Unmatched Endpoint Resilience that drives IT Governance
Protect citizen and mission-critical data while strengthening national security
Lack of real-time visibility and mishandling of outdated systems can create security gaps that can threaten operations, leaving the door open to a data breach.
Compliance mandates require various departments to prevent sensitive data from being leaked through endpoints. Gaining visibility into IT and controlling the data sprawl is instrumental since non-compliance due to configuration drift can lead to significant penalties.
Cybercriminals constantly adapt their tactics. Federal agencies may struggle to keep pace with the latest threats and implement appropriate defenses.
Data breaches, slow turnaround times, and lack of transparency can cause frustration among citizens and shake public confidence.




Secure your agency's digital footprint and simplify your government IT management
All features
Comply with regulations and standards by offering audit-ready templates aligning with compliance mandates.
Turn your corporate perimeter into a digital fortress by curbing data leakage from your network through hardware and browsers.
Restrict unauthorized access, prevent data exfiltration, and neutralize security threats by defining roles and controlling admin privileges with Endpoint privilege management.
Trim costs and complexities in standardizing management of modern and legacy systems, and securing attack surface, all within a single console.
Proactively detect, prevent and respond to ransomware attacks through real-time threat detection, behavioural analysis and malware protection.
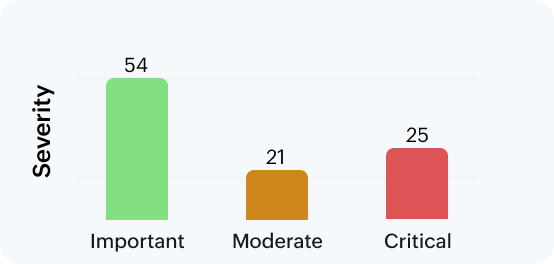
Unpatched systems are either a source of breaches or downtime. Prevent unauthorized access into your systems by routine scans and proactive vulnerability remediation.
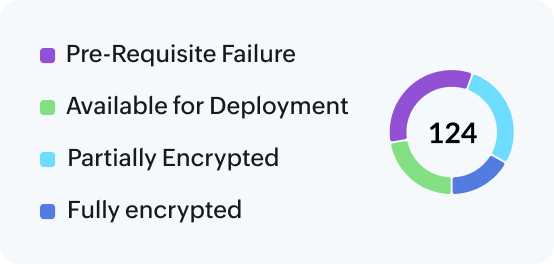
Reduce risk of data breaches by centrally managing recovery keys and encryption policies for smoother operations.
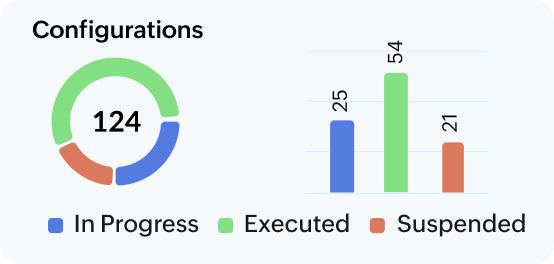
Endpoint Central gives you a consolidated view of your devices, apps, and users by letting you keep tabs on every aspect of endpoint fleet from onboarding to retiring.
Endpoint Central adds an extra layer of defense on top of your advanced intrusion detection systems to ensure a highly secure network. Secure your fleet with system hardening policies and continuous vulnerability monitoring on top of a predefined security baseline. Facilitate your Zero trust model with device-based trust signals and access controls.
Top 3 Imperatives:Gain visibility, protect data, and secure your healthcare services while complying with HIPAA. Shield both hospital and patient data (ePHI) against cyberattacks with Endpoint Central’s endpoint security features while ensuring the confidentiality and security of health information.
Top 3 Imperatives:Secure criminal records, implement strong privilege management and encrypt sensitive devices. Protect IT assets and data Judiciary-wide with patching, regular vulnerability scanning for identification and remediation of misconfigurations and system weaknesses. Endpoint Central lets you protect browsers by blocking malicious websites and plugins.
Top 3 Imperatives:Since Public infrastructure is the mainstay of any nation's economy, it is often frequented by cyberattacks, especially ransomware attacks. Beyond offering proactive security measures that strengthen your overall cybersecurity posture, Endpoint Central protects your organization from Malware, protecting your critical infrastructure and its operations.
Top 3 Imperatives:Safeguard citizen data in Social Services by enforcing strict access controls and robust authentication to prevent unauthorized access and identity theft. Endpoint Central goes beyond by encrypting data on devices, offering centralized management for consistent security policies, and maintaining audit trails for easier investigation. These measures build trust with the public and ensure the efficient and secure operation of critical assistance programs.
Top 3 Imperatives:In order to monitor, audit and enforce tax laws, Revenue and Taxation departments need to manage citizen data and IT infrastructure. While laptops and desktops are essential for user access to government networks and systems, they also pose significant security risks owing to system vulnerabilities, negligence, and insider threats. Endpoint Central can monitor devices for suspicious activity, detect threats in real-time, and take remediative actions like isolating compromised systems or quarantining infected files.
Top 3 Imperatives:Endpoint Central safeguards sensitive data, devices, and enhances network security in educational institutions. It ensures the integrity of academic records and personal information by managing inventory, deploying timely patches, and securing mobile devices. Wi-Fi protection and network segmentation bolster overall security, while content filtering and cyberbullying prevention prioritize student well-being.
Top 3 Imperatives:Endpoint Central safeguards critical research data, including climate and conservation data, from unauthorized access, tampering, and theft. By securing mobile devices used by environmental protection field agents and enforcing software updates through centralized patch management, Endpoint Central protects sensitive information and minimizes vulnerabilities across the endpoint infrastructure.
Top 3 Imperatives:Citizen and administrative data is at the heart of governance, and Endpoint Central safeguards it end-to-end.
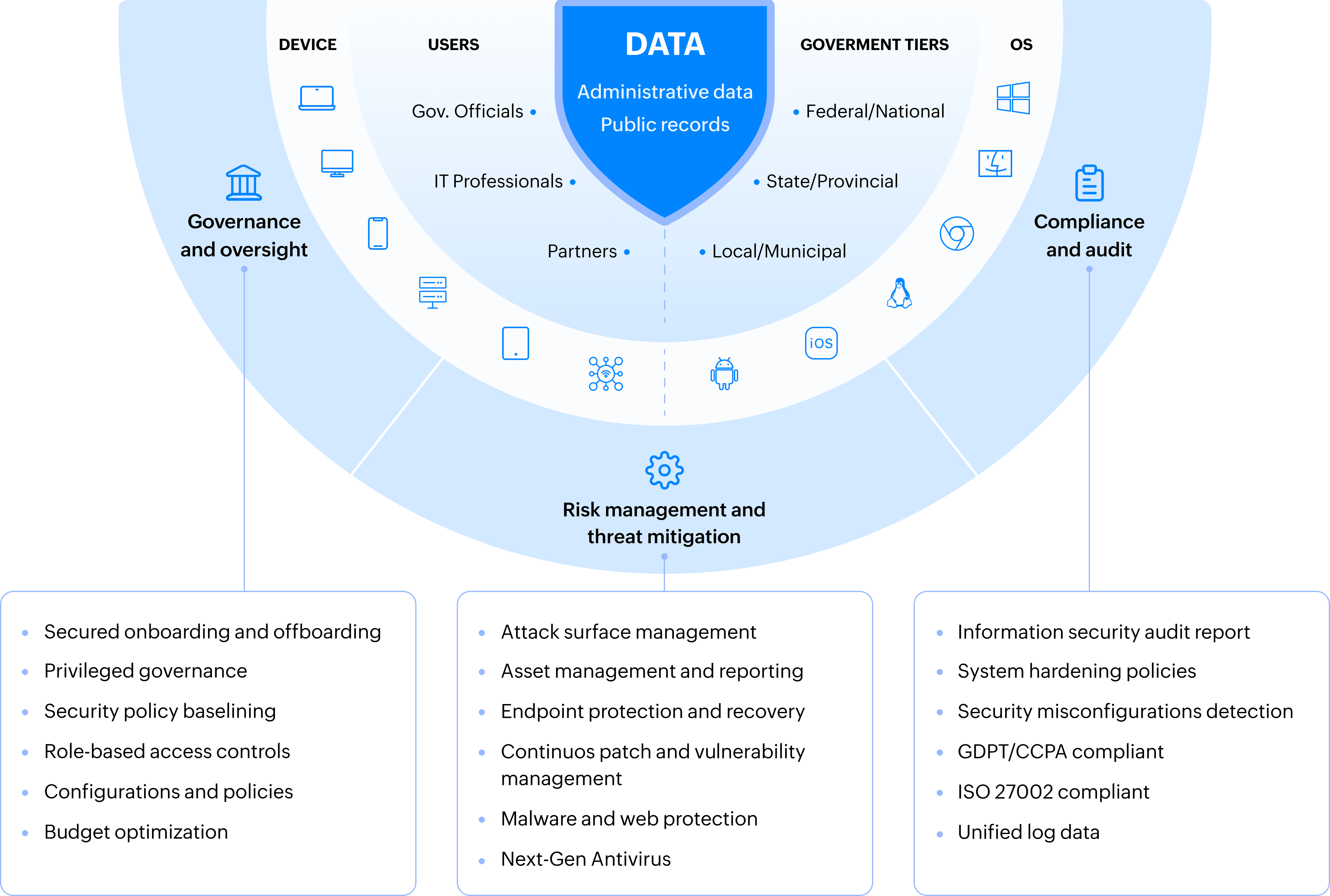
Empower and secure key stakeholders of your government IT while fulfilling their core priorities.







