

This document outlines a step-by-step process for investigating and addressing potential malware intrusion. Timely and precise analysis is essential to accurately determine the extent of a security breach and implement appropriate countermeasures.
Endpoint Central's threat detection engine has flagged suspicious activity on your network. To accurately assess the situation, it's crucial to verify the nature of the intrusion before categorizing the breach.
Utilize the Incidents tab for key information:
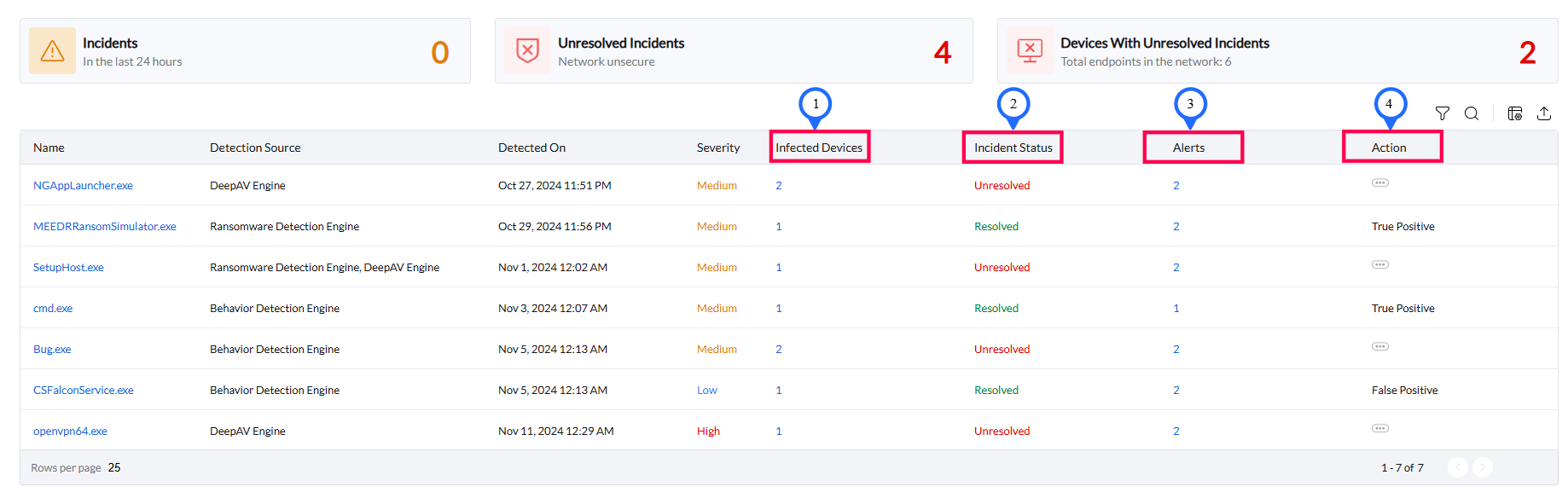
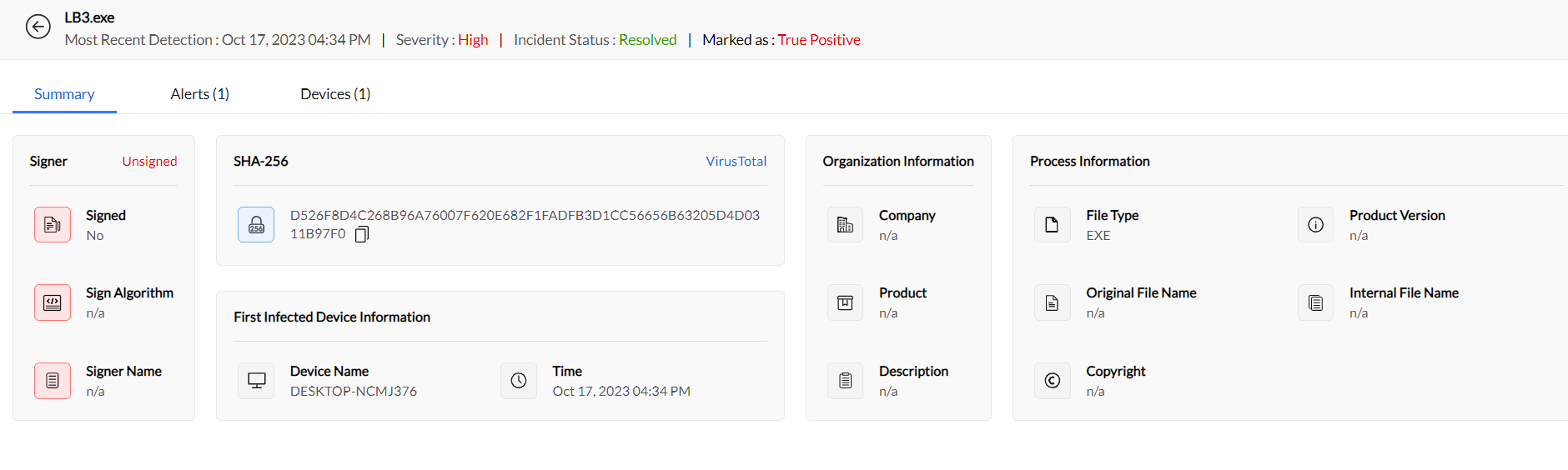
Click the incident and access the Summary section to view crucial incident details.
