The Audit and Reports feature provides admins with comprehensive visibility through an intuitive dashboard and detailed audit reports on sensitive file transfers, file audits, and override incidents, ensuring thorough monitoring and control.
The Sensitive Email Audit feature provides detailed insights into emails with sensitive attachments sent outside the corporate boundary.
It includes complete information such as the computer used, the logged-in user, the sender and recipient email addresses, the subject of the email, the name of the attached file, the time the email was sent, and the event status - whether it was allowed, blocked, or reported as a false positive.
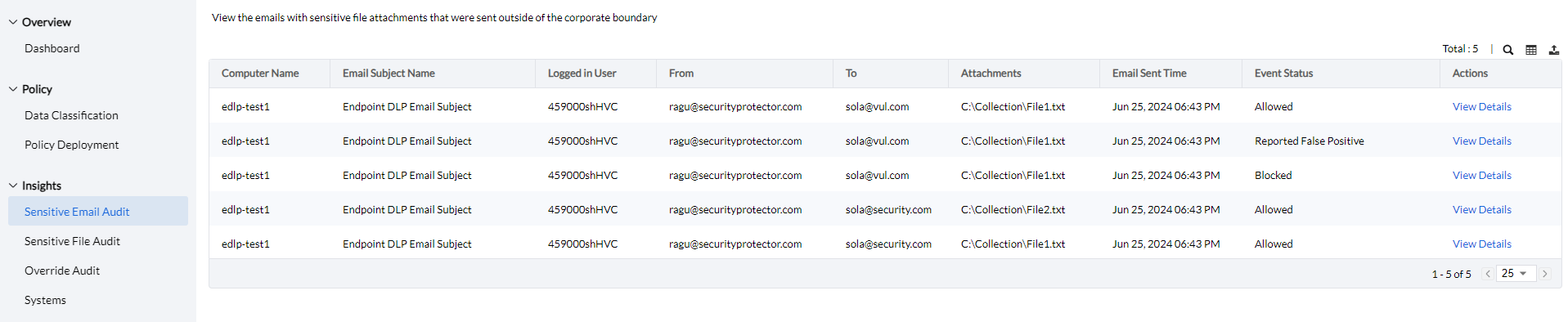
Clicking the Column button allows admins to choose which columns to display, and the Export button provides options to export the audit report in PDF, XLSX, or CSV format.
The Sensitive File Audit feature offers detailed insights into sensitive file activities. It provides information such as the computer name, logged-in user, event type (File Access, File Upload, File Transfer, or File Printing), file name, applications that accessed the sensitive files, event status (blocked, allowed, or false positive), classification category, classification rule, and event time.
Additionally, this data can be filtered by custom computer groups, event type, and event status for more focused analysis.
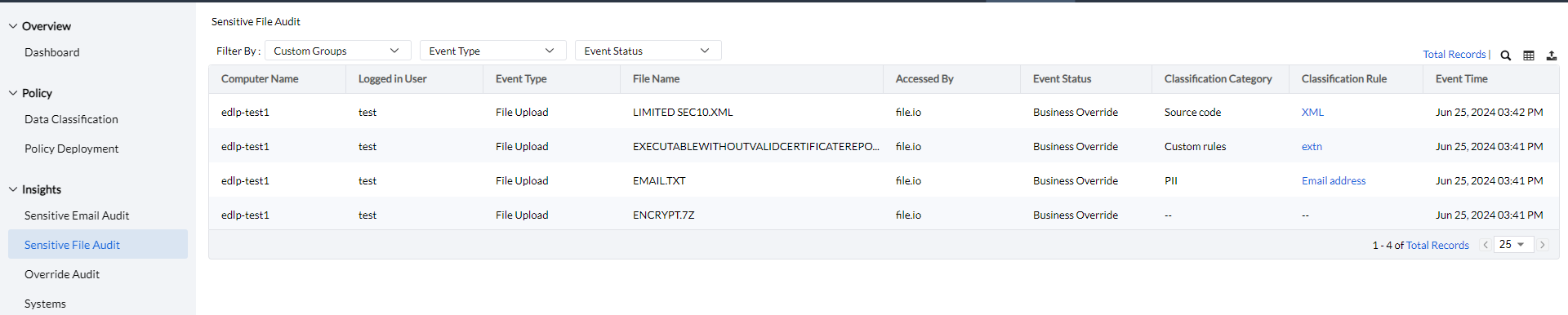
Clicking the Column button allows admins to choose which columns to display, and the Export button provides options to export the audit report in PDF, XLSX, or CSV format.
