- Home
- Logging Guide
- How do Linux file permissions work?
Linux permissions: Explained
In this page
- Understanding Linux permissions
- What is a file mode?
- How to check the permissions of a file in Linux
- What are special permissions?
- How to change permissions in Linux
- Enhancing security for file and directory permissions in Linux with ManageEngine EventLog Analyzer
Linux permissions are crucial to ensure system security and integrity. They control who can access and modify files, directories, and other system resources. Assigning appropriate permissions to users is crucial to protect sensitive data and prevent unauthorized access. Setting up file permissions also helps prevent accidental or malicious modifications that could compromise security data, system stability, or functionality. This article will explore the Linux permission structure and the methods to set them.
Understanding Linux permissions
Linux permissions determine who can access and modify files, directories, and other system resources. These permissions are assigned to each file or directory and are based on the owner, group, and other categories. The permissions assigned to a file or directory are known as file modes.
When a user tries to access a resource, Linux checks if their effective permissions allow the action. Effective permissions are determined by the user's primary group and any supplementary groups. If the user has the necessary permissions, access is granted; otherwise, it's denied. This system provides flexible control over resource access, allowing for different permissions to be set for different files and directories based on their sensitivity and usage.
The three main types of Linux permissions are:
| Particulars | Description |
|---|---|
| Read | Users are only allowed to view the contents of a file. For directories, users are allowed only to view the names of files and sub directories stored in them. |
| Write | With write permission enabled, users can modify and delete the contents of a file if they wish. Users are allowed to create, modify, delete, and rename files and sub directories, too. However, unlike for files, execute permission needs to be enabled for directories for the permission type to take effect. |
| Execute | For files, execute permissions allow the user to execute a file as a script. For directories, the user can access them and access details about files in the directory. |
The above permissions are assigned to three categories:
| User groups | Description |
|---|---|
| Owner | The user who created the file is given full permissions. |
| Group | A set of users that share access to a file with a specific set of permissions. |
| All users | Users on the system who are not owners of the file or directory and are not part of the group associated with the file or directory. These users are given the least access rights by default until elevated permissions are enabled. |
File or directory permissions can either be granted or denied for each of the user categories described above. They are also denoted by numeric values as outlined in the table below:
| Numeric | Symbolic | File permission |
|---|---|---|
| 0 | --- | None |
| 1 | --x | Execute only |
| 2 | -w- | Write only |
| 3 | -wx | Write and execute |
| 4 | r-- | Read only |
| 5 | r-x | Read and execute |
| 6 | rw- | Read and write |
| 7 | rwx | Read, write, and execute |
File modes are typically represented using a three-character sequence, where each character corresponds to a permission. For instance, permission code 764 means read, write, and execute permission for the owner, read and write permission for the group, and read only permission for everyone else.
What is a file mode?
In Linux, a file mode refers to the permissions and access control levels that pertain to a file or directory that determine who can read, write, or execute the file, and what special permissions, if any, are set.
The file mode is represented by a series of ten characters, with the first one indicating the file type we are dealing with; the next nine characters represent the read (r), write (w), and execute (x) permissions for the file's owner, group, and other users.
Let's take a string, drwxr-xr-x, to understand how a file mode can be interpreted.
- d indicates the file type, which is directory.
- rwx means read, write, and execute access for the owner.
- r-x means read and execute permissions for the group.
- r-x means read and execute permissions for other users.
Examples of file mode permissions in Linux:
| File modes | Description |
|---|---|
| -rw-rw-rw- | A file that is open to modification by every user on the system. |
| -rw------- | A file that is only accessible by its owner. |
| drwxrwx--- | A directory that can be modified by its owner and group. |
| -rw-rw-r-- | A file that can be modified by its owner and group but not by others. |
We can concur that the owner is usually granted the most permissions, and by limiting group and other permissions to a subset, Linux ensures that files are accessible only to those who need them while safeguarding information from being susceptible to unauthorized access.
How to check the permissions of a file in Linux
There are several ways to check the permissions of a file in Linux.
- Using the ls command
- Using the stat command
Using the ls command:
The most common method to view permissions of a file is to use the ls command with the long-lasting option (-l).
