- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
The System Logging Protocol (syslog) is a standardized protocol that enables network devices, routers, switches, firewalls, and Unix/Linux servers to communicate log messages in a universal format.
The challenge
As organizations grow, manual syslog analysis consumes four to eight hours weekly per engineer, compliance audits require over 40 hours of manual work, and visibility across multi-vendor infrastructure becomes impossible. Basic syslog servers only store logs, but they don't analyze them.
What is syslog management and why does it matter?
Syslog management is the practice of automating syslog collection, parsing, analyzing, and storing logs in a centralized manner, enabling real-time analysis, threat detection, and compliance.
ManageEngine EventLog Analyzer centralizes syslog management from Cisco, Palo Alto, Fortinet, Juniper, Check Point, and over 30 other vendors. It transforms raw syslog data into actionable intelligence, supporting RFC 3164, RFC 5424, and CEF formats from over 1,000 device types.
Key benefits:
- Simplify compliance with over 1,000 prebuilt audit reports for the PCI DSS, HIPAA, SOX, GLBA, FISMA, ISO 27001, and more.
- Reduce downtime through automated parsing, correlation, proactive alerting, and automated incident response workflows.
- Real-time syslog visibility across your entire infrastructure via searchable archives and live dashboards.
- Audit-ready evidence with tamper-proof syslog archival and encrypted storage (one to seven year retention).
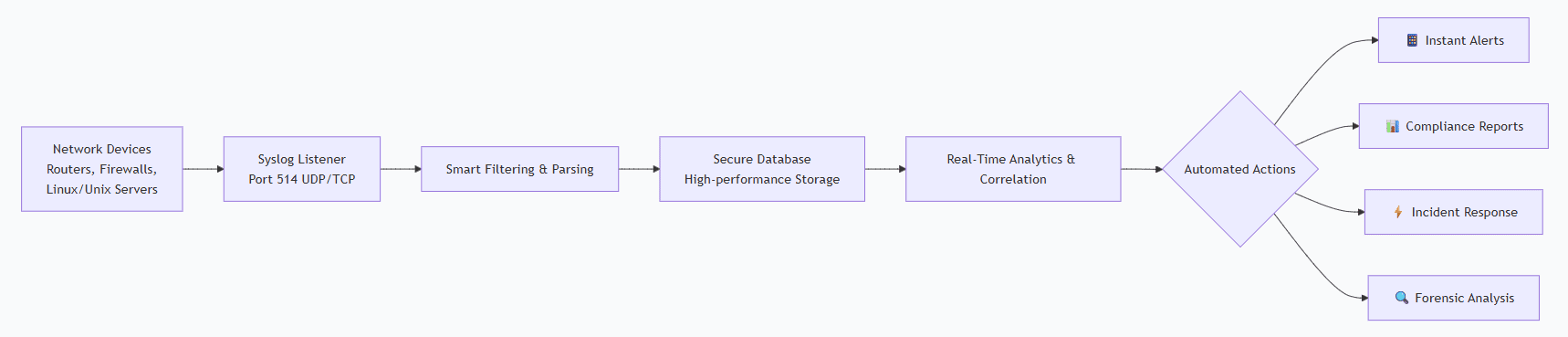
How syslog management works
Every syslog management solution has three core components:
- Collection: Receives syslog messages from network devices and applications (typically port 514, UDP/TCP). EventLog Analyzer supports both UDP (fast) and TCP (reliable) for flexible syslog transport optimization.
- Storage and indexing: Efficiently stores and indexes massive syslog volumes for instant retrieval. Structured database enables rapid syslog search across your entire log archive by severity, source, timestamp, or extracted fields.
- Analysis and reporting: Standard syslog servers provide basic filtering. EventLog Analyzer adds automated intelligence: syslog correlation, compliance reporting, and alerting, turning raw syslog data into strategic assets.
