Device Control Temporary Access
Creating Temporary Access
Temporary access allows the admin to grant users permission to use a specific blocked peripheral device for a limited time.
To create Temporary Access, Navigate to Policies -> Temporary Access -> Create
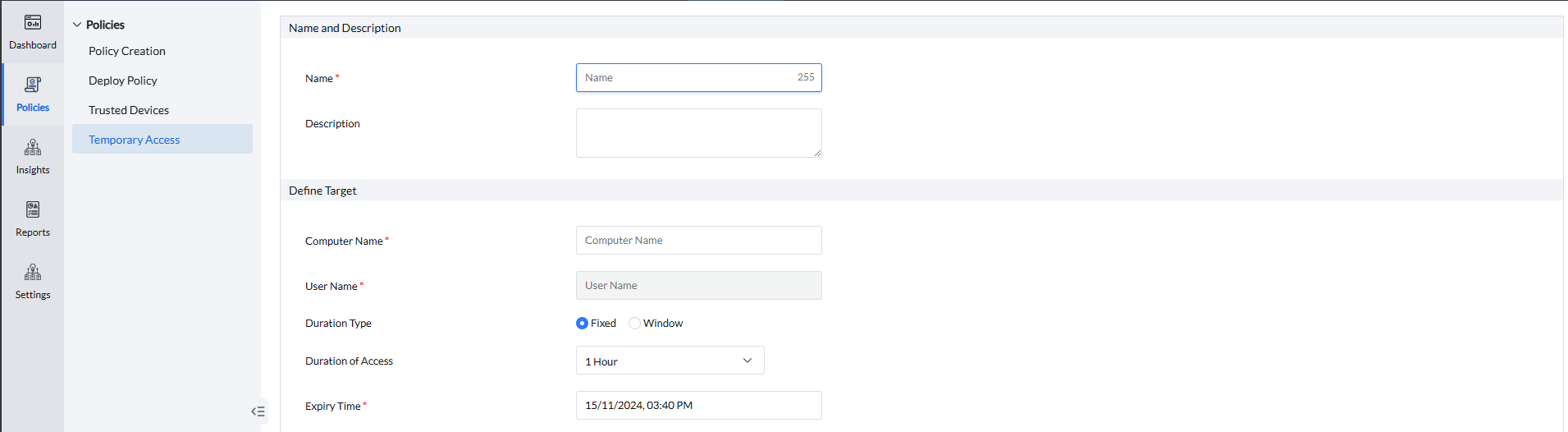
- Name:
Enter a name for the policy to be created.
- Description (optional):
Add a description to clarify the purpose or Key details
Define Target
- Select the computer name and specific user to grant temporary access.
- Duration type:
- Fixed: Fixed duration allows admins to set a specific access duration and define an expiry date and time. Temporary access begins once the policy is deployed on the computer.
- Window: The Window Access option allows admins to set a specific time frame by specifying the From and To date and time. Users can access the specified device within this period.
Allowed Device
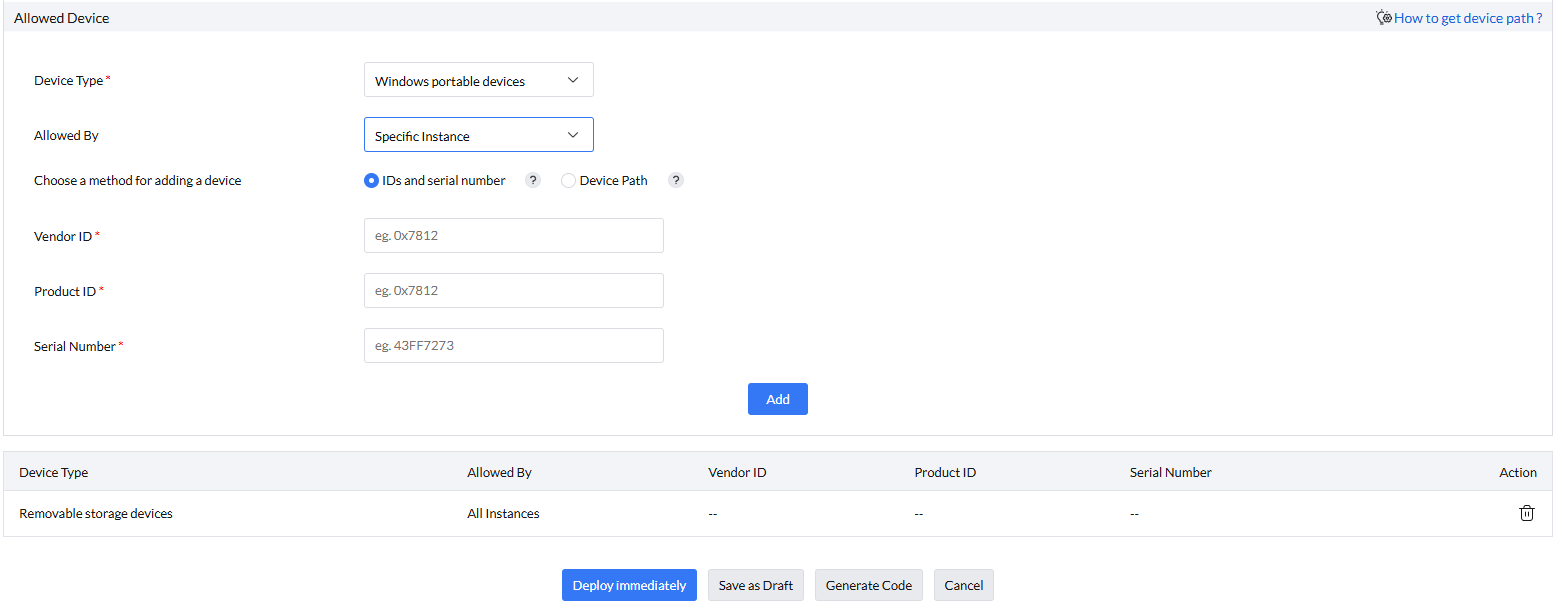
Device type: Select the device type for which temporary access will be provided.
Allowed By:
