-
IT sabotage
When an insider intentionally misuses information technology (IT) to cause harm to the organization or an individual.
-
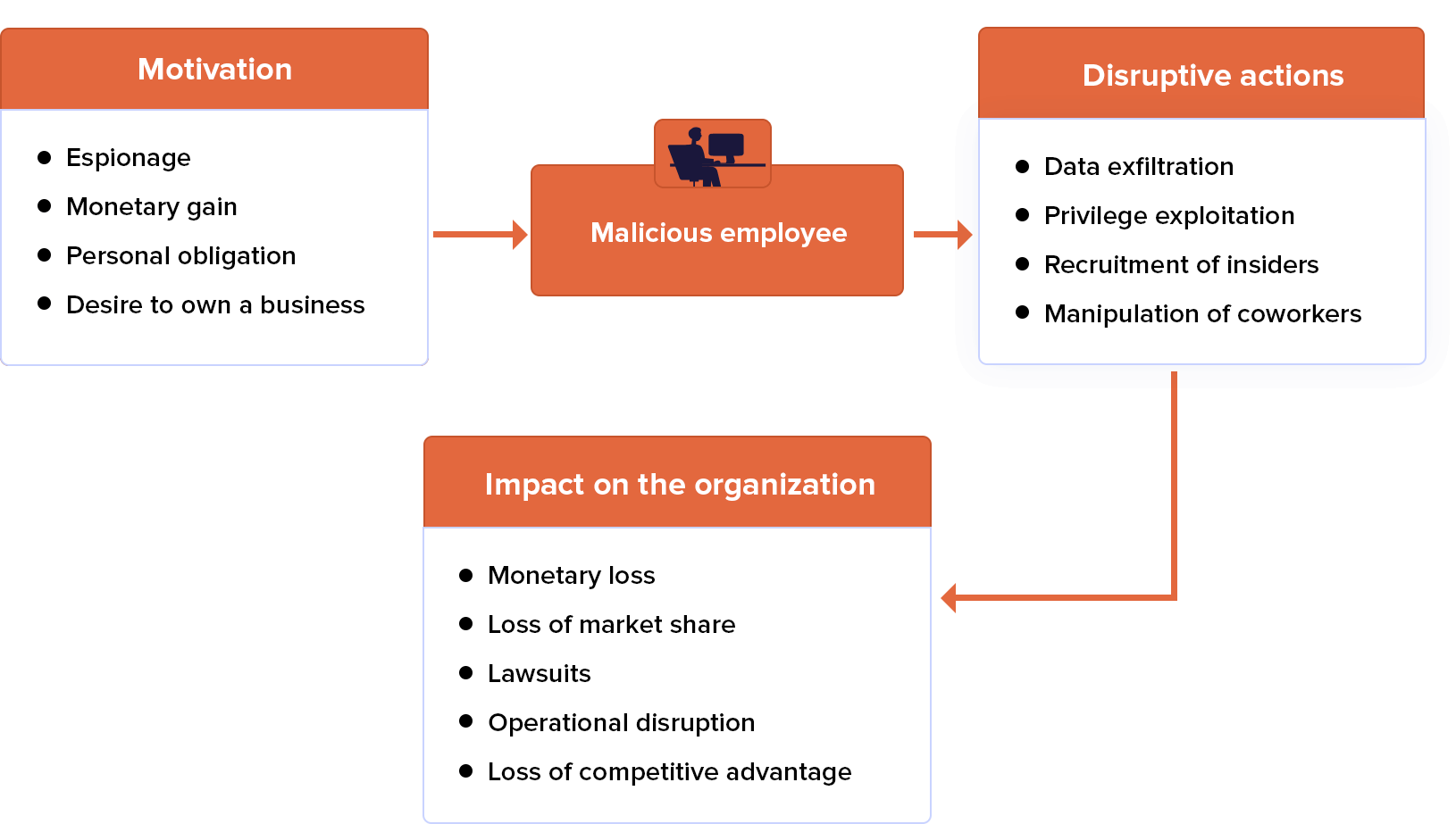
Intellectual property theft
When an insider misuses IT to steal intellectual property from the organization for personal gain or to sell this information to another firm.