Syntax: ls -l filename
You can also check the permissions of all files in your directory by running the following command:
ls -l
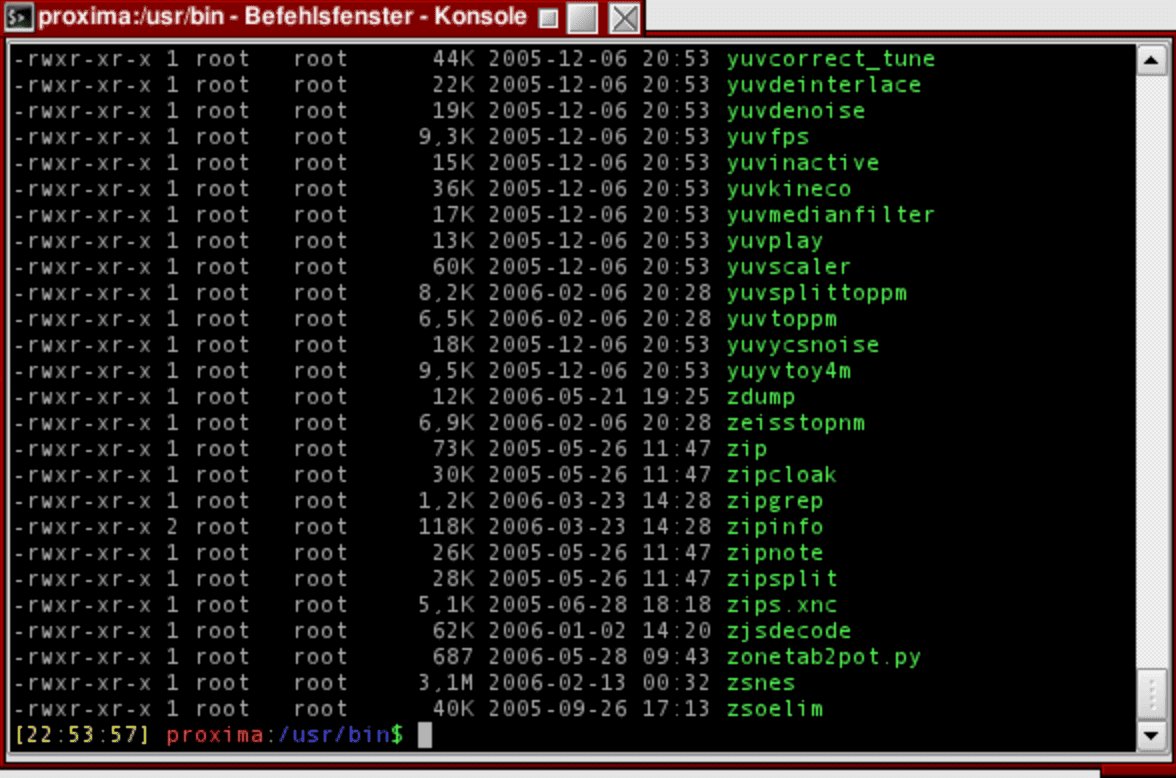
Dissecting long listing output
The components of the output being shown are:
- The file mode
- The owner of the file
- The permission classes corresponding to groups and other users
- The file size in bytes
- The last modified date of the file
- The name of the file
These are the details to pay attention to when you are dealing with a long listing.
What are special permissions?
Linux also has special permissions that provide more granular control over who can manage files and directories, thereby ensuring that users have the right access while also protecting sensitive data from unsolicited modifications. The three main types of special permissions are set user ID, set group ID, and the sticky bit.
setuid permission
When the setuid permission is set on an executable file, it allows users to execute the file with the privileges of the file's owner, rather than their own. This is particularly useful for tasks that require elevated privileges. So, when a user executes a file with the setuid bit set, the process runs with the user ID (UID) of the file's owner. For example, if a file owned by the root user has the setuid bit set, any user executing that file will run it with root privileges.
Setting up the setuid permission on a file using the chmod command
The setuid permission can be assigned to a file using the chmod command by executing the following command:
chmod 4755 filename
Where 4 is the octal representation of setuid's numeric value, and 755 is the permission bits a file holds.
setgid permissions
The setgid permission allows users to execute a file with the permissions of the file's group. When setgid is applied to a directory, files created within that directory inherit the group ownership of the directory rather than the user's default group. This is useful for allowing users in a group to perform tasks that require group-level privileges.
