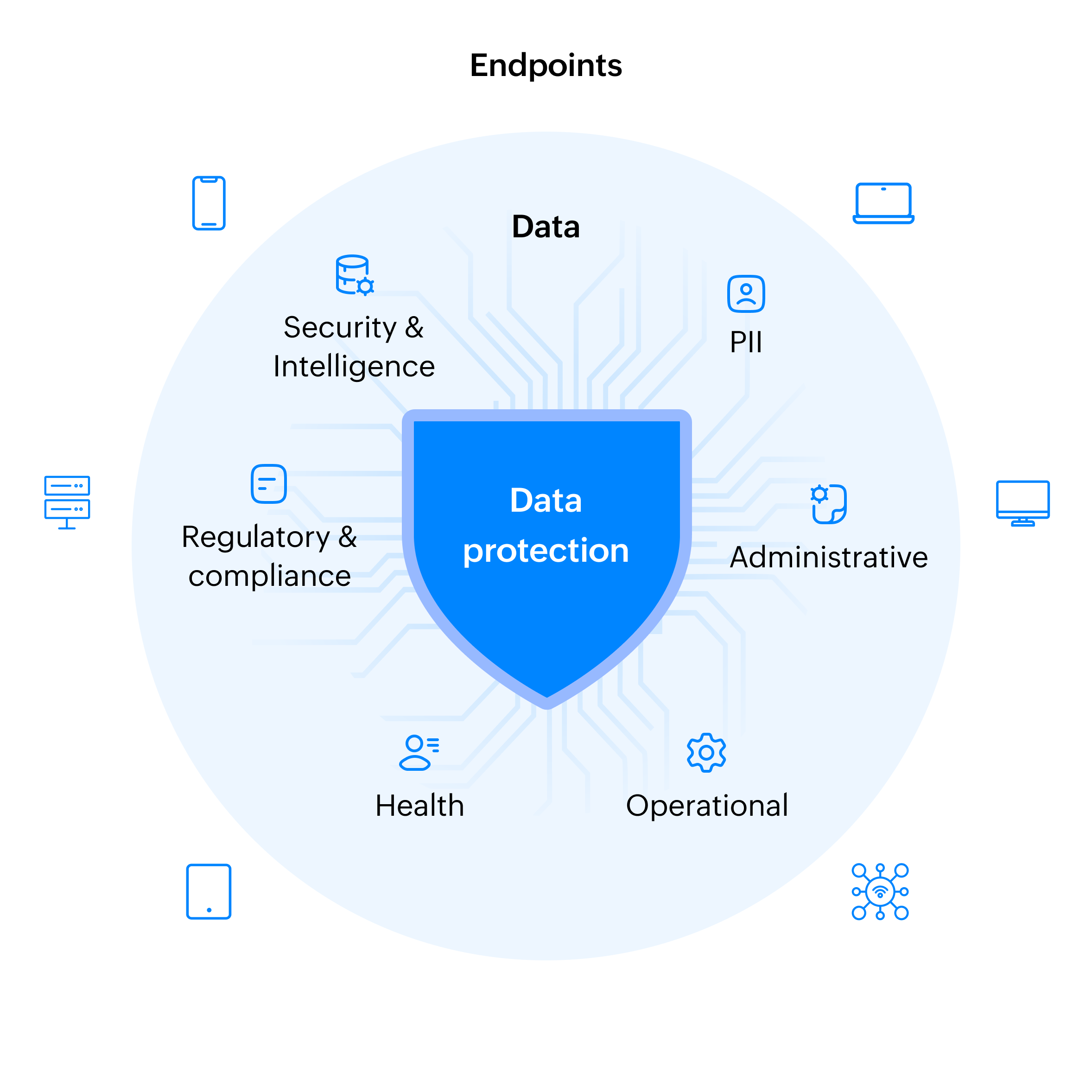
Endpoint Security for Government: Strengthen your GRC Strategy
Today's complex regulatory landscape revolves around data, and data resides on endpoints. Endpoint Central enhances governance by providing visibility and security across an organization’s entire endpoint estate.