- Free Edition
- What's New?
- Quick Links
- Log Management
- Application Log Management
- Application log monitoring
- IIS log analyzer
- IIS web log analyzer
- IIS FTP log analyzer
- IIS log parser
- VMware log analyzer
- Hyper V event log auditing
- SQL database auditing
- SQL server auditing
- MySQL log analyzer
- Apache log analyzer
- DHCP server auditing
- Database activity monitoring
- Database auditing
- Oracle database auditing
- IT Compliance Auditing
- IT Compliance Auditing
- SOX Compliance Audit
- GDPR Compliance Audit
- ISO 27001 Compliance Audit
- HIPAA Compliance Audit
- PCI Compliance Audit
- FISMA Compliance Audit
- GLBA Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- CCPA Compliance Reports
- CCPA Compliance Software
- NERC Compliance Audit Reports
- Cyber Essentials Compliance Reports
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
- PDPA compliance audit reports
- CMMC Compliance Audit
- SIEM
- Security Information and Event Management (SIEM)
- Threat Intelligence
- STIX/TAXII feed processor
- Server Log Management
- Event Log Monitoring
- File Integrity Monitoring
- Linux File Integrity Monitoring
- Threat Whitelisting
- Advanced Threat Analytics
- Security Log Management
- Log Forensics
- Incident Management System
- Application log management
- Real-Time Event Correlation
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Linux Log Analyzer
- Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Cisco Logs Analyzer
- VPN log analyzer
- IDS/IPS log monitoring
- Solaris Device Auditing
- Monitoring user activity in routers
- Monitoring Router Traffic
- Switch Log Monitoring
- Arista Switch Log Monitoring
- Firewall Log Analyzer
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet log analyzer
- Endpoint Log Management
- System and User Monitoring Reports
- More Features
- Resources
- Product Info
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
EventLog Analyzer, a centralized logging solution, provides you with flexibility in collecting, storing, and analyzing logs from network devices and applications—all from a centralized dashboard.
Here's how EventLog Analyzer is the best centralized logging tool
Centralize log collection across your network
EventLog Analyzer automatically collect logs from over 750 log sources including firewalls, IDS/IPS, servers, routers, switches, database applications, web servers, proxy servers, and more. This centralized logging solution automatically discovers all devices in your network based on their IP or in the Central Identities Data Repository range, collects logs and stores from them in a central location.