Syslog vs. Windows event log: Understanding the difference
| Aspect | Syslog | Windows event log |
|---|---|---|
| Protocol | Standardized across vendors | Windows-specific |
| Format | RFC 5424 standard | Windows binary/XML |
| Coverage | Network devices, Unix/Linux, multi-vendor | Windows systems only |
| Flexibility | Works with most log management tools | Limited to Windows environment |
For enterprises with mixed infrastructure, syslog management centralizes logs from network devices, Unix/Linux, and Windows systems in one platform, solving the unified visibility challenge that scattered syslog servers create.
Why use EventLog Analyzer for syslog management?
- Better than basic syslog servers: Standard syslog servers store logs and provide filtering, meaning you do the analysis manually. EventLog Analyzer adds automated intelligence: syslog correlation, over 1,000 predefined alerts, compliance reporting, and secure archival.
- Faster compliance audits: Manual syslog reporting takes 40–60 hours per audit cycle. EventLog Analyzer generates audit-ready syslog reports in minutes, saving approximately $60K–$80K annually in labor and reducing audit time by 80%.
- Unified visibility across vendors: Managing syslog from Cisco, Palo Alto, and Juniper separately creates operational complexity. EventLog Analyzer centralizes syslog management from over 1,000 device types with native parsing and automatic field extraction—no per-device configuration needed.
- Cost-effective alternative to enterprise SIEMs: Enterprise SIEMs cost $50K–$500K+ annually. EventLog Analyzer provides syslog management with correlation, compliance reporting, and alerting at a fraction of SIEM costs, optimized specifically for syslog data.
EventLog Analyzer vs. rsyslog, syslog-ng, and alternatives
Rsyslog and syslog-ng are excellent open-source log transport tools that efficiently collect and forward syslog messages. They excel at filtering and forwarding but lack correlation, compliance reporting, and analytics.
EventLog Analyzer includes syslog collection of rsyslog and syslog-ng, plus you get the intelligence layer with automated syslog correlation, compliance automation, and reporting, all in one platform with minimal setup.
| Capability | Rsyslog/Syslog-ng | EventLog Analyzer |
|---|---|---|
| Syslog collection | Yes | Yes |
| Syslog correlation | No | Yes |
| Compliance reporting | No | Over 1,000 reports |
| Setup time | 2–4 weeks | Under 30 minutes |
| Expert configuration | Yes | No |
Key benefits of our syslog management solution
- Real-time threat detection: Get instant notifications via email, SMS, or SNMP traps. Includes over 1000 predefined alerts and the ability to build custom ones using the Alert Profile builder. Detect brute-force attacks, data exfiltration, and policy violations.
- Automated correlation engine: Move beyond simple alerts. Our rule-based correlation engine includes predefined rules for common attack chains and a custom rule builder to match your unique environment. Correlate events across Windows, Linux, network devices, and applications.
- Secure, audit-ready archiving: Meet GDPR, PCI DSS, and other regulatory retention mandates (one to seven years). Archives are encrypted and tamper-evident. The archive manager allows for easy search and restoration of historical data for forensics.
- Compliance reporting simplified: Generate audit-ready reports for the PCI DSS, HIPAA, SOX, GLBA, FISMA, and ISO 27001 in minutes. Custom report builder allows creation of any report based on extracted log fields. Schedule and distribute reports automatically to auditors.
- Accelerated incident response: Reduce response time with the Incident Workbench, providing user analytics, process analytics, and advanced threat analytics in one pane. Automate responses with workflow profiles that can execute scripts, block network access, or integrate with IT service management tools.
- Scalable, robust architecture: Start with the Standalone Edition and seamlessly upgrade to the Distributed Edition as your log volume grows. The distributed architecture uses a central admin server and multiple managed servers to handle tens of thousands of EPS.
How leading organizations transformed their security with syslog management
Here are three real-world customer stories showcasing how leading organizations have transformed their security posture through strategic syslog management.
