Create Policies for Effective Device Control and Security
Table of Contents
- Creating Device Access Control Policy for Windows
- Creating Device Access Control Policy for Mac
- Configuring Device Audit Settings
- Configuring Alert Settings
Device control policies are essential for managing and restricting the use of peripheral devices within an organization's IT environment. Defining these policies is a critical step in ensuring comprehensive device security and establishing precise, granular control over device usage and access.
To view the list of supported devices, click here
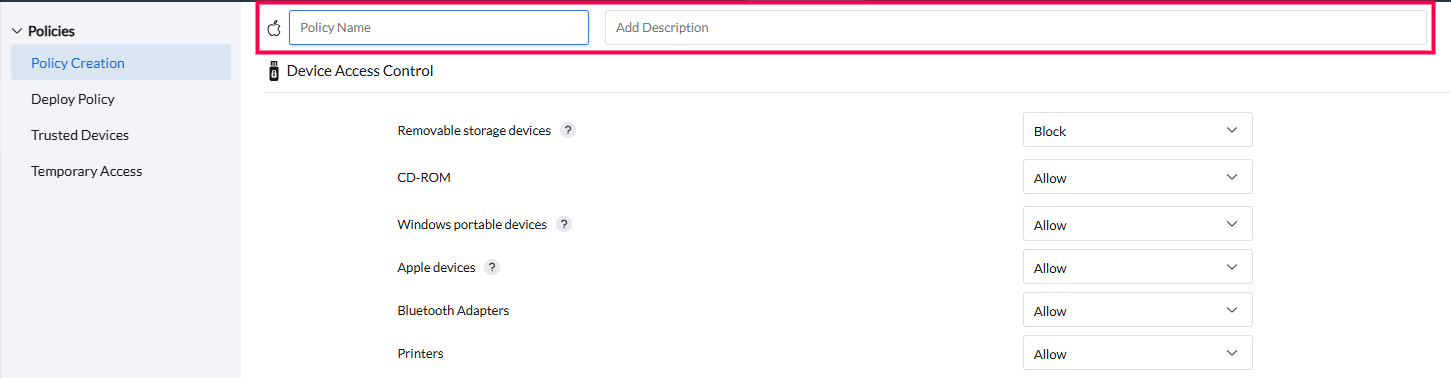
Navigate to Policies -> Policy Creation -> Create Policy -> Select Windows
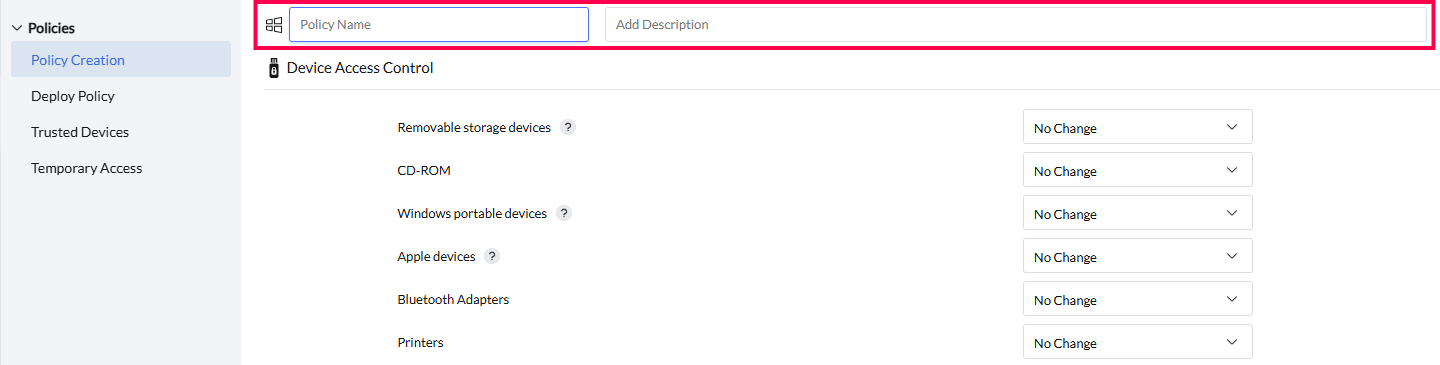
- Policy name:
Enter a name for the policy to be created.
- Description (optional):
Add a description to clarify the policy's purpose or Key details
Device Access Control allows you to manage and restrict peripheral device usage to enhance security.
- Allow: Permits full functionality of peripheral devices, with additional controls available in advanced settings for specific devices.
