Configuring SAML Single Sign-On for Okta
Key Manager Plus (KMP) integrates with Federated Identity Management Solutions to act as the SAML service provider and works with SAML identity providers to offer single sign-on. Okta is an identity and access management solution that acts as an identity provider and lets users to log into other systems using its single sign-on (SSO) feature. Through this integration, KMP acts as the service provider and allows users to log into the KMP interface using Okta's SAML SSO. Key Manager Plus provided out-of-the-box support for Okta SAML SSO.
Prerequisite: Before proceeding with the configuration steps, add Key Manager Plus as an application in Okta.
Below mentioned are the steps for configuring SAML SSO with Okta:
- Adding KMP as an application on the Okta Dashboard
- Configuring Okta details in Key Manager Plus
- Assigning the Application to Users in Okta
- Setting up SAML SSO in Key Manager Plus
1. Adding KMP as an Application on the Okta Dashboard
1. Log in to your Okta Admin account and click 'Applications' tab.
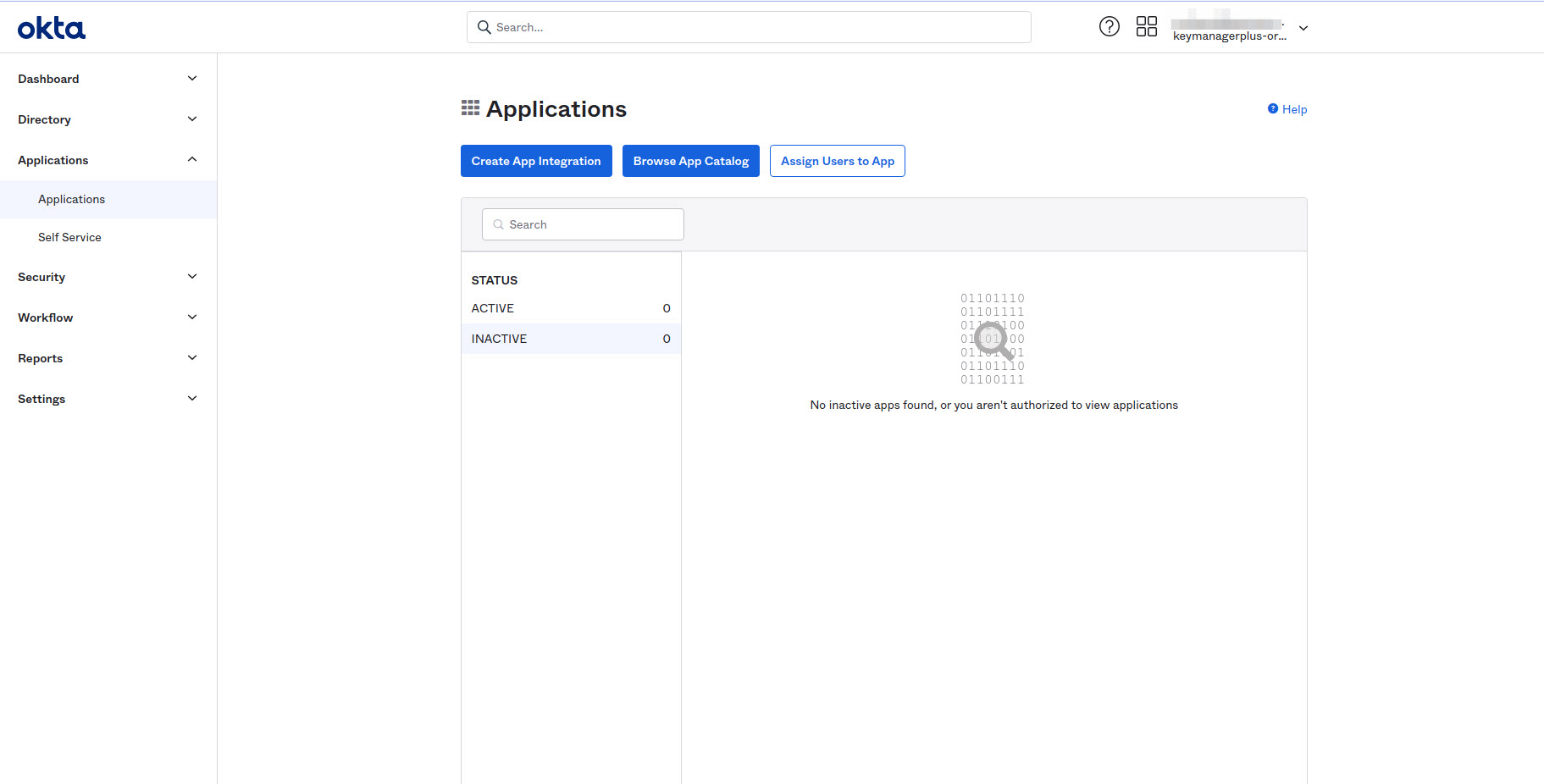
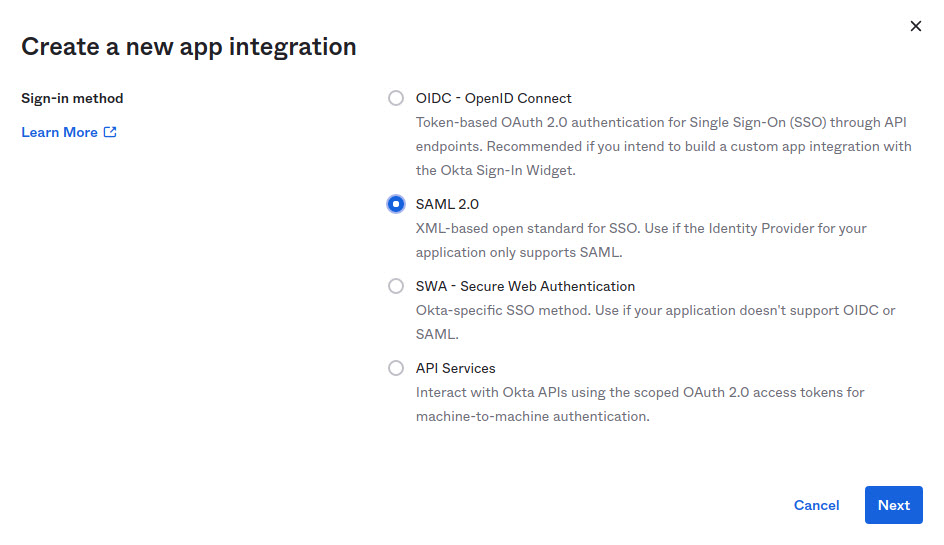