The Override Audit provides detailed insights on sensitive file activities, including the computer name, logged-in user, event type (File Access, Email Upload, File Transfer, or File Printing), file name, websites that accessed the sensitive files, event status (blocked, allowed, or false positive), classification category, classification rule, and event time.
Additionally, the data can be filtered by custom computer groups, event type, and justification message for more refined analysis.
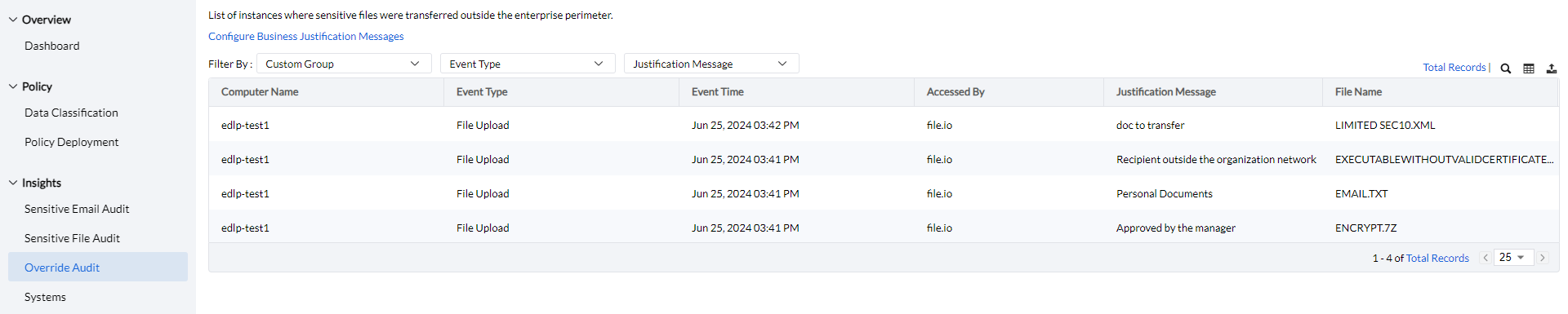
Clicking the Column button allows admins to choose which columns to display, and the Export button provides options to export the audit report in PDF, XLSX, or CSV format.
The Configure Business Justification Messages feature allows admins to create predefined templates for users to justify sensitive file transfers. Additionally, users have the option to provide a custom justification if needed.
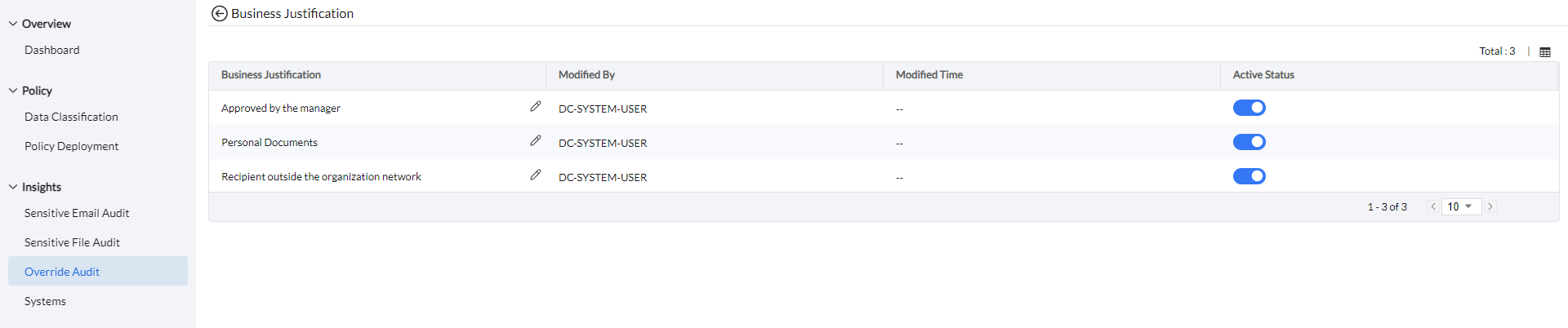
To view the Justification Summary Report, Navigate to Reports -> DLP Reports -> Justification Summary.