- Block: Restricts all functions of peripheral devices. For Removable Storage and CD-ROM devices, advanced controls allow blocking specific connection types, such as USB or SCSI.
- Allow Trusted Devices: Enables admins to specify a list of trusted devices that are permitted access, while blocking others.
For instructions on creating a trusted devices list, click here.
- No Change: Ensures that the agent does not enforce any block or allow policies on endpoints, ideal when Group Policy Object (GPO) has been applied.
- Read Only: Allows users to view data but blocks any transfer or modification of the data on the device.
Advanced Settings
While control options apply to all devices, some devices offer an "Advanced Settings" option for configuring granular controls.
The "Removable Storage Devices" enables control over the behavior of USB drives, external hard drives, and virtual drives.
When "Allow" or "Allow Trusted Devices" is selected, the admin can access advanced settings for more granular control over device configurations.
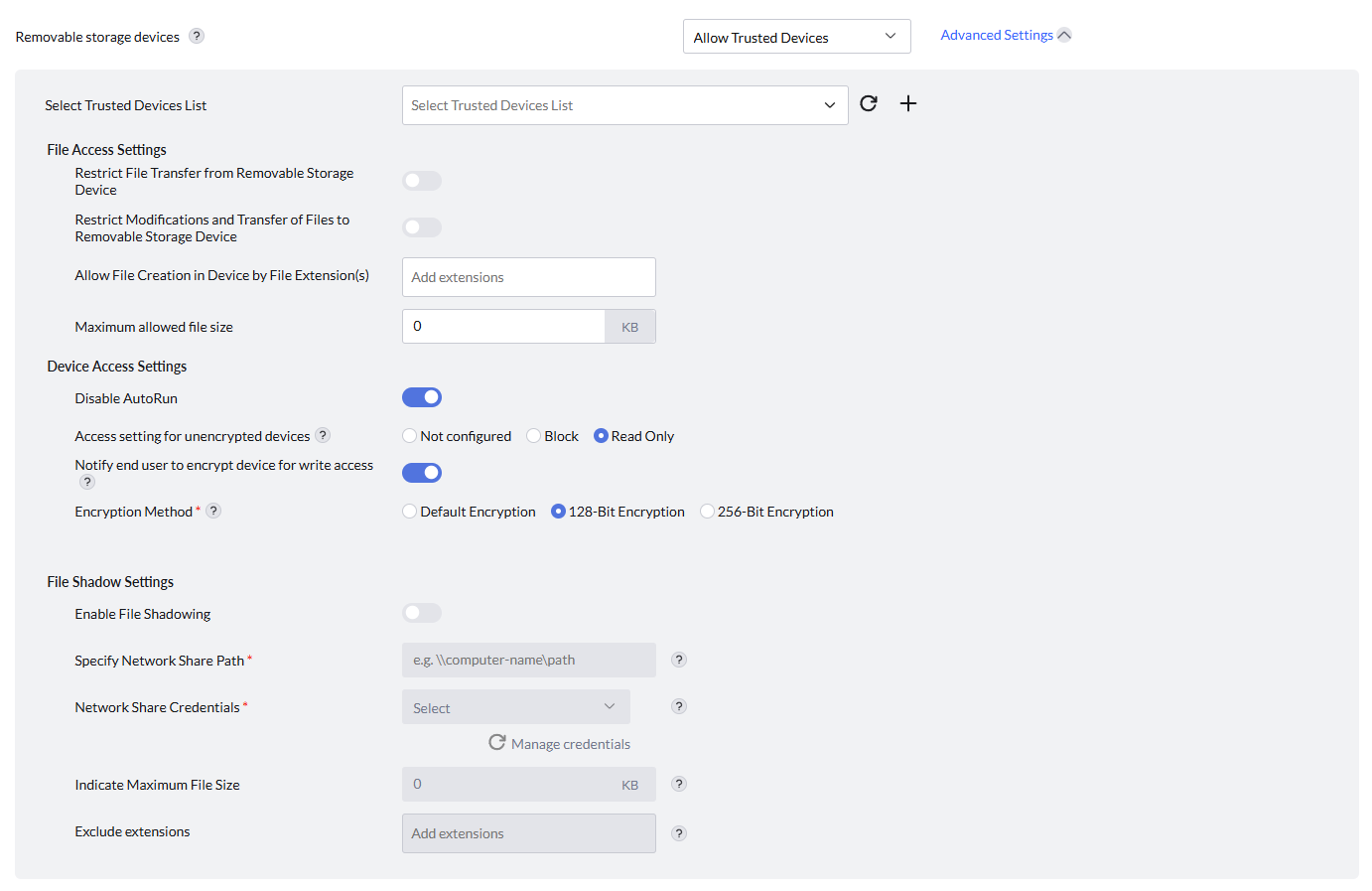
- File Access settings
- Restrict file transfer from removable storage device: Controls file transfer from a connected removable storage device to a computer
- Restrict Modifications and Transfer of Files to Removable Storage Device: Allows administrators to enable or disable permissions for modifying files on removable storage devices, preventing changes to file content and restricting transfers from the computer to the storage device.