| Parameter | Detected Incident | Prevented Incident | Blocked Intrusion |
|---|---|---|---|
| Initial Status | Incident has been detected. | Incident has been successfully prevented. | Attempted intrusion has been blocked. |
| Urgency | Urgent attention is needed. | No immediate urgency, as the incident has been prevented. | Urgent attention may be needed, but the intrusion is blocked. |
| User Action Required | Investigate and label the intrusion as true/false positive. | Further analysis can be performed to enhance security. | Immediate user action may be required, as the intrusion is blocked. |
| Proactive Measures | Investigate and label the intrusion to ensure system security. | Enhance security measures based on additional analysis. | Prevent and block the intrusion, ensuring network stability. |
| Follow-up Action | Modify configurations to enable prevention/blocking in future incidents. | Investigate additional details to enhance security measures. | Monitor for any potential future incidents. |
| File Modifications | Restore the device to its pre-malware state if file modifications occurred. | None required | Restore the device to its pre-malware state if file modifications occurred. |
| System Stability | Potential impact on system integrity and security. | System security and stability are ensured. | System integrity and security are maintained. |
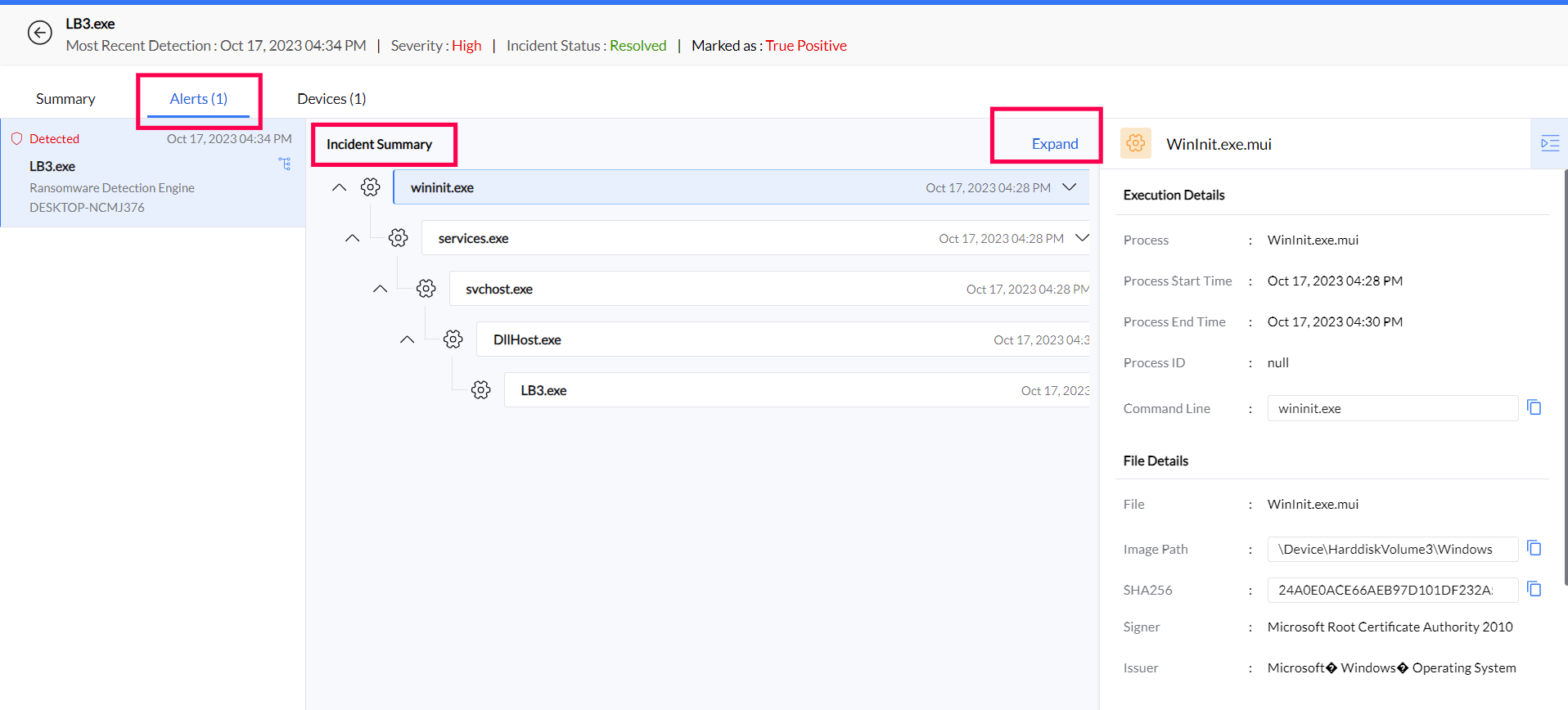
Expand the Incident Summary in the Alerts tab. Gain granular insights by examining the process source, child processes, and command-line tools. Clicking a child process provides detailed information, including SHA value, image path, and command line details.