-
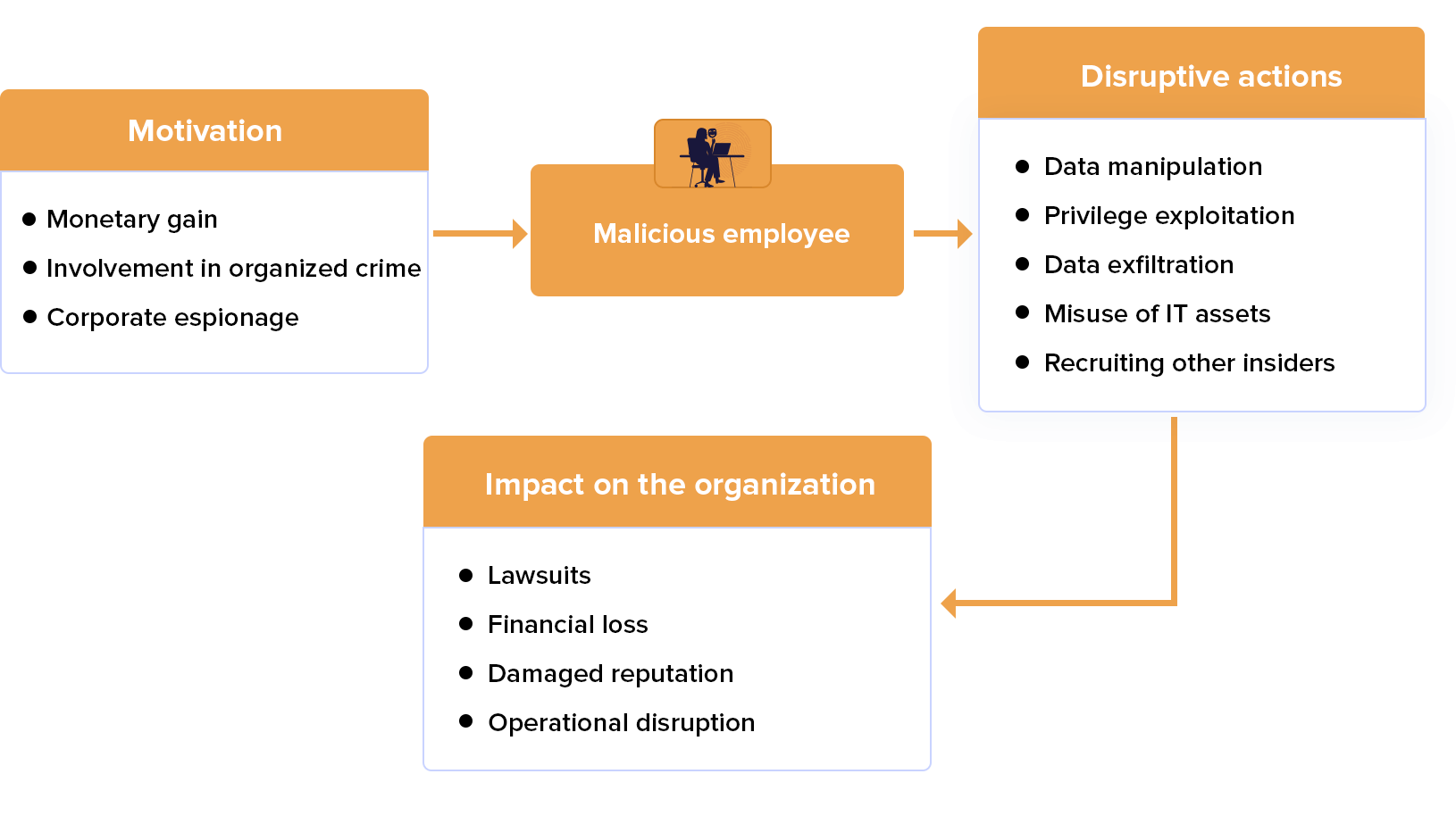
Insider fraud
When an insider utilizes IT to carry out unauthorized addition, deletion, or modification of the organization's information for personal gain, or steals data to conduct identity theft.
