Managing Cloud Entitlements via PAM360
Cloud Infrastructure Entitlement Management (CIEM) is essential for organizations to manage and secure cloud identities in rapidly expanding cloud environments. CIEM focuses on identifying, analyzing, and managing the permissions/privileges assigned to the identities, providing clear visibility into who has access to what.
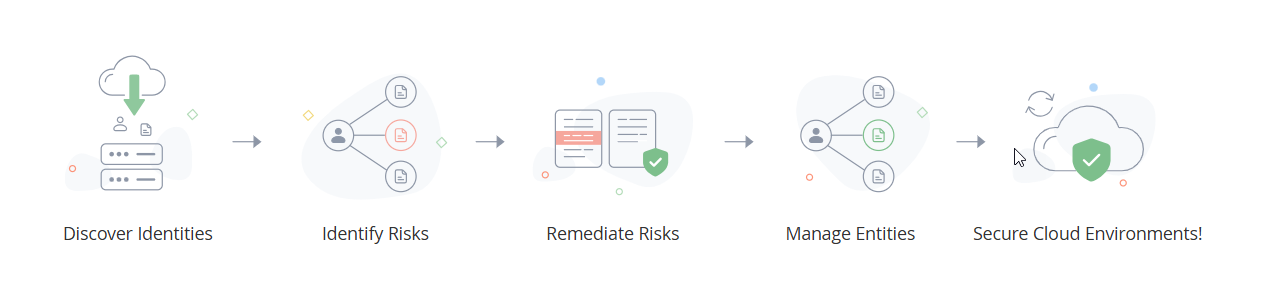
PAM360 is a comprehensive privileged access management solution that is now more advanced with its newly introduced Cloud Entitlements Management feature with the required CIEM capabilities. With PAM360's cloud entitlement feature, you can discover your cloud accounts, identify risks in your cloud environment, and remediate risks using the recommended actions. PAM360's cloud entitlement not only provides remediation for risk but also meticulously tracks all remediation activities, ensuring a secure and compliant cloud environment via PAM360.
Additional Detail
For the time being, PAM360 only supports the management of AWS cloud accounts.
Salient Highlights of Managing Cloud Entitlements via PAM360
- Enhanced Visibility: Gain detailed insights into entitlements and permissions across your cloud infrastructure.
- Risk Mitigation: Identify and address excess privileges and other potential security risks due to shadow IT permissions.
- Right-Size Privileges: Enforce a Just Enough Access (JEA) model by enforcing least privileges to all the accounts.
- Improved Security Posture: Reduce the risk of privilege escalation attacks by leveraging inline policies for your AWS account suggested by PAM360.
- Compliance Assurance: Ensure your cloud environment meets industry regulations and standards.
1. Roles and Permission
There are certain roles required in PAM360 to perform the necessary cloud entitlements management.
- By default, PAM360 users with Privileged Administrator and Cloud Administrator roles can completely manage the cloud entitlements and relevant audits carried out on the cloud accounts within PAM360.
Additional Detail
PAM360 allows users with Administrator, Privileged Administrator, and Cloud Administrator roles to disable the Cloud Entitlements tab when required. This can be performed via Admin >> Customization >> General Settings >> Miscellaneous.
- Apart from these predefined roles, you can also create a Custom Role with the Manage Cloud Entitlements privilege enabled to manage the complete cloud entitlements via PAM360.
- From build 8400 onwards, the Manage Cloud Entitlements privilege has been split into more granular, category-based permissions, Manage Cloud Accounts (Add, Reconfigure, Remove, Show Identities) and Risk Actions (Remediate, Revert). This granular breakdown provides administrators with finer control and more precise role delegation for users when managing cloud entitlements.
2. Glossary of Terms
While managing the cloud entitlements via PAM360, you will come across some terminologies that have unique meanings. It is worthwhile to take note of those terminologies before proceeding further.
| Terms | Description |
|---|---|
Access Map | A visual representation of access permissions involved in policies and services attached to an identity. |
Athena | An interactive query service in AWS that allows you to analyze data directly in Amazon S3 using standard SQL queries. |
CloudTrail | An AWS service that enables governance, compliance, and operational and risk auditing of an AWS account. |
Cloud Administrators | A PAM360 user role with administrative privileges to manage and configure AWS accounts in PAM360. |
Groups | Refers to IAM groups in AWS, which are collections of IAM users that share common permissions, simplifying access management. |
Identity | Denotes a user, user group, or role with assigned permissions to access cloud resources. |
Impact | The potential effect or consequence of a security risk on cloud resources. |
Permissions | Denotes the permissions granted to identities to access and perform actions on cloud resources. |
Policy | Denotes a set of rules and configurations governing access and permissions in the cloud environment. |
Remediate | An action or set of actions taken to resolve identified risks or vulnerabilities. |
Remediation | Denotes the process of addressing and correcting identified security risks or misconfigurations. |
Risks | Denotes potential threats or vulnerabilities that could compromise cloud security. |
Revert | An action or set of actions taken to revert the remediated risk. |
Roles | Refers to IAM roles in AWS, which are identities that grant temporary permissions to users or services for accessing resources. |
Services | Denotes specific functionalities or resources provided by cloud service providers. |
Shadow Admins | Users who have acquired administrative privileges unintentionally or without proper oversight. |
Time Stamp | The record of the date and time when an event or action occurred within the cloud environment. |
Users | Refers to IAM users created within an AWS account to represent individual users or applications with specific access permissions. |
3. Glossary of Symbols
| Symbol | Description |
|---|---|
Non-MFA User | |
Shadow Admin Privileges | |
Inactive User | |
Inactive Role | |
Non-Rotated Passwords | |
Non-Rotated Access Keys | |
Excessive Privileges | |
No Defined Risks | |
Critical Impact | |
High Impact | |
Medium Impact | |
Low Impact | |
No Impact |
To learn more about the process involved in managing the cloud entitlements from PAM360, refer to the following sections:
- AWS Account Discovery
- Cloud Entitlements Dashboard - A Walkthrough
- AWS Account Dashboard - Overview
- Risks Defined in PAM360 for Cloud Entitlements
- Summary of Available Users, User Groups, and Roles
- Remediating Cloud Entitlements' Risks from PAM360
- Audits and Reports of Cloud Entitlements