2. In the new page that opens up, select Create App Integration and select SAML 2.0 and click next.
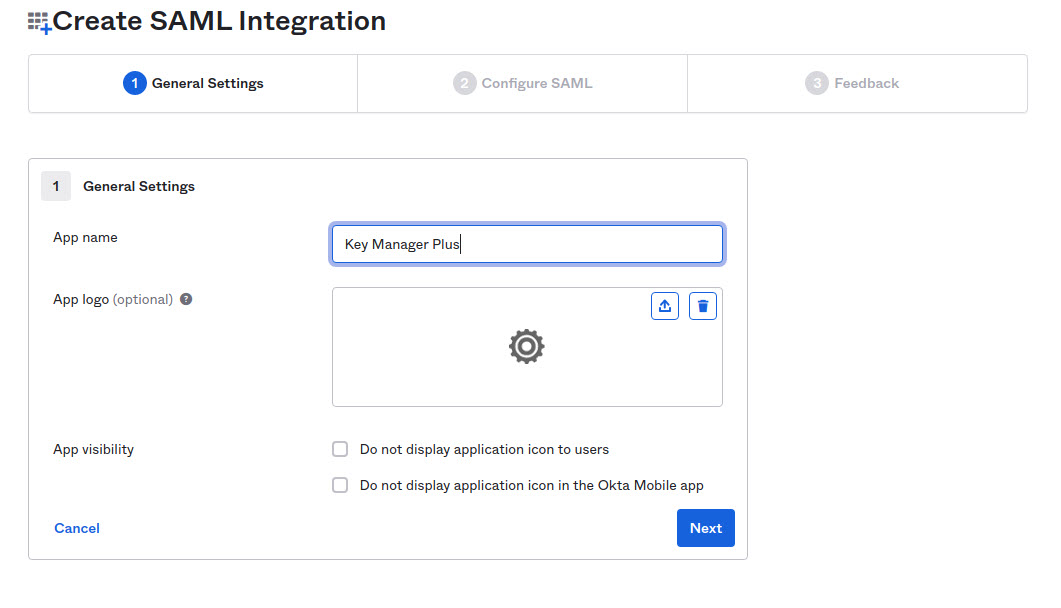
3. Provide App name (Key Manager Plus) and click Next.
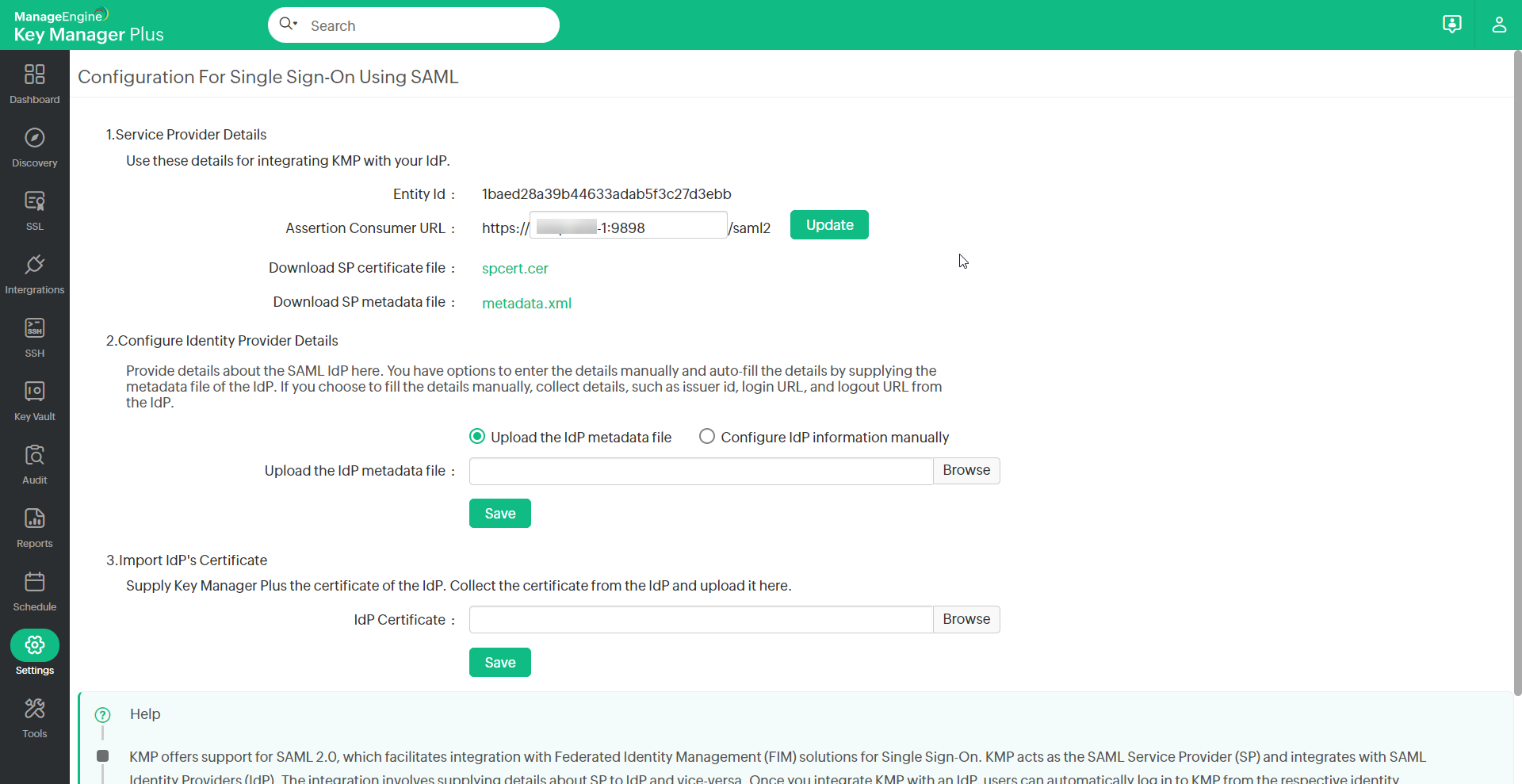
4. The second step in configuring SAML integration consists of providing details about the Service Provider (ME KMP) to Okta.
i. To access these details, go to KMP Homepage and select Settings >> User Management >> SSO.
ii. Under 1. Service Provider Details, you will find Entity Id, Assertion Consumer URL; copy the values.