This log management, auditing, and IT compliance management resource provides users with an option to configure syslog devices from within its console, and to send log data directly to its central server. EventLog Analyzer also has a built-in central syslog server that receives syslogs from the configured devices, analyzes, and displays actionable information in the dashboard. Further, EventLog Analyzer comes with a custom log parser that helps users extract specific log fields for better log analysis.
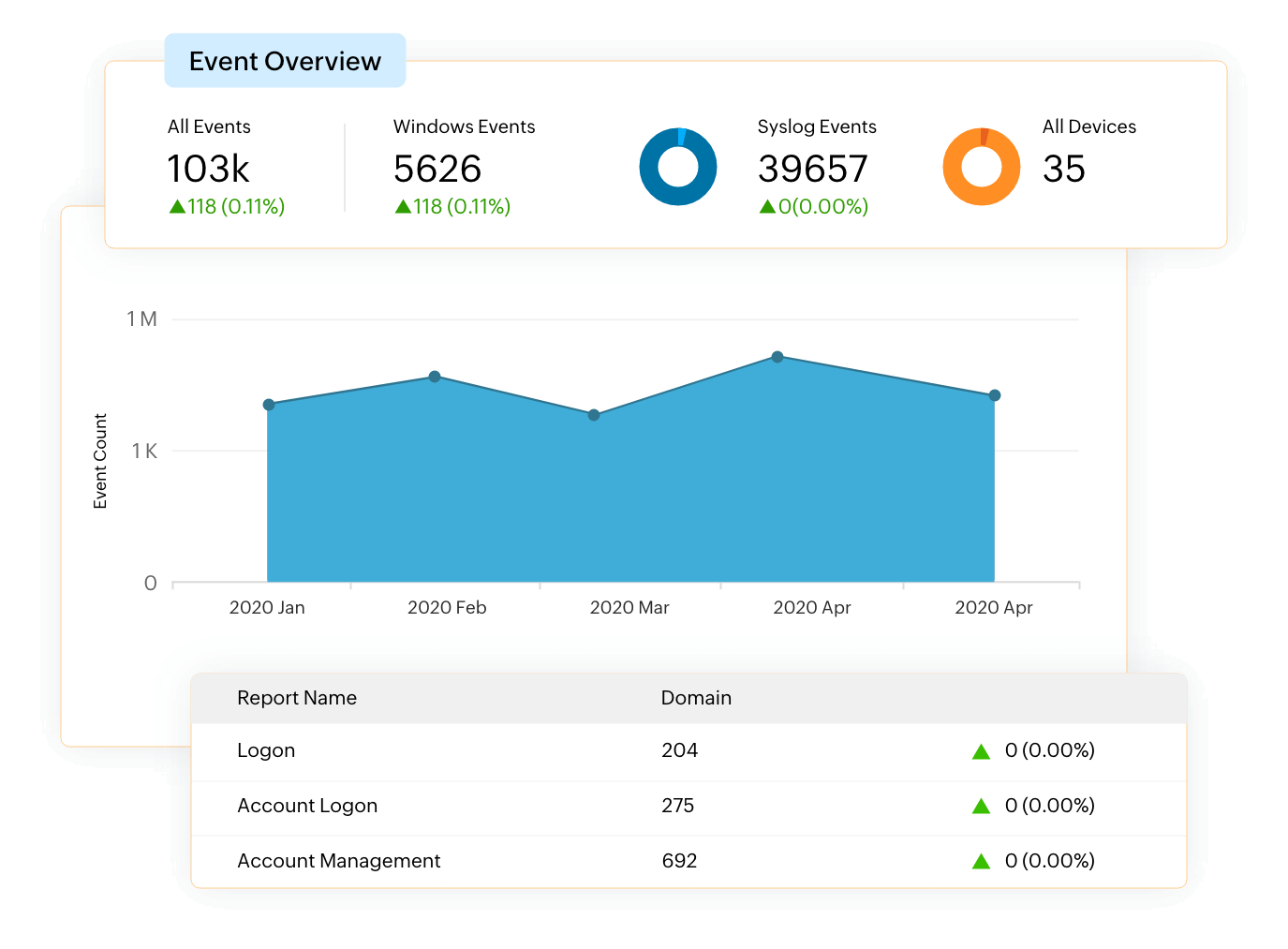
Analyze and search logs from a central console
Analyze the centralized log data using in-depth security analytics reports and dashboards. Gain deep insights into user activity, configuration changes, policy violations, network anomalies, system downtime, and more to detect security threats. You can easily search through a vast range of logs with our easy-to-use search module and render specific logs that match your query. EventLog Analyzer's sophisticated heuristic search capability helps you easily sift through voluminous log data. Intuitive search options, click-based search, range and group searches, and more help automate search query building and perform static correlation. The solution's advanced search engine scours multiple search criterion groups at once and can filter logs based on certain event types, severity and other attributes.
Gain security insights from the unified security dashboard
The security analytics component of EventLog Analyzer presents critical information from centrally collected log data in the form of intuitive dashboards.The solution's unified security dashboard provides insights into the network security events.
- Network Overview dashboard gives insights into traffic trends, top denied connections, top VPN logons, interface status and more.
- Security Overview dashboard offers actionable insights into the number of threats detected, incidents spotted using log correlation, top network security attacks, top endpoints affected by security threats, and more.
- Events Overview dashboard provides details on top Windows, Linux, and Syslog security events, critical application events, and file and folder modification events.
Further, the solution provides over 1,000 predefined security analytics widgets that present insights for security auditing, threat detection, and compliance needs. You can also create a custom security analytics dashboard based on your organization's needs.
