Introduction
In a world where everything from socializing and shopping to banking and healthcare is online, the importance of securing accounts cannot be emphasized enough. In this regard, passwords play a major role in protecting these identities. But are your passwords really safe? What do attackers do to lay hands on them? And most importantly, how do you stop them?
In this guide, we discuss some popular password attacks, such as phishing, brute-forcing, and keylogging, along with some tips on how not to fall prey to them.
- Phishing attacks
- Man-in-the-middle attacks
- Brute-force attacks
- Credential stuffing
- Keylogging attacks
Phishing attacks
In a phishing attack, the attacker tries to trick users into providing their password by sending emails that look legitimate. These attacks are crafted with one goal: Steal credentials from users.
Regular phishing
Regular phishing emails are mass-targeted emails in which the attacker targets accounts on a well-known service in order to obtain sensitive information. These emails are sent from an email address that’s similar to the actual service, making it difficult to distinguish between real and fake and email addresses.
The email content can be anything from a password reset link to a request for an information update. They usually urge the receiver to act quickly. Since they’re mass-targeted, these emails use generic terms such as “user,” “customer,” or “client” to address the receiver.
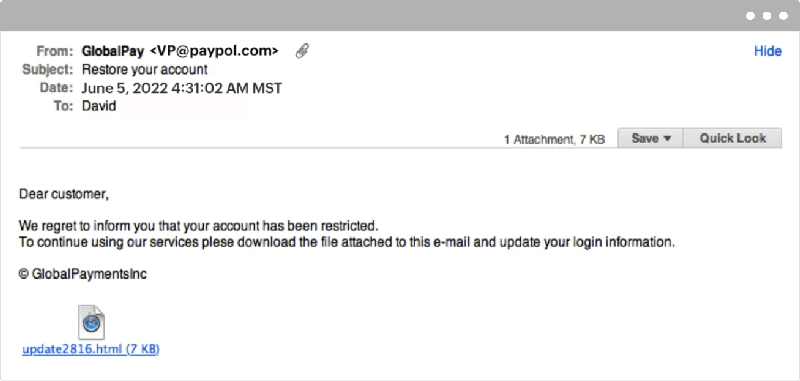
Spear phishing attacks
Spear phishing attacks are targeted specifically at a user or an organization and are perpetrated by hackers posing as a trusted service that could be used by the organization, such as payroll, suppliers, or other third-party subscriptions. Since it’s more personalized, the chances of targeted receivers becoming victims is high.
These emails come in many forms, including:
- Fake bills asking the user to pay for a recent purchase on a website they regularly shop at.
- Password reset links from a bank asking for existing password credentials to reset the password.
- Fake account lockout notifications.
- Login failure notifications asking the user to “re-enter” their credentials.
Watch out for these tell-tale signs
- The email address mimics a trusted organization but is fake
- The email requires urgent action
- The email addresses the receiver in generic terms
- Fake links and shortened URLs
How not to fall prey to phishing attacks
Double-check the sender’s domain address
Attacks try their best to mimic the legitimate domain, but with a bit of scrutiny you can easily spot fake email addresses.
Pause before clicking shortened links
Hover your mouse over the link text and check if the link is the same as the link text. Attackers use shortened link texts to make it look legitimate.
Cross-verify with the concerned person or organization
Don’t hesitate to contact the person or the organization directly to confirm the email is really from them. If you aren’t able to identify the name in the email address, it’s most likely fake.
Report to your IT team
If you aren’t sure about the email, don’t hesitate to mark it as spam or contact your IT team.
Man-in-the-middle attacks
In a man-in-the-middle (MITM) attack, attackers either try to intercept communications or impersonate a trusted authority in order to steal passwords and usernames. MITM attackers can also go one step further and manipulate communication at both ends.
One of the most common ways of carrying out a MITM attack is setting up free, passwordless Wi-Fi hotspots in public spaces. Using this technique, attackers take advantage of the fact that communication over an unprotected network is readable. When unsuspecting users connect to these hotspots, the attacker becomes privy to all their information, including their credentials.
If the communication is over SSL, the attacker deploys various decryption techniques such as HTTPS spoofing, SSL beast, SSL hijacking, or SSL stripping to decrypt user information.
How not to fall prey to MITM attacks
Don't connect to free, unknown hotspots:
Information sent over insecure public networks is easily visible to third parties. A good practice is to not connect to any public hotspots that are not password protected.
Enable encryption on your router:
Encrypted information is harder for MITM attackers to crack. Enabling encryption on your router along with using strong credentials are good practices.