- All Instances: Access is granted to all instances of the selected device type.
- Specific Instance: Allows admins to specify a device path, granting access only to that particular device.
Removable Storage Device
When device type removable storage device is selected, administrators can configure specific advanced settings to manage its behavior effectively.
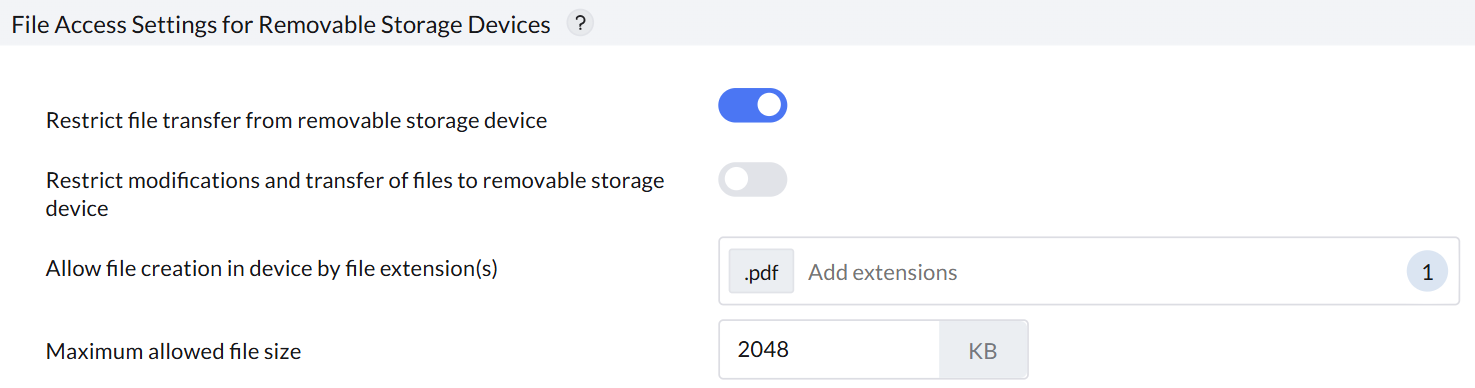
- Restrict file transfer from removable storage device: Controls file transfer from a connected removable storage device to a computer
- Restrict Modifications and Transfer of Files to Removable Storage Device: Allows administrators to enable or disable permissions for modifying files on removable storage devices, preventing changes to file content and restricting transfers from the computer to the storage device.
- Administrators can allow file transfers to removable storage devices based on specific file extensions and corresponding file sizes.
Deployment Methods
Admins have two deployment options:
- Deploy Immediately: Applies the policy directly to the target user.