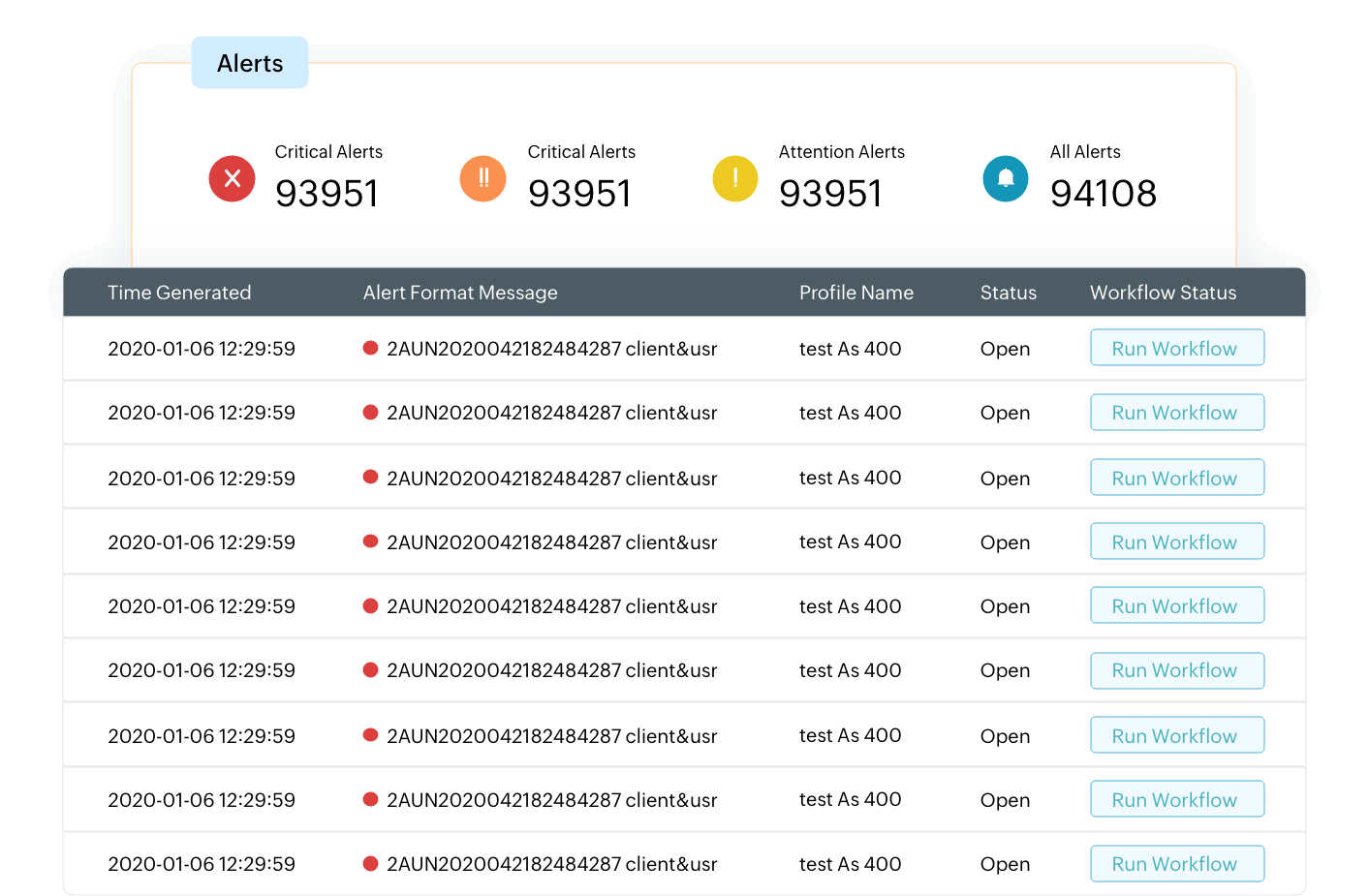
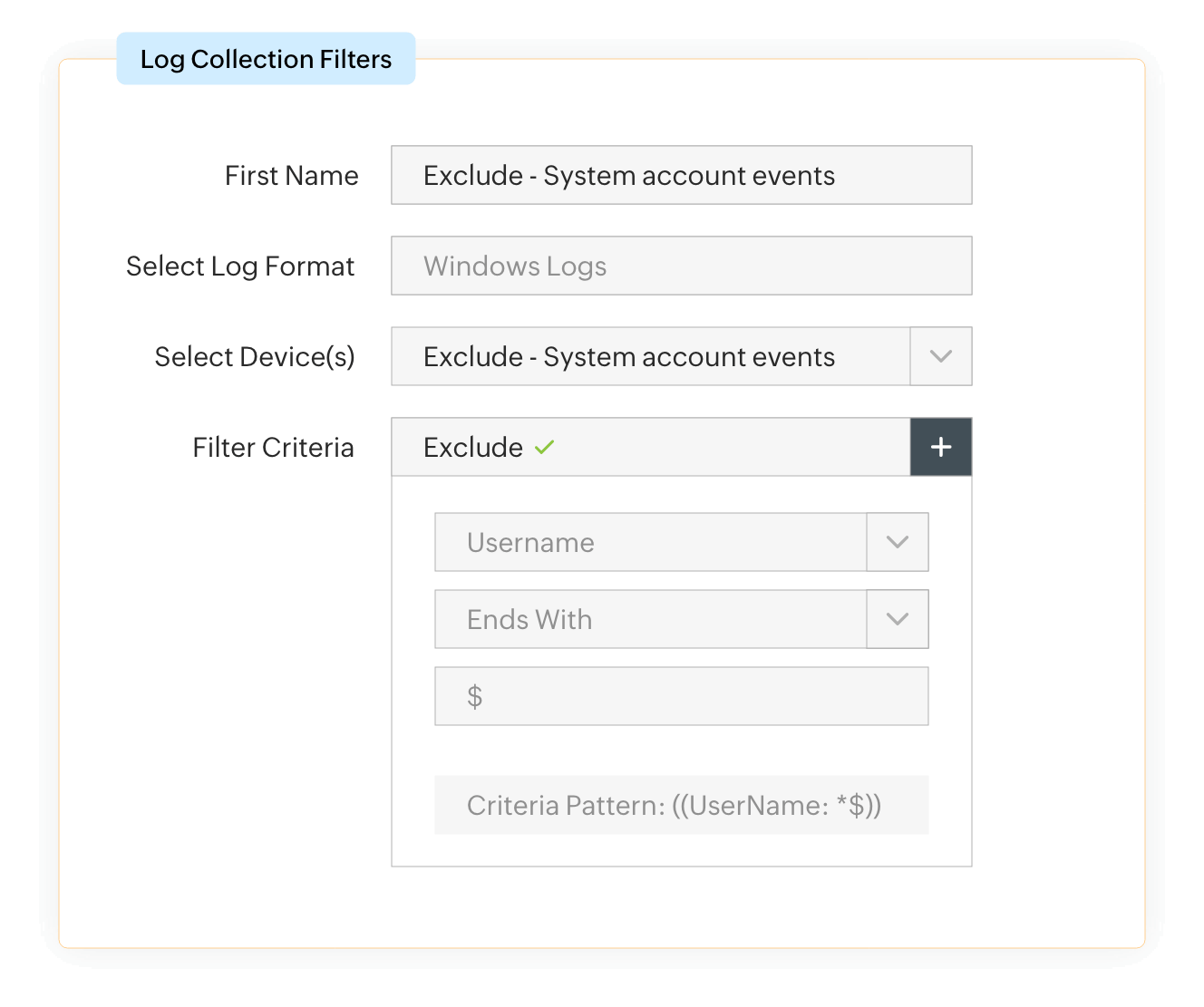
Central console for incident detection and management
Apart from its centralized logging capability, EventLog Analyzer offers capabilities to detect and manage security incidents from its central console. Detect security threats and attacks using rule-based, signature-based, and ML-based detection techniques. Gain in-depth details on compromised attacks, identify threat patterns, and more. Once detected, the incidents can be prioritized, assigned, and automatically remediated using the central incident management console.
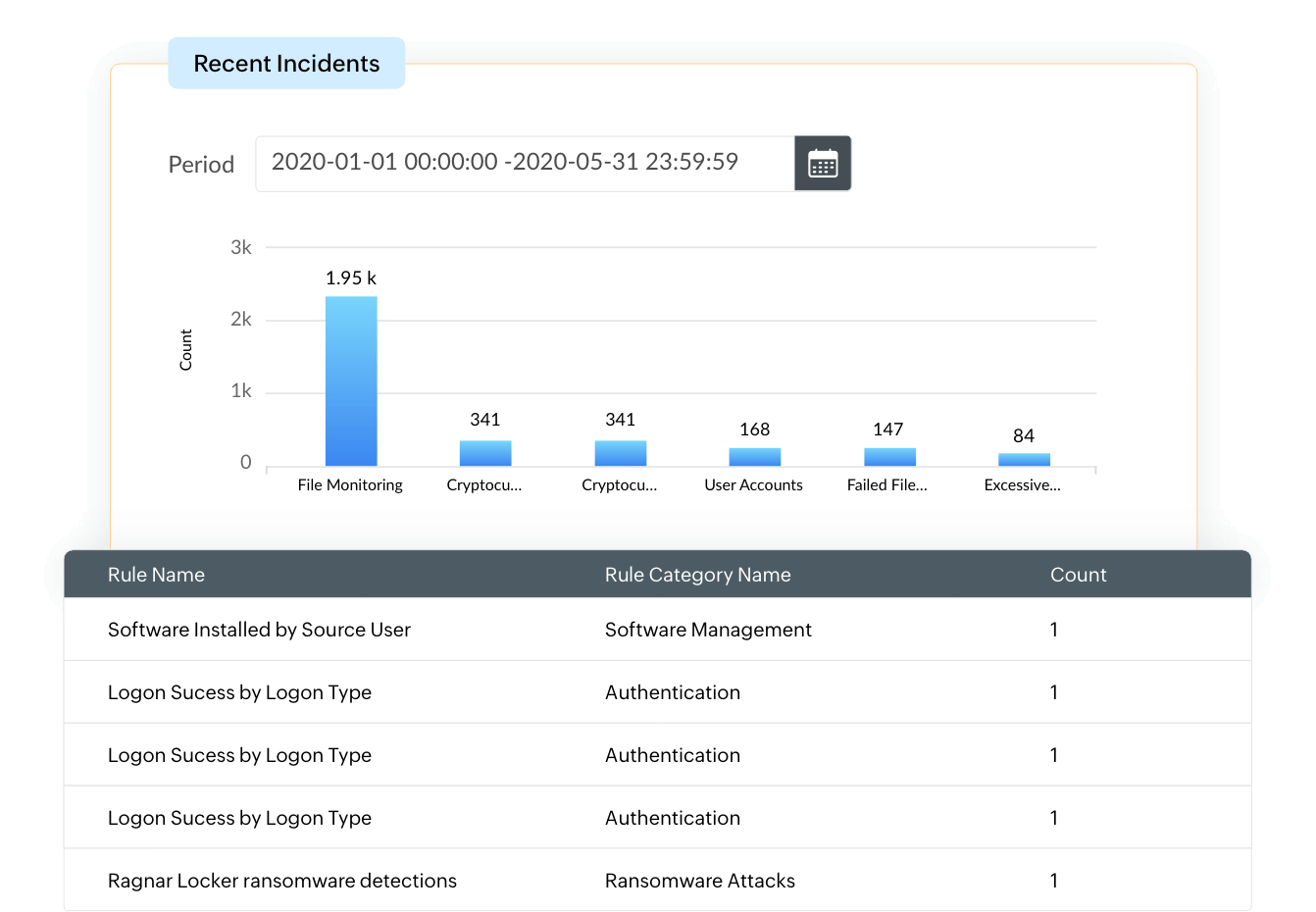
Secured log archival for future requirements
EventLog Analyzer automatically archives collected audit logs, and provides secured and central log storage to conduct log forensic analysis with ease.The solution ensures that the log remains tamperproof and enables you customize the log retention period. Using EventLog Analyzer, it easy for you to filter and search the raw logs collected from a multitude of devices to uncover the cause of a failure. The archived log data can be stored on the database, or shared across network devices. The archived log data can be easily reloaded at anytime to the products' database for forensic analysis.
5 reasons to choose EventLog Analyzer as your centralized log management tool
