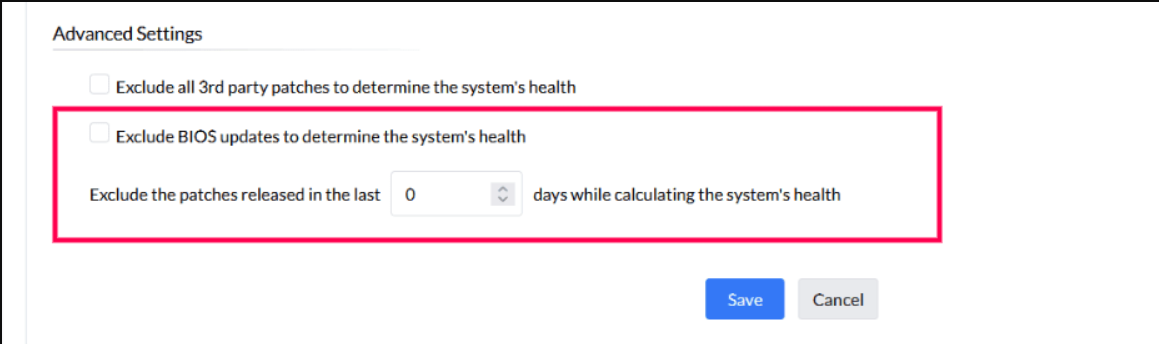
You also have the option to calculate the overall system health while excluding BIOS patches from the assessment. Additionally, you have the option to calculate system health by excluding patches based on their release date. This means you can choose to ignore patches released within a certain timeframe.
|