5. Go back to Okta's SAML Settings page.
6. Enter Assertion Consumer URL from KMP under SSO and deselect the checkbox Use this for Recipient URL and Destination URL and mention the Assertion Consumer URL from Key Manager Plus under Recipient URL and Destination URL.
7. Mention the Entity Id from KMP under Audience URI (SP Entity ID).
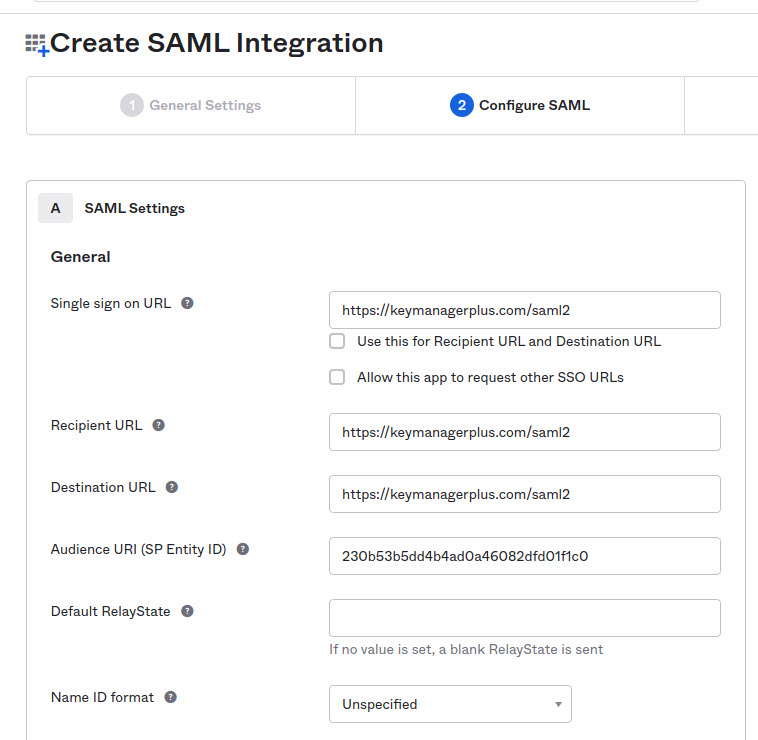
8. After filling in the Single Sign On URL and SP Entity ID (Audience URI) fields, specify how you want Okta to recognize the names of your users in KMP. Since the way in which the usernames are displayed in Okta is different from how they are depicted in KMP, you have to specify the format. There are two scenarios here:
Scenario 1: If you have imported users from AD into KMP, they would have been imported in the format Domain\Username. For more help on integrating Okta with your on-premise AD, please check Okta's help documentation. In Okta GUI, choose the option "Custom" from the drop-down "Name ID format". Then, specify the custom format as given below:
toUpperCase(substringBefore( substringAfter(user.email, "@"), ".")) + "\" + substringBefore( user.email, "@")
Scenario 2: If you have not used AD integration in KMP, select the option Okta Username Prefix. This is because in Okta, user profiling is done in the format username@domain.com. But, in KMP, user names are depicted only as usernames.
This step is crucial because, only if you specify the correct Name ID format in Okta, you will be able to assign the application (KMP) to other users in Okta.
9. Once you have filled in the required details as mentioned above, click 'Finish' to add the application. On addition, the application details will be displayed as shown in the image below. Click the 'Sign On' and then select 'View Setup instructions'. A new tab will open containing the details required to configure SAML 2.0 in KMP.