Simplified deployment
As soon as the solution is deployed in your IT environment, it automatically starts to discover all devices and applications and collect logs using agentless and agent-based log collection methods.
Security reports for spotting threats & incidents
The solution's robust real time event correlation engine correlates events occurring across your systems and generates security reports so you can quickly take remedial action.
Non-event threat feed data for contextual log analysis
Detect malicious IP addresses, URLs, or domain interactions by correlating logs from various devices with built-in global threat intelligence feeds and advanced threat analytics.
Real-time notification and incident management
Instead of manually executing mundane repetitive actions in response to incident alerts, automated incident response workflow improves efficiency in resolving security incidents.
Integrated and centralized compliance management
Simplify audit processes and get notified of compliance violations in real time. Adhere to strict regulatory compliance mandates such as PCI-DSS, HIPAA, FISMA, SOX, and more.
Frequently asked questions
A centralized logging solution collects logs and unifies the data from various network devices (such as servers, firewalls, routers, workstations), applications (such as IIS, Apache, DHCP), intrusion detection systems, and more. The solution presents logs in a central console which makes it easy to access. Logging solutions are capable of automates and streamlining the process of manual log management and saving enormous amount of time.
Simplifies log search: Centralized logging solution helps collect, analyze, and display logs in an intuitive dashboard to easily search logs.
Secure storage and retrieval: Retain log data in a file as long as you need it. Easily store and search logs to monitor your network health and security.
Proactive monitoring of log trends: Centralized logging helps analyze the enormous amount of logs and helps you understand the trends and patterns in the network to identify potential issues.
Better visibility of events: Gain a unified view of event logs to quickly find and fix issues before they become critical, so you can enhance the network security of your organization.
EventLog Analyzer, a centralized logging tool processes 20,000 logs per second to help security admins detect attacks in real time and evade the daunting task of analyzing enormous logs. The solution automates the process of monitoring network logs, and provides a comprehensive view of network performance, persisting issues, vulnerabilities, and helps preempt security attacks.