- Generate a Code: Provide users with a .tac file. Users can activate this by:
Right-click the agent tray icon -> Select View Device Temporary Access Portal -> Select the .tac file -> Click Apply
Handling Temporary Access Requests
Users can request device access directly from their computers, sending the request to the admin for approval.
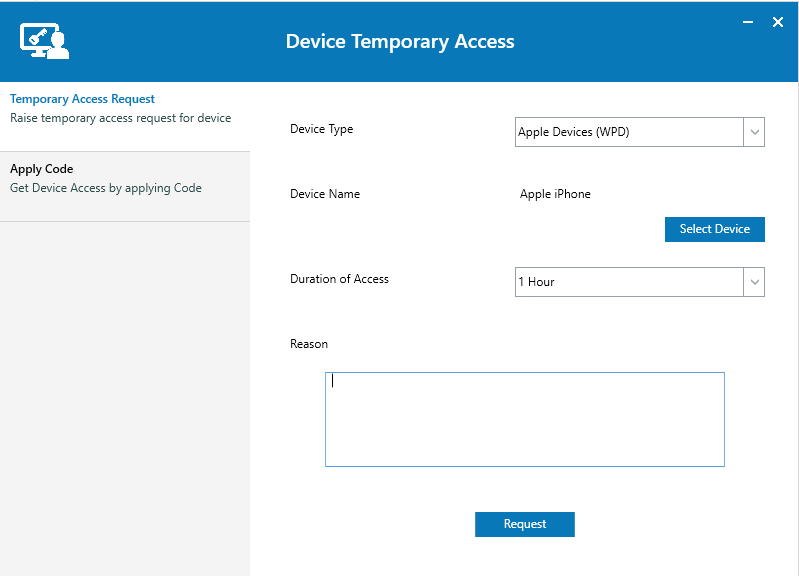
- User's can Right-click the agent tray icon -> Select View Device Temporary Access Portal -> Temporary Access Request
- Select the Device, Duration of Access, specify the reason and click request
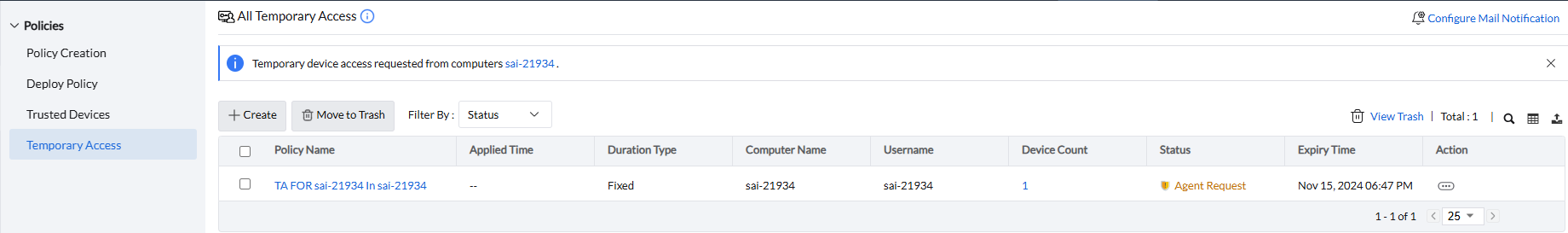
Admins can click on the policy to view details of the device for which access is requested, along with the reason provided by the user.
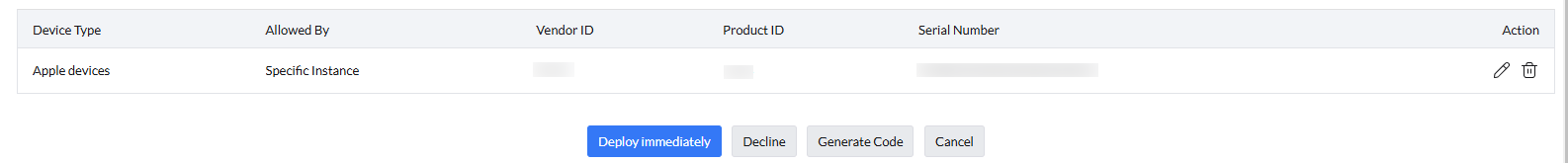
Admins can click on modify to:
- Deploy Immediately: To accept the request and deploy the policy
- Generate Code: To generate a .tac file that can be provided to the user, allowing them to activate the policy.
- Decline: Enables admins to reject a temporary access request.