The Justification Summary Report provides a detailed overview of the justifications users provide to override policies. The report can be filtered by computer groups, event types (Email Upload, File Upload, File Transfer, or File Printing), or by business justifications—either admin-created templates or custom justifications provided by users.
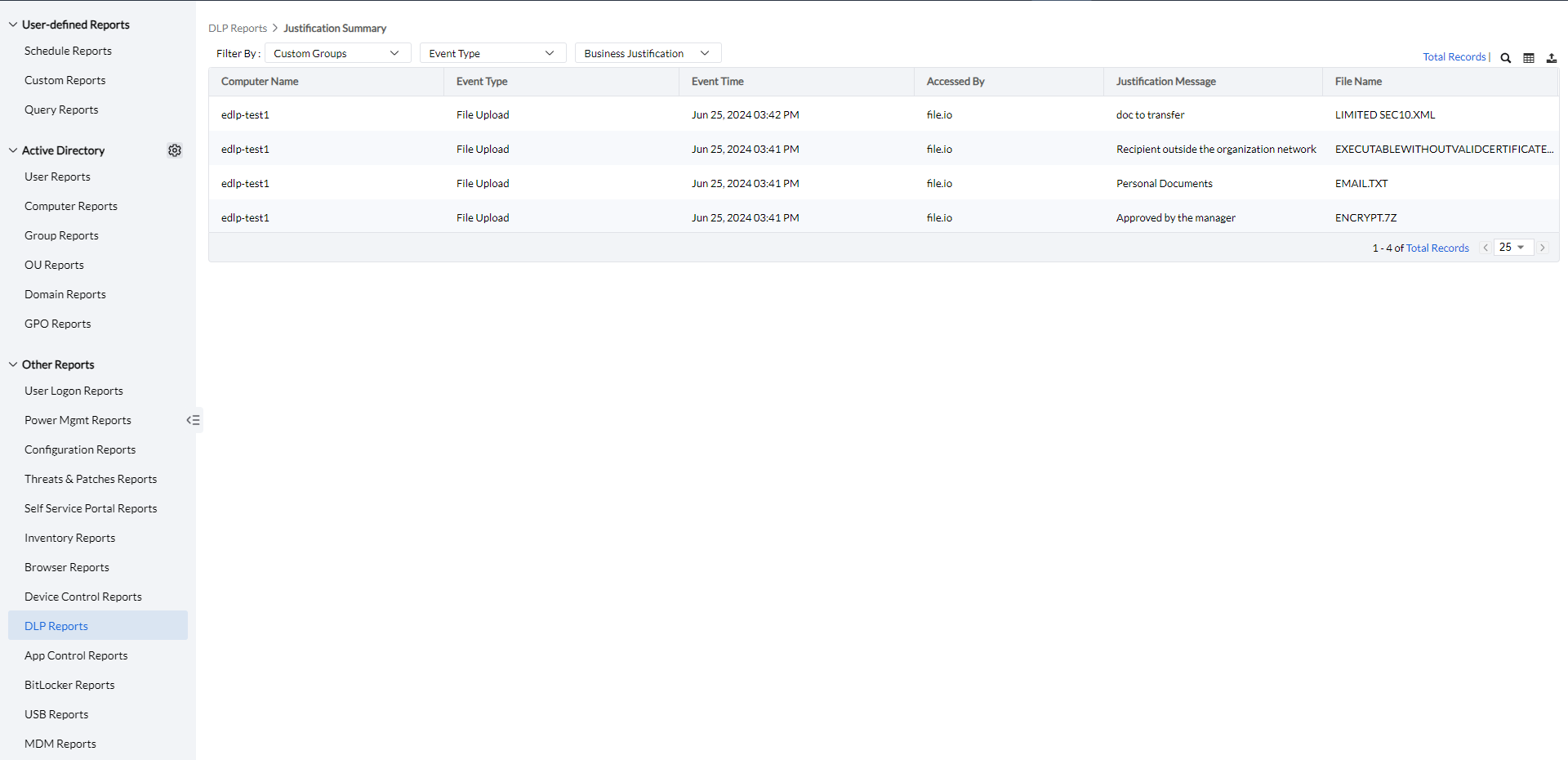
Clicking on the column button allows admins to select the columns to view and the export button allows admins to export the audit report as PDF, XLSX, or CSV
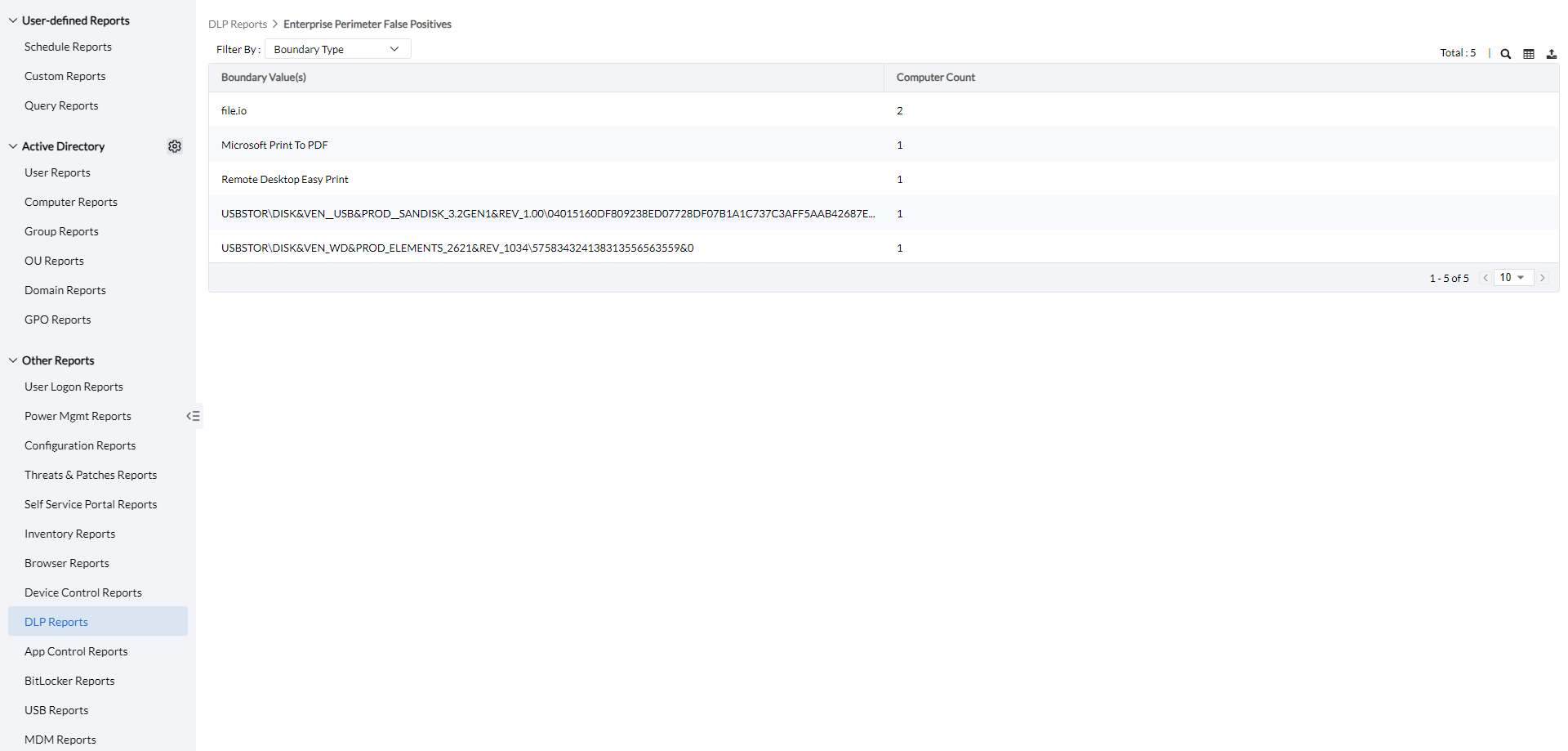
To view the Enterprise Perimeter False Positives Report, Navigate to Reports -> DLP Reports -> Enterprise Perimeter False Positives.
Enterprise Perimeter False Positives occur when a file upload, transfer, or print action is blocked within the Enterprise perimeter, but the user overrides the block by marking it as a false positive. This feature helps in identifying areas for adjustment and redefining the enterprise perimeter to improve accuracy.
The data can be filtered based on the boundary type, allowing for more precise analysis of Enterprise Perimeter False Positives.