- Administrators can allow file transfers to removable storage devices based on specific file extensions and corresponding file sizes.
- Device Access Settings
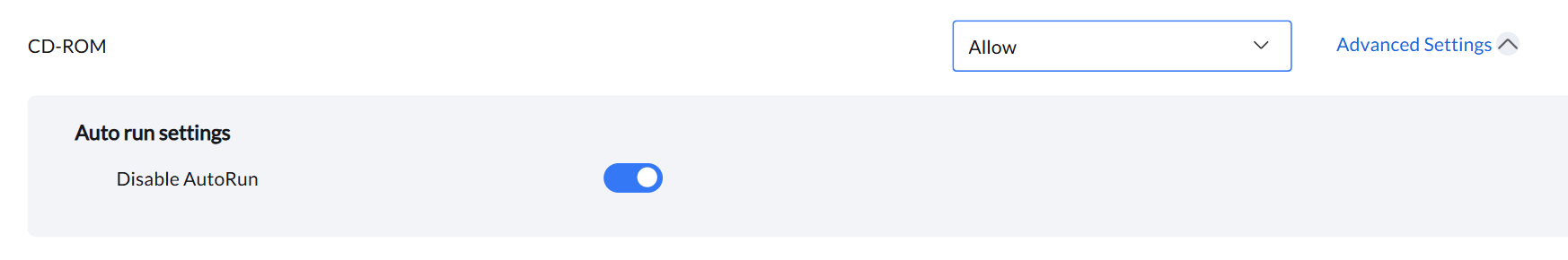
- Disable Auto-Run: Blocks auto-run functionality when a removable storage device is connected.
- Access Setting for Unencrypted Devices:
- Not Configured: No restriction is applied to unencrypted devices.
- Block: Restricts the use of unencrypted removable storage devices.
- Read-Only: Allows unencrypted removable storage devices to be connected in read-only mode.
- Notify end user to encrypt device for write access: When 'Read Only' is selected for unencrypted devices, this option enables a pop-up notification on the end-user's machine. The notification alerts the user that they must encrypt their device to restore write capability.
- Encryption Method:
- Default Encryption: Uses the default encryption method specified by the system.
- 128-bit Encryption: Uses 128-bit encryption for data protection.
- 256-bit Encryption: Uses 256-bit encryption for enhanced data security.
- File shadow Settings
- Administrators have the capability to enable or disable file shadowing as needed.
- If file shadowing is enabled, specify the path for the remote network shared folder.
- Select credentials for authorized users to access the network share where shadowed file copies are stored.
- Set the maximum file size allowed for file shadowing.
Note:
- You can enter a value between 0 KB and 1,048,576 KB (1 GB). If 0 is entered, no size restriction will be applied and all files, irrespective of size, will be shadowed.
- File shadow occurs only when a file is transferred from a computer to a removable storage device.
Scenario:If the file shadow size limit is set to 1 GB, a 2 GB file will not be shadowed because it exceeds the specified limit. However, if the limit is set to 0 KB, no size restriction will be applied, and the 2 GB file will be shadowed as all files are allowed irrespective of size.
- File extensions listed under "Exclude Extensions" will be excluded from file shadowing.
Note:If the remote path is not reachable, the data will be stored locally on the agent machine and automatically posted to the remote path during the next refresh.
The CD-ROM controls access to CD/DVD drives, allowing you to set permissions, restrict write functions, and enforce read-only access to secure data.
When "Allow" is selected, admin can access advanced settings to enable or disable auto-run functionality.