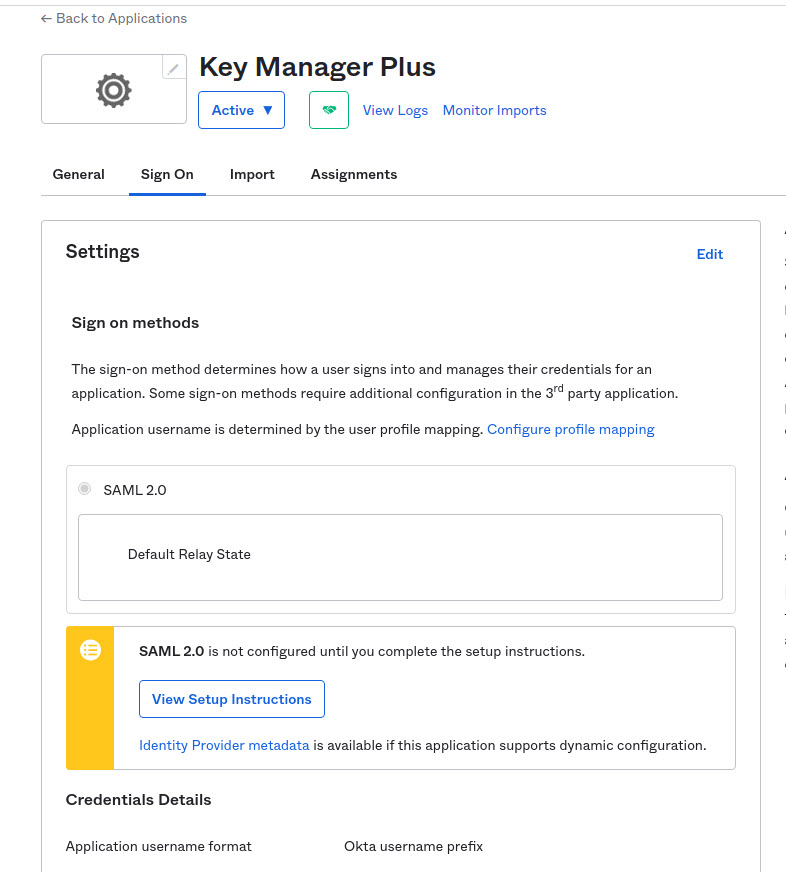
2. Configuring Okta Details in Key Manager Plus
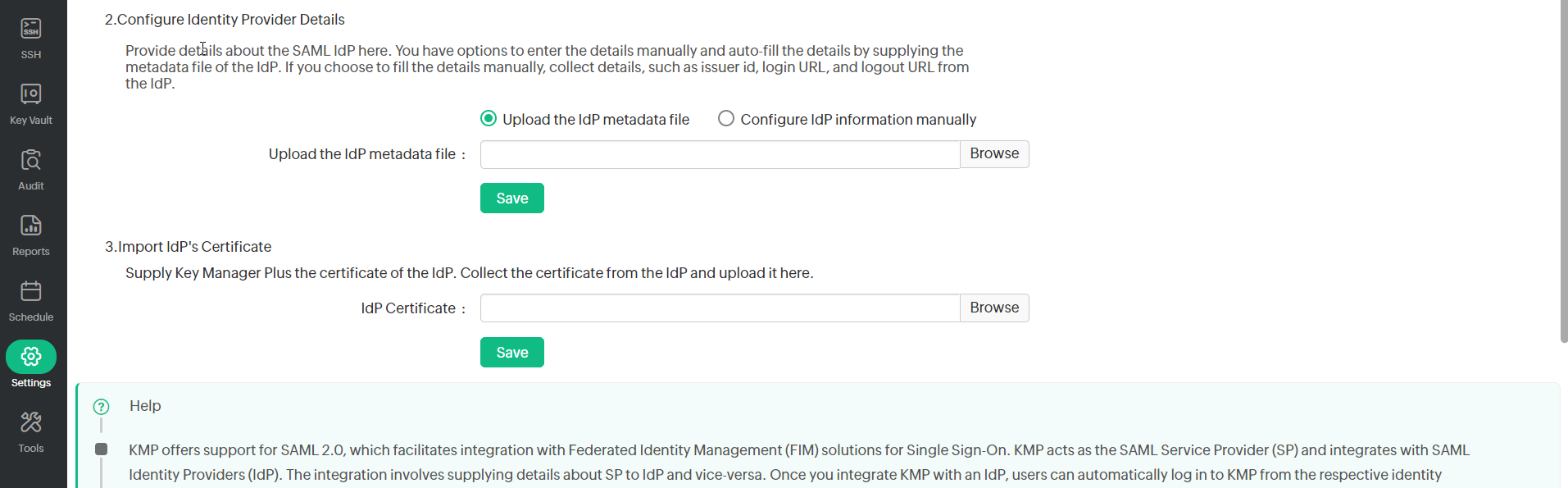
To continue the set up process, configure IdP details in KMP; This is done as part of the second step, Configure Identity Provider Details in KMP's SAML Single Sign On page. Here, you have the option either to enter the details manually or auto-fill the same by supplying the metadata file from the IdP.
