Thank you for your interest!
View answer
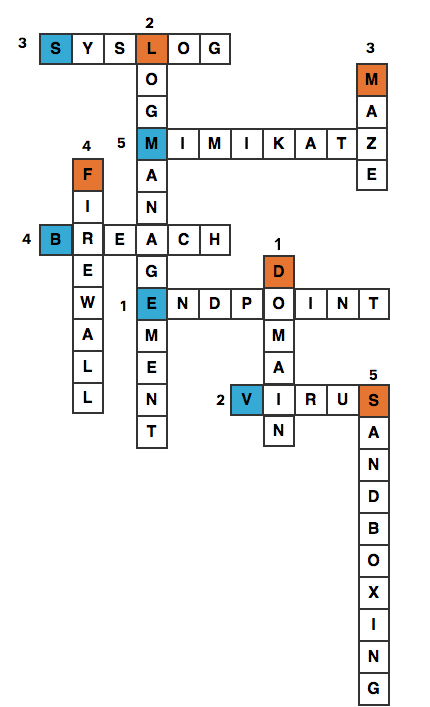
The below logic is an example of which cyber-attack that targets the vulnerabilities on the databases?
‘ OR ‘1’=’1′ — ‘ OR ‘1’=’1′ { ‘ OR ‘1’=’1′ /*
What was the name of the first computer virus?
Which OS was written based on Knoppix by Kali Linux?
Who coined the term Virus?
A virus that migrates freely within a large population of unauthorized email users is known as _____?
Keylogger is a type of _____?
Name the process of altering the data so that it is not used unless the changes are undone.
Code Red is an example of _____?
_____ is a computer security venture that gives data about security vulnerabilities and helps in penetration testing and IDS signature advancement.
What does DDoS stand for?
ManageEngine Log360 help strengthen your defense against cyberattacks, data breaches, and identity thefts.
Try Log360Your Answer:
Correct Answer: SQL injection
Your Answer:
Correct Answer: Creeper system
Your Answer:
Correct Answer: Backtrack
Your Answer:
Correct Answer: Len Adleman
Your Answer:
Correct Answer: Macro
Your Answer:
Correct Answer: Spyware
Your Answer:
Correct Answer: Encryption
Your Answer:
Correct Answer: Virus
Your Answer:
Correct Answer: Virus
Your Answer:
Correct Answer: Virus
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.