Benefit One Inc. lowered costs and centralized syslog visibility
The challenge:
Benefit One Inc. needed continuous visibility into its member services platform but lacked automated monitoring. Syslog-driven server and firewall oversight was outsourced, costing more time and money without improving security.
The syslog management solution:
With EventLog Analyzer, Benefit One centralized syslog collection from firewalls, switches, and servers, automated alerting, and gained unified visibility. Syslog correlation helped detect suspicious internal activity while reducing manual checks.
The outcome:
- 20% reduction in operational costs.
- Real-time firewall and network visibility.
- Faster troubleshooting through centralized syslog dashboards.
- Reliable monitoring without outsourcing.
CVGT Employment strengthened security and compliance through syslog monitoring
The challenge:
Across 120+ offices, CVGT Employment lacked visibility into server, workstation, and network events. With no centralized syslog collection, detecting anomalies or demonstrating ISO 27001/ACSC ISM compliance was difficult.
The syslog management solution:
Enabled unified monitoring with syslog ingestion from firewalls and network systems, real-time detection of lockouts and unauthorized access, and automated alert forwarding to ServiceDesk Plus.
The outcome:
- Mean time to detect reduced to under one minute.
- Stronger audit readiness with syslog-backed reports.
- Faster incident response via automated syslog alerts.
- Simplified monitoring across hybrid infrastructure.
HA International automated syslog alerts and achieved rapid threat detection
The challenge:
HA International relied on manual log checks and a basic syslog server, making it difficult to identify threats across AD, SQL, VMware, and its Cisco/Meraki environment.
The syslog management solution:
Automated syslog collection from firewalls and switches provided real-time alerts on brute-force attempts and abnormal device activity and correlated syslog with Windows and VMware logs for deeper context.
The outcome:
- Threat detection accelerated from days to seconds.
- Immediate investigation of suspicious account activities.
- Improved audit readiness with consistent syslog reports.
- Eliminated manual monthly monitoring.
Spending 40–60 hours per audit cycle on manual syslog analysis?
Replace rsyslog and syslog-ng complexity with EventLog Analyzer. Centralize syslog management from your entire infrastructure, with automated compliance reporting, real-time visibility, and instant syslog search across all your devices.
Frequently asked questions
Syslog messages follow RFC 5424 standard with header (timestamp, hostname, priority), structured data (key-value pairs), and message content. EventLog Analyzer parses all syslog formats including RFC 3164 and CEF, automatically extracting searchable fields.
UDP is faster (port 514) but may lose messages in high-traffic environments. TCP is slower but guarantees reliable delivery of every syslog message (port 6514). Use UDP for non-critical, high-volume syslog, and use TCP when syslog data loss would impact compliance or security investigations. EventLog Analyzer supports both for flexible syslog transport optimization.
Syslog severity levels (0–7, Emergency to Debug) categorize log message importance. They help prioritize action: Emergency (0) and Alert (1) require immediate attention, while Warning (4) and Debug (7) are less urgent. EventLog Analyzer automatically filters and alerts based on severity levels, helping your team focus on critical syslog events first.
No. Windows doesn't natively support syslog; it generates Windows event logs, which can be viewed using the Windows Event Viewer. However, EventLog Analyzer can collect Windows event logs directly from servers and syslog messages from network devices, correlating both within a single unified platform for complete infrastructure visibility.
Most customers are up and running in under 30 minutes. The setup wizard, auto-discovery of syslog devices, and preconfigured dashboards provide immediate visibility. Our customers see value on day one.
Yes. The Distributed Edition is designed for large enterprises and MSSPs. It uses a central admin server with multiple managed servers to scale horizontally, handling 50,000+ devices and 20,000+ EPS.
EventLog Analyzer can act as a powerful log collection and normalization layer. It parses raw logs, enriches them, performs initial correlation, and can forward filtered, high-value events to your SIEM, reducing ingestion costs and noise.