- Manual Set-up: If you choose to fill the details manually, get the IdP details such as Issuer ID, Login URL, and Logout URL from the Setup Instructions page of Okta. Configure the same in the step 2 given in KMP SAML Sign On configuration page. Enter the details in the corresponding fields and also download the Okta certificate and upload onto the KMP client (Listed as the 3rd step in the KMP GUI).
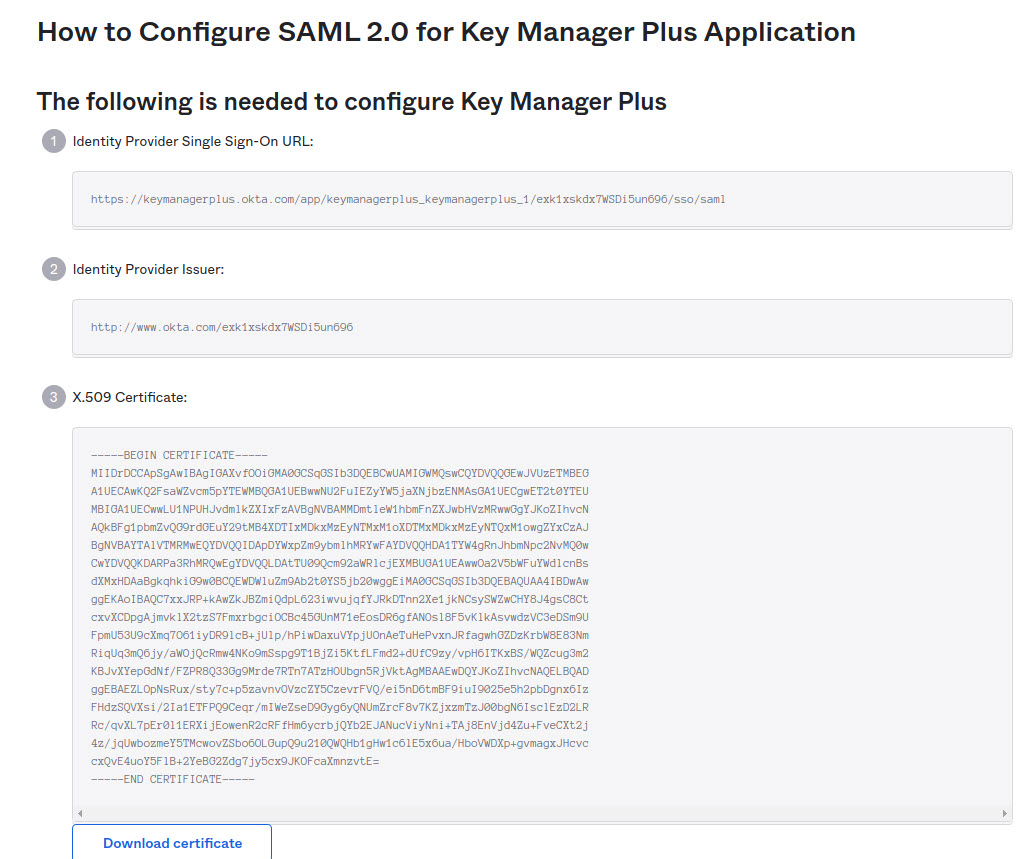
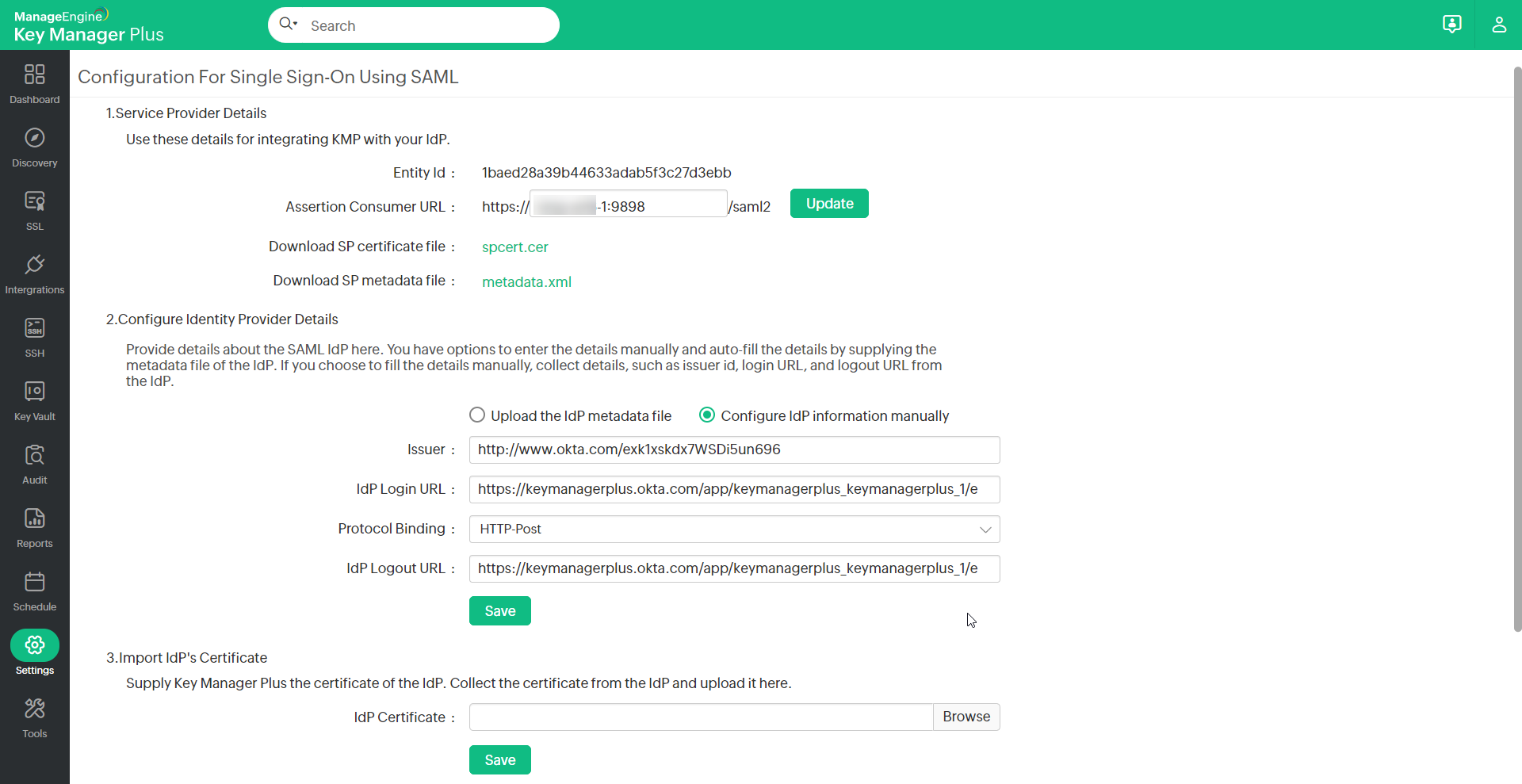