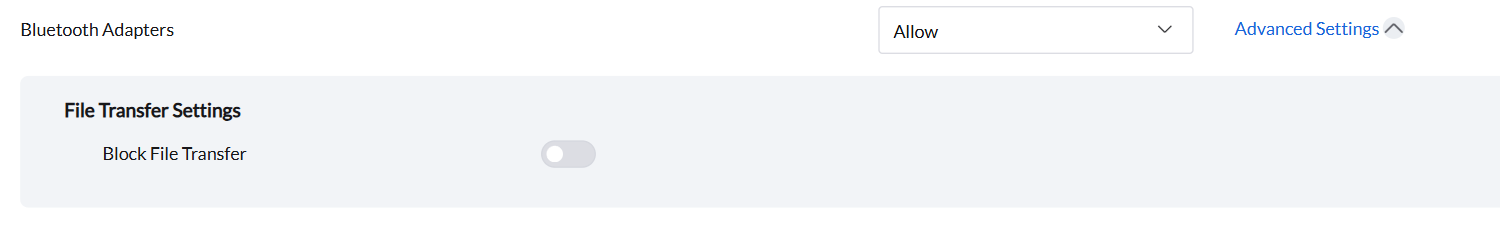
The Bluetooth Adapters manages access to Bluetooth devices, enabling you to set permissions and restrict file transfers to protect data.
When "Allow" is selected, admin can enable or block file transfer to functionality
Navigate to Policies -> Policy Creation -> Create Policy -> Select Mac
- Policy name:
Enter a name for the policy to be created.
- Description (optional):
Add a description to clarify the policy's purpose or Key details
Control Options
Device Access Control allows you to manage and restrict peripheral device usage to enhance security.
- Allow: Permits full functionality of peripheral devices, with additional granular controls available in advanced settings for specific devices.
- Block: Blocks all functions of peripheral devices. For Removable Storage and CD-ROM devices, advanced controls allow blocking specific connection types, such as USB or SCSI.
- Allow Trusted Devices: Enables admins to specify a list of trusted devices that are permitted access, while all other devices are blocked.
For instructions on creating a trusted devices list, click here.
- No Change: Ensures that the agent does not enforce any block or allow policies on endpoints, ideal when an administrator has applied a Group Policy Object (GPO).
- Read Only: Allows users to view data but blocks any transfer or modification of the data on the device.
Advanced Settings
While control options apply to all devices, some devices offer an "Advanced Settings" for configuring granular controls.
For macOS, the "Removable Storage Devices" provides essential controls over USB drives, external hard drives, and virtual drives, allowing administrators to restrict file modifications and transfers to removable storage devices.
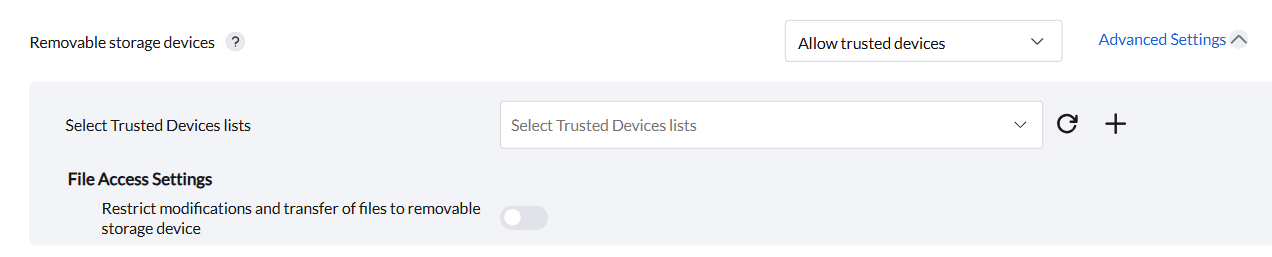
The "Restrict Modifications and Transfer of Files to Removable Storage Device" allows administrators to enable or disable permissions for modifying files on removable storage devices. Enabling this option prevents changes to file content within the removable storage device and restricts file transfers from the computer to the storage device.
Device audit settings lets admins configure audit parameters and settings related to generating audit reports to maintain compliance and security. This helps admins get a clear insight on device interactions across the network.
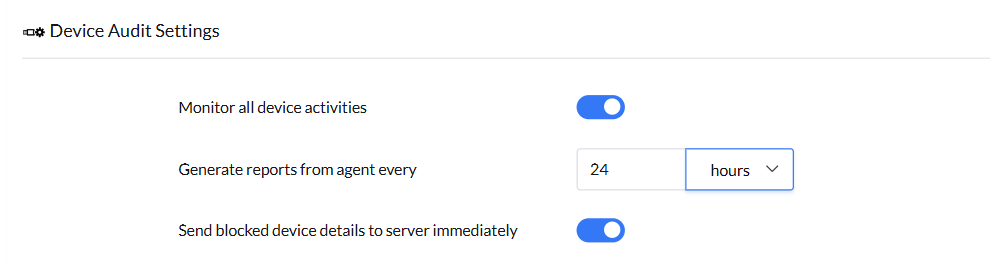
- Monitor All Device Activities enables comprehensive auditing and tracking of all device activities.