Clicking on the column button allows admins to select the columns to view and the export button allows admins to export the audit report as PDF, XLSX, or CSV
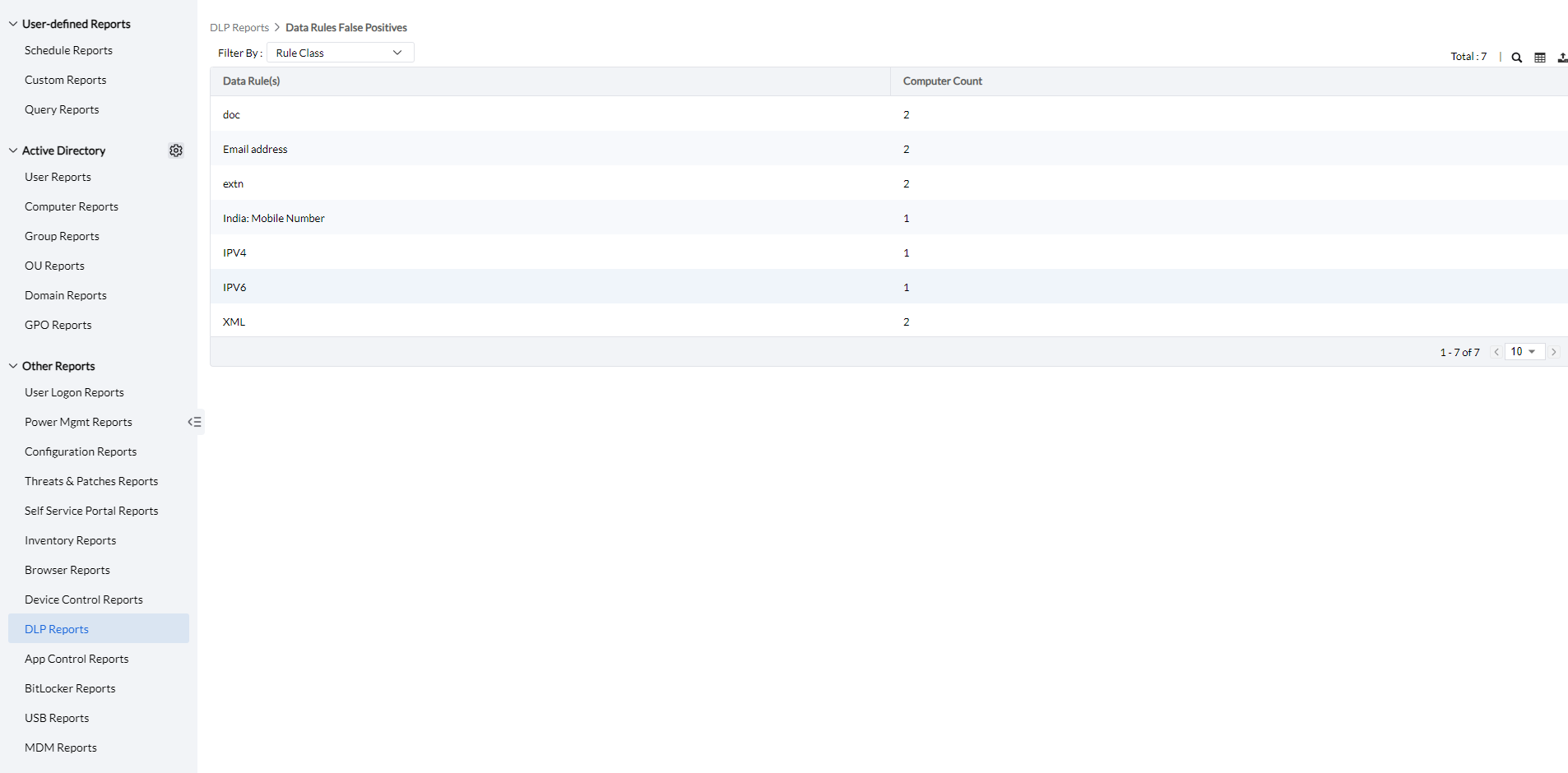
To view the Data Rules False Positives Report, Navigate to Reports -> DLP Reports -> Data Rules False Positives.
The Data Rule False Positive Report provides insights into false positives reported based on specific data rules, including the number of computers that have flagged the rule as a false positive. This report helps in analyzing, reviewing, and refining deployed data rule policies to improve their accuracy and effectiveness.