Only you truly own your data, and we don't even show ads, even in our free version. It has stayed that way for 20 years and will continue to do so. We make money by selling you paid subscriptions for Endpoint Central, not your private information
We've built our codebase from the scratch without any acquisitions. That means we own our core tech stack which allows us to deliver a seamless experience and provide the much-needed assurance for our customers.
We are not answerable to any investors since we have none. We are privately-held, and we intend to remain this way. This allows us to make decisions in the long-term interest of our customers and employees.
A curated collection of best practices, checklists and resources for IT professionals in Public sector and Federal departments
Tell us your pain points and concerns to get personalized assistance from our experts. See what you’ve been missing out.

Federal agencies can strengthen their cybersecurity posture by combining continuous patching, endpoint hardening, and zero-trust access controls. A solution like Endpoint Central automates patch deployment, monitors vulnerabilities, and isolates compromised devices to stop ransomware before it spreads, ensuring mission-critical systems remain secure and compliant.
Read moreAn endpoint management solution like ManageEngine Endpoint Central helps government IT teams securely manage large, distributed device networks. It supports strict compliance requirements, automates patching, enforces encryption, and provides complete visibility across all endpoints—helping agencies maintain security, reduce downtime, and ensure audit readiness.
Read moreA Unified Endpoint Management (UEM) solution simplifies compliance with mandates like NIST, HIPAA, and CJIS by enforcing standardized security policies, automating audits, and generating detailed reports. With Endpoint Central, agencies can encrypt data, control access, and monitor configurations to ensure every endpoint meets regulatory and security standards.
Read more
Trusted by your peers
"Within Endpoint Central, the Louisiana Governor's Office utilizes auto-patch deployment, inventory, and computer configurations such as monthly defragmentation schedules."
Jerry Wade,
Governor's Office, LA,