2. Auto-Filling with IdP Metadata File: Scroll down on the SAML 2.0 setup instructions page of Okta and you will find the IdP metadata under Optional. Copy the text and save in a file with .xml extension. Now, upload the same .xml file onto the KMP client. In this case, you need not import IdP certificate in KMP. It will be updated automatically.
3. Assigning the Application to Users in Okta
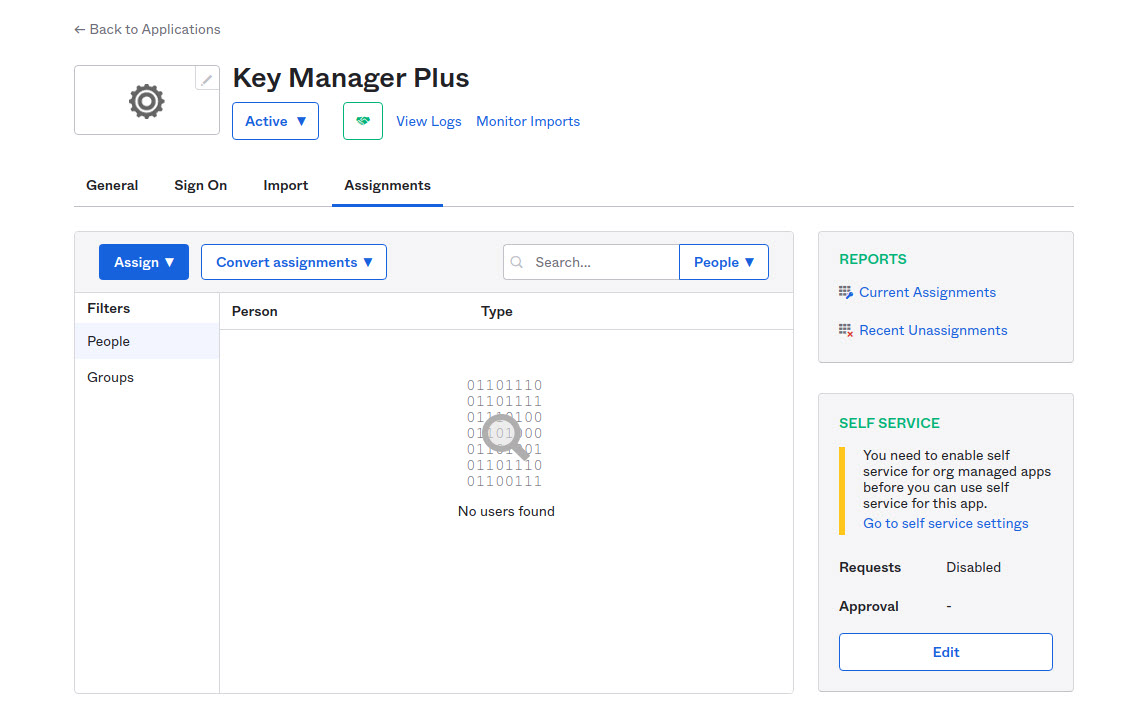
After completing the configurations in KMP, go back to Okta to assign the newly added application to your users.