-
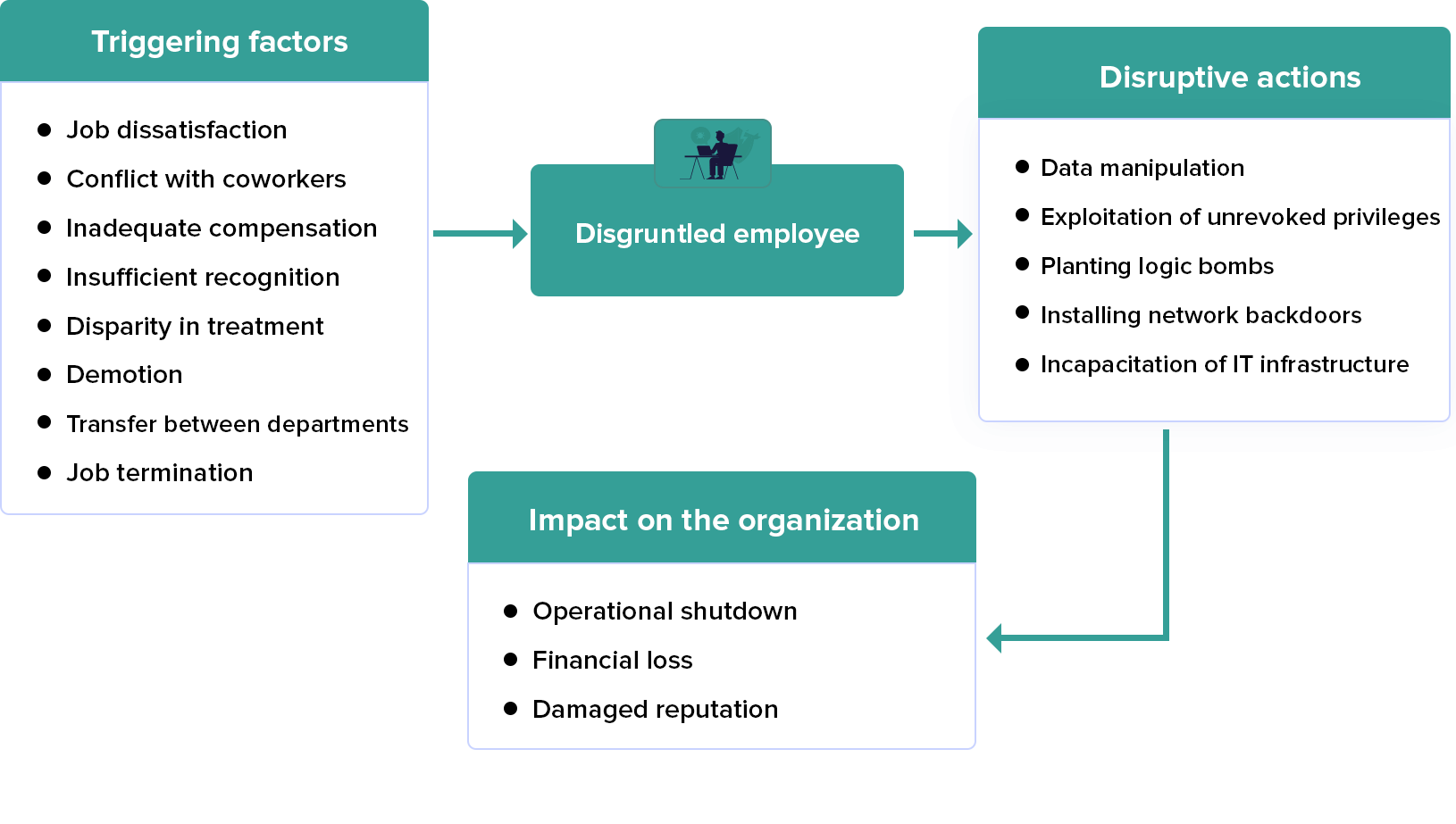
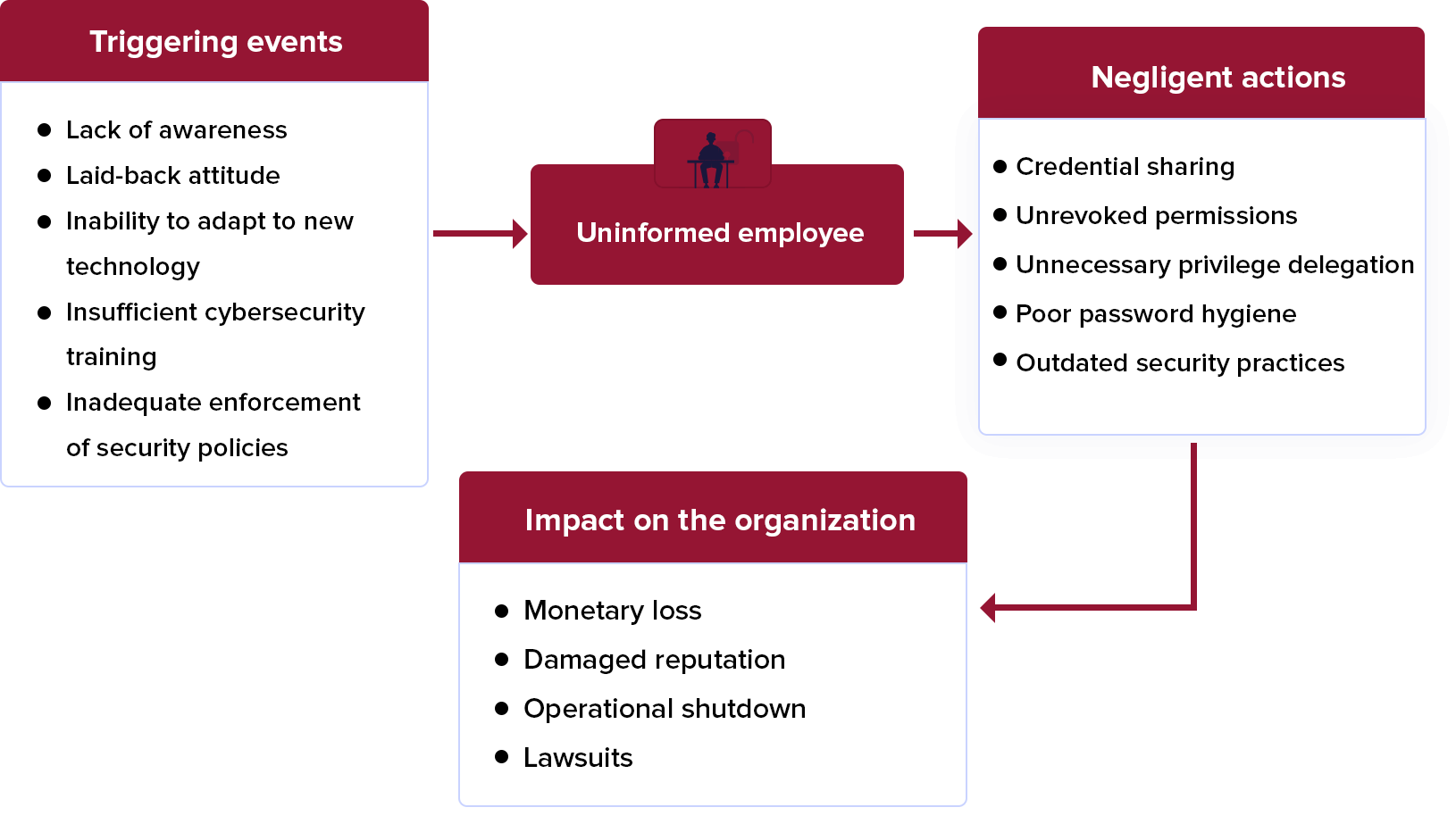
Negligent employee
When an employee is oblivious to IT security best practices, and puts the business at risk due to their behavior.