Connect over a VPN:
When accessing your office network or a critical business network from remote locations, VPNs add a layer of protection by encrypting your traffic.
Brute-force attacks
Brute-force attacks are the most popular password attacks in which the attacker tries out different login passwords until they find the right one. There are two types of brute-force attacks: online and offline.
Online brute-force attacks are performed by bots that try different combinations of login information on the targeted service. It's easier to brute-force shorter passwords than longer ones. Some tools used for online brute-force attacks are Medusa, ncrack, and patator. However, online attacks can be thwarted if the account is locked out after a few logins.
To eliminate the problem of account lockouts, attackers perform offline brute-force attacks. In offline attacks, attackers use various tools and techniques to decrypt stolen password hashes. One such technique is the dictionary method, also known as the dictionary attack.
Dictionary attack
Originally, dictionary attacks were a type of brute-force attack where the attacker guessed passwords against a dictionary of words. This dictionary has expanded from lists of words to lists of the most common passwords, their variations when substituting similar-looking numbers or symbols, lists of previously breached passwords, and more.
For more efficiency, attackers sometimes use rainbow tables, which are pre-computed databases of hashed passwords. The stolen hash can be looked up on the rainbow table to find the corresponding plaintext password.
Some popular dictionary attack tools include Cain and Abel, Crack, Aircrack-ng, John the Ripper, L0phtCrack, Metasploit Project, Ophcrack, and Cryptool.
How not to fall prey to brute-force attacks
Use long and complex passwords:
The more complex a password is, the more difficult it is to guess or brute-force. A strong password is 8-15 characters long with a mix of numbers, cased letters, and special characters. Use a password generator or manager to protect yourself from password attacks.
Enable multi-factor authentication:
Multi-factor authentication (MFA) adds an extra layer of authentication to the login process. Even if they have access to your credentials, attackers will be locked out if they try to log in when MFA is enabled.
Change your passwords periodically:
Changing passwords invalidates stolen credentials. It's a good practice to change your passwords every 45 or 90 days.
Credential stuffing
Credential stuffing is unlike brute-force attacks in the sense that the attacker obtains a list of passwords and tries it across different services as opposed to a single service. These attacks rely on the possibility of the same password being used across different services or the reuse of old passwords.
Credential stuffing works with already available plaintext password combinations. Attackers set up several bots that try out stolen credentials across multiple sites and accounts simultaneously. This way, attackers successfully avoid the issue of account lockouts. Credential stuffing attacks have a higher chance of succeeding where brute-force attacks fail, all while evading detection.
How not to fall prey to credential stuffing
If you're an end user
Avoid using your email address as your username:
Email addresses have greater visibility. By using different usernames, you reduce the chances of being exploited.
Use a password manager:
A password manager can keep track of different usernames and passwords across websites.
If you're an IT security professional
Enable MFA and CAPTCHAs:
When bots are used to perform credential stuffing, using MFA and CAPTCHAs can be effective to thwart them.
Block access to headless browsers:
Headless browsers can bypass CAPTCHAs, so they're indicative of suspicious activity.
Monitor your network and blocklist IP addresses:
Check for IP addresses that try to log in to multiple accounts and block them.
Keylogging attacks
Touted as one of the oldest form of cyberattacks, keylogging spyware, if installed on your system, can record every keyboard stroke and pass on the information to attackers through the web.
Keylogging hardware and software is highly useful in applications such as telemetry, development, and testing, where it helps in debugging, proving IT compliance in some corporate environments, and so on. It's sometimes built-in as a hardware or a software feature. However, attackers exploit this functionality in malicious ways.
One example is when they build malware with keystroke logging. These malicious keyloggers can be propagated through techniques such as phishing or vulnerability exploits, or built into malicious websites and apps. When these websites or apps access systems through the web or through direct installation, they quietly spy and collect passwords and other sensitive information. This information is sent over the web to their command and control (C&C) servers.
How not to fall prey to keylogger attacks
If you're an end user
Use antivirus solutions:
Antivirus solutions can scan your downloads for malware and quarantine suspicious applications.
Don't fall prey to phishing attacks:
Malware installations can happen via phishing. Check out the section on phishing for more information.
If you're an IT security professional
Monitor outbound traffic in your network:
Keystroke logging spyware is usually programmed to contact malicious C&C servers from your network. Monitoring outbound traffic with threat intelligence software can help you detect and remediate spyware in your network.
Monitor suspicious software installations:
When keystroke logging spyware is disguised as legitimate software, it can go undetected by antivirus solutions. It's recommended to monitor suspicious activity around a software installation such as multiple login attempts or installations in unusual drives.