Endpoint Security
Complete endpoint protection and autonomous threat response — from one platform and one agent — for your on and off network endpoints.
In the perimeter-less world, endpoints remain the largest attack surface. Our platform provides protection against a broad range of surfaces and vectors.

Control what apps and processes should run across your departments. Audit what would have happened if you had enabled the feature, so you can make data-driven decisions without impacting productivity.
Learn more
Protect against exfiltration by monitoring data movement and approved access to removable storage, printers, and USB drives.
Learn more
Move away from central proxies, and bring gateway and protection against web-based threats closer to the user via the endpoint's browser to support anywhere work.
Learn more
Apply the principle of least privilege and allow standard users to elevate their privileges for apps for justified use cases.
Learn more
Evaluate endpoints for security configuration exposures and harden them against widely recognized benchmarks such as CIS.
Learn more
Manage native security controls across multiple OSes from an unified interface, including Windows Defender, Firewall, Bitlocker and Firevault encryption, and more. Migrate your GPO workflows to our unified scripting interface to achieve control beyond native OS capabilities.
Learn more
Utilize our built-in mobile device management integrated with mobile threat defense partners for comprehensive device protection. Safeguard your device autonomously from phishing and mobile-based threats, implement app and data-only management for BYOD, and enforce risk-based device restrictions with conditional access for workspace suites.
Learn more
Restrict intranet access only to devices meeting security standards and organizational compliance.
Learn morePowered by in-house and integrated partner feeds, we bring you the industry's largest and fastest vulnerability content. Security teams can leverage analytics to prioritize risk, and collaborate with IT to automate response using built-in patching and configuration, ultimately reducing the MTTR.
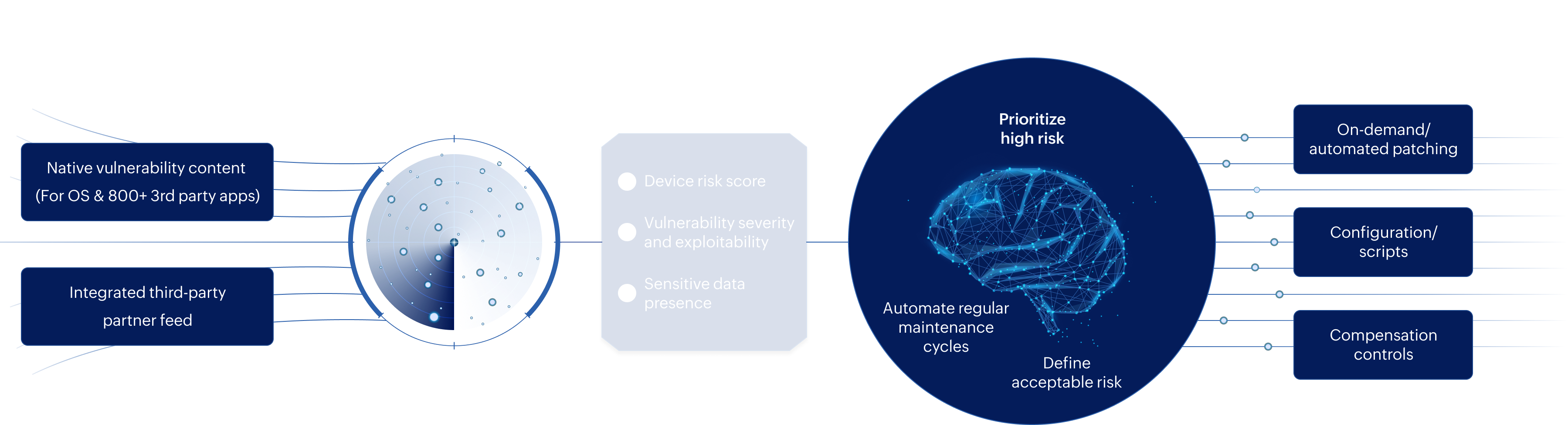

Identify sensitive data on endpoints per industry regulations and organizational IP to meet regulatory compliance and data security.
Learn more
Prevent endpoint data loss across various channels, including web, apps, BYOD, email, cloud storage, and removable media.
Learn more
Patented data back-up and restore capabilities to reverse encryption from ransomware attacks.
Learn moreDetect known and unknown threats with deep-learning ML and behavioral analytics. Autonomously contain threats, reverse damage, and quarantine endpoints at scale to prevent further damage. Each incident is linked to the MITRE knowledge base, and the entire attack chain is visualized contextually with all related events to understand the root cause. Resolve incidents through a full suite of surgical capabilities built into a single console.
Analyzes 10 million events/day on the endpoint edge to stop time-sensitive threats before execution.
Catch the unknown and file-less malware that escapes the AI by their behavior.
As most attacks result in data theft or encryption, be it espionage or financially motivated, the last line of defense ensures no threats evade you.
99.99% accuracy


9 of every 10 Fortune 100 companies trust ManageEngine






Together, let's build a brave new world, where our people can work safely from anywhere, on any device, with a rich experience across all their workplace services.
Key features include vulnerability & patch management, browser security, device & application control (including USB/peripheral restrictions), data loss prevention/encryption, anti-ransomware and next-gen malware protection.
Read moreBy scanning for misconfigurations, using security configuration baselines (e.g., CIS benchmarks), enforcing access controls, device encryption and applying role-based policies across all managed endpoints.
Read moreEssential types include threat prevention (malware, ransomware), vulnerability & patch remediation, device control (USB/peripherals), application control and privilege management, data protection (DLP/encryption), and browser security.
Read moreYes — modern enterprise endpoint security platforms include mobile device protection, BYOD policies, remote wipe, and conditional access for mobile endpoints.
Read moreYes – a unified enterprise endpoint security solution can scale to protect many endpoints across desktops, laptops, mobile and servers, offering centralized policy enforcement, monitoring and remediation.
Read more