Data Protection Officers are considered as modern super heroes to defend and secure business critical data of every enterprise. Realizing the need of the hour, ManageEngine's Endpoint Central (formerly known as Desktop Central) introduces a dash board exclusively for the DPOs.
This DPO dashboard empowers them by providing more clarity on the security status of the computers in the enterprise and detailed insights on the areas which needs to be on red alert for breaches. The dashboard can be accessed from the product console by navigating to Admin tab --> Security and Privacy --> DPO Dashboard.
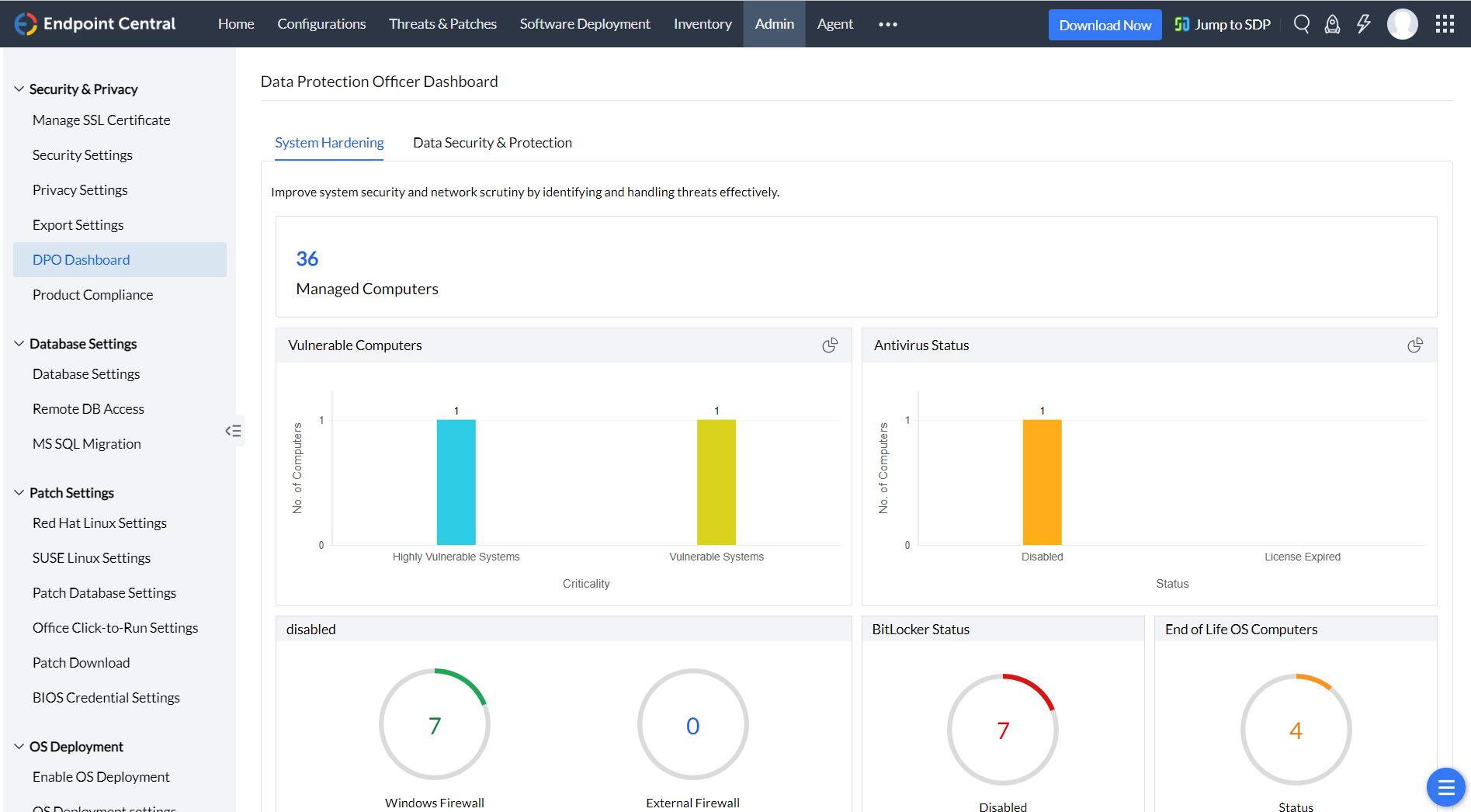
Scan your entire network and identify computers which are missing critical patches, on your laptops, desktops and servers. You can automate the entire patch management life cycle from detection to deployment by creating an automated patch deployment task. You can also verify the status of the anti-virus on the computers that are managed in the enterprise. You can also use Endpoint Central's definition updates feature, under patch management to update few anti-virus.
Configuring firewall becomes the most essential part of securing the network. DPO can understand the glitches on the firewall configuration from the dashboard. A quick summary can give insights on the status of the inbound and outbound firewall configurations. You can use Endpoint Central's Firewall configuration to enforce the firewall settings to your enterprise. Wireless transmission becomes more vulnerable when data is transmitted through unauthenticated Wifi connections. Using Endpoint Central's wireless configuration, you can secure the data transfer made using wireless transmission and enforce encryption using WPA or WPA2.
DPO can now limit the usage of vulnerable applications in the enterprise. DPO dashboard provides a clear summary on the number of prohibited software that are used in the network. You can use features like prohibited software and block executable to restrict the applications from the network. These configurations can be created and deployed to your entire domain or custom group. These policies will be forced on all the computers which becomes a part of this group.
Securing USB devices can never miss the check list, when data security becomes a concern. Using Endpoint Central you can not only secure unauthenticated USB devices, you can also tailor your needs like allowing USB devices to certain computers, or specific users or entertaining only corporate owned USB devices, etc., DPO can periodically check the DPO dashboard to identify the USB device policy and its usage in the network.
Data security and protection plays a vital role in escaping any potential breach or threat. Proper management of incoming and outgoing data becomes the wisest way to achieve complete data security. DPO provides you more information on various levels of data security from File level security, importance of configuring a strong password to encrypting confidential data using Windows Bitlocker and lets you understand and configure each one of them.
With these data breaches and cyberattacks, it has become mandatory for any enterprise to keep on track on the amount of data being shared across the network and to whom it has been shared to? and what kind of privilege does the person hold on the shared data? DPO has answers ready for you by furnishing information on,
Ransomware taught us enough on how important it is to keep track on computers with end of life Operating Systems. With Endpoint Central DPO, you can effortlessly get a detailed list of computers running on OS's that Microsoft had officially stopped supporting.
Effective management of user accounts in computers is of substance and can save any enterprise from data disasters. Endpoint Central DPO helps you get the list of AD computers with,
Let us say you encountered some virus in your network computer and you removed it. The infection is not completely out of your network until you empty your trash. Likewise, removing unused data and cleaning up disks periodically can save us from a lot of troubles. Endpoint Central has File/Folder configurations to remove unused from your network.
Browsers have become a significant part of any enterprise. They can also put your company into risk if not maintained properly. Endpoint Central's Browser configuration saves you from this misfortune with which you can define a default browser, search engine and proxy for your network computers. You can even restrict your users from accessing undesirable sites and define trustworthy ones.