Clicking on the column button allows admins to select the columns to view and the export button allows admins to export the audit report as PDF, XLSX, or CSV
To view the Endpoint Activity Report, Navigate to Reports -> DLP Reports -> Endpoint Activity Report.
The Endpoint Activity Report provides a comprehensive overview of Endpoint Data Loss Prevention, detailing the computer name, logged-in user, event type, event status, and event time. It also offers insights into the sensitive file that was accessed, the software used to access it, and the classification rule that flagged the file as sensitive.
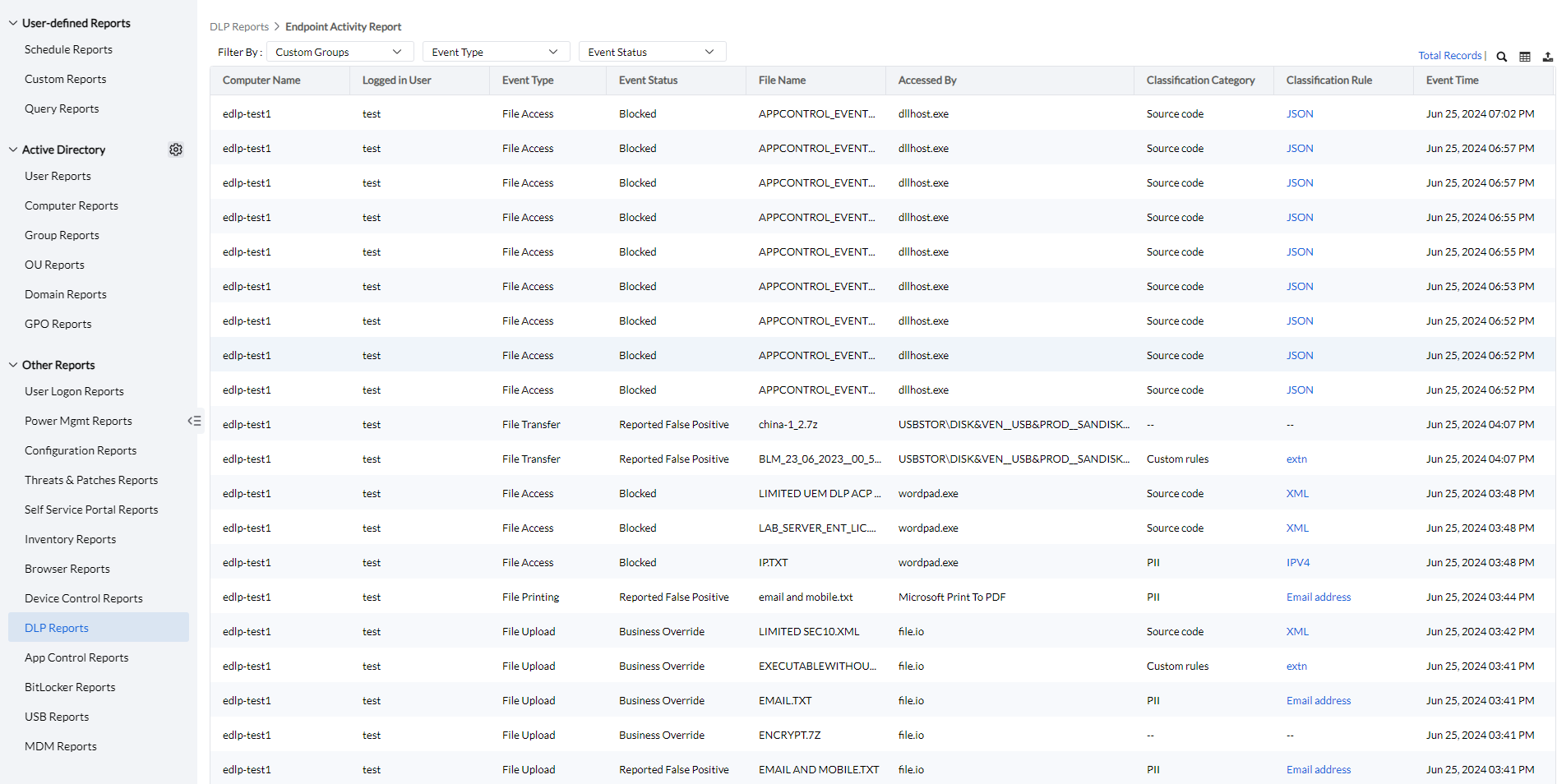
Clicking on the column button allows admins to select the columns to view and the export button allows admins to export the audit report as PDF, XLSX, or CSV
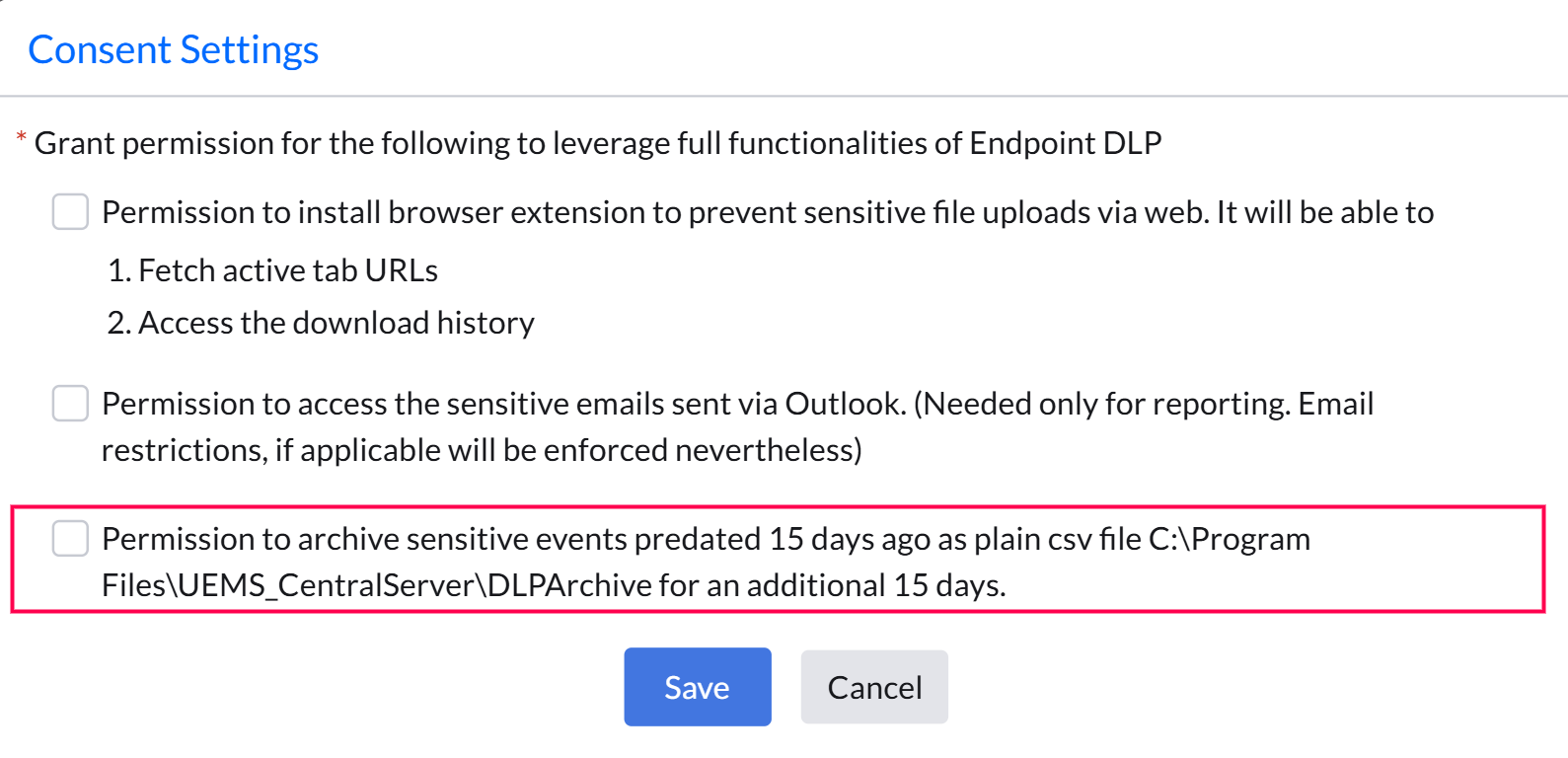
Audit reports containing sensitive data are retained for up to 15 days. If consent is granted, reports older than 15 days are automatically archived as CSV files under <Server installation directory>\UEMSCentralServer\DLPArchive. To configure this, go to Policy Deployment -> Associate Policy -> Configure Consent Settings, and enable the option to allow report archiving.