In light of recent security breaches across the globe, it has become imperative to exercise more caution when it comes to safeguarding customer data in various environments.One of the biggest security threats that businesses face in the present day and time are caused by compromised passwords and unused account privileges. In addition to securing endpoints, Endpoint Central has an additional layer of security to protect its highly secure endpoint management framework from any threats that involve breaching into the system at the access level. With the Two-factor Authentication system involved, Endpoint Central ensures that the key to ensuring safety and security lies on the hands of reliable administrators who have the authority in accessing the endpoint management system.
When you enable two-factor authentication, users will be required to add a security code in addition to the username and password to login. To enable TFA,
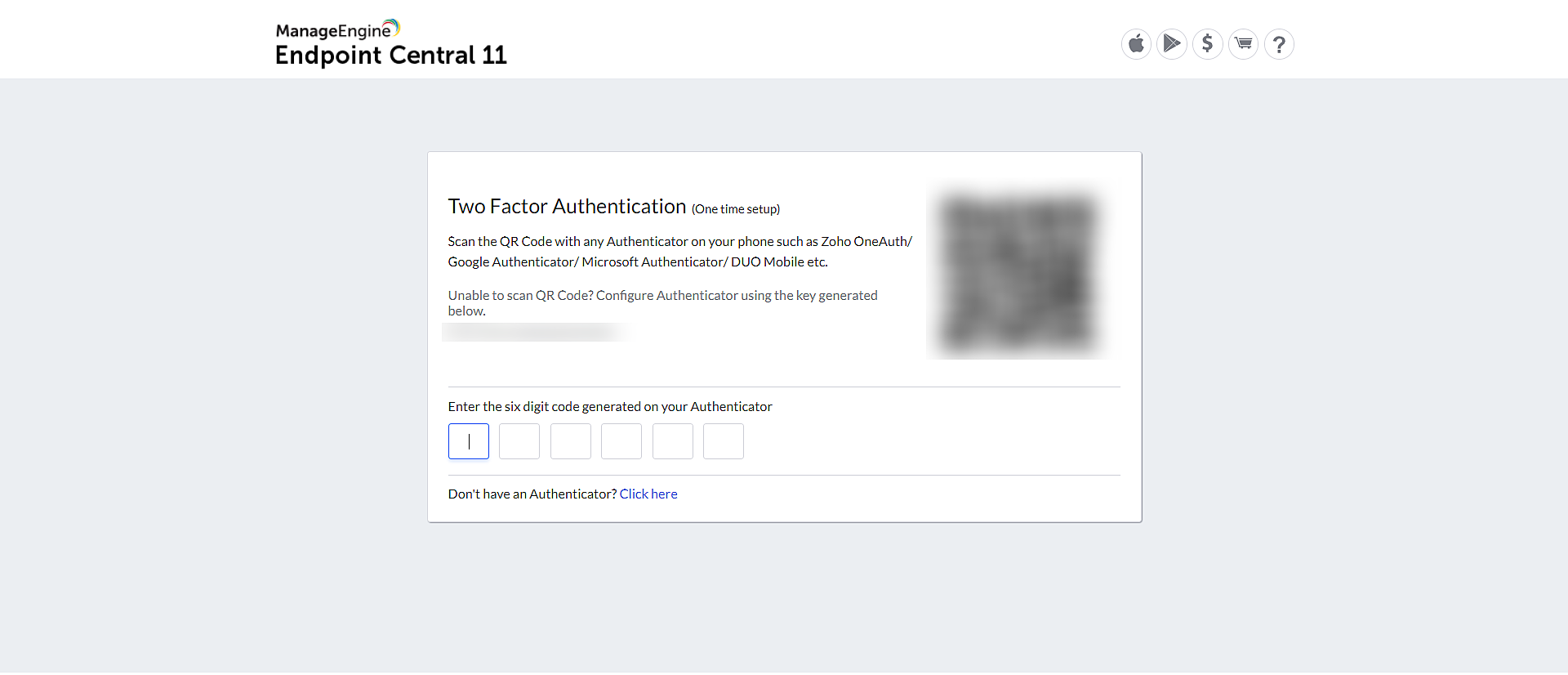
To ensure high levels of safety and security when logging in, it is important to download an authenticator app on your phone and map the product server details to the app. By doing so, you can use the OTP generated by the app to log in to the product.
The authenticator apps that you can use to maintain a high level of security are listed down below:
To log in to the product using the authenticator app,
If you choose Email as a mode for two-factor authentication, then you have to enter the OTP you have received via mail in addition to entering your username and password to login to the web console. Every generated OTP is valid for 15 minutes from the generation. You can save the OTP for specific browsers for (n) specified days.
1. Can I disable TFA after it is enabled?
No. As a part of security enforcement, TFA cannot be disabled once it is enabled. However, you can contact our Support in any case of trouble with TFA.