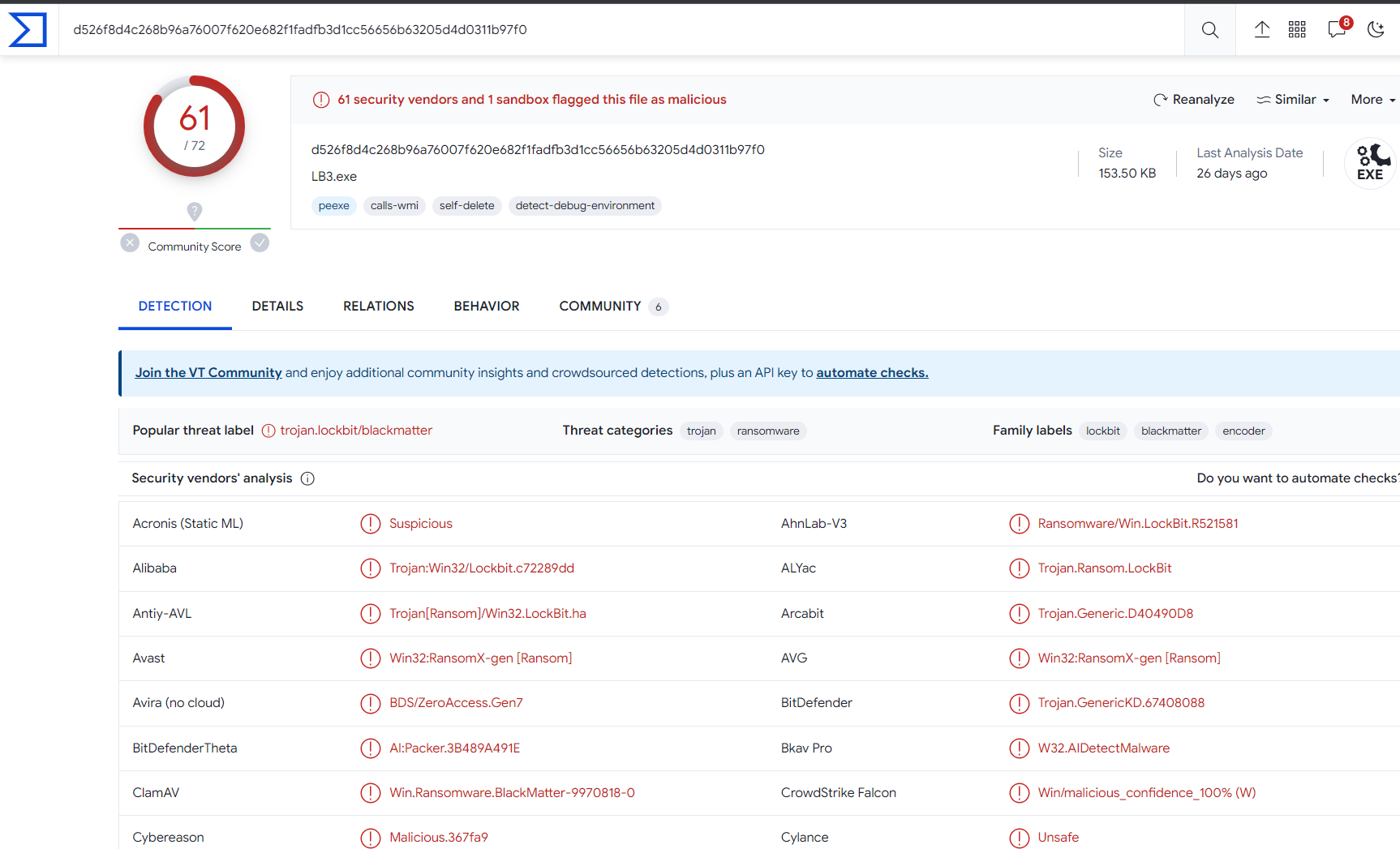
Validation through VirusTotal can affirm the hash as a true positive, offering conclusive evidence of malware attempting infiltration. VirusTotal conducts a comprehensive analysis using diverse antivirus scan engines to scrutinize files for potential threats. Upon verification, take proactive security measures by quarantining the infected device.
Proceed to quarantine the infected device.
Clicking VirusTotal may sometimes provide unclear or no results. In such cases, further investigation is required.