- Navigate to Applications, click Application and select the Assignments tab.
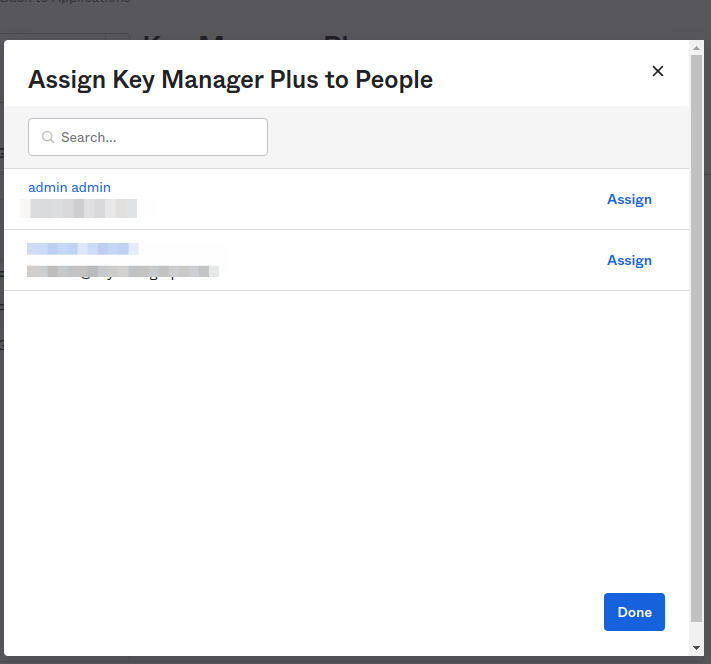
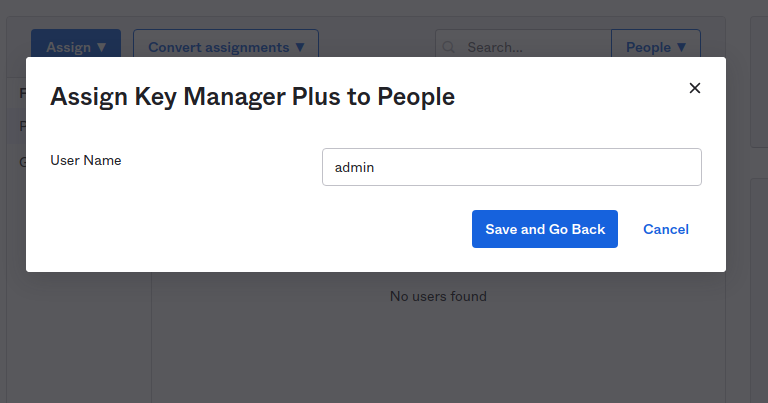
- Click the Assign option and select Assign to people and select the Assign option available beside the user in the list.
- Provide the App user name as the user name in KMP.
4. Setting up SAML SSO in Key Manager Plus
The final step of this configuration is enabling SAML Single Sign On in KMP. This would be shown as the 4th step in the SSO page in KMP GUI. Click Enable to enable SSO.