Note: Disabling this setting will stop all device activity audits.
- Admins can configure the frequency at which the agent generates audit reports
- Enabling the "Send Blocked Device Details to Server Immediately" ensures blocked device reports are sent to the server in real-time. When disabled, the reports are sent during the next scheduled agent report period.
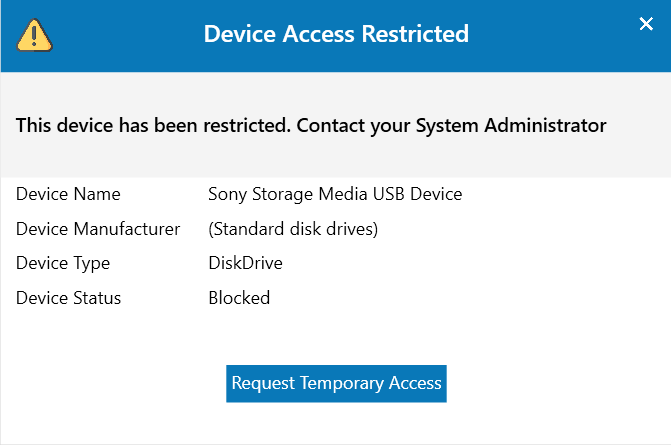
Alert settings let admins configure notifications for users when a blocked device is connected.
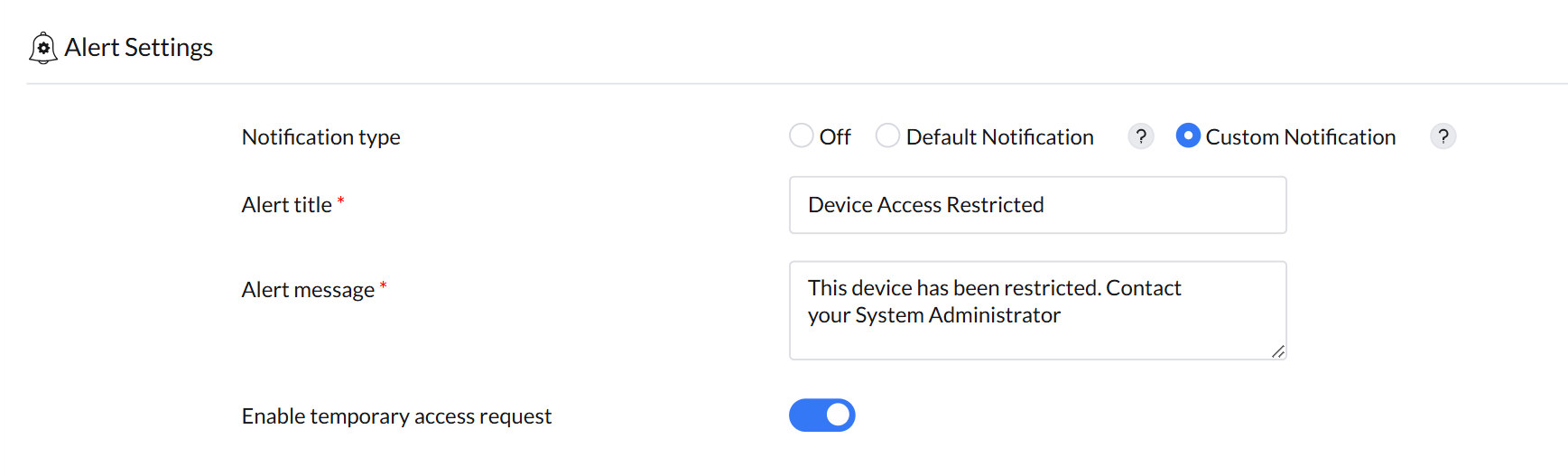
- Off: Users receive no alert indicating that their device has been blocked.
- Default Notification: Users receive a standard message informing them that their device has been blocked.
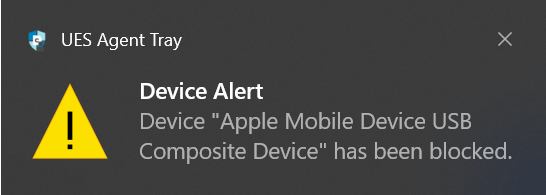
- Custom Notification: Admins can define a unique alert title and message that users see when inserting a blocked device. Additionally, admins can enable a "temporary access request" option, allowing users to request temporary permission to use a blocked device.