Setting up the setgid permission on a directory using the chmod command
The setgid permission can be assigned to a directory using the chmod command by executing the following command:
chmod 2755 dir
Where 2 is the octal representation of setgid's numeric value, and 755 is the permission bits of the directory.
Sticky bit
The Linux sticky bit permission is useful in instances where you want to restrict what groups and other users can do. When you set a sticky bit on a directory, files in that directory can only be removed or renamed by the owner, and users won’t be able to delete the file, even though the permissions say otherwise.
Understanding and appropriately utilizing special permissions like setuid, setgid, and the sticky bit is important for enhancing security and access control in Linux environments.
Setting a sticky bit permission on a directory is similar to that of setuid and setgid, with the octal representation of the sticky bit being 1.
How to change permissions in Linux
File and directory permissions in Linux can be modified using the change mode command, which reads as chmod.
Using symbolic mode
The syntax for changing permissions on a file using the chmod command is as follows:
chmod [permissions] [file]
Permissions can be set in either symbolic or numeric mode as you deem fit. The chmod symbolic representation particularly uses a single character to indicate the user class.
Here's the complete list of letters and operators that can be used to change a user's access to a file:
| Symbol | What it denotes |
|---|---|
| u | The user who manages the file |
| g | The other users who have specified access to the file |
| o | Others |
| a | All user classes |
| + | Add permissions |
| - | Remove permissions |
| = | Permissions set to specified values |
Let's take a look at an example to understand how the chmod command works.
chmod u+x filename
In this example, execute permission is granted to the owner.
Similarly, the command used if you don't want the group to have write access is:
chmod g-w filename
Maybe you want to set read and write permissions for other users. The command for setting permissions as such for other users is:
chmod o+rw filename
You can also change permissions for all user classes at once by listing the modes separated using commas. Take the following command as an example:
chmod u+x, g-w, o+rw filename
The chmod command provides execute permission for the owner of the file. It also removes the write permission for the group and turns on read and write options for other users.
The following command should be executed if you want all user classes to share permission across the file:
chmod a+rw filename
In this example, the owner of the file, the group, and other users all get to read and write to the file in question.
Changing file permissions using absolute mode:
In this mode, permissions for user classes are represented as a three-digit number. This is called absolute mode, and it uses the following numbers to determine the user’s desired permissions:
| Particulars | Attributed permissions |
|---|---|
| 4 | Read (r) permission |
| 2 | Write (w) permission |
| 1 | Execute (r) permission |
| 0 | No permission whatsoever |
The following example sets read, write, and execute for the owner, read and execute for a group, and read only for other users:
chmod 754 filename
You can also use the -R option to apply the permissions to all files and sub directories. For example, executing the following command grants a user class its specified permissions for all files in the directory.
chmod -R 754 directory_name
You can also change the ownership of a file or directory in Linux using the chown command. The syntax for the command is:
chown [ new owner or group] [ file or directory ]
For example, if you want to change the owner of a file, the command to be executed is:
chown luffy file.txt
The command will change the owner of file.txt to luffy.
You can also change both the owner and the group by using the following syntax:
chown luffy:crossguild file.txt
Executing the above command will change the owner of file.txt to luffy and the group to crossguild.
In this example, the group name (crossguild) starts with a colon (:) to allow the command to distinguish it from a user account (luffy).
Enhancing security for file and directory permissions in Linux with ManageEngine EventLog Analyzer
EventLog Analyzer is a log management tool designed to collect, analyze, and report on various logs across a network, including those related to file operations. Its file integrity monitoring capability provides visibility and detailed reports on actions such as file creation, modification, deletion, and permission changes as well as system file alterations.
This Linux monitoring tool offers detailed insights into who made what changes to Linux files and directories, from where, and when. Further, sysadmins can also get notified on unusual file permission changes, such as file permission changes in bulk, outside of business hours, from unusual locations, and more with the predefined alert profiles. This helps ensure the integrity of data stored in the file system. Further, the solution also provides detailed audit trails on file permission changes and other file operations.