Linux vulnerability scanner meticulously inspects Linux-based systems to mitigate potential risks and vulnerabilities.
Organizations are increasingly gravitating towards Linux as their preferred OS for both desktops and servers due to its reliability, adaptability, and ease of configuration. Due to this rising prevalence, Linux has amassed increasing attention among threat actors in recent days. Therefore, it's become necessary to employ a Linux vulnerability scanner to regularly identify vulnerabilities and misconfigurations in your Linux deployments and applications running on them. Even with regular scanning, only by applying timely remediation can risks to the network be minimized.
ManageEngine Vulnerability Manager Plus, is an end-to-end vulnerability management solution, that offers automated scanning, risk-based assessment, and built-in remediation of vulnerabilities and misconfigurations for all major distros of Linux, in addition to Windows OSs.
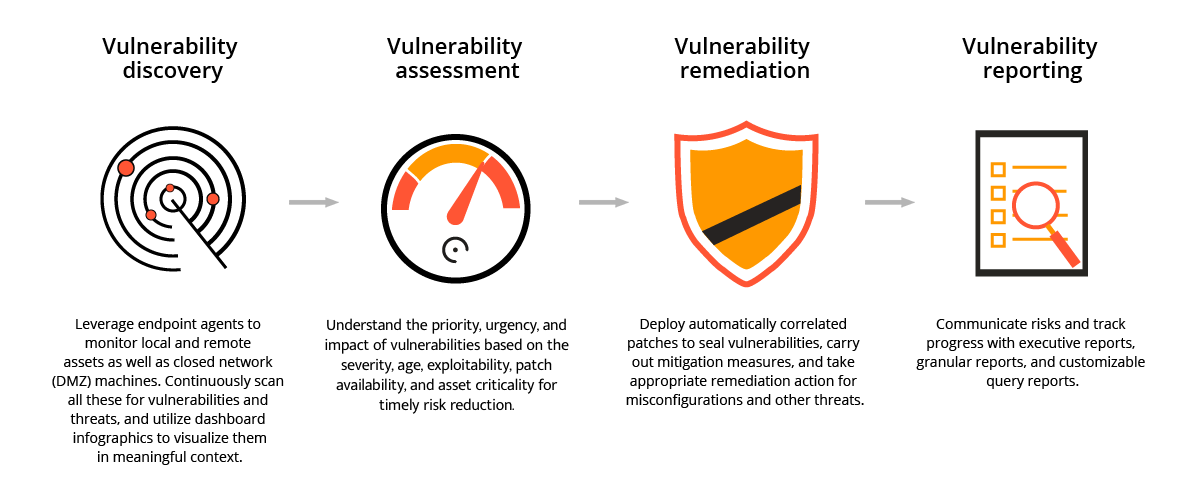
ManageEngine's Linux Vulnerability Scanner operates by conducting comprehensive scans of Linux systems, applications, and network components. The tool identifies vulnerabilities, provides detailed reports, and offers remediation recommendations to strengthen the security posture of Linux environments.
Vulnerabilities are expanding exponentially, and so are the release of patches to fix them. To give you an example, SUSE Linux alone releases 300 patches a month to resolve vulnerabilities and bugs. Considering the number of Linux endpoints to be patched and the complexities involved, warding off vulnerabilities is often a cumbersome task.
What if we told you there's a way to prioritize high-risk vulnerabilities while patching the rest on an automated basis?
Vulnerability Manager Plus, with its integrated vulnerability and patch management functionality, automates your regular patching schedules, enabling your IT staff to spend more time on assessing and prioritizing high-risk vulnerabilities. This integrated approach eliminates the need for multiple agents, disparity in data transferred between solutions, potential delays in remediation, unnecessary silos, and false positives, all of which increase the effectiveness of your overall Linux vulnerability management program.
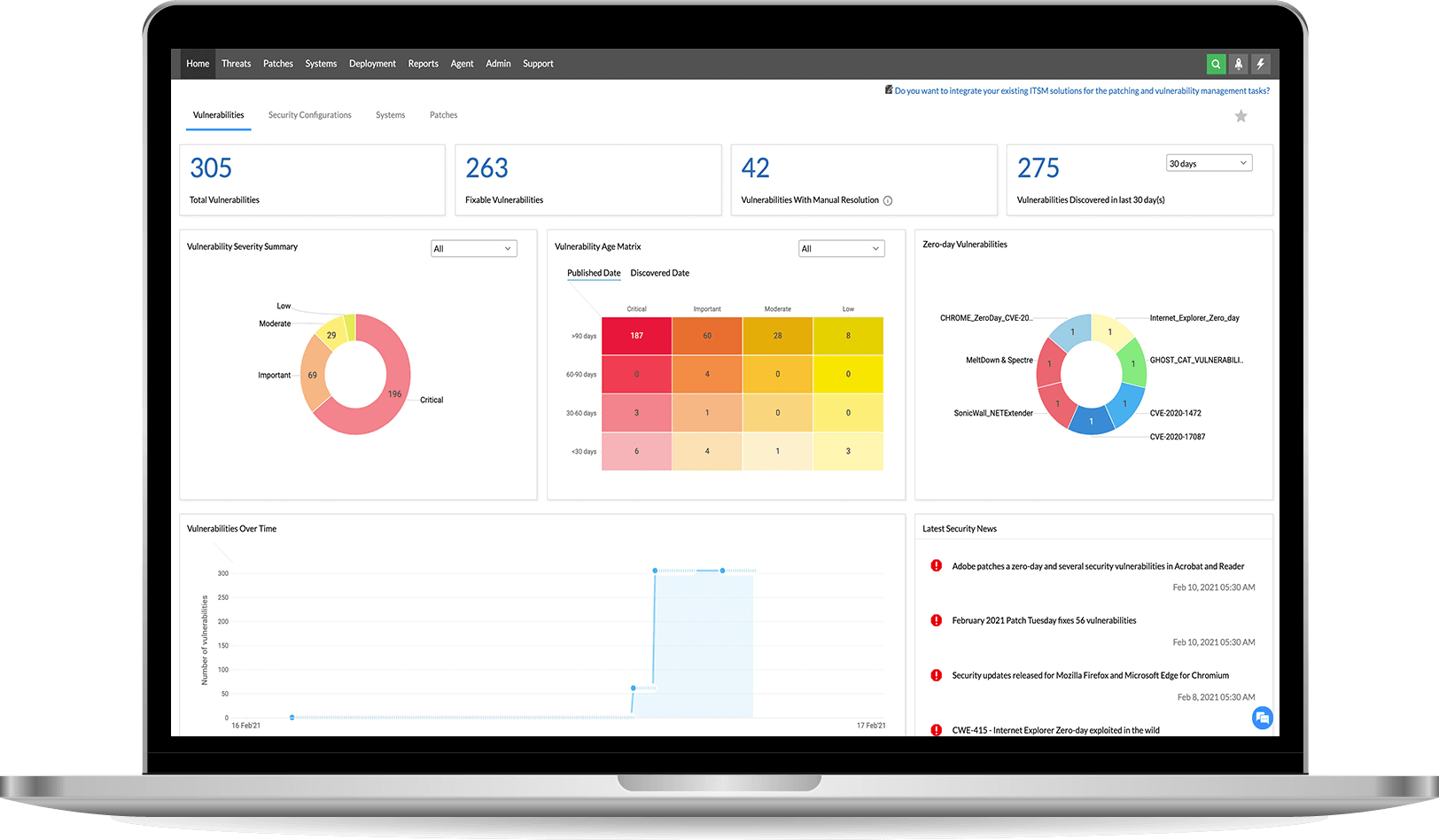
Continually detect OS and third-party vulnerabilities in systems, servers, virtual machines, and laptops, as well as web servers and database servers that run on the Linux platform.
Triage exploitable and impactful vulnerabilities with risk factors such as Common Vulnerability Scoring System (CVSS) scores and severity ratings, exploit availability, intel on exploit activity published in continually updated security newsfeed, vulnerability age, affected asset count, Common Vulnerabilities and Exposures (CVE) impact type and patch availability.
Leverage a dedicated tab that isolates zero-day vulnerabilities and publicly disclosed vulnerabilities from the rest. This enables you to swiftly identify them and administer workarounds to all the affected machines in an instant, preventing exploitation of those vulnerabilities until fixes are rolled out by vendors.
Automatically correlate corresponding patches to detect vulnerabilities with the integral patching module. This allows you to push patches to affected machines and close the vulnerability management loop instantly without employing multiple solutions.
See the full list of Linux OSs and applications for which vulnerability management is supported by Vulnerability Manager Plus.
Ditch the manual, clumsy command-line approach to Linux patching. You can now automate the entire cycle of patching—from scanning to deployment—for all major Linux distros from once central location.
Patch an extensive list of more than 350 third-party applications for the Linux platform, including the largest patch repository from Adobe, Java, and various Internet browsers. You don't have to spend countless hours of research, creation, testing and deployment of third-party packages. Vulnerability Manager Plus simplifies third-party patching by providing pre-built, tested, and ready-to-deploy packages.
Customize every aspect of the patching processing, including scheduling deployment of patches during non-business hours, initiating deployment for specific users at system start-up, enabling users to postpone deployments, and much more.
Cancel or postpone Linux server patching and reboots until the weekend or off-hours to minimize downtime.
Automatically test patches for incompatibility issues, unintended bugs, or any other installation failure issues before rolling them out to production machines.
Practice bandwidth-efficient patching. Patches are only downloaded once for your whole network and it's replicated to your Linux endpoints via endpoint agents.
Configure remote agents to directly download patches from vendor sites to remote clients with zero impact to VPN bandwidth. This ensures no waiting for remote clients to log on to your network via VPN. From scanning to deployment, everything is silently accomplished with the help of lightweight agents residing in your remote clients. Learn more about securing remote endpoints.
With a predefined library of security configuration baselines derived from industry standards and best practices, Vulnerability Manager Plus continuously detects and reports on systems that are not aligned with your security configurations—and all without any user intervention. You can push the resolution to all affected machines and close the security configuration management loop instantly.
According to Wired, around 67 percent of web servers worldwide run on Linux. Linux's popularity as a platform for hosting web servers, makes it a prime target for remote code execution (RCE), cross-site scripting (XSS), and denial of service (DoS) attacks. Gain continuous visibility on misconfigurations that can lead to security flaws in web servers such as Apache, Nginx, Internet Information Services (IIS), and Tomcat and utilize the security recommendation to set-up the servers in a fashion that makes them secure against multiple attack variants.
Gaining continuous visibility over the active ports in your network systems, and discover what is listening on each port so you can identify ports that may be activated by malware or unsecure services.
Sniff out endpoints with missing, disabled, or out-of-date antivirus, and ensure your enterprise-grade antivirus software is up and running with the latest definitions.
Track the Linux operating systems and applications running on Linux platform that are approaching, or have already reached, end of life. Identify peer-to-peer and remote desktop sharing software deemed unsafe, and uninstall it with a click of a button.
Now you can perform complete vulnerability management—from scanning to remediation—for all the major Linux distros directly from a single pane of glass.
A Linux vulnerability scanner is a specialized vulnerability scanning tool designed to identify security vulnerabilities and weaknesses in Linux-based systems. It scans for misconfigurations, outdated software versions, and known vulnerabilities.
A Linux vulnerability scanner is essential for identifying security weaknesses and vulnerabilities specific to Linux systems. It helps ensure proactive security measures, timely patch management, and effective risk mitigation.
Linux vulnerability scanning offers benefits such as identifying weaknesses in Linux systems, facilitating effective patch management, and enabling proactive vulnerability remediation. By scanning for vulnerabilities, organizations can enhance the security of their Linux environments and mitigate potential risks.
When choosing a vulnerability scanning tool, prioritize comprehensive coverage across systems, applications, and networks. Look for tools with up-to-date vulnerability databases, flexible scanning options, and robust reporting capabilities. Ensure the tool supports your platform and technology requirements, providing detailed reports for effective vulnerability management.
View the OS comparison matrix for all the capabilities supported for Linux.
Leverage the built-in database that holds a long history of, and is continually fed with, regular updates on vulnerability information, patch details, configuration baselines, and more that forms the basis for scanning and remediation.
View the consolidated data collected across multiple endpoints, including vulnerability status, patch status, configuration posture and system details, in a web console for centralized management. This information is represented in a dashboard with meaningful context and actionable insights for quick remediation.
Deploy lightweight endpoint agents to carry out all vulnerability management activities. These agents are designed to have minimal impact on the system and the network, giving you direct access to all hosts without disrupting your end users. They don't require host credentials to run. Since they reside on your endpoints, you can secure your assets irrespective of their whereabouts—whether they are located at the local office, on a demilitarized zone (DMZ), at a remote location, or always on the move..
Leverage the secure gateway server to receive communication from remote agents over the internet, and redirect it to the primary server hosted within your corporate firewall to prevent the primary server from being exposed to the internet.
Create roles and delegate routine activities to chosen users with well-defined privileges, so that you can focus on the more pressing areas without compromising the security.