Note:
1) Available only in Patch Manager Plus on-premises version.
2) In case Tenable Security Center (formerly Tenable.sc) integration isn't available in your Patch Manager Plus server, kindly contact support.
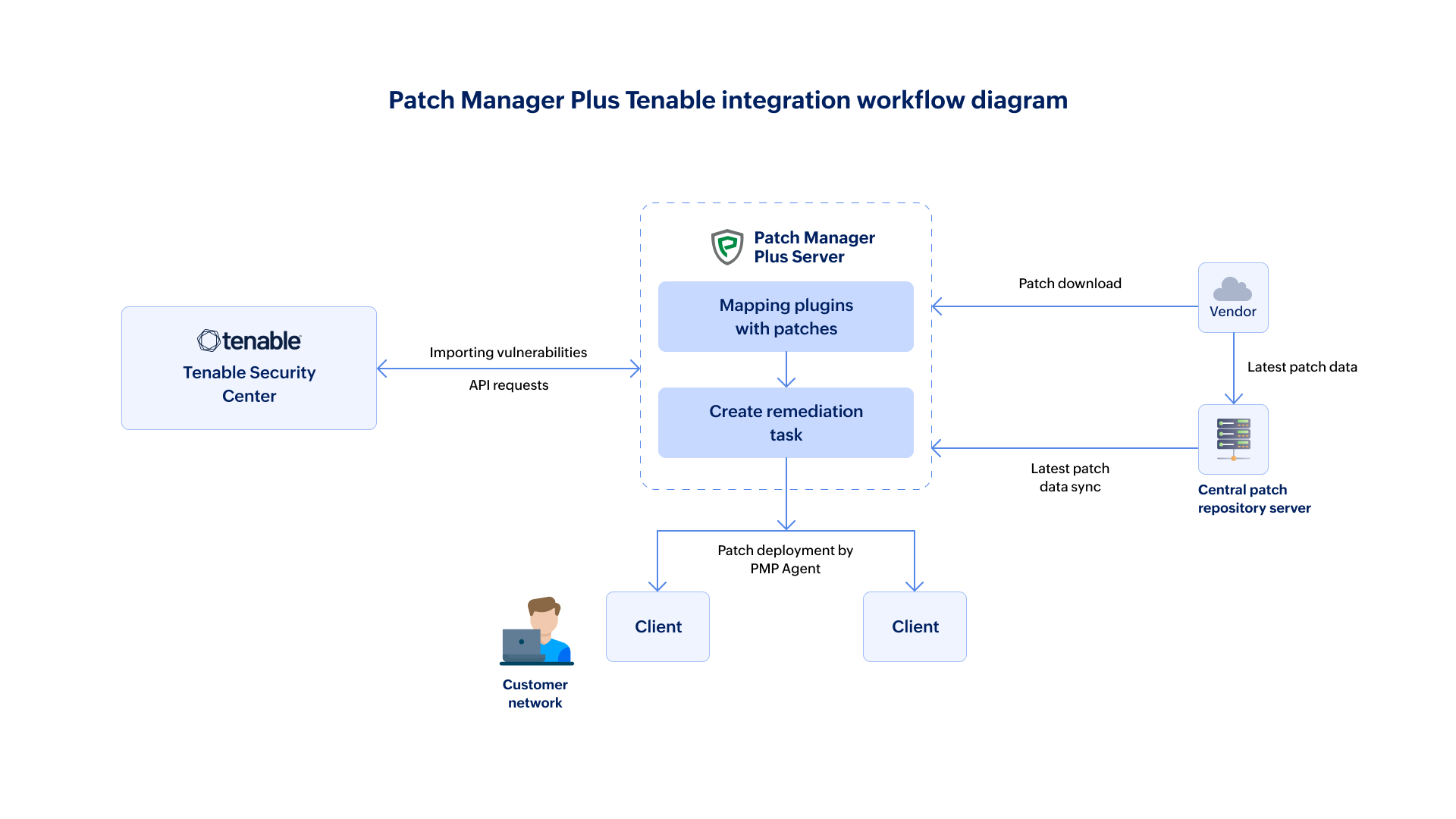
The integration of Tenable Security Center (formerly Tenable.sc) aims to bridge the gap between the detection of vulnerabilities and the deployment of patches. With this integration, IT admins can effortlessly deploy patches from the Patch Manager Plus console for the vulnerabilities detected by Tenable Security Center (formerly Tenable.sc). No more multiple dashboards, No more manual correlations between vulnerabilities and the relevant patches, the Tenable Security Center (formerly Tenable.sc) integration does all the work for you!
1) Will the required patches be updated automatically by Tenable or do we need to configure Patch Manager Plus to extract the scan result?
The Tenable API details are required to be configured in the Patch Manager Plus console (one-time setup). Once the integration is set, the vulnerabilities scanned by Tenable would automatically be imported to the Patch Manager Plus console and the required patches will be mapped.
2) Do we need to perform scanning after patching or will the data be automatically updated to Tenable after Patch Manager Plus patches the vulnerabilities?
Once a Manual Deployment task is created in Patch Manager Plus and the patches are successfully deployed, a scan is required to be performed in Tenable (this can also be scheduled). This will update the latest scan results.
3) Can I integrate Patch Manager Plus with Nessus?
Since Nessus does not support APIs for integration, it is not possible to integrate it with Patch Manager Plus.
4) How would patches be deployed to mitigate the vulnerabilities, post-integration?
Upon successful integration, the details of the vulnerabilities scanned by Tenable can be imported to the Patch Manager Plus console. Patches can then be deployed for the required vulnerabilities by creating a Manual Deployment task. Patches would not be automatically deployed (via Automate Patch Deployment tasks) for the imported vulnerabilities.
5) Why are certain vulnerabilities marked as Not Available in terms of Patch Availability?
Patches for vulnerabilities detected by Tenable are mapped by comparing with the imported CVE information. Specifically, only patches supported by Patch Manager Plus will be associated with Tenable-detected vulnerabilities. Check the list of supported applications for reference. Note: Patch Manager Plus currently does not support patching user installed applications.
6) Why are the imported vulnerability details fewer than the data present in Tenable?
Only vulnerabilities associated with certain Tenable plugin families are imported. Additionally, vulnerability details are imported solely for systems accessible to or within the scope of the specific integrated user.
Kindly